Virtual Private Cloud (VPC)
A VPC is a logical, isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. It gives you complete control over your networking environment, allowing you to:- Configure subnets, IP ranges, routing tables, network access control lists (NACLs)
- Define security groups for controlling traffic at the instance level
- Manage gateways to regulate traffic between your VPC and the internet
VPCs and AWS Regions
VPCs are region-specific. When creating a VPC, you must choose a region (e.g., US East 1, US East 2, Australia) where your VPC and its resources will be deployed. This regional limitation means that resources within a VPC are confined to that specific region.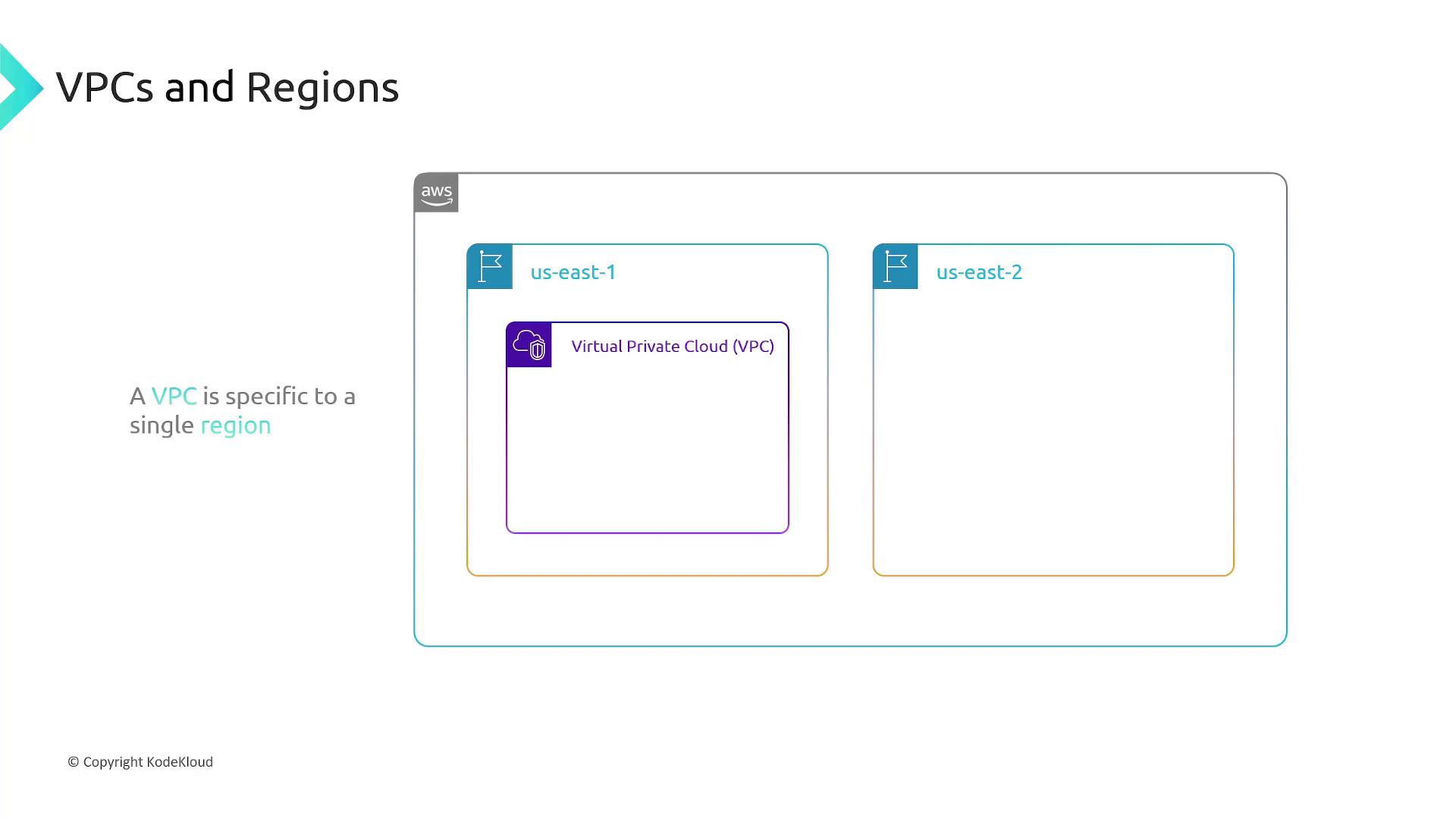
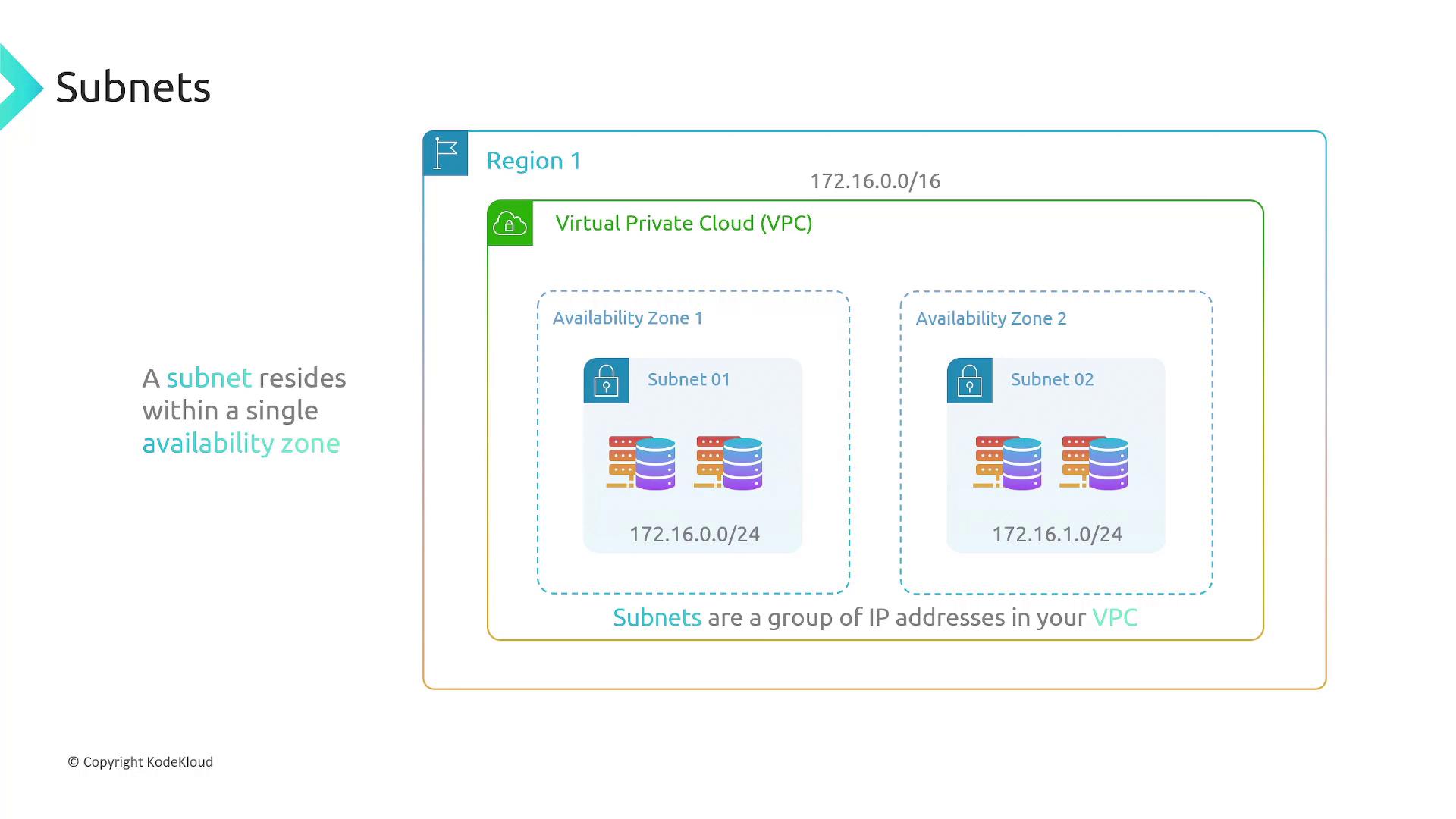
Subnets
Subnets are subdivisions of a VPC’s IP address range (CIDR block), providing more granular control over where resources reside. When you create subnets, each is associated with a single Availability Zone. For example, consider the following subnets:- Subnet 1: IP range 172.16.0.0/24
- Subnet 2: IP range 172.16.1.0/24
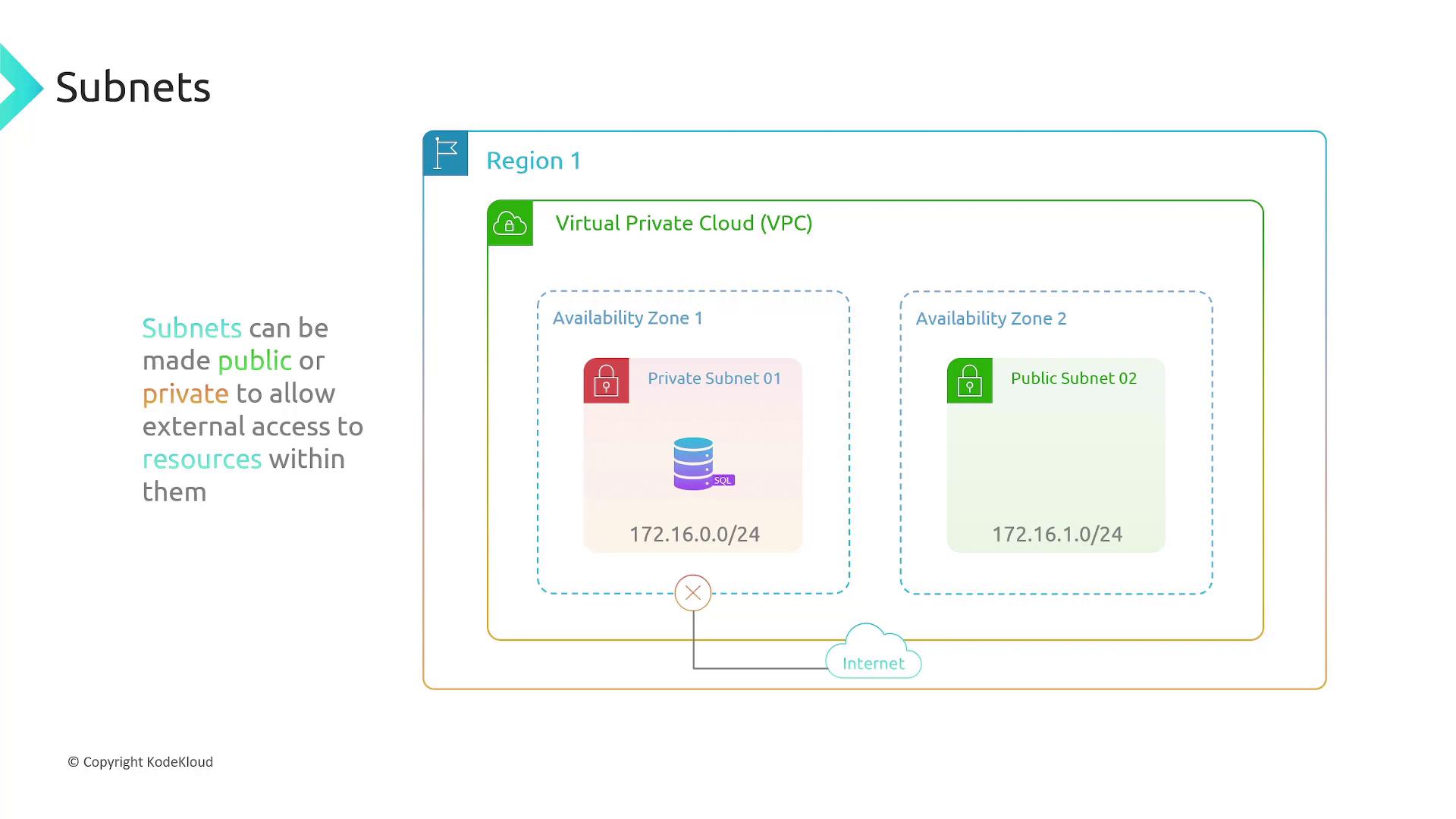
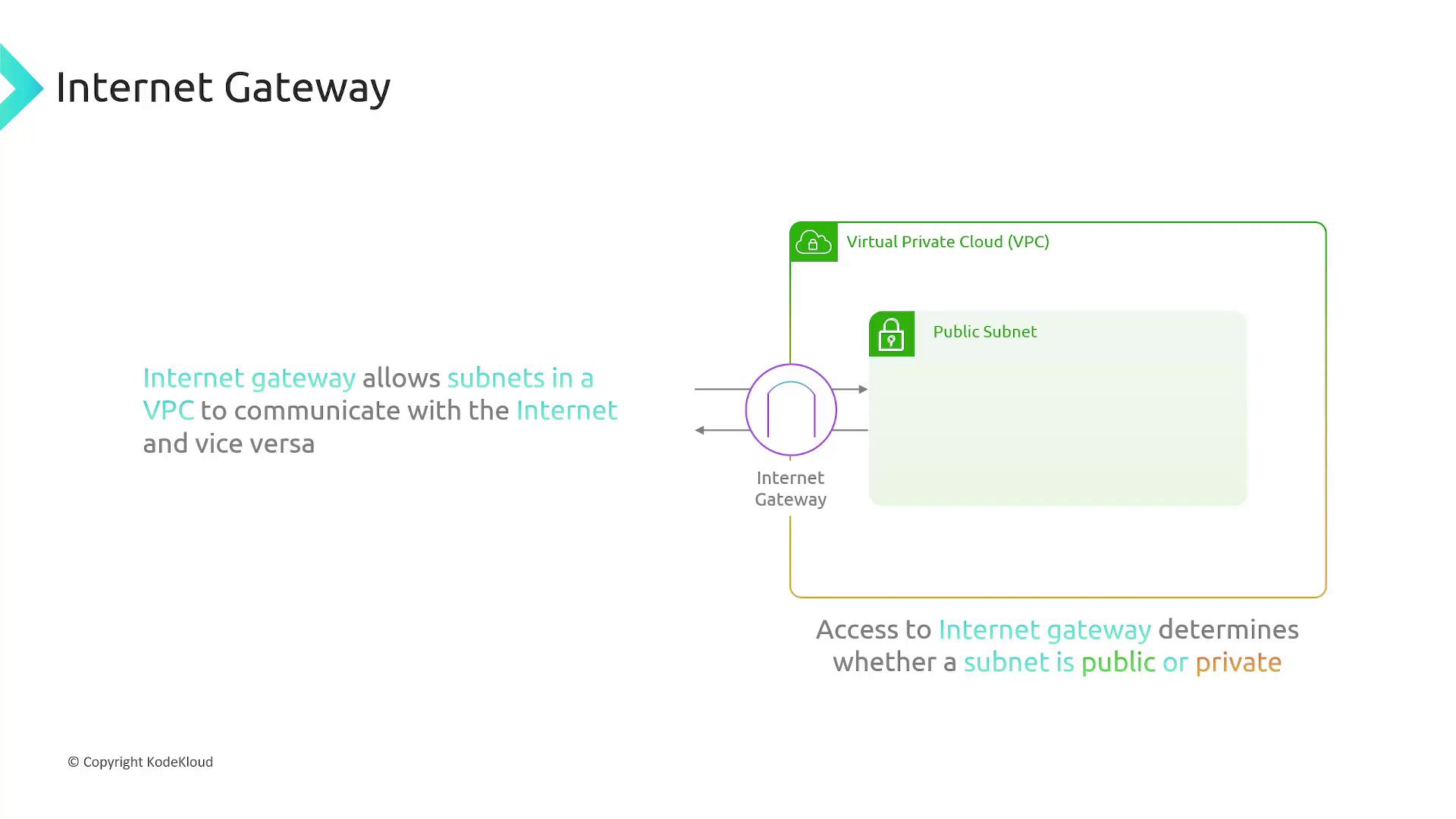
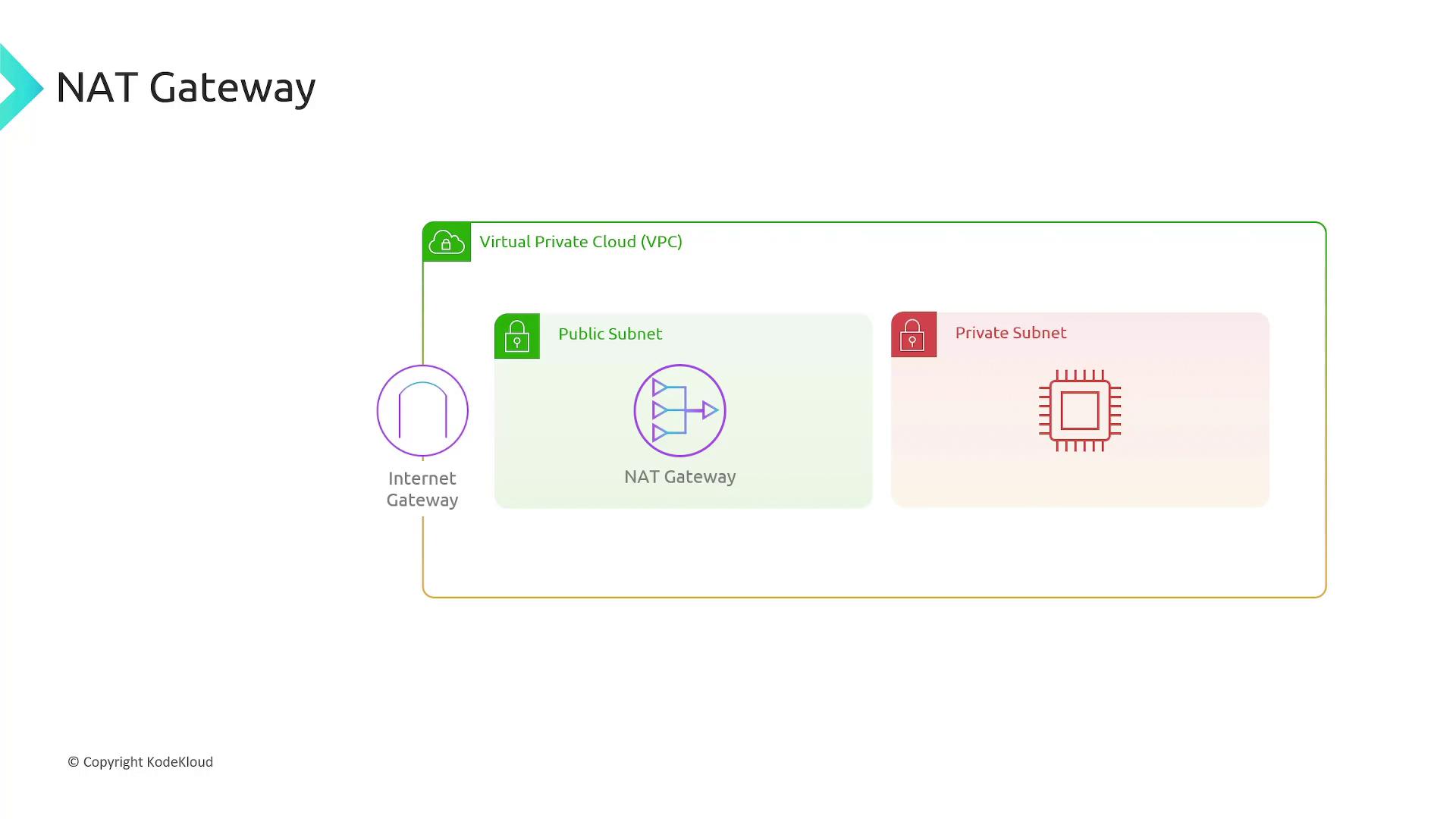
- Public Subnet: Directly exposed to the internet via an attached Internet Gateway. Ideal for web servers.
- Private Subnet: Not directly accessible from the internet, making it suitable for databases and internal resources.
Hybrid Deployments and CIDR Blocks
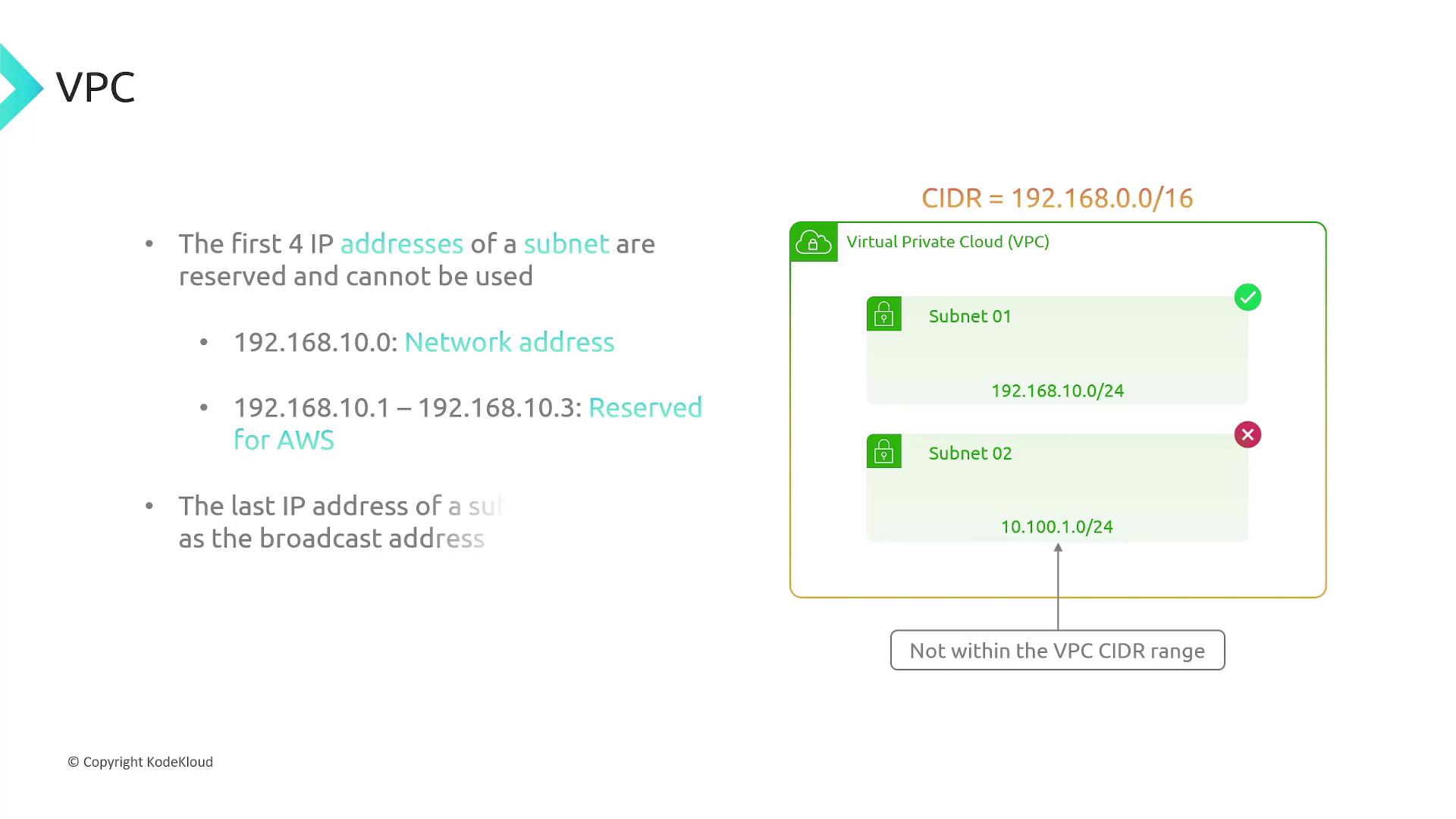
For hybrid deployments, you can extend your on-premises data center to AWS using VPN connections. When creating a VPC, you must define a CIDR block—a range of IP addresses available to your VPC. For example, specifying a CIDR block of 192.168.0.0/16 allocates addresses from 192.168.0.0 to 192.168.255.255.AWS reserves the first four IP addresses and the last IP address in each subnet for internal use. In a 192.168.10.0/24 subnet, usable IP addresses start at 192.168.10.4.
Internet Connectivity for Subnets
By default, subnets are private and not accessible from the internet. To enable internet connectivity, you need to associate your subnet with an Internet Gateway. The Internet Gateway is attached to the VPC and allows bi-directional traffic between the internet and public subnets.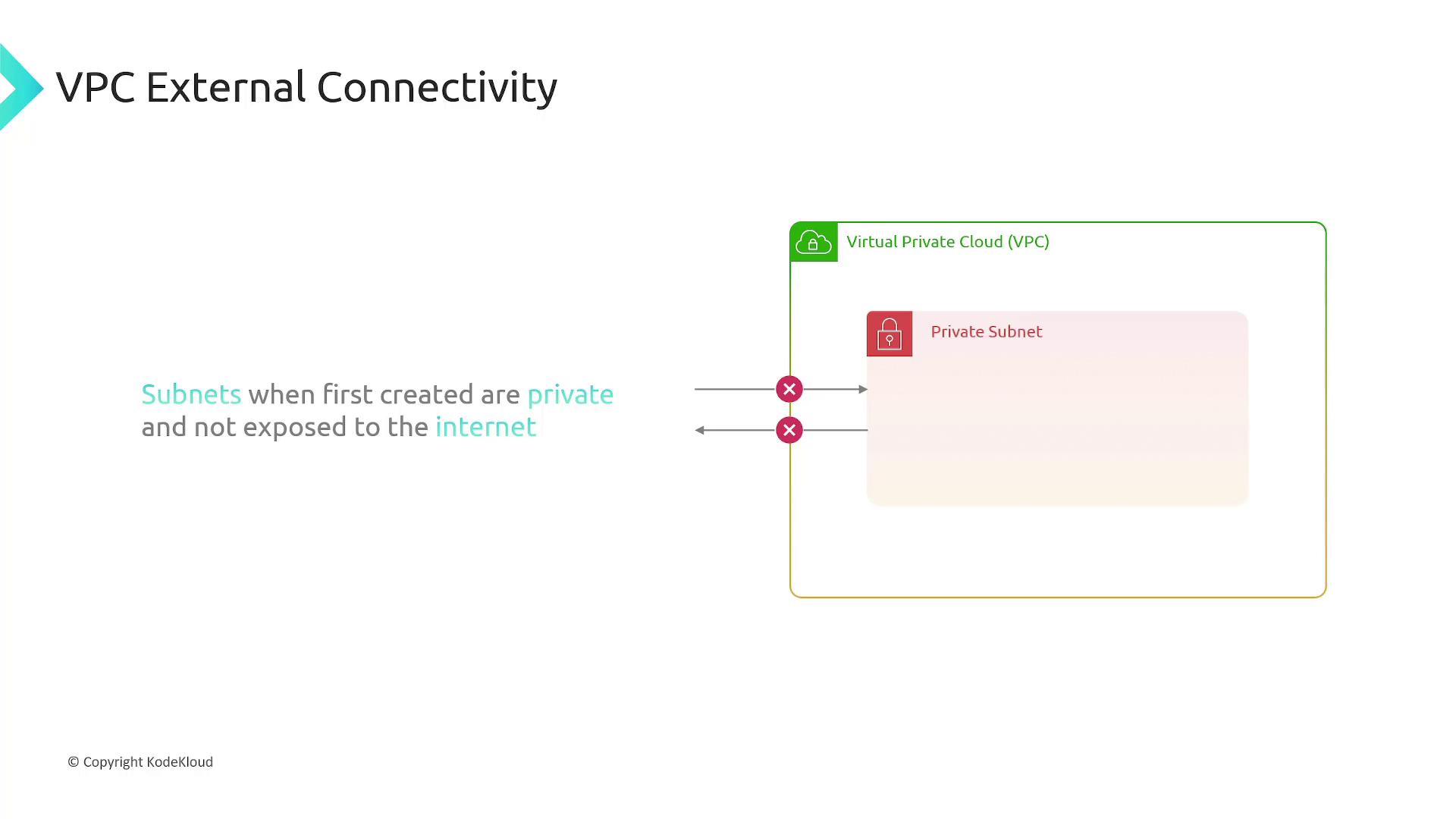
Secure Connectivity to Private Resources
Managing or monitoring resources in a private subnet requires secure connectivity. To achieve this, AWS offers VPN gateways (also known as Virtual Private Gateways). These gateways establish an encrypted VPN connection over the internet, enabling secure access to private resources.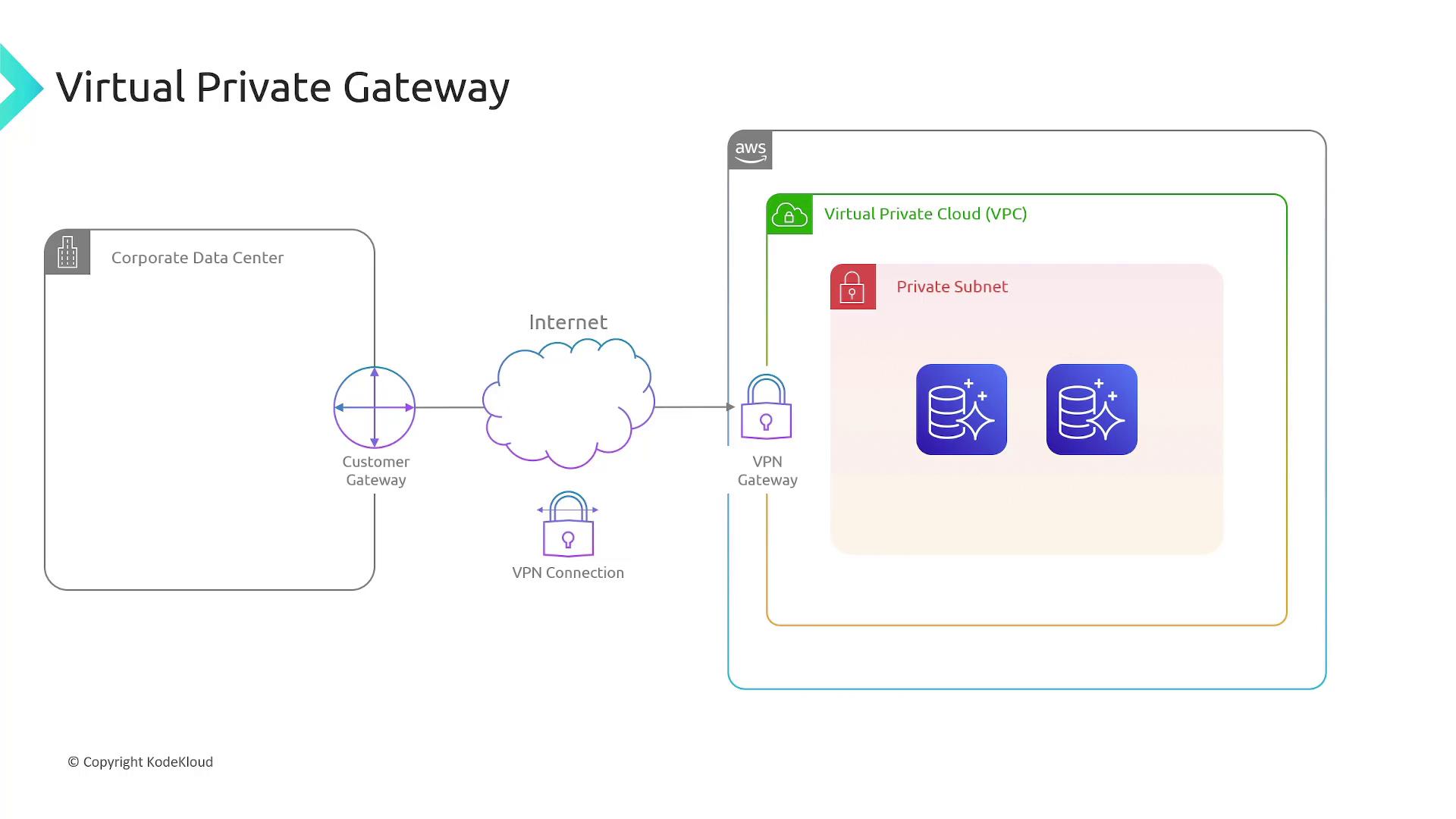
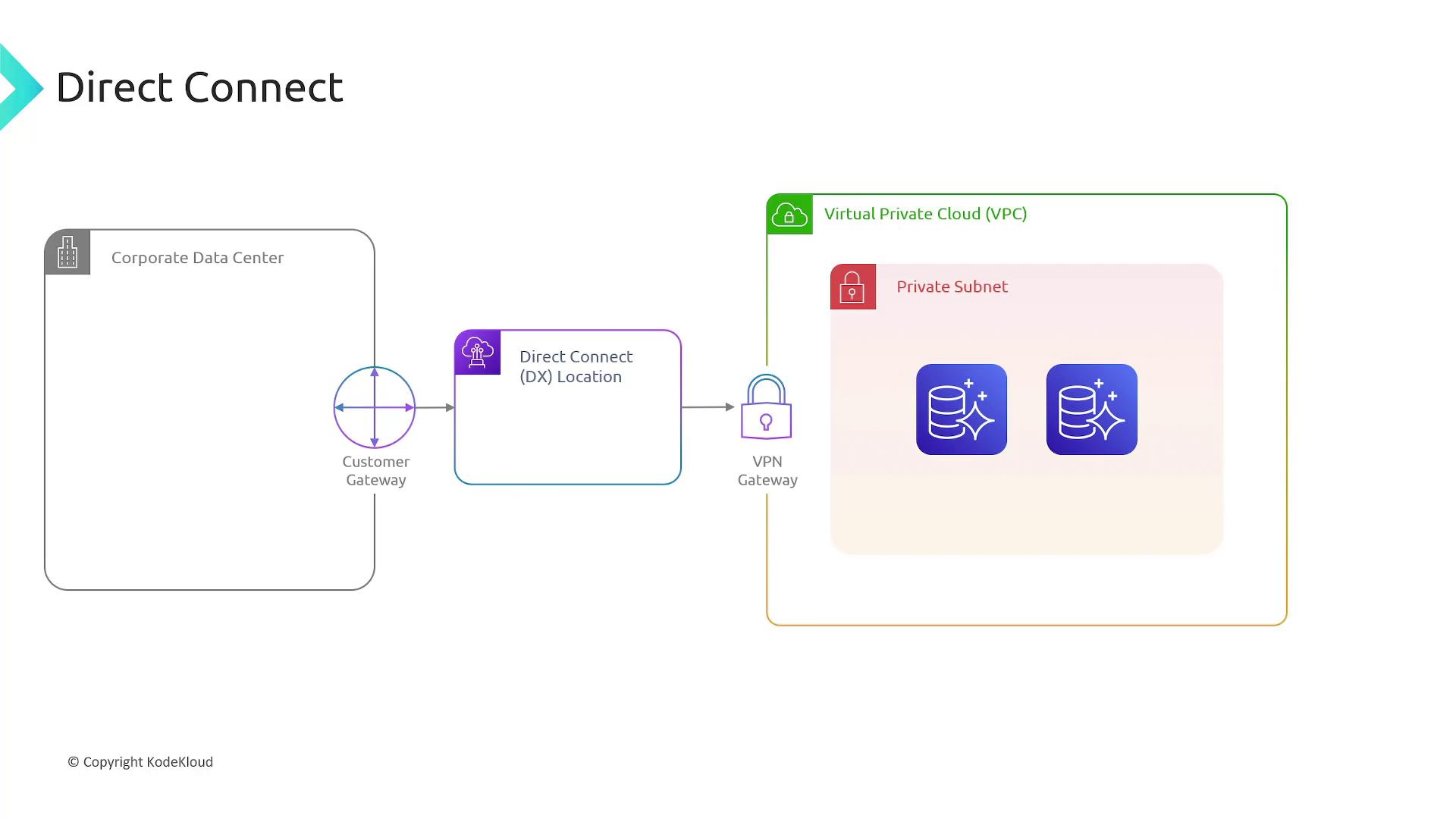
Summary
To recap, here are the essential points covered in this article:- A Virtual Private Cloud (VPC) offers a secure, isolated networking environment in AWS where you can control IP addressing, subnets, and traffic flow.
- Each VPC is linked to a single region and is defined by a CIDR block, with subnets carved out of that block.
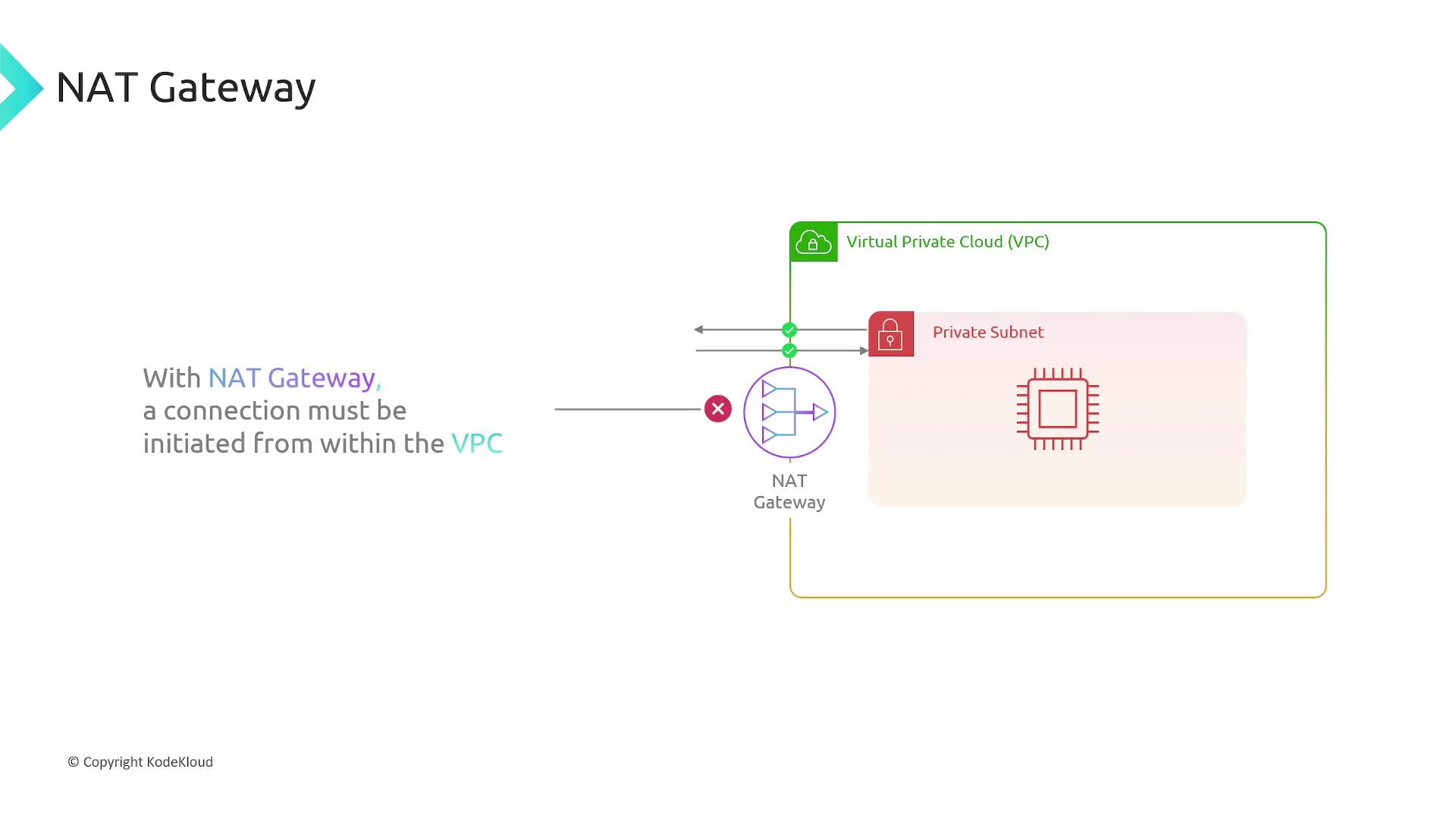
- Subnets are designated as public (with direct internet access via an Internet Gateway) or private (requiring a NAT gateway for internet access).
- Secure connectivity to private resources is enabled through VPN gateways or AWS Direct Connect.