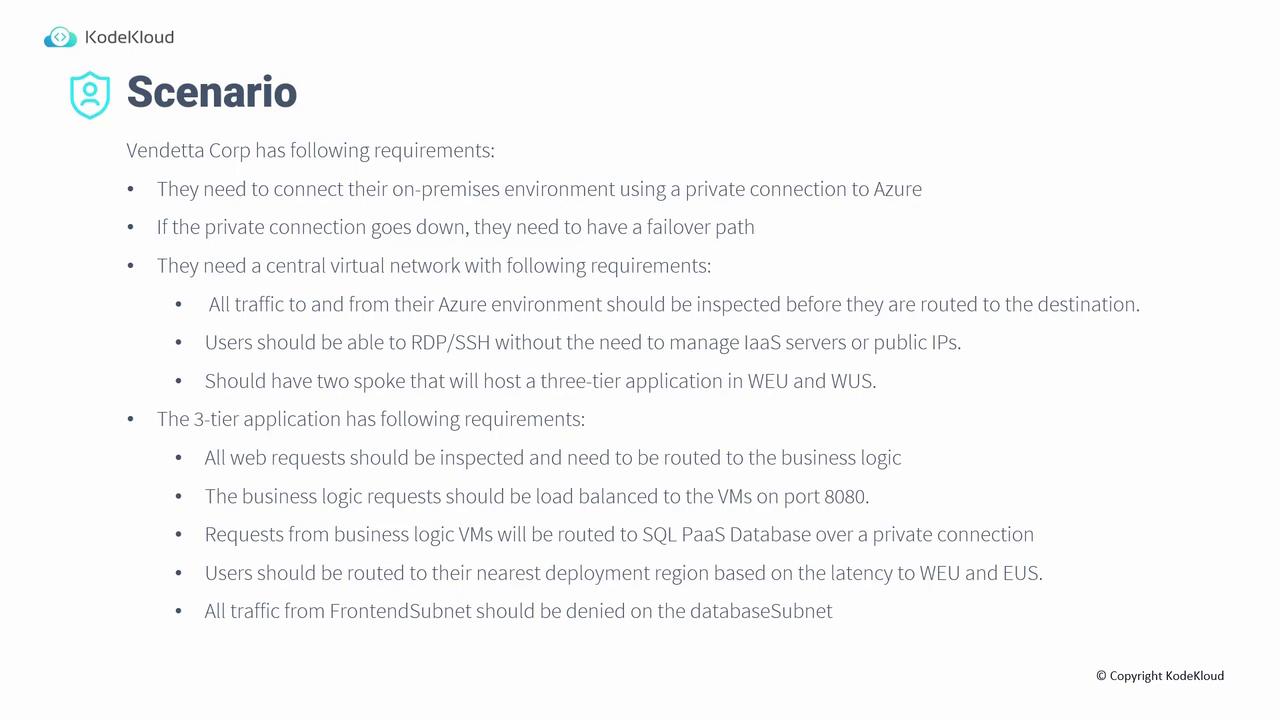
Venator Corp Requirements
Venator Corp has set the following requirements for its network infrastructure:- Establish a private connection between the on-premises environment and Azure.
- Include a failover path in case the private connection experiences downtime.
The diagram above illustrates the network requirements for Venator Corp. It details how private connections, failover strategies, and centralized virtual networks come together to support mission-critical applications.
- All traffic entering or leaving Azure must be inspected before reaching its destination.
- Users should securely connect via RDP or SSH without the need to manage IaaS servers or rely on public IP addresses.
- The architecture should incorporate two spoke networks designed to host a three-tier application, with deployments in West US and West Europe.
Three-Tier Application Requirements
The three-tier application within this network infrastructure must meet these specific requirements:- Web Request Inspection: All incoming web requests should be inspected prior to reaching the business logic tier.
- Load Balancing: Requests directed to the business logic tier must be load balanced across virtual machines on port 8080.
- Private Database Communication: The communication between the business logic tier and the SQL PaaS database should occur exclusively over a private connection.
- Latency-Based Routing: Users should be routed to their nearest region based on latency, with the choice between West Europe and East US.
- Subnet Isolation: Traffic from front-end subnets must not have access to the database subnets.