AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Troubleshooting Access With IAM Access Analyzer
Welcome to this lesson on troubleshooting access using the IAM Access Analyzer. In this guide, you will learn how to analyze IAM policies and address common access issues in AWS. By understanding the interaction between resource policies, identity-based policies, permission boundaries, and Service Control Policies (SCPs), you can effectively diagnose and resolve access challenges.
The IAM Access Analyzer simplifies the process of identifying permissions by reviewing and validating policies. It is especially beneficial for implementing a least privilege strategy, centrally reviewing access, and refining overly broad permissions.
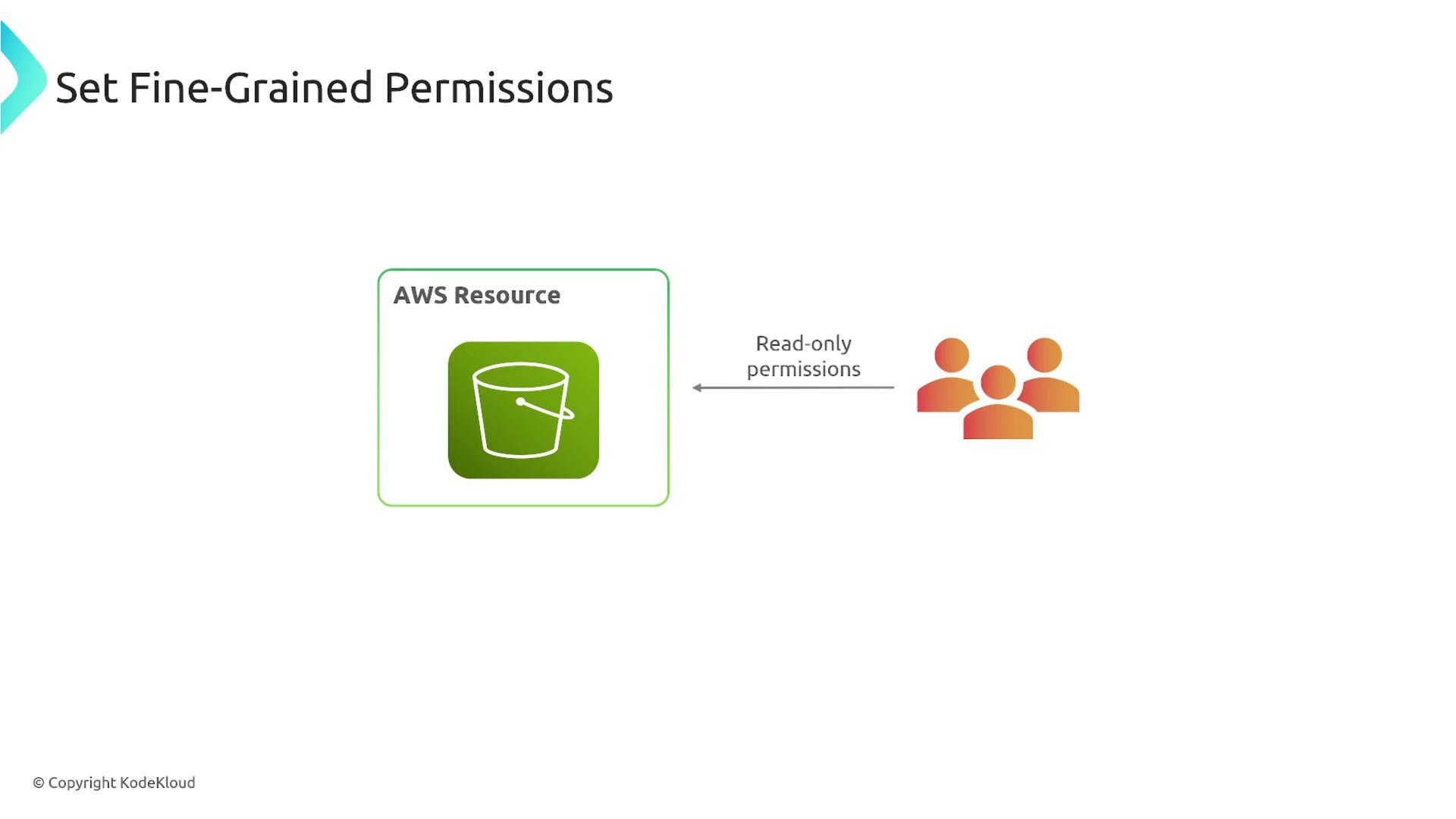
By automating policy reviews and providing clear insights, the Access Analyzer enables you to enforce fine-grained permissions. For instance, if a user only requires read-only access, you can quickly adjust their permissions accordingly.
Note
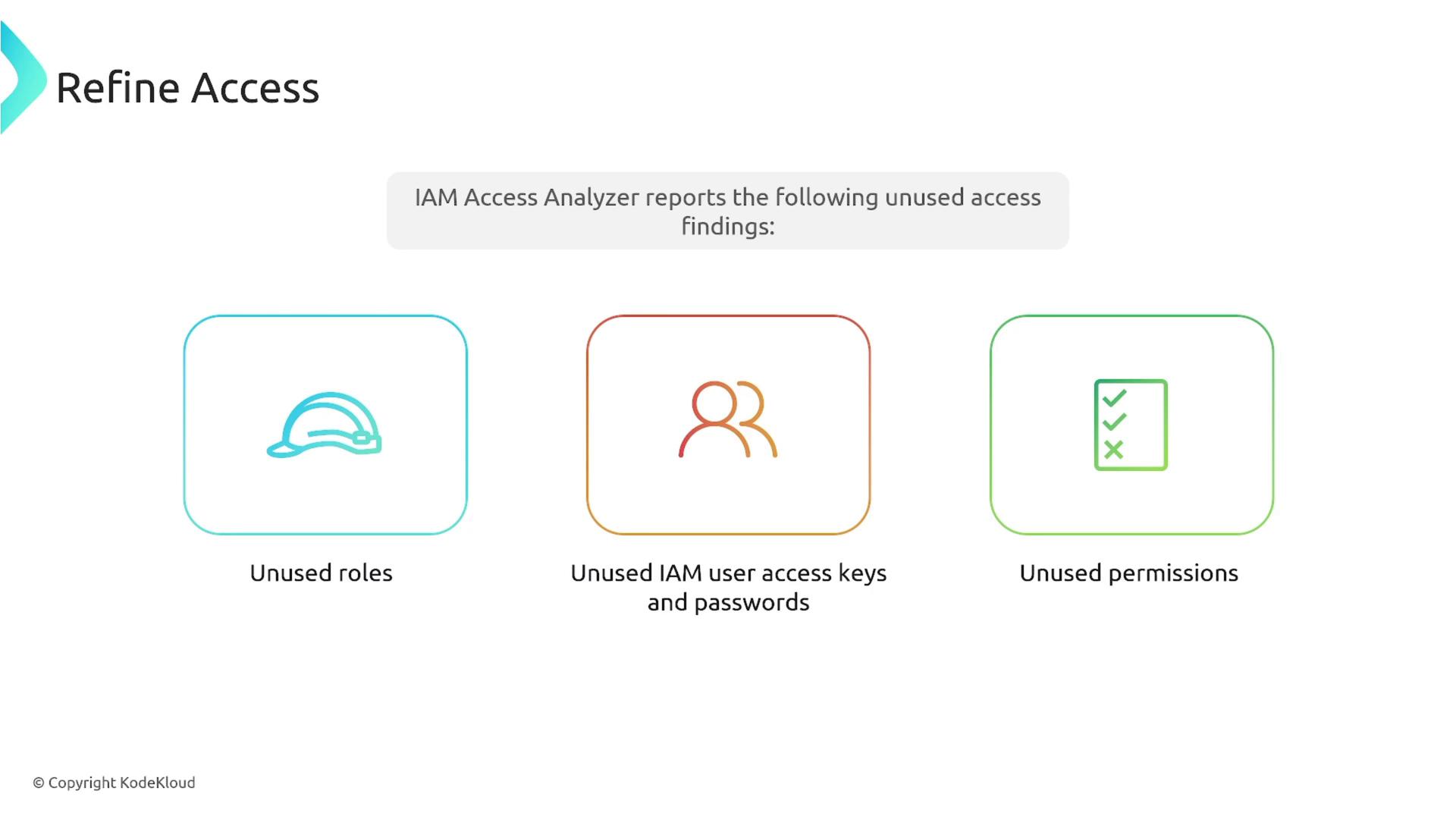
The IAM Access Analyzer also identifies unused access findings for roles, IAM user keys, and passwords, which helps mitigate potential security risks by remediating unused permissions.
Unused access findings can be integrated with AWS Security Hub, centralizing all security-related events and ensuring that unusual or unused access is brought to your attention. Additionally, you can configure the Access Analyzer to automatically trigger remediation actions using AWS services.
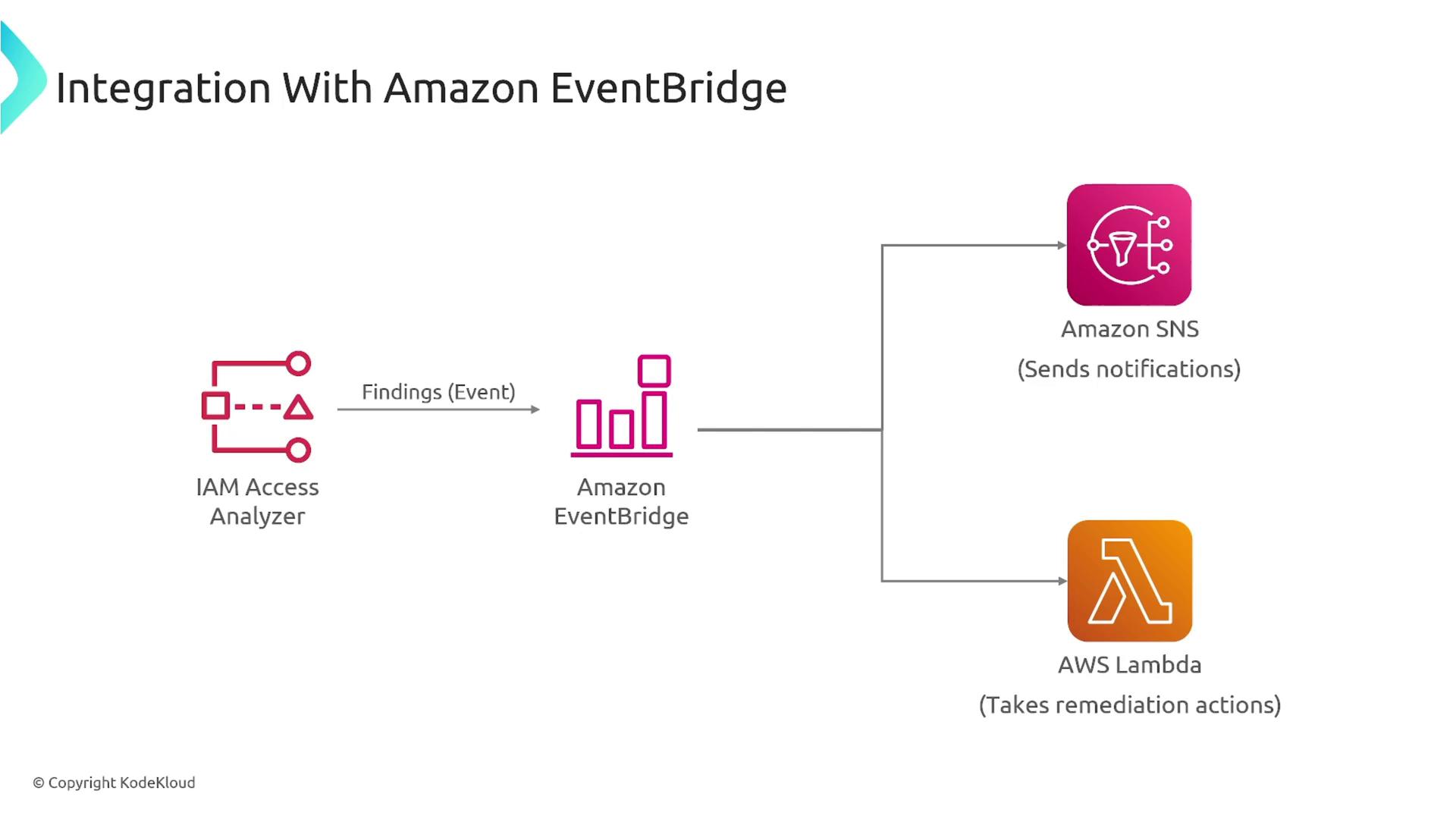
The Security Hub aggregates findings from various AWS services. When the Access Analyzer detects unexpected access patterns or unused permissions, it sends these findings to the Security Hub as security events. This integration ensures that your security team receives prompt alerts and can take action as needed.

For example, findings can trigger an Amazon EventBridge response that sends notifications or invokes AWS Lambda functions to remediate issues—such as revoking permissions that have been unused for a specified period (e.g., 30, 60, 90, or 180 days).
One of the key advantages of IAM Access Analyzer is that it comes at no additional cost. It plays an essential role in identifying unintended public access, such as resources or objects with overly permissive settings, and detecting misconfigured cross-account access. This ensures that only the intended users have access and that their access levels remain strictly controlled.
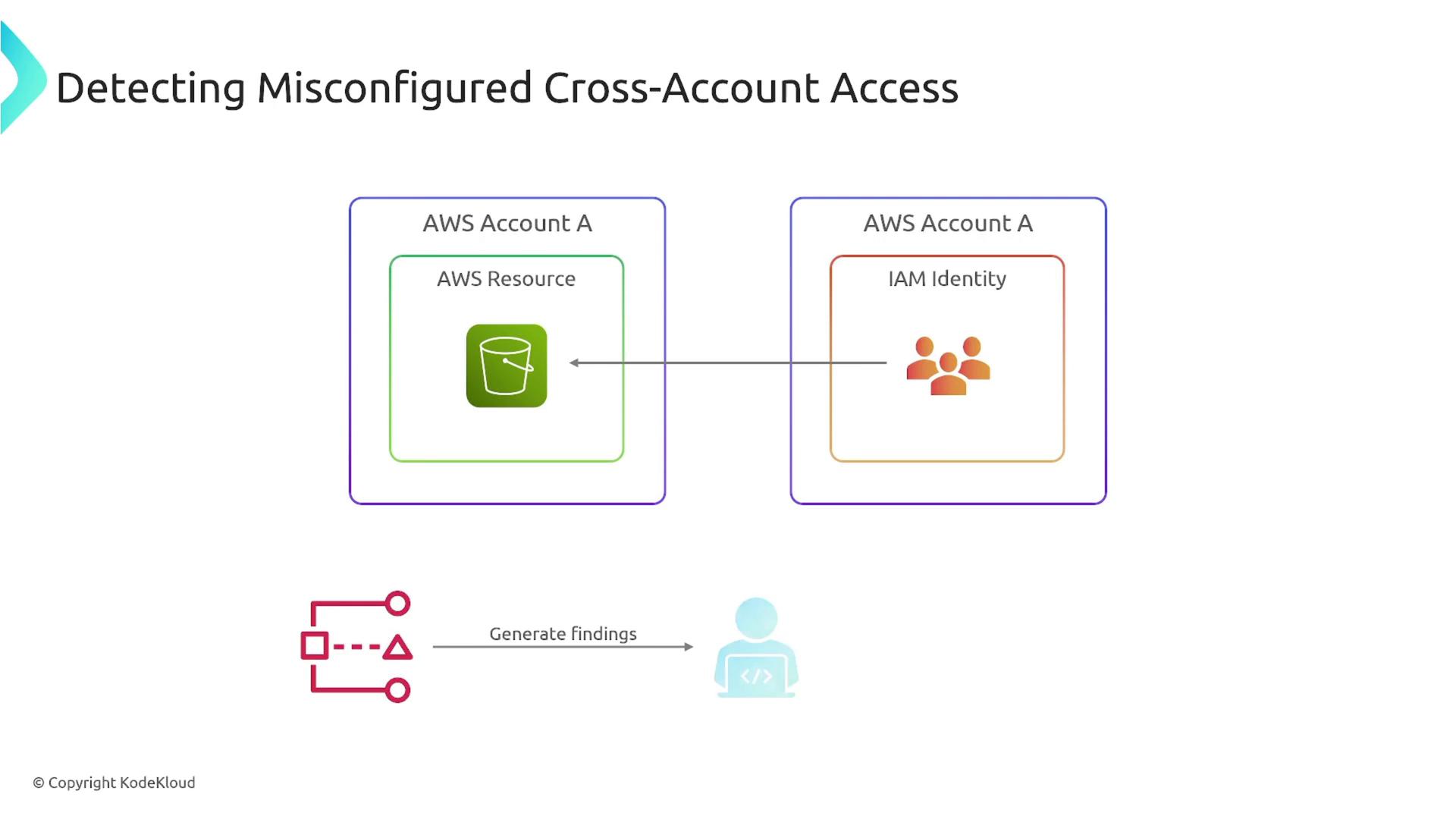
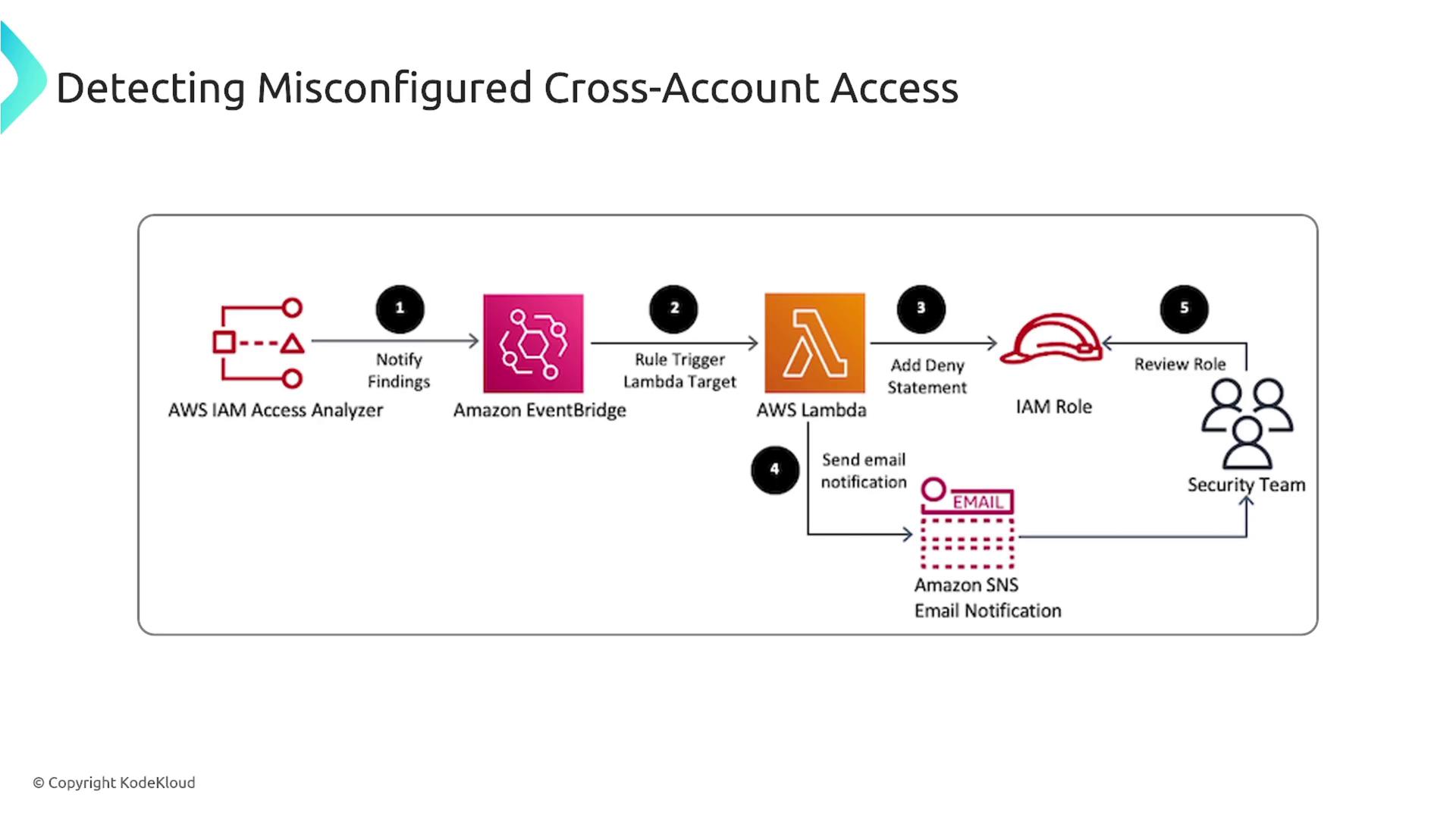
In scenarios where users from one account gain inappropriate access to resources in another account, the Access Analyzer detects these misconfigurations. Such findings can trigger automated processes—for example, sending notifications or modifying role settings via EventBridge and Lambda—to ensure that your security team is alerted and necessary changes are applied.
Integrating these capabilities, the IAM Access Analyzer is an effective tool for identifying unused permissions, detecting non-compliant access patterns, and ensuring adherence to the principle of least privilege. It not only generates valuable insights regarding access but also integrates with AWS EventBridge, Lambda, and Security Hub to automate remediation actions and improve overall security posture.
Warning
Always ensure you review and test any automated remediation actions in a controlled environment. Incorrect configurations or overzealous automation can lead to unintended access restrictions.
In summary, the IAM Access Analyzer is an essential part of managing access in AWS environments. It effectively supports least privilege practices and secures your resources by detecting and addressing misconfigurations and unused permissions.
If you come across a question regarding the enforcement of least privilege using IAM Access Analyzer on your exams or in practical scenarios, remember that its capabilities extend across validating permissions, integrating with other AWS services for automated responses, and ultimately ensuring a robust security posture.
Thank you for reading, and we look forward to seeing you in the next lesson.
Watch Video
Watch video content