AWS Networking Fundamentals
Transit Networks
Privatelink
In this article, we’ll cover what AWS PrivateLink is, why you need it, and how it works under the hood.
Challenges with Private Subnets
When an EC2 instance in a private subnet needs to access a public service like Amazon S3, the typical solution is to route traffic through an Internet Gateway or NAT Gateway. This approach:
- Exposes your instance to the public Internet and potential attacks
- Introduces additional infrastructure components and management overhead
- Incurs extra data processing costs on NAT devices
Warning
Using NAT gateways or Internet Gateways for service access can increase your AWS costs and expand your security attack surface.
What Is AWS PrivateLink?
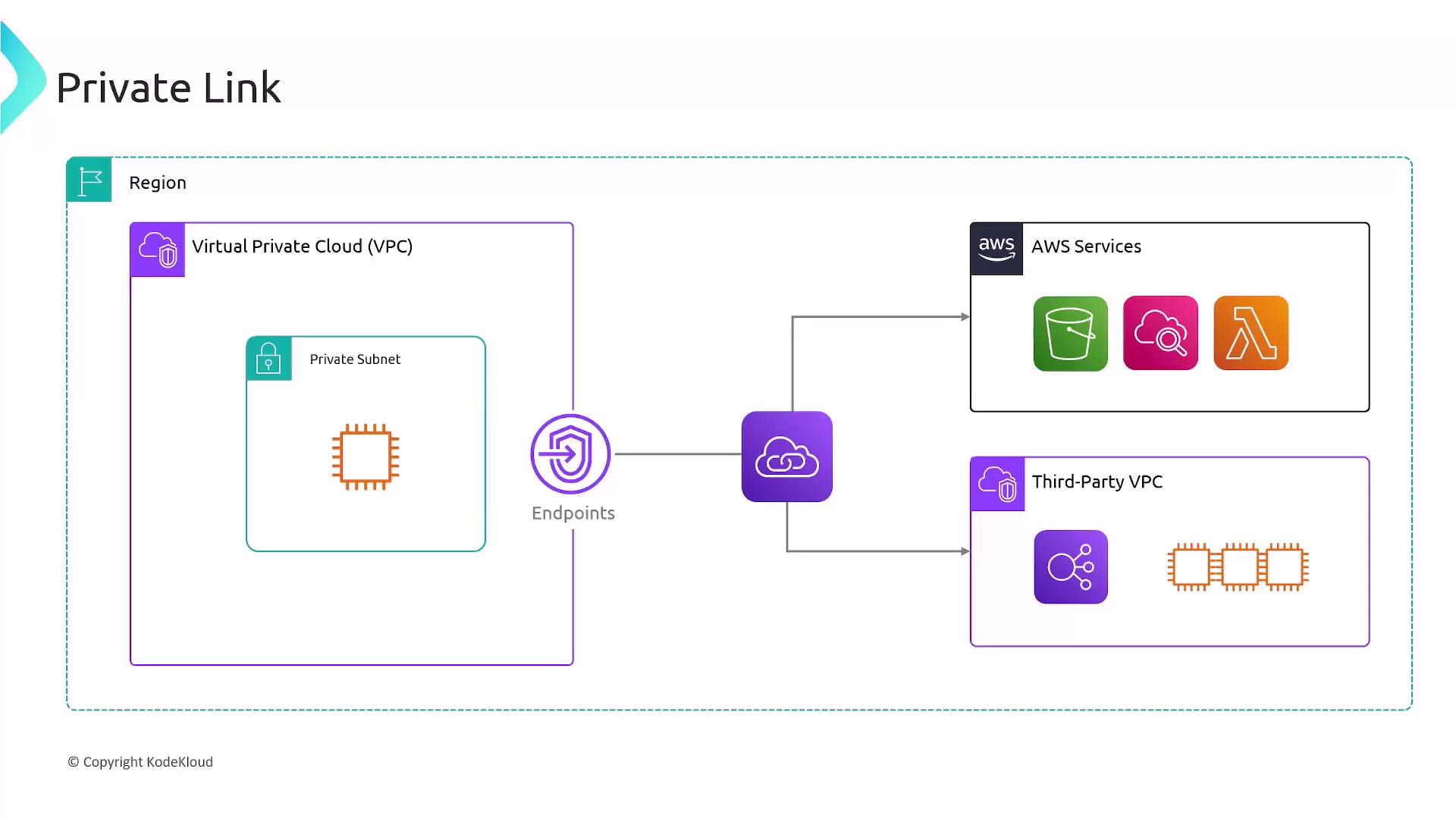
AWS PrivateLink provides private, highly available connectivity between your Virtual Private Cloud (VPC) and supported AWS services, other VPCs, or third-party services. All traffic stays within the AWS global network, never traversing the public Internet.
Key Benefits
| Benefit | Description |
|---|---|
| Security | Traffic remains on the AWS network, reducing exposure to Internet-based threats. |
| Simplicity | Eliminates the need for Internet Gateways, NAT gateways, or complex firewall configurations. |
| Scalability | Easily connect to supported AWS services (S3, Kinesis, EC2 API) or external VPC endpoint services. |
Note
AWS PrivateLink endpoints incur per-hour and per-GB data processing charges. Review the VPC pricing page for details.
How AWS PrivateLink Works
Service Owner
- Creates a VPC Endpoint Service and configures one or more Network Load Balancers.
- Shares the service with specific AWS accounts or makes it publicly available.
Service Consumer
- Creates an Interface VPC Endpoint in their VPC, selecting subnets and security groups.
- The endpoint provisions elastic network interfaces with private IPs in each subnet.
DNS Integration
- AWS automatically creates DNS records that map the service’s public hostname to the private IP addresses of your endpoint.
- Your application uses the same API endpoint (e.g.,
s3.amazonaws.com), but traffic routes securely via PrivateLink.
When to Use AWS PrivateLink
- Accessing AWS services (S3, EC2, Kinesis, Secrets Manager) from private subnets
- Connecting to partner or third-party services without exposing data to the Internet
- Establishing cross-account or cross-VPC communication with granular access control
Summary
AWS PrivateLink simplifies and secures your network architecture by enabling private connectivity to AWS and partner services. It eliminates the need for Internet Gateways or NAT devices, keeps traffic within AWS’s backbone, and scales seamlessly to meet your application demands.
Links and References
- AWS PrivateLink Overview
- Interface Endpoints for Amazon S3
- VPC Endpoint Pricing
- AWS Network Security Best Practices
Watch Video
Watch video content