AZ-204: Developing Solutions for Microsoft Azure
Exploring Azure Blob Storage
Azure Storage Security Features
Azure Storage provides a comprehensive suite of security features that safeguard your data both at rest and in transit. This guide delves into essential mechanisms such as Microsoft Entra ID integration, role-based access control (RBAC), data in transit encryption, Shared Access Signatures (SAS), and encryption at rest using both Microsoft-managed and customer-managed keys.
Microsoft Entra ID Integration and Role-Based Access Control
Azure Storage integrates seamlessly with Microsoft Entra ID (formerly known as Azure Active Directory) to offer a robust role-based access control (RBAC) system. With RBAC, you can allocate specific roles to users, groups, or service principals, ensuring that each entity receives the exact permissions needed for its tasks—be it reading, writing, or managing storage resources. This granular control adheres to the principle of least privilege, enhancing your security posture.
For example, if your application needs to write logs to Azure Blob Storage, you can grant it write permissions without giving it full control over the entire storage account.
Data in Transit Encryption
Azure Storage automatically encrypts data as it moves between your application and the Azure cloud. This encryption is critical, as data traveling over networks can be vulnerable to interception. Azure leverages HTTPS and TLS protocols to secure these communications, ensuring that data is both encrypted and decrypted transparently during upload or download operations.
Note
When data is uploaded or downloaded from Blob Storage, Azure takes care of encrypting and decrypting the data automatically, ensuring that the transfer remains secure and uninterrupted.
Shared Access Signatures (SAS)
Shared Access Signatures (SAS) provide a method to delegate access to your Azure Storage resources without revealing your storage account keys. SAS tokens allow you to grant temporary and limited access to specific parts of your storage, such as permitting a third party to access certain files within Blob Storage. These tokens can be finely tuned with expiration dates, permission levels, and IP address restrictions for enhanced security.
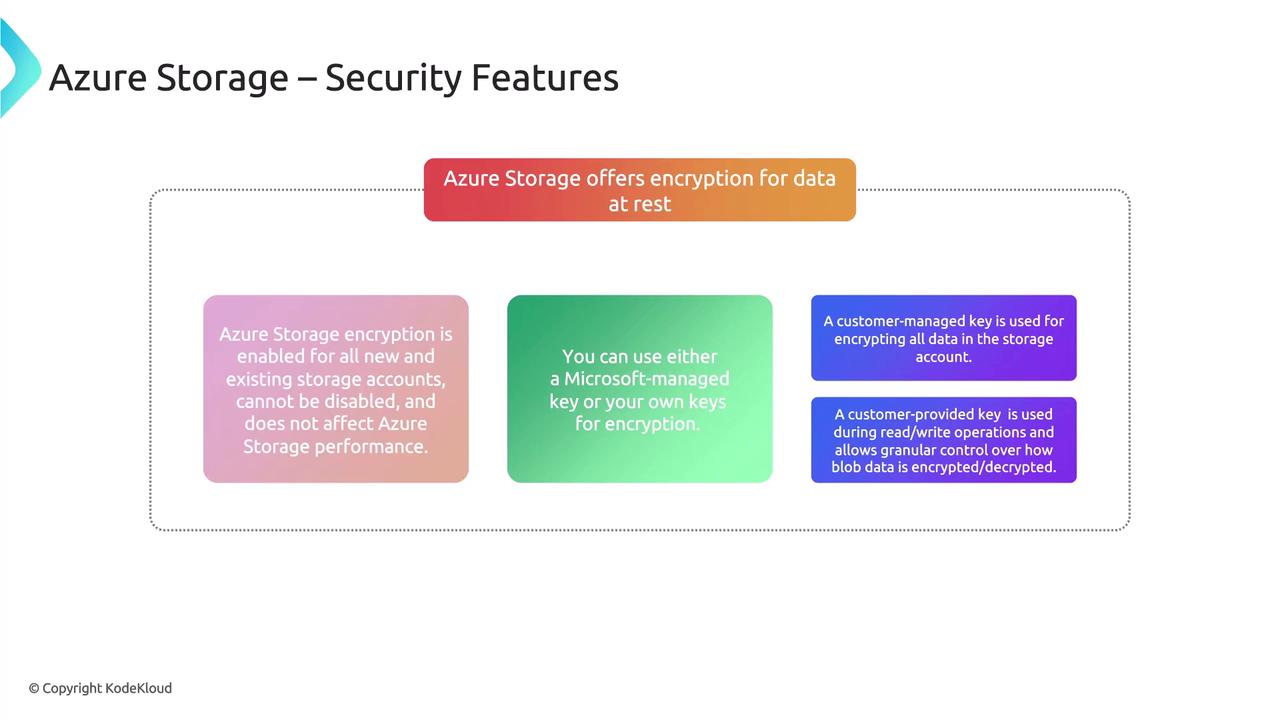
Encryption at Rest
Azure Storage ensures that your data remains secure even when not in active use through automatic encryption at rest. This protection applies to Blob, file, and disk storage, ensuring that your information stays encrypted even if unauthorized physical access occurs at the data center. The encryption process is designed to maintain performance and is enabled by default across both new and existing storage accounts.
For managing encryption at rest, you have two options:
- Microsoft-managed keys: Microsoft takes charge of encryption and key rotation, offering a simple yet robust solution without additional configuration.
- Customer-managed keys (CMK): This option gives you full control over your encryption keys, allowing you to manage key rotation and lifecycle management according to your specific security requirements.
In addition, Azure supports the use of customer-provided keys (CPK) during read or write operations. This feature provides granular control over the encryption and decryption of your blob data, which is particularly useful for scenarios involving highly sensitive information, such as financial records.
Warning
Ensure that your encryption keys and SAS tokens are managed with care, as mismanagement could lead to unauthorized access to your storage data.
Transition to Azure Blob Storage
With these robust security features in place, Azure Storage offers a secure environment for your data. The forthcoming section will shift focus to Azure Blob Storage, exploring its functionalities and best practices for secure data handling.
For more details on securing your cloud storage environment, refer to Azure Security Documentation.
Watch Video
Watch video content