AWS - IAM
IAM Policies Federation STS and MFA
Identity Federation
Identity federation enables users authenticated by an external Identity Provider (IdP) to access AWS resources without managing separate AWS credentials. By establishing a trust relationship between your IdP and AWS Security Token Service (STS), you can issue temporary, scoped credentials that improve security and simplify user management.
How Identity Federation Works
When you federate identities with AWS:
- A user signs in to your organizational IdP (e.g., Active Directory Federation Services, Okta).
- The IdP returns an authentication response (SAML assertion, OIDC token).
- Your application or client calls AWS STS to exchange the response for temporary credentials.
- AWS STS issues short-lived security credentials (access key ID, secret access key, session token).
- The user or application uses these credentials to call AWS APIs.
Note
Temporary credentials are valid for a limited duration (from 15 minutes up to 12 hours). Always request only the permissions required to follow the principle of least privilege.
AWS Federation Standards
AWS supports multiple federation protocols, enabling integration with on-premises directories, web identity providers, and custom IdPs.
| Protocol | Use Case | AWS Integration |
|---|---|---|
| SAML 2.0 | Enterprise federation (LDAP, Active Directory) | AssumeRoleWithSAML API |
| OpenID Connect | Modern web/mobile apps | AssumeRoleWithWebIdentity API |
| OAuth 2.0 | Granular authorization for APIs | Supported via OIDC/OAuth flows |
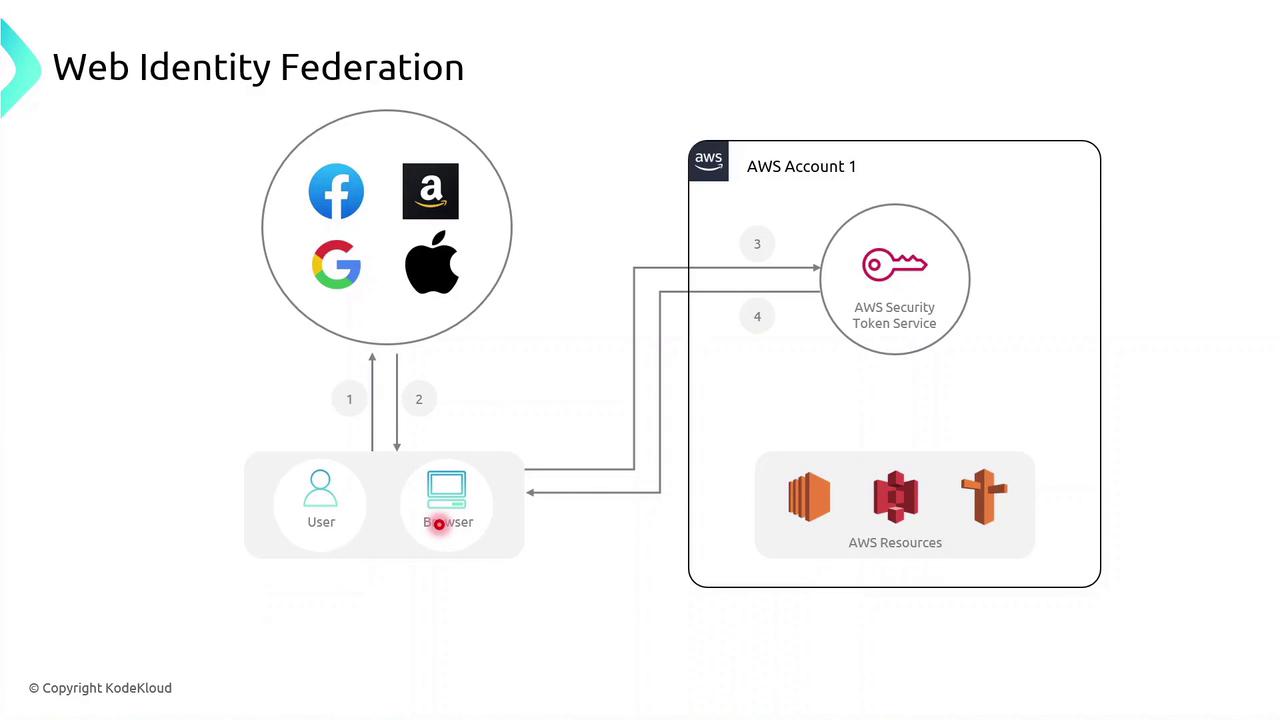
Web Identity Federation
Web and mobile applications can let users sign in with social or external IdPs (e.g., Facebook, Google, Amazon, Apple). The flow typically follows these steps:
- User selects a provider (e.g., Google) on your app’s login page.
- User authenticates and the provider returns an identity token (OIDC ID token).
- App calls
AssumeRoleWithWebIdentityon AWS STS, passing the token. - STS returns temporary AWS credentials.
- App uses these credentials to access AWS services on behalf of the user.
aws sts assume-role-with-web-identity \
--role-arn arn:aws:iam::123456789012:role/WebIdentityRole \
--role-session-name WebSession \
--web-identity-token file://token.jwt
Warning
Do not embed long-lived AWS keys in your mobile or browser-based applications. Always use temporary credentials obtained through web identity federation.
Benefits of AWS Identity Federation
- Simplified User Management
Leverage existing corporate or social identities—no separate AWS passwords. - Centralized Access Control
Define policies in IAM roles and manage permissions in one place. - Enhanced Security
Temporary, automatically rotated credentials reduce the risk of compromised keys.
Links and References
- AWS Security Token Service API Reference
- AWS IAM Identity Federation
- OpenID Connect on AWS
- SAML 2.0 Federation on AWS
Watch Video
Watch video content