AWS Networking Fundamentals
Transit Networks
VPC Peering Demo
In this tutorial, you’ll learn how to establish a VPC peering connection between two AWS VPCs so that their EC2 instances can communicate over the private AWS network:
| VPC Identifier | CIDR Block | EC2 Instance | Private IP |
|---|---|---|---|
| VPC-A | 10.1.0.0/16 | server1 | 10.1.1.13 |
| VPC-B | 10.2.0.0/16 | server2 | 10.2.1.139 |
Prerequisites
Make sure both VPCs have security groups and network ACLs allowing ICMP traffic. You also need IAM permissions to manage VPC peering and route tables.
Since VPCs are isolated by default, pinging from server1 to server2 will initially fail:
[ec2-user@ip-10-1-1-13 ~]$ ping 10.2.1.139
PING 10.2.1.139 (10.2.1.139) 56(84) bytes of data.
^C
--- 10.2.1.139 ping statistics ---
195 packets transmitted, 0 received, 100% packet loss
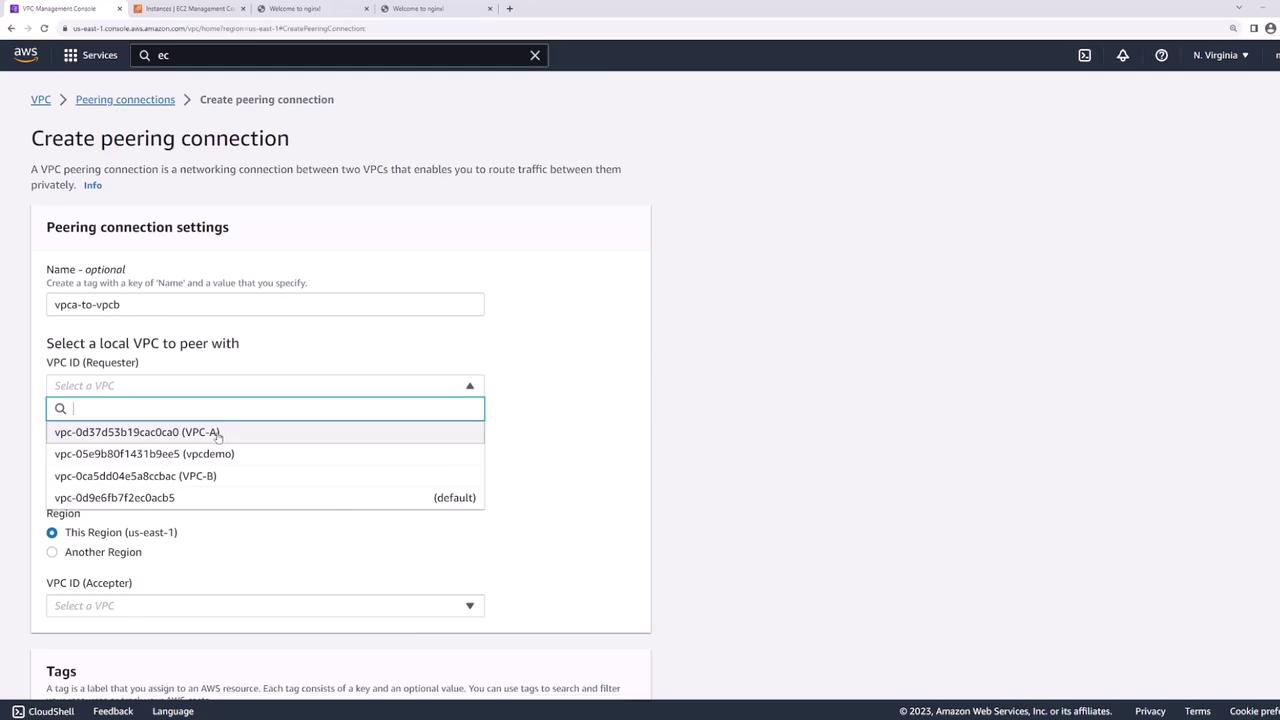
1. Create the VPC Peering Connection
- Open the AWS VPC console and select Peering Connections → Create Peering Connection.
- Name the connection
VPC-A-to-VPC-B. - Under Requester, choose VPC-A.
- Under Accepter, select your account and region, then choose VPC-B.
- Click Create Peering Connection.
Automation Tip
You can also provision VPC peering using Infrastructure as Code tools like Terraform or AWS CloudFormation.
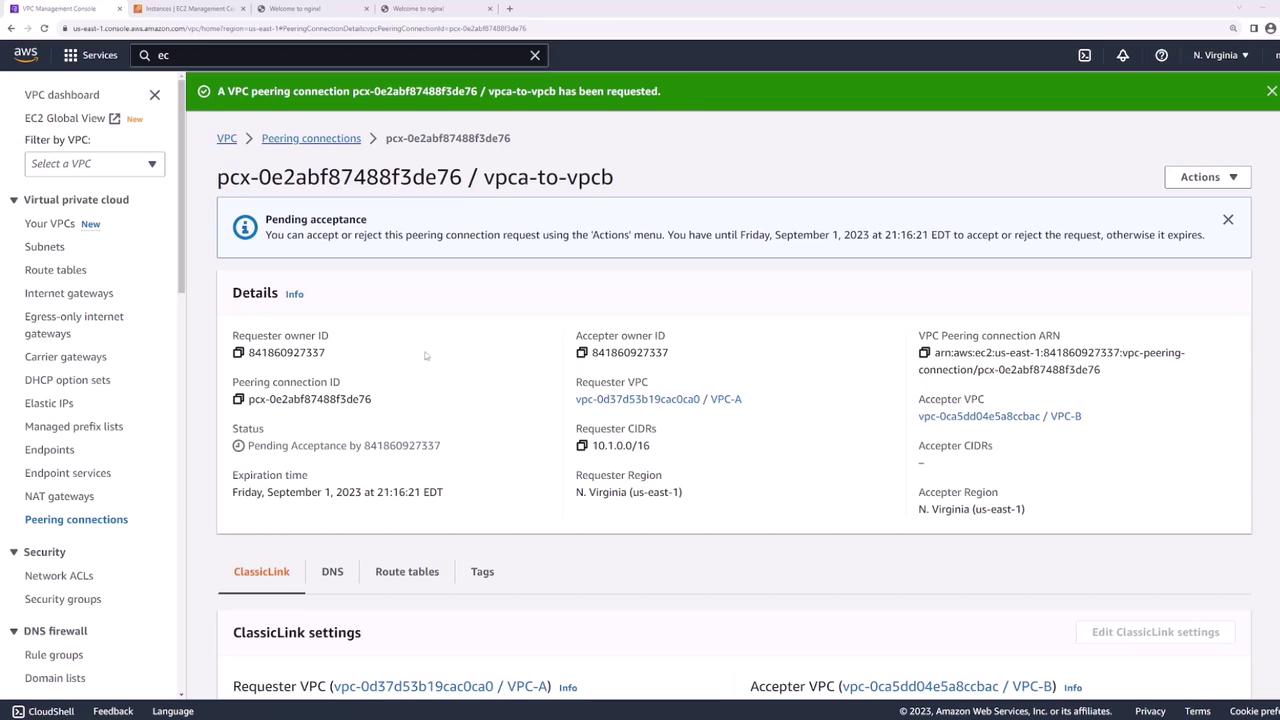
2. Accept the Peering Request
- In Peering Connections, locate the new connection in Pending Acceptance.
- Select it, then choose Actions → Accept Request.
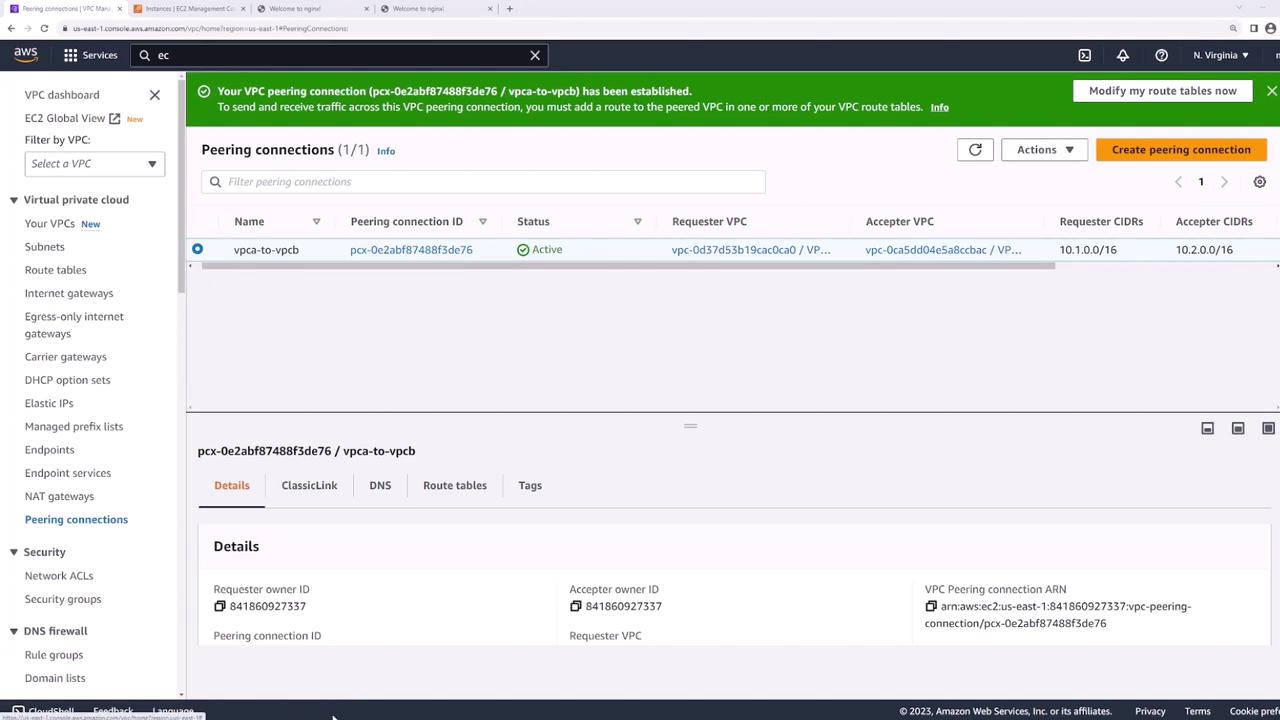
Once accepted, its status changes to Active:
Important
Even after peering is active, traffic won’t flow until you update each VPC’s route tables.
3. Update Route Tables
Each VPC needs a route pointing to the other VPC’s CIDR block through the peering connection:
- In the VPC console, go to Route Tables.
- Select the route table for VPC-A.
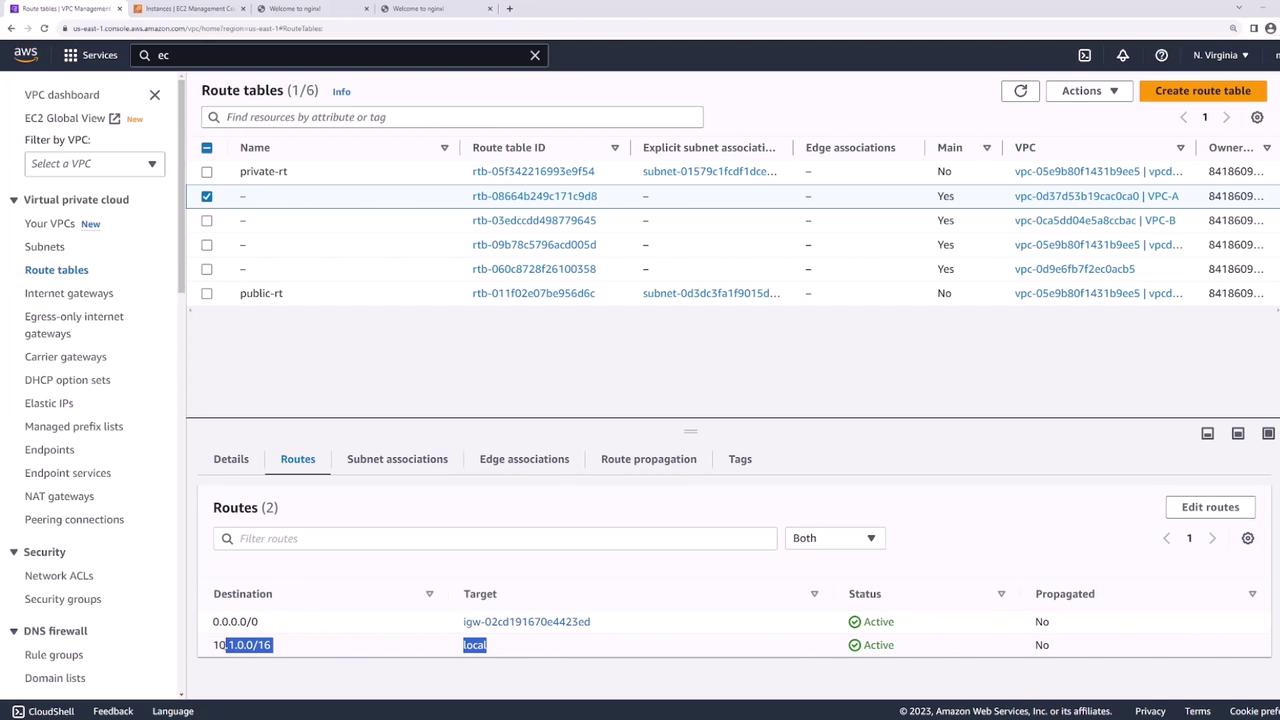
- Under Routes, click Edit routes → Add route:
- Destination:
10.2.0.0/16 - Target: the peering connection (
VPC-A-to-VPC-B)
- Destination:
- Save changes.
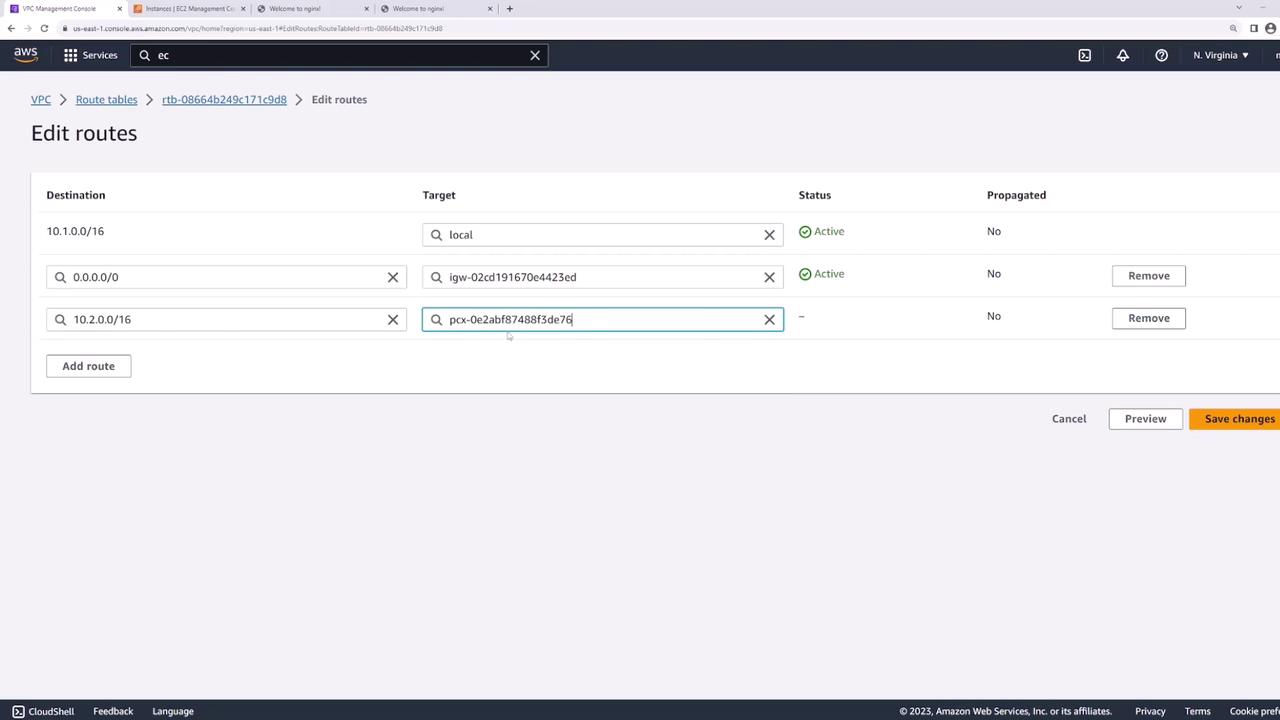
- Repeat these steps on VPC-B’s route table, adding a route to
10.1.0.0/16via the same peering connection.
4. Verify Connectivity
Return to server1 and ping server2:
[ec2-user@ip-10-1-1-13 ~]$ ping 10.2.1.139
PING 10.2.1.139 (10.2.1.139) 56(84) bytes of data.
64 bytes from 10.2.1.139: icmp_seq=1 ttl=127 time=1.88 ms
64 bytes from 10.2.1.139: icmp_seq=2 ttl=127 time=1.43 ms
64 bytes from 10.2.1.139: icmp_seq=3 ttl=127 time=1.38 ms
^C
--- 10.2.1.139 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 1.382/1.563/1.882/0.187 ms
Your EC2 instances can now communicate across VPCs using the private AWS backbone.
Links and References
Watch Video
Watch video content
Practice Lab
Practice lab