- A running EC2 instance under stress
- A CPU utilization alarm
- Email notifications on alarm trigger
1. Launch an EC2 Instance
- Sign in to the AWS Management Console and confirm you’re in the correct region.
- Navigate to EC2 → Instances and click Launch Instance.
- Under Name, enter
demo-instance. Select Amazon Linux 2023 as your AMI. - In Key pairs, choose Proceed without a key pair.
Launching without a key pair prevents SSH login via key-based authentication. You’ll connect using EC2 Instance Connect or Session Manager.
- Keep the default VPC and subnet. Under Security groups, select Create security group with default rules.
- Click Launch instances, then view your instance on the Instances page. Wait until its status changes from Pending to Running.
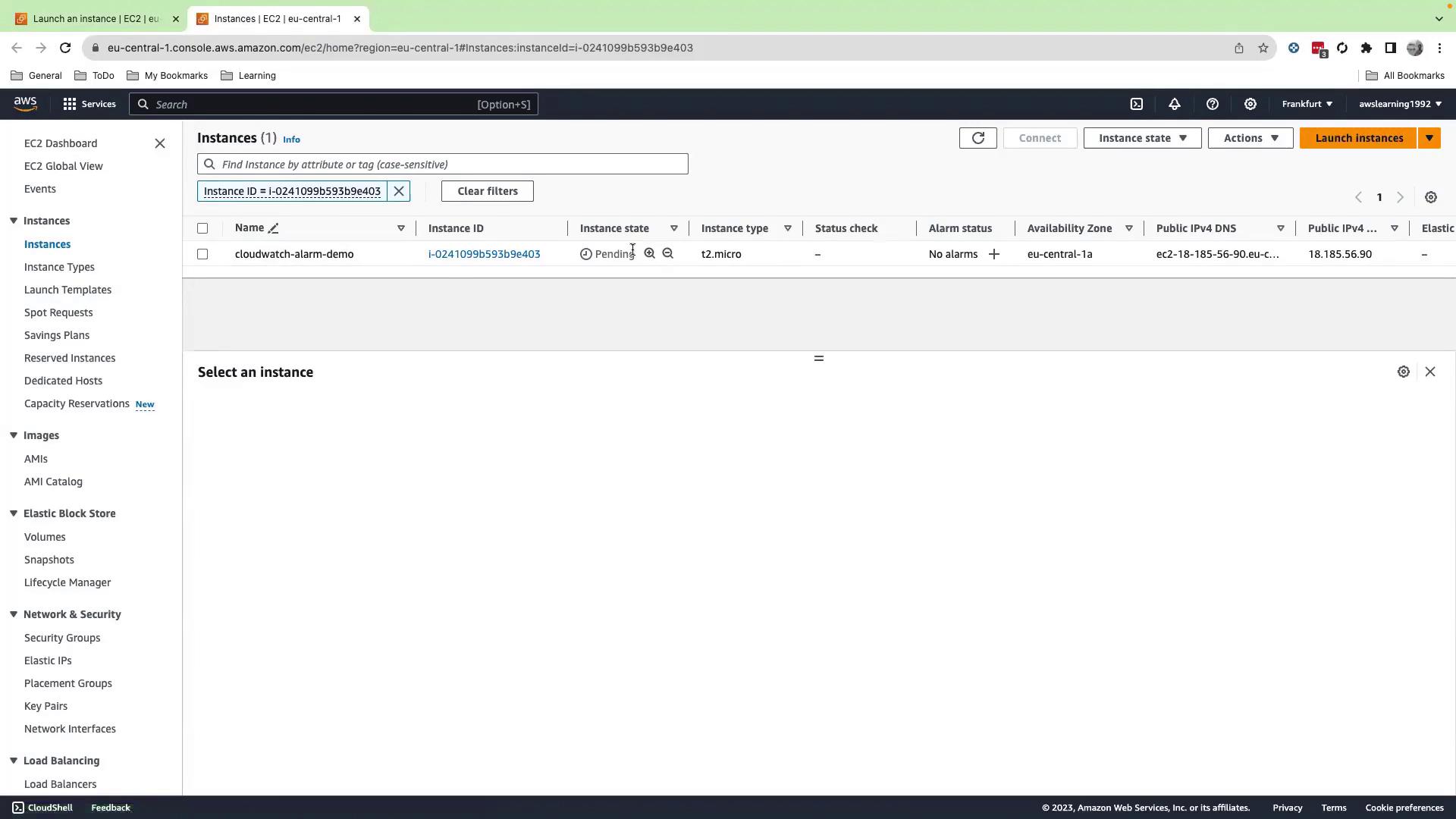
2. Connect to the Instance
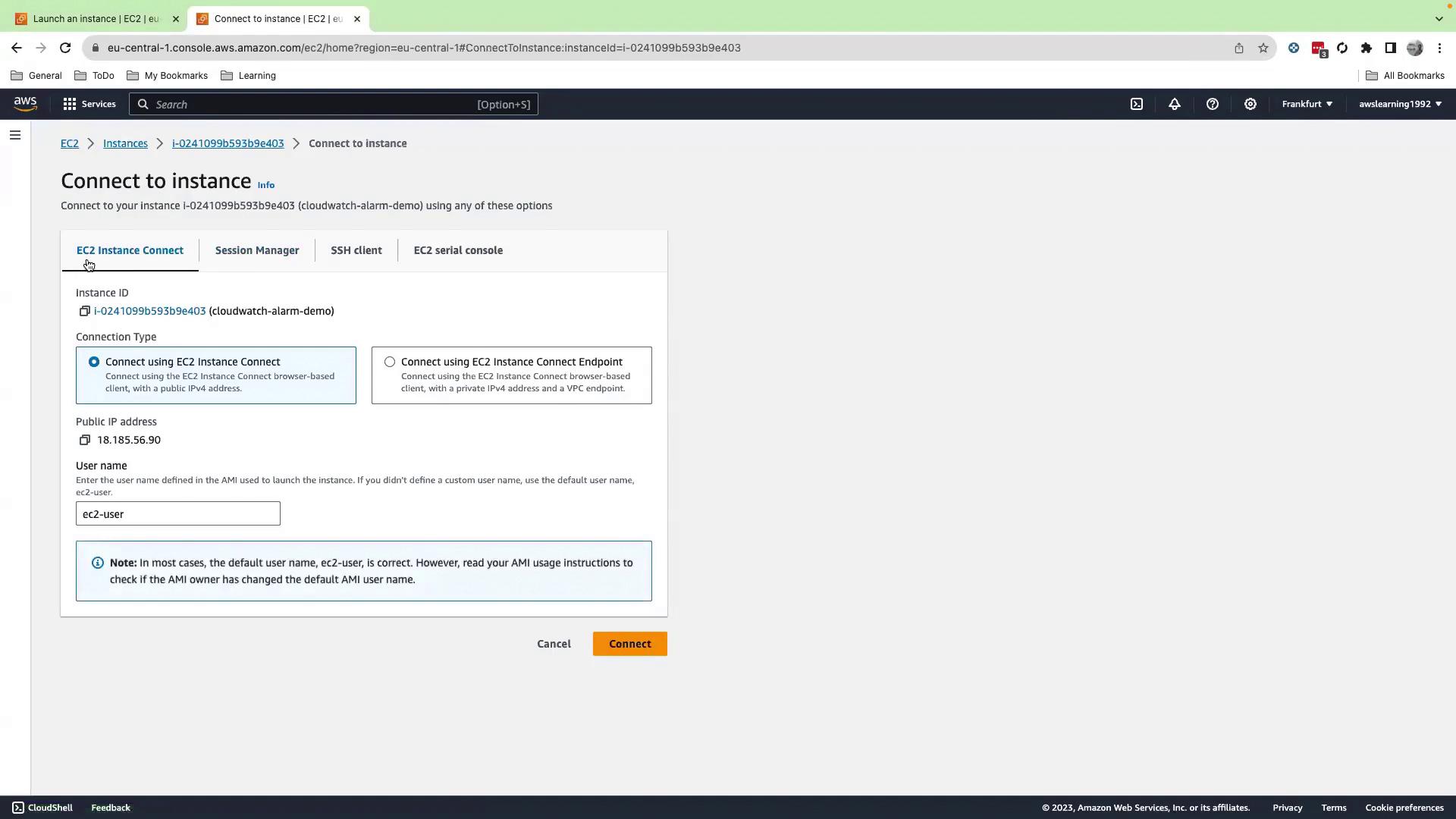
- Select your running instance and click Connect.
- Choose EC2 Instance Connect and then Connect again to open the browser-based shell.
- Switch to root:
3. Install and Run the stress Utility
CloudWatch doesn’t collect detailed CPU or memory load by default. To simulate load:stress:
Ctrl+C to stop the load.
stress Command Options
| Flag | Description | Example |
|---|---|---|
| —cpu | Number of CPU workers | --cpu 4 |
| —io | Number of I/O workers | --io 4 |
| —vm-bytes | Memory per VM worker | --vm-bytes 1G |
| —hdd | Number of HDD workers | --hdd 2 |
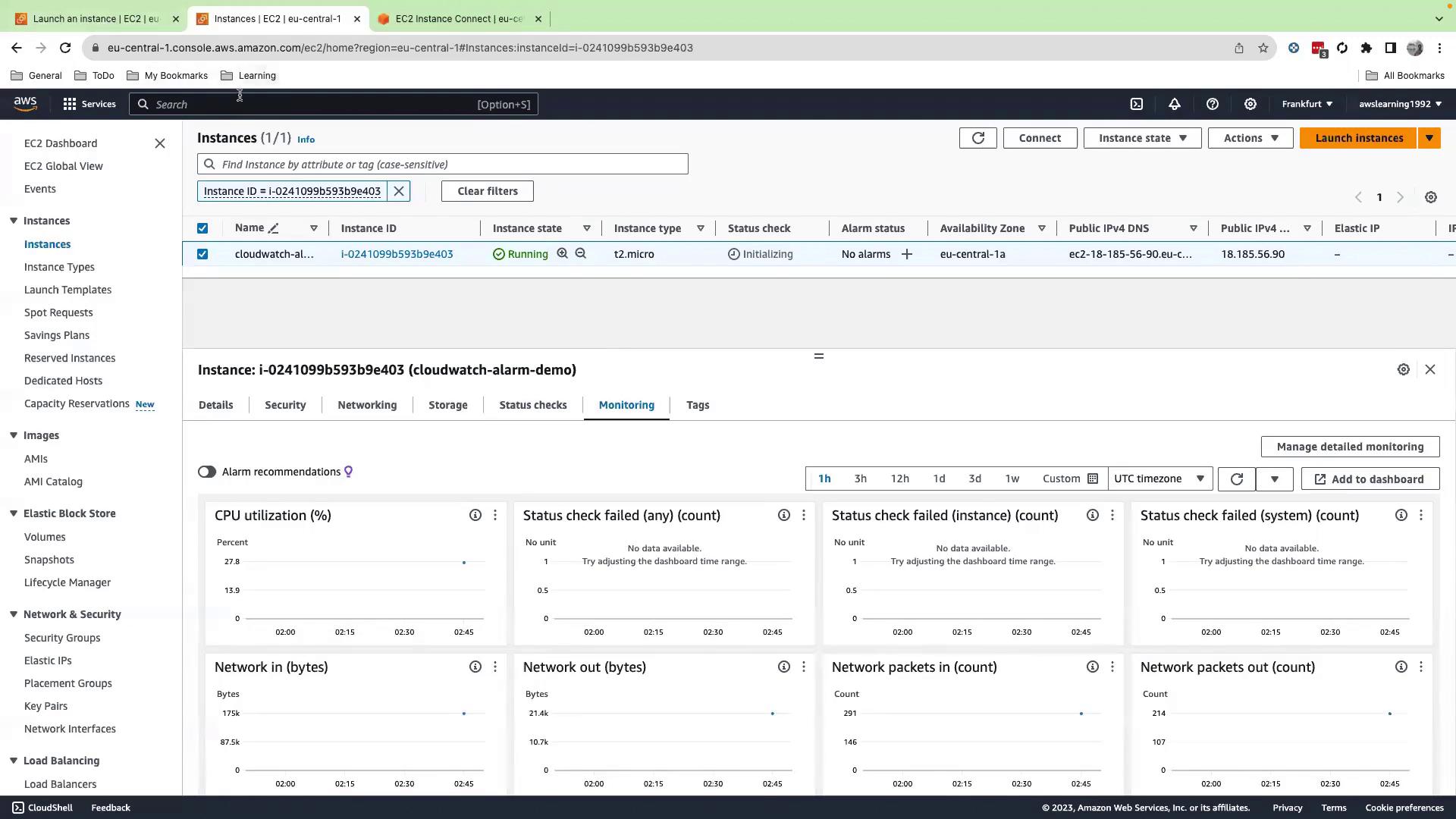
4. View Metrics in CloudWatch
- Open the CloudWatch console in a new tab.
- Go to Alarms → Create an alarm.
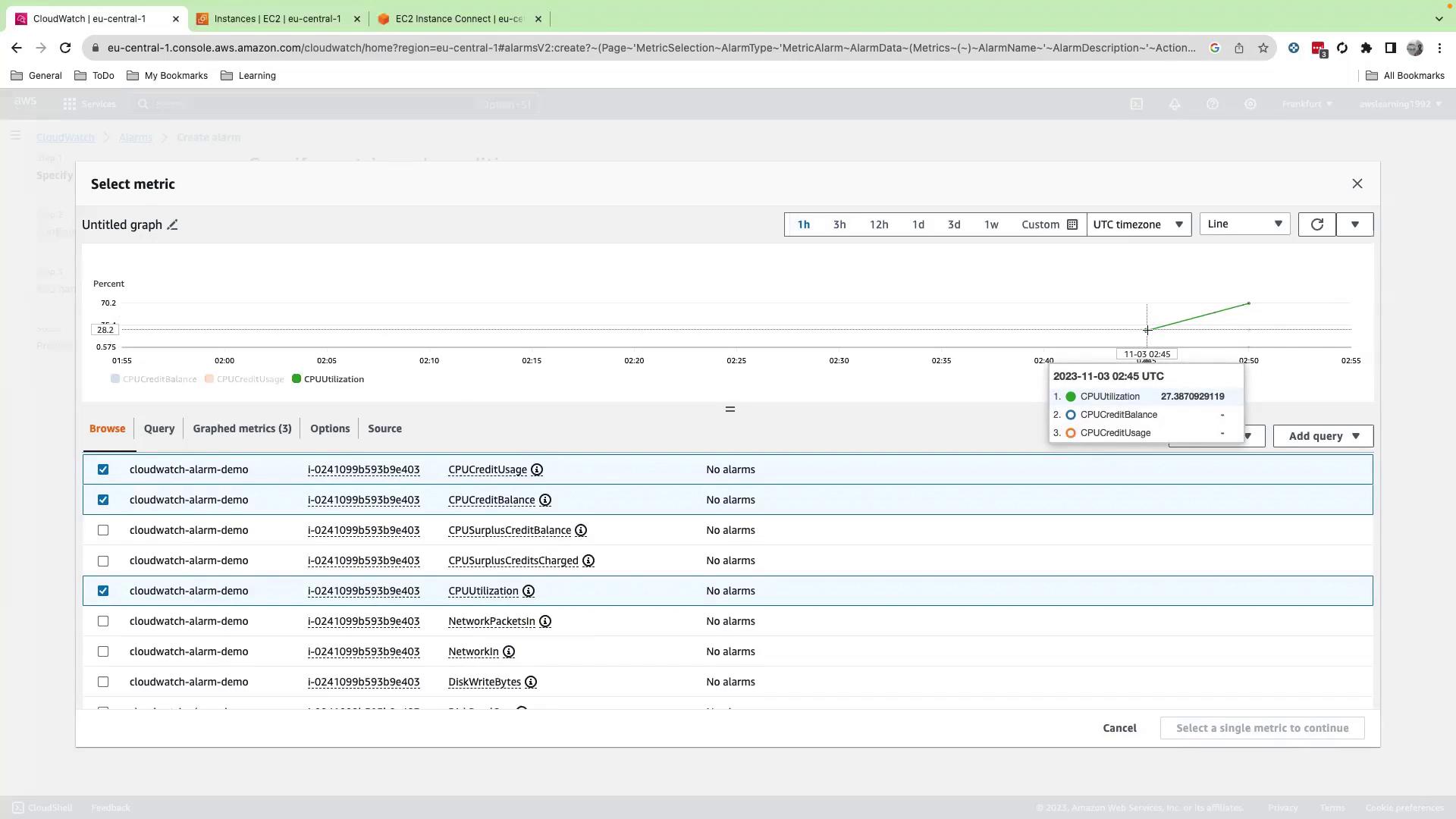
- Click Select metric, navigate to EC2 → Per-Instance Metrics, and search your instance ID.
- Initially select CPU Credit Balance, CPU Credit Usage, and CPU Utilization, then set the graph to a 1-hour view to spot spikes.
- Because alarms support only one metric at a time, uncheck the credit metrics and keep CPU Utilization selected, then click Select metric.
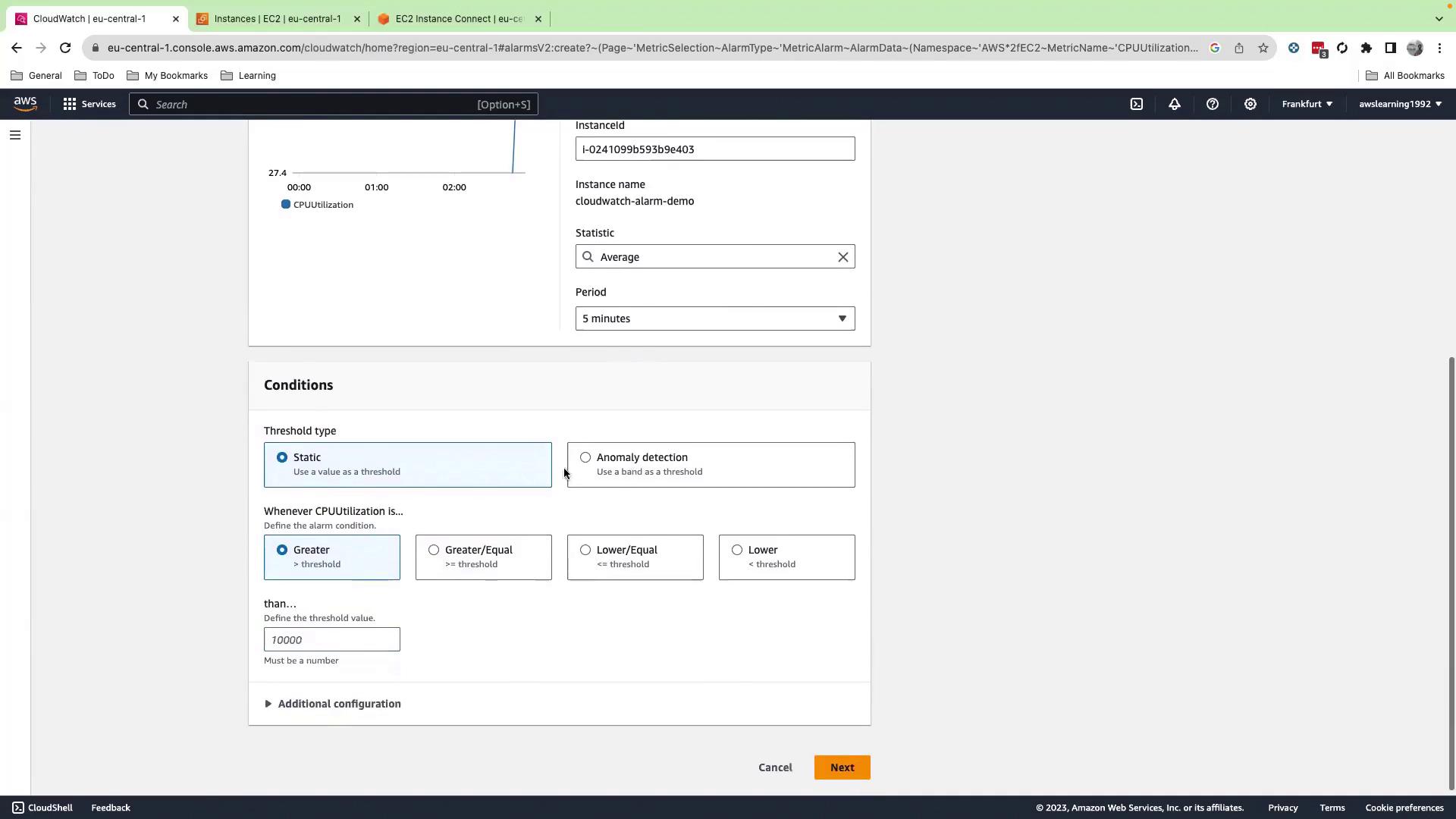
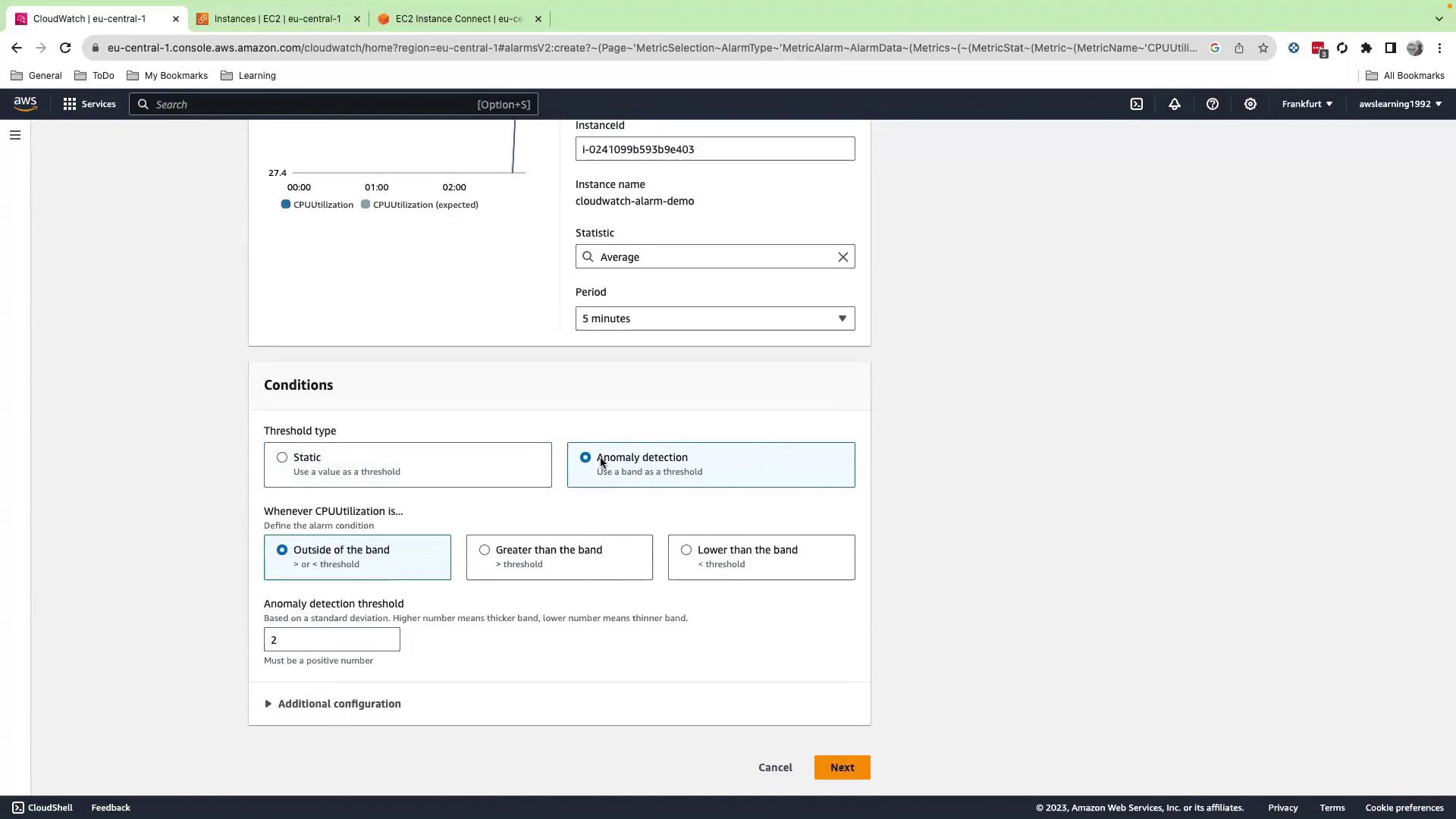
5. Configure Alarm Conditions
- Under Threshold type, choose Static.
- Set Greater than or equal to 65 (%).
- Click Next.
You can also use Anomaly detection for adaptive thresholds that adjust based on historical data.
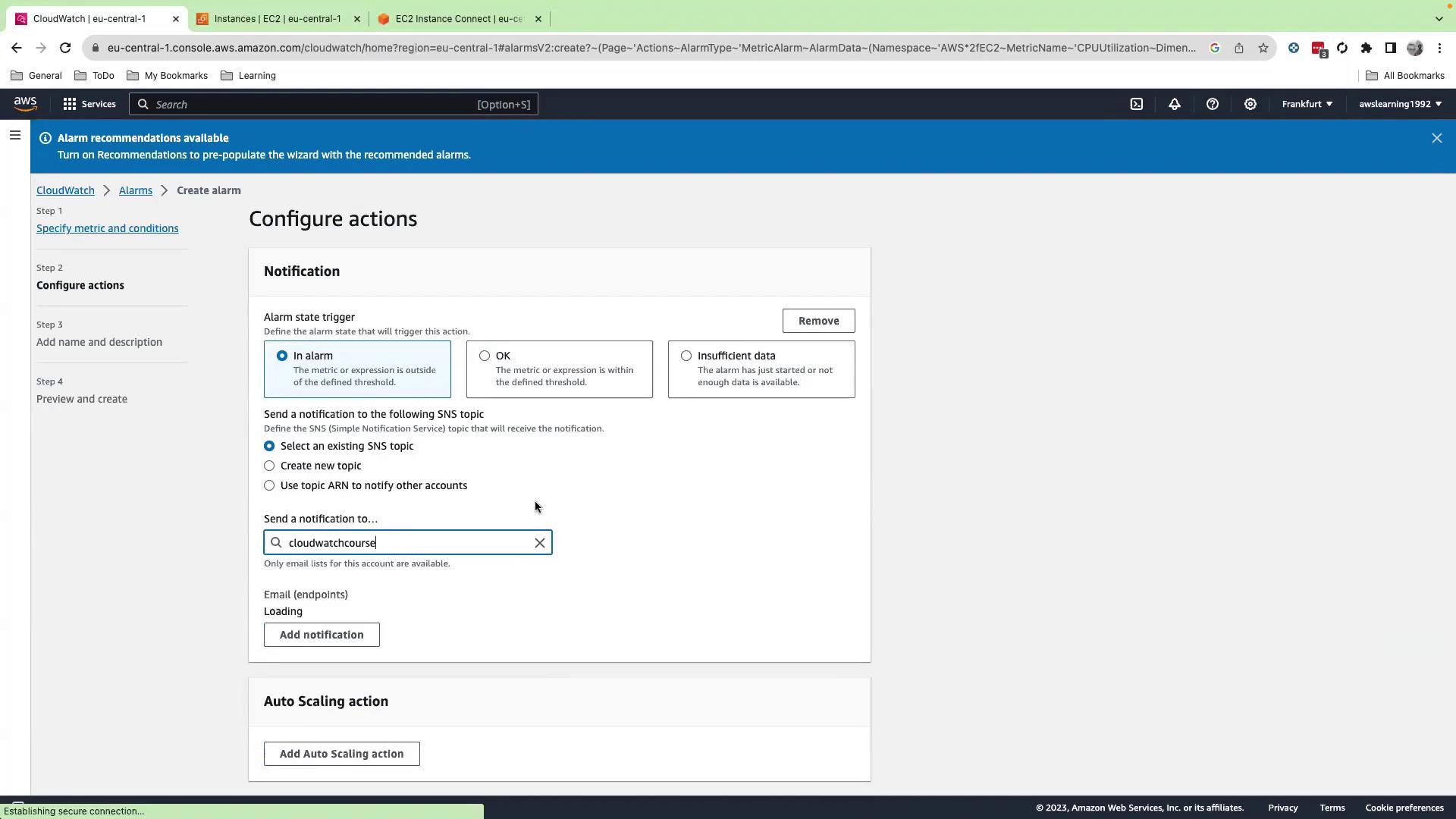
6. Set Alarm Actions
- Under Select an SNS topic, choose an existing topic—e.g.,
CloudWatch-course-topic. - This topic delivers email alerts to its subscribers.
- Click Next.
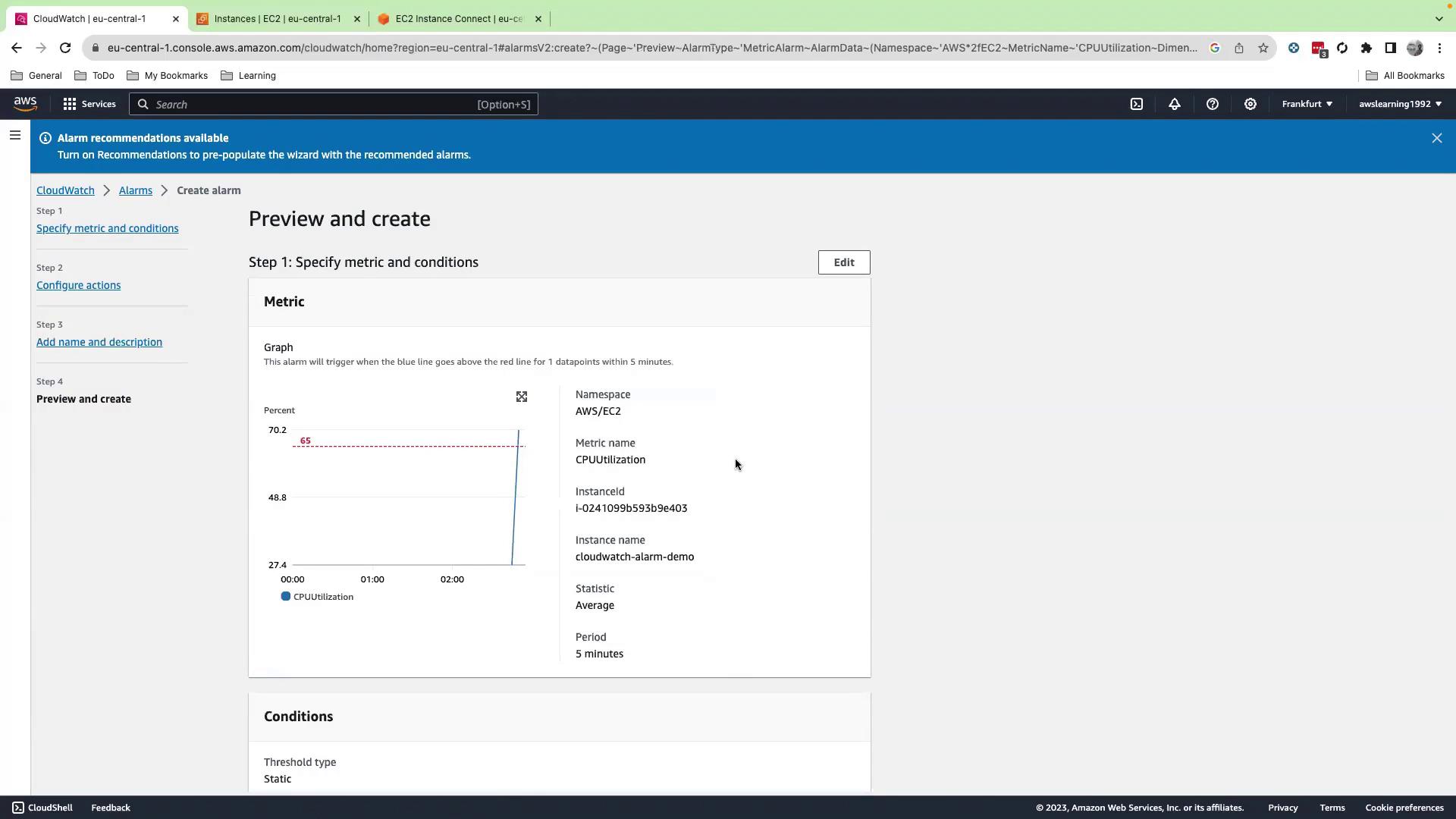
- Provide an alarm name (e.g.,
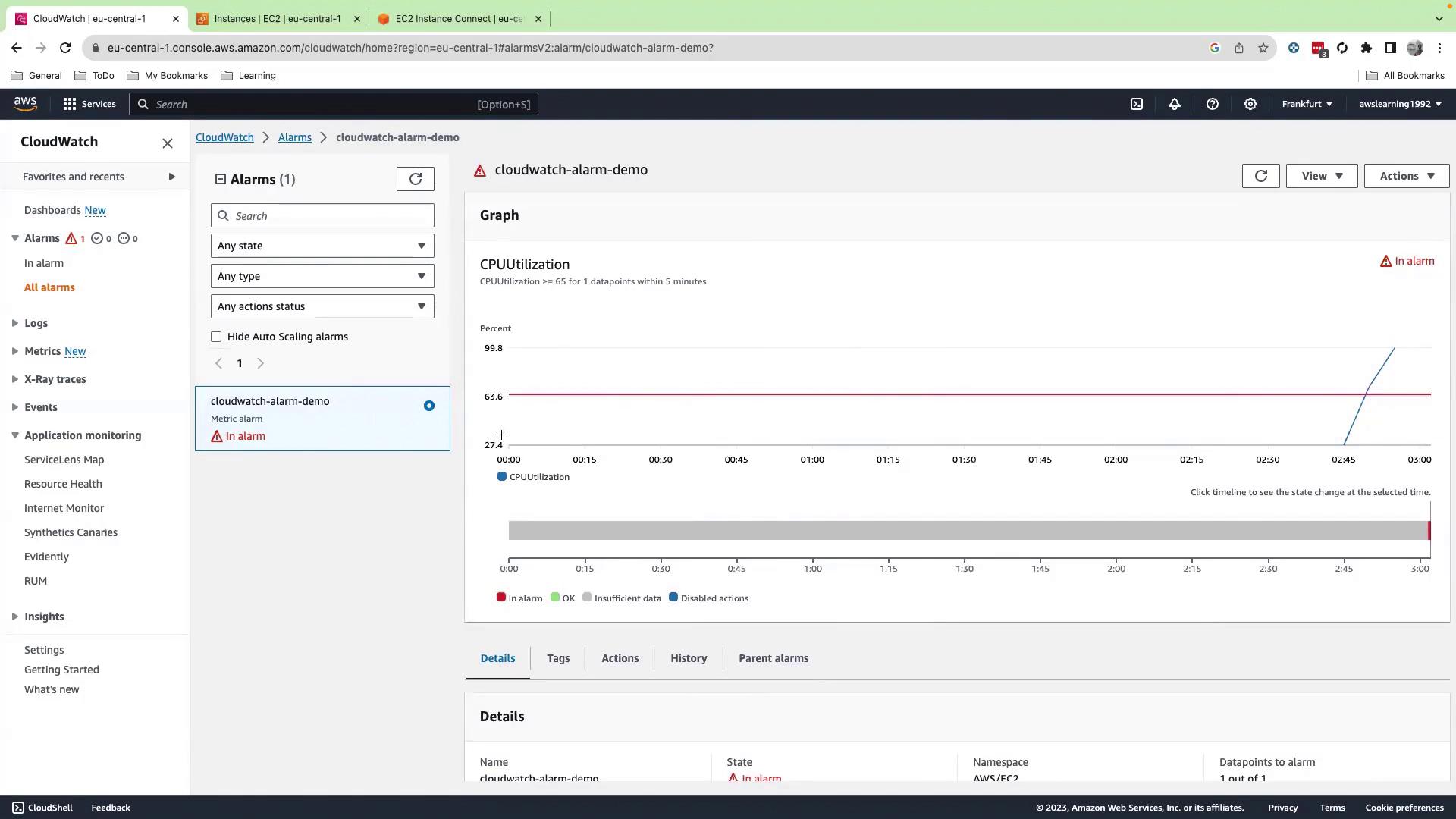
cpu-utilization-alarm) and an optional message. Preview the email content. - Click Next, then Create alarm. Initially, the alarm shows Insufficient data; once metrics arrive and CPU ≥ 65%, it shifts to In alarm.
7. Verify Notifications
Check your email inbox for an alert: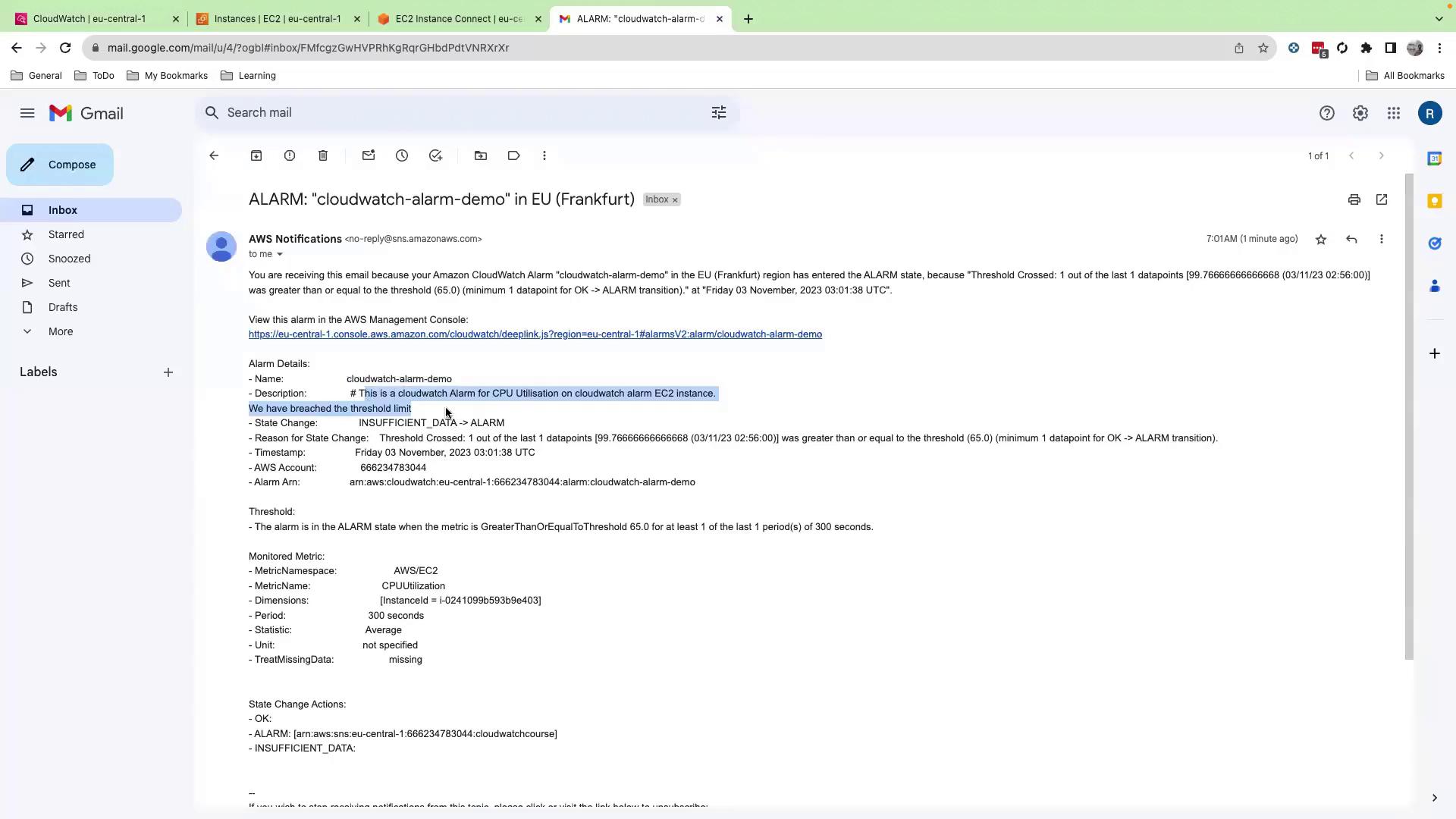
- Alarm name
- Instance details
- Custom message
- CloudWatch console link
- Triggering metric graph
8. Resolve the Alarm
- On the EC2 instance, stop
stresswithCtrl+C. - After CPU drops below 65%, the alarm transitions to OK.
Summary
You’ve successfully:- Launched and connected to an EC2 instance
- Installed and ran
stressto generate CPU load - Navigated CloudWatch and created a CPU utilization alarm
- Configured SNS notifications and verified delivery
- Resolved and monitored alarm recovery