- Identity and Access Management (IAM)
- Authentication and Authorization
- Encryption (Data at Rest & In Transit)
- Secrets Management
1. Identity and Access Management (IAM)
IAM ensures that only authorized principals can perform actions on your pipeline and its resources.1.1 Authentication
Use IAM users, groups, and roles to control who can access CodePipeline:- IAM Users & Groups
Provide long-term credentials for developers and administrators. - IAM Roles
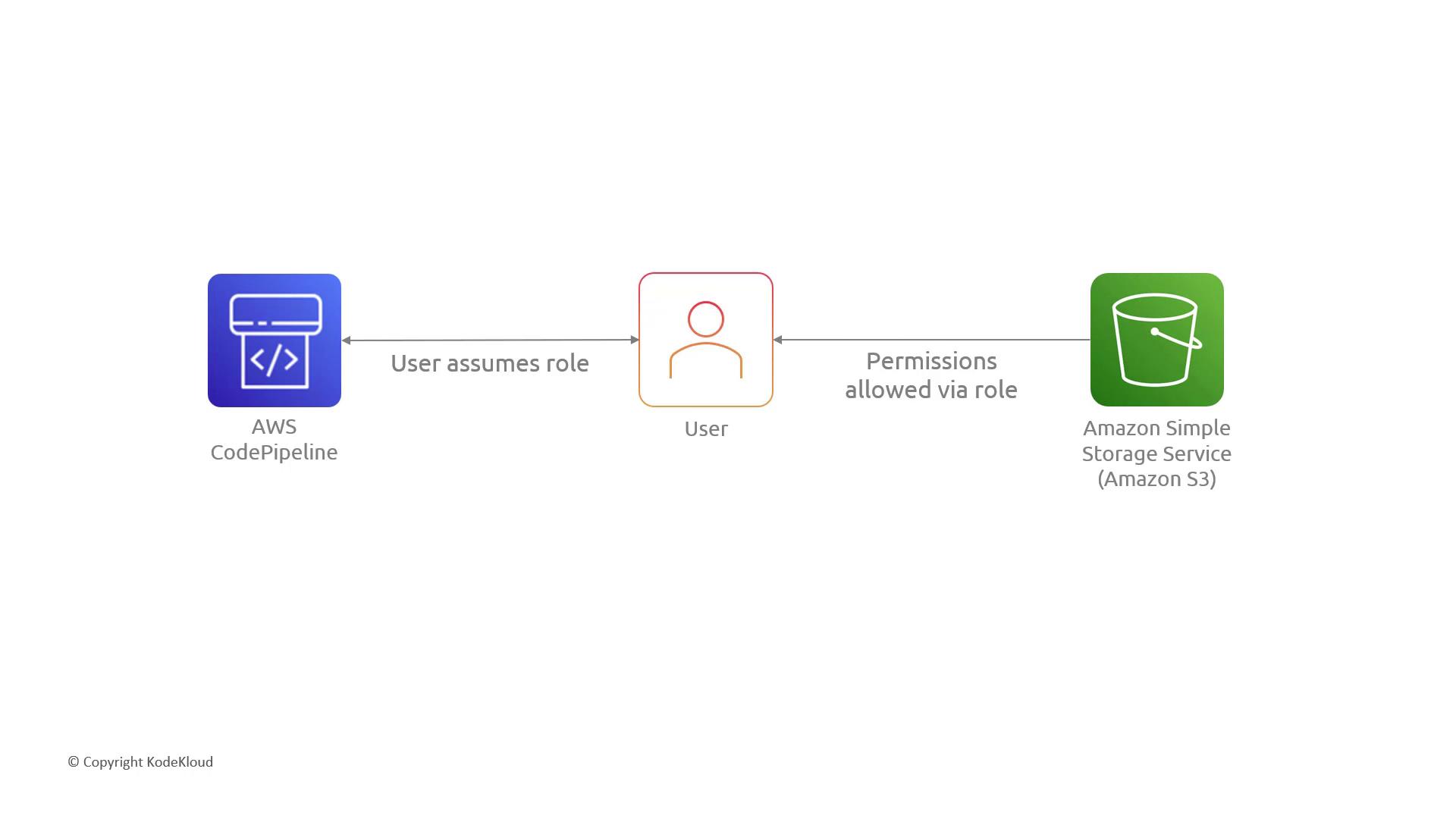
Grant temporary permissions when assumed by users, AWS services, or federated identities.
- Short-lived access across AWS accounts
- Federated users (e.g., SAML, OIDC)
- Applications running on EC2 (via instance profiles)

1.2 Authorization
Fine-grained permissions are enforced through IAM policies. These JSON documents define allowed or denied actions:| Policy Type | Attachment Target | Use Case |
|---|---|---|
| Identity-based policy | IAM Users, Groups, Roles | Grant or deny actions to principals |
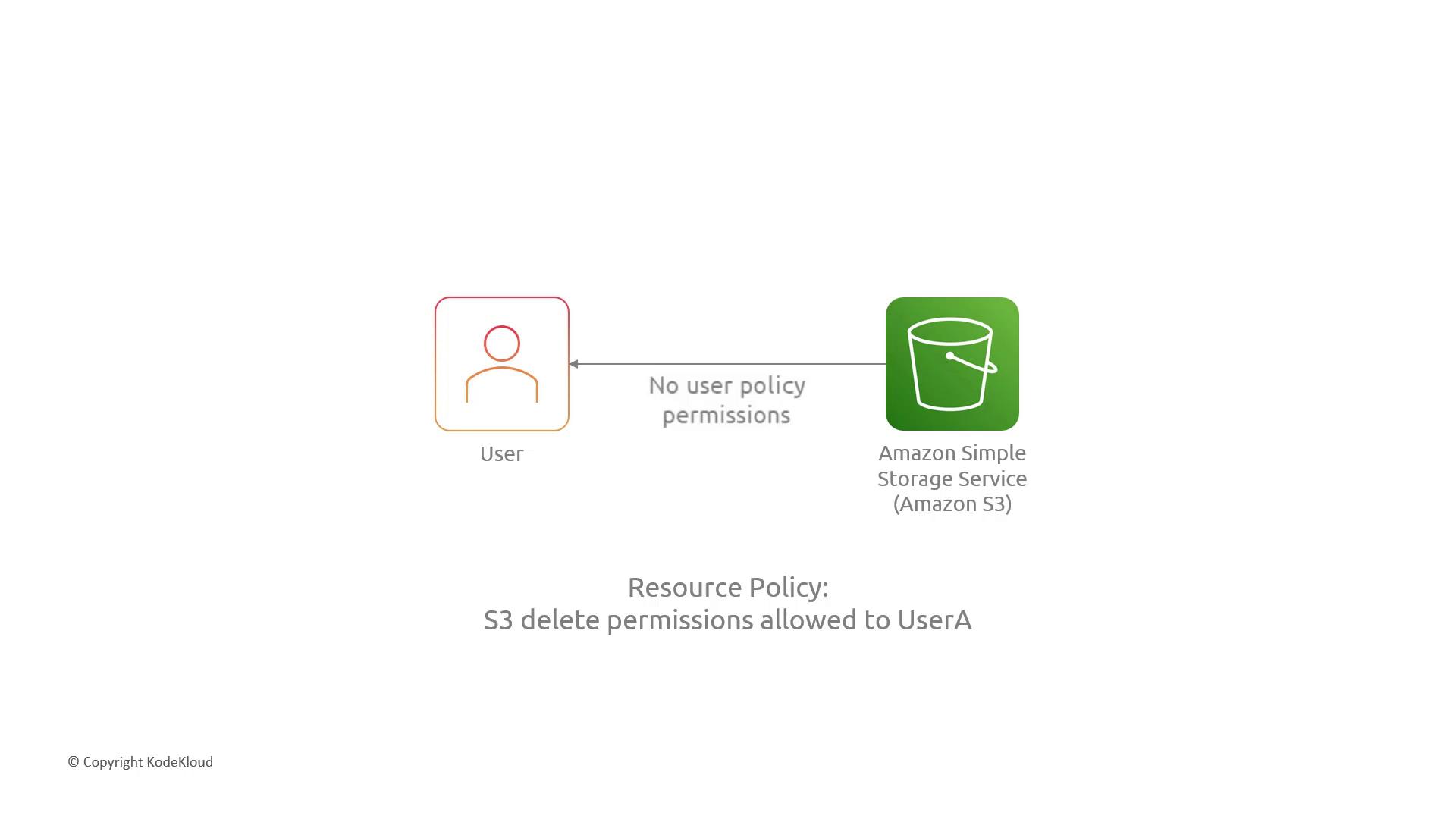
| Resource-based policy | S3 Buckets, KMS Keys | Control access at the resource level |
s3:DeleteObject, UserA can delete items:
2. Encryption
Protect data confidentiality by encrypting artifacts at rest and securing data in transit.2.1 Data at Rest
When storing build artifacts in S3, enforce server-side encryption (SSE). Compare your key management options:| Encryption Option | Key Management | Control Level |
|---|---|---|
| SSE-S3 (AWS-managed) | AWS-managed | No key rotation or policy control |
| SSE-KMS (AWS-managed) | AWS KMS | Automatic, limited policies |
| SSE-KMS (Customer-managed) | AWS KMS CMK | Full rotation & policy control |
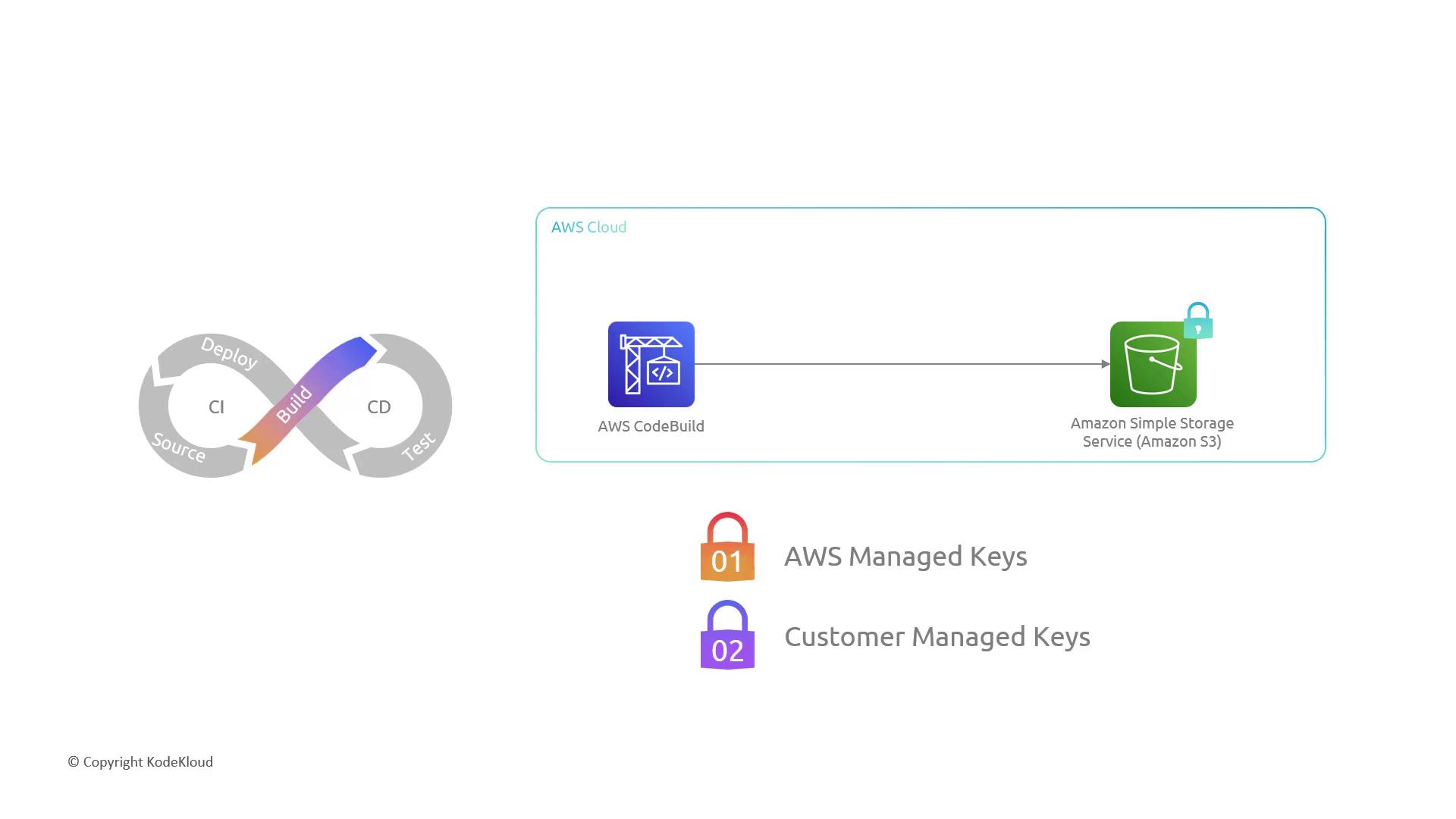
Always enforce HTTPS and server-side encryption in your S3 bucket policy to block unencrypted uploads or insecure connections.
2.2 Data in Transit
Always use TLS (HTTPS) for:- CodePipeline interactions with AWS services
- Integrations with third-party repositories (GitHub, Bitbucket)
- Calls to build and deployment providers
3. Secrets Management
Avoid hard-coding credentials such as API keys or passwords in your pipeline. Instead, centralize secrets in AWS Secrets Manager:
Use the AWS SDK or AWS CLI to fetch secrets at runtime:
Summary
We’ve covered the critical security controls for AWS CodePipeline:- IAM for robust authentication and authorization
- Encryption of artifacts at rest (SSE) and in transit (TLS)
- Secure secret handling with AWS Secrets Manager