AWS - IAM
Configure AWS IAM at Scale
Demo Cross Account Access
Enable a role in your source account (ID: 672261773768) to read objects from an S3 bucket in your target account (ID: …2021). This walkthrough covers:
- Configuring the bucket policy
- Creating and trusting an IAM role
- Testing access via AWS CloudShell
| Step | Description |
|---|---|
| 1 | Add a bucket policy in the target account |
| 2 | Create IAM policy & role with trust policy |
| 3 | Assume role and verify access in CloudShell |
1. Configure the Bucket Policy in the Target Account
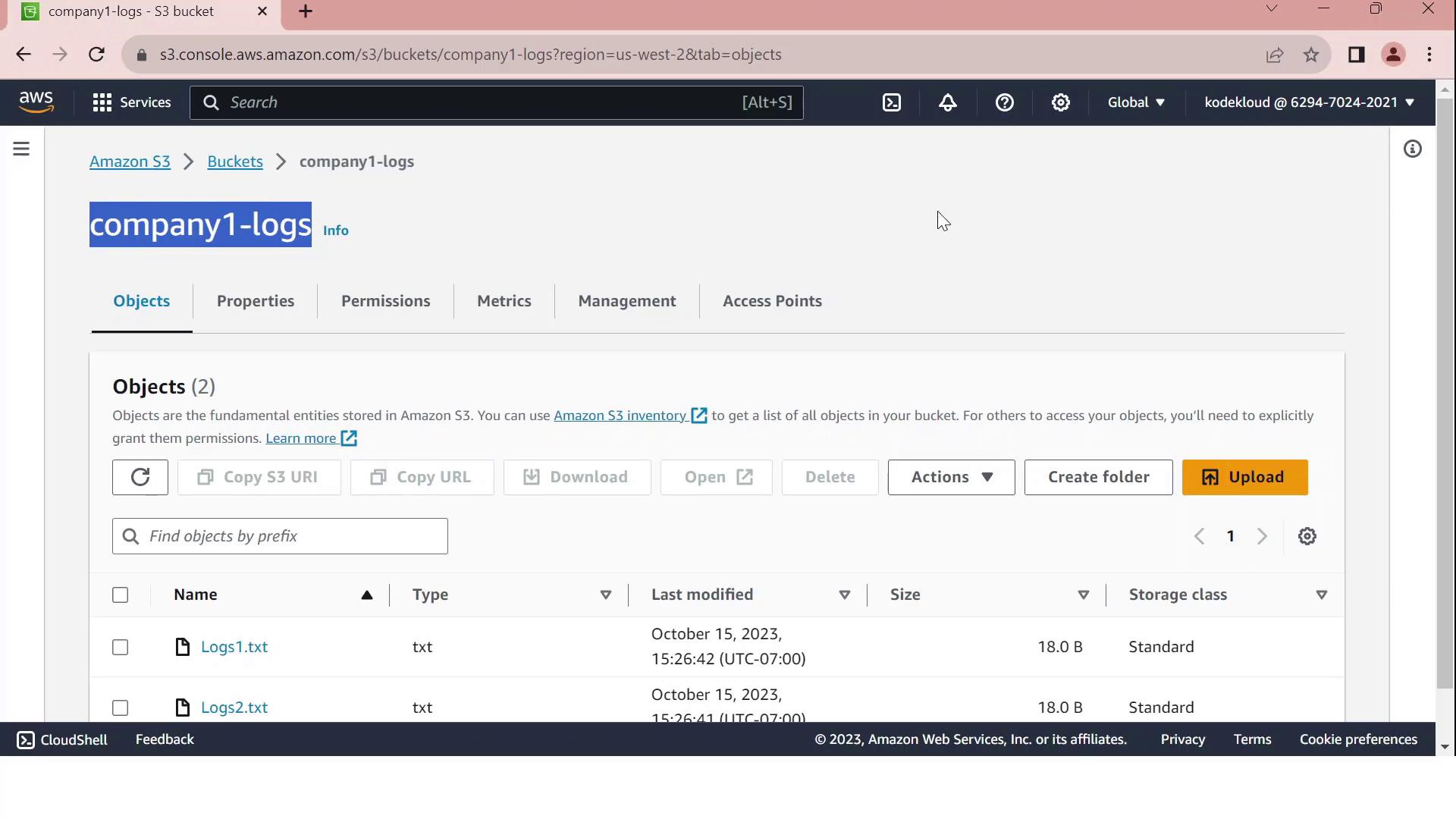
In the target account, go to S3 > company1-logs > Permissions > Bucket policy and paste:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::6294702402021:role/LogAnalystsRole"
},
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": [
"arn:aws:s3:::company1-logs",
"arn:aws:s3:::company1-logs/*"
]
}
]
}
Note
Ensure the bucket ARN and role ARN exactly match your resources. Typos in ARNs will prevent access.
2. Create the IAM Role in the Target Account
2.1 Define a Read-Only Policy
Create an IAM policy named company1-logs-read-policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": [
"arn:aws:s3:::company1-logs",
"arn:aws:s3:::company1-logs/*"
]
}
]
}
2.2 Create the Role and Configure Trust
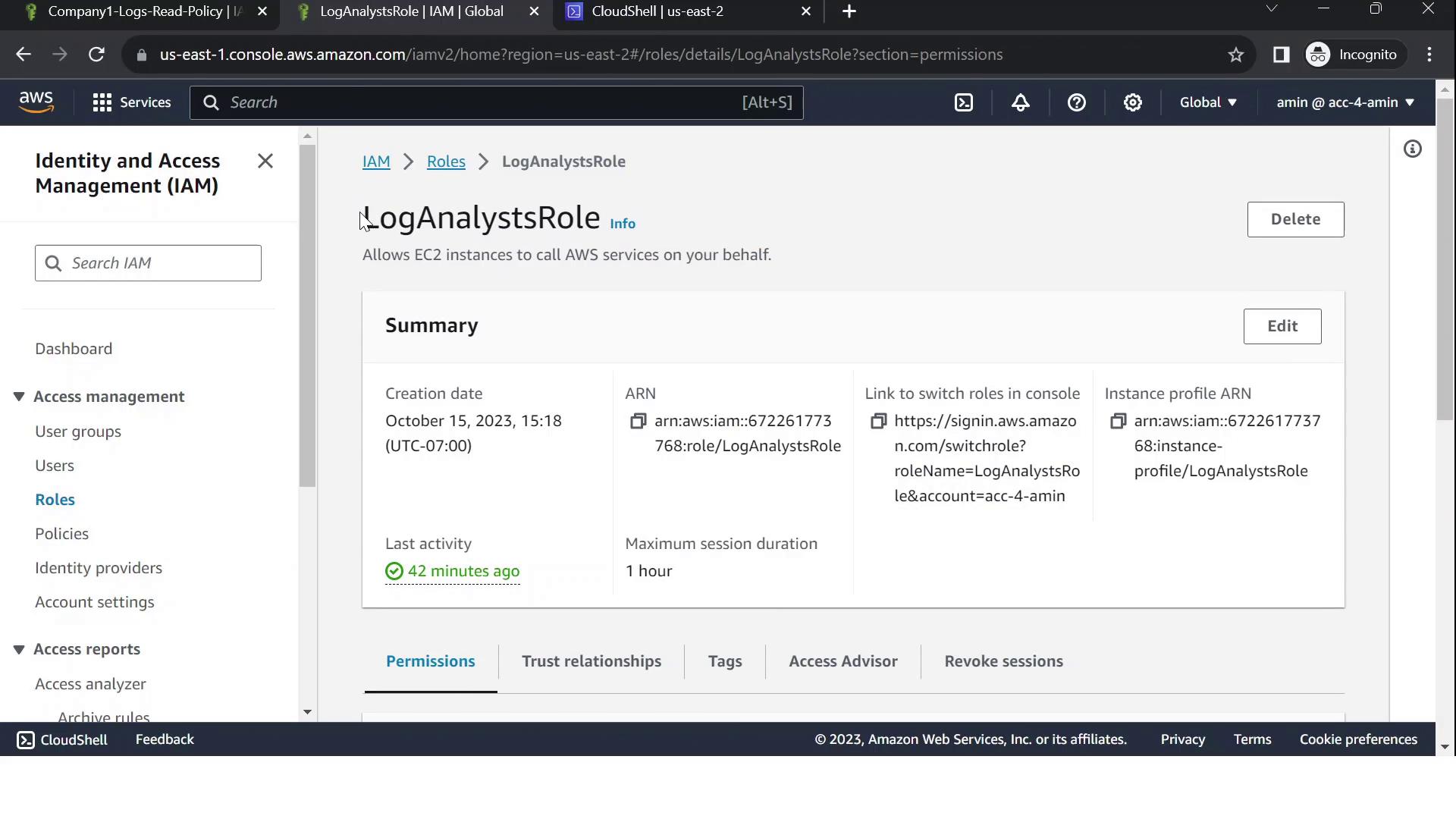
- In IAM, create a role called LogAnalystsRole.
- Attach company1-logs-read-policy.
- Edit Trust relationships to allow the source account user (
amin) to assume this role:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::672261773768:user/amin"
},
"Action": "sts:AssumeRole"
}
]
}
Warning
Grant only the minimum privileges needed. Review your trust policy to prevent unauthorized access.
3. Test Cross-Account Access via CloudShell
- Confirm your caller identity in the source account:
aws sts get-caller-identity - Assume the cross-account role:
aws sts assume-role \ --role-arn arn:aws:iam::6294702402021:role/LogAnalystsRole \ --role-session-name CrossAccountSession - Export the temporary credentials:
export AWS_DEFAULT_REGION=us-east-2 export AWS_ACCESS_KEY_ID=<YOUR_ACCESS_KEY_ID> export AWS_SECRET_ACCESS_KEY=<YOUR_SECRET_ACCESS_KEY> export AWS_SESSION_TOKEN=<YOUR_SESSION_TOKEN> - Verify you’re now the assumed role:
You should see an ARN withaws sts get-caller-identityassumed-role/LogAnalystsRole. - List bucket contents:
Expected output:aws s3 ls s3://company1-logs2023-01-01 12:00:00 18 Logs1.txt 2023-01-01 12:00:00 18 Logs2.txt
If you see the log files listed, your cross-account S3 access is working!
Links and References
Watch Video
Watch video content