AZ-305: Microsoft Azure Solutions Architect Expert
Design a nonrelational data storage solution
Design for Azure Blob Storage
In this lesson, we explore advanced design aspects of Azure Blob Storage. Building on the fundamentals discussed in the AZ-104: Microsoft Azure Administrator course, this article delves deeper into choosing the appropriate access tier and setting up immutable storage. Before proceeding, ensure you are familiar with the basics of blob storage, including file uploads, access tiers, and lifecycle management policies.
Choosing the Storage Access Tier
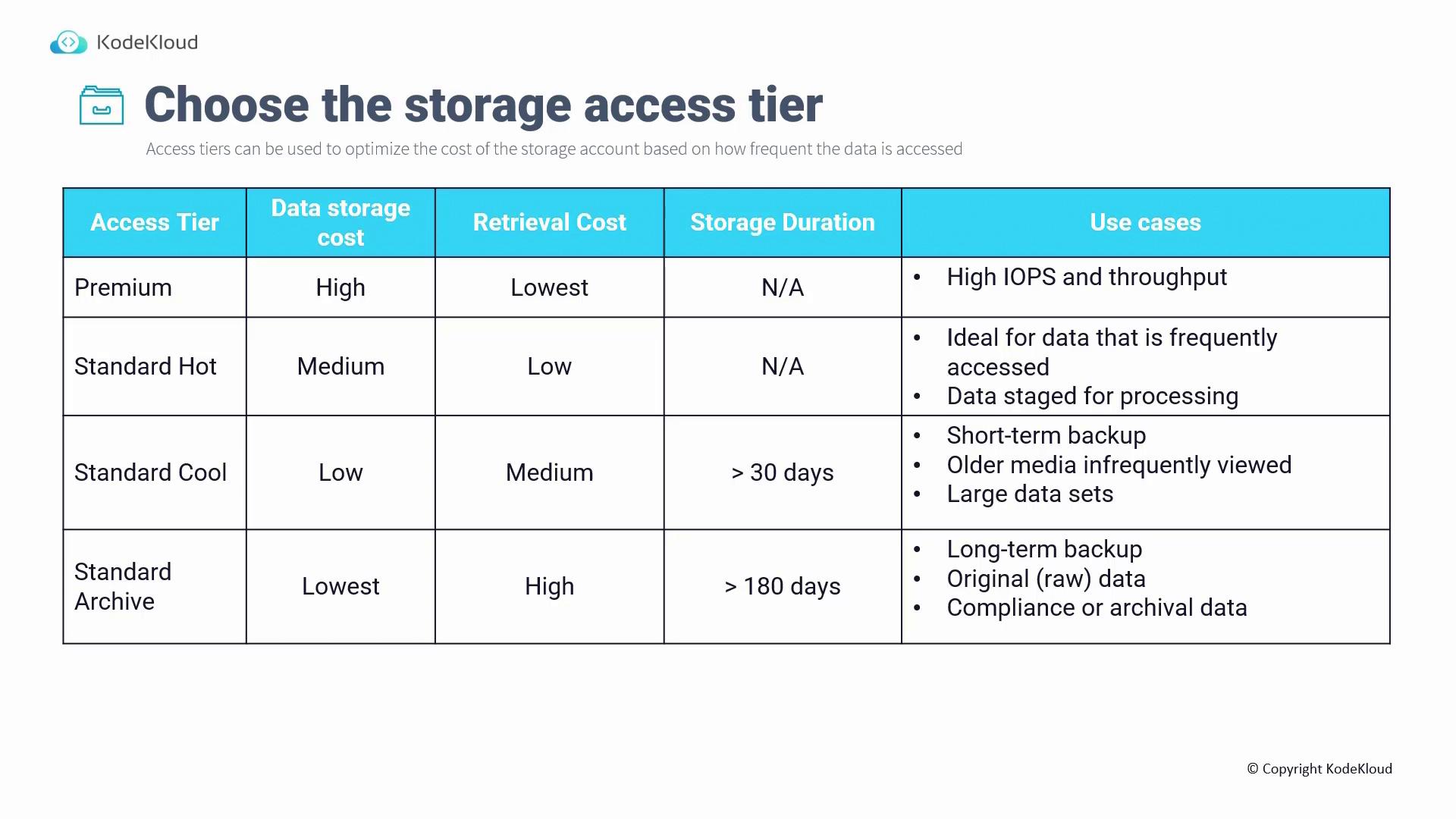
Access tiers are crucial for optimizing storage costs based on data access frequency. Azure provides several tiers for standard storage accounts: hot, cool, and archive. In addition, a premium tier that uses SSDs is available for high-performance needs.
Premium Tier
- Designed for scenarios that demand high IOPS and throughput.
- Features higher data storage costs but minimal retrieval costs.
- Not applicable for hot, cool, or archive concepts since data is accessed frequently.
Standard Hot Tier
- Best suited for frequently accessed data such as web assets (e.g., images, banners).
- Offers medium storage costs compared to premium, yet higher than cool or archive.
- Boasts very low retrieval costs, ideal for continuous data reading.
- Works well for data staging in processing scenarios.
Note: By default, a storage account is created with the hot tier. However, you can later change the access tier for the entire storage account or individual blobs.
Standard Cool Tier
- Ideal for data that is accessed less frequently, such as short-term backups.
- Provides lower storage costs compared to the hot tier but comes with medium retrieval costs.
- Enforces a minimum storage duration of 30 days.
Archive Tier
- Recommended for long-term archival and compliance needs (e.g., retention for 10 or 15 years).
- Offers the lowest storage cost, but retrieval is expensive.
- Microsoft advises a retention period of more than 180 days.
The table below summarizes the differences among these access tiers:
Important Information
- At the storage account level, you can only set the hot or cool tier.
- The archive tier is configurable at the blob level.
Additionally, you can automate tier transitions using lifecycle management policies based on the last modified date, including optional blob deletion after a specified period.
Requirements for Azure Blob Immutable Storage
Immutable storage is essential for scenarios where compliance or business-critical data must adhere to a Write Once, Read Many (WORM) model. For example, regulations might require data retention for five years under strict policies. Once data is written, immutable storage ensures that it cannot be modified or deleted until the retention period expires. This is achieved by enforcing container-level policies that cover all blobs within the container.
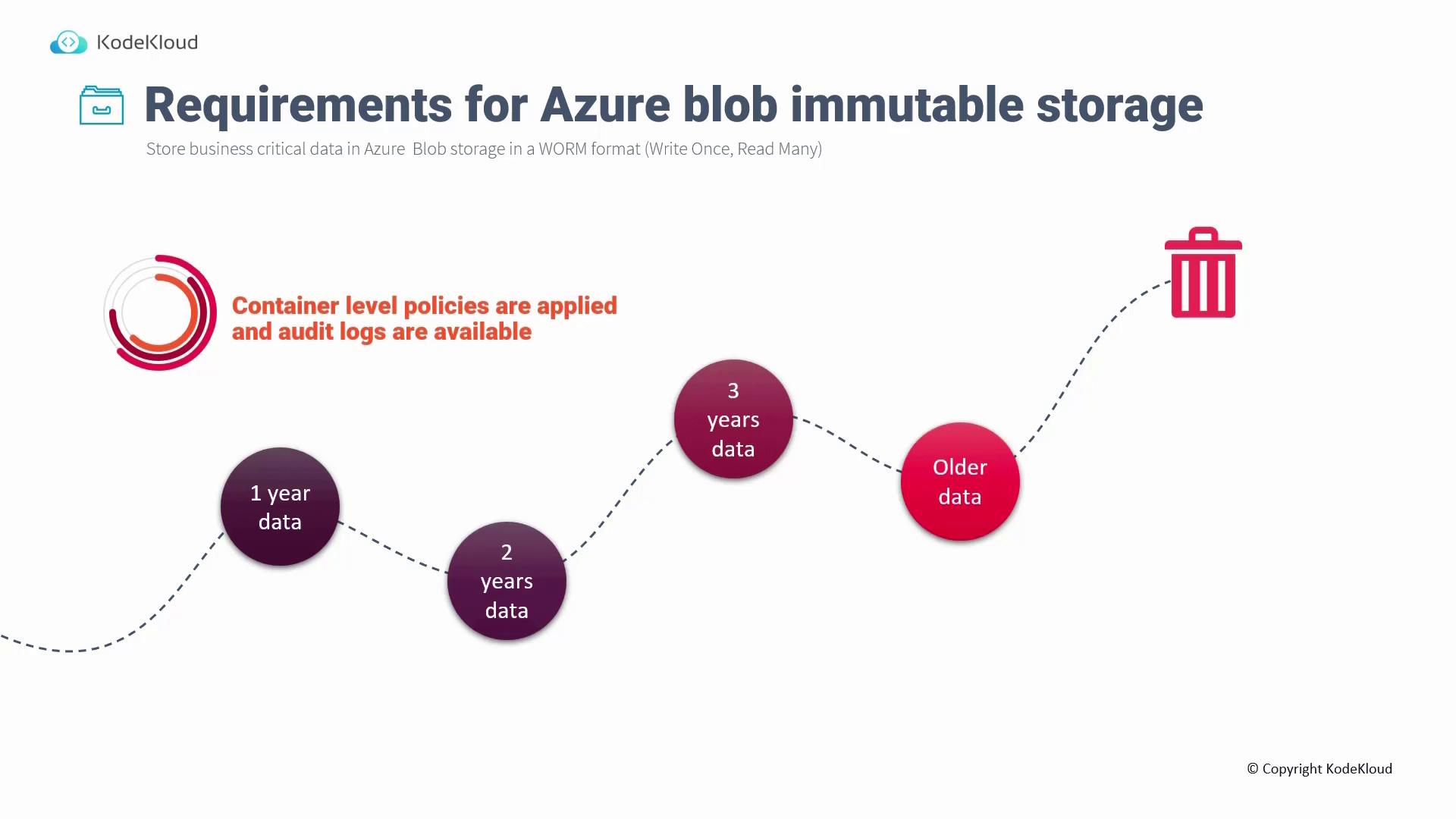
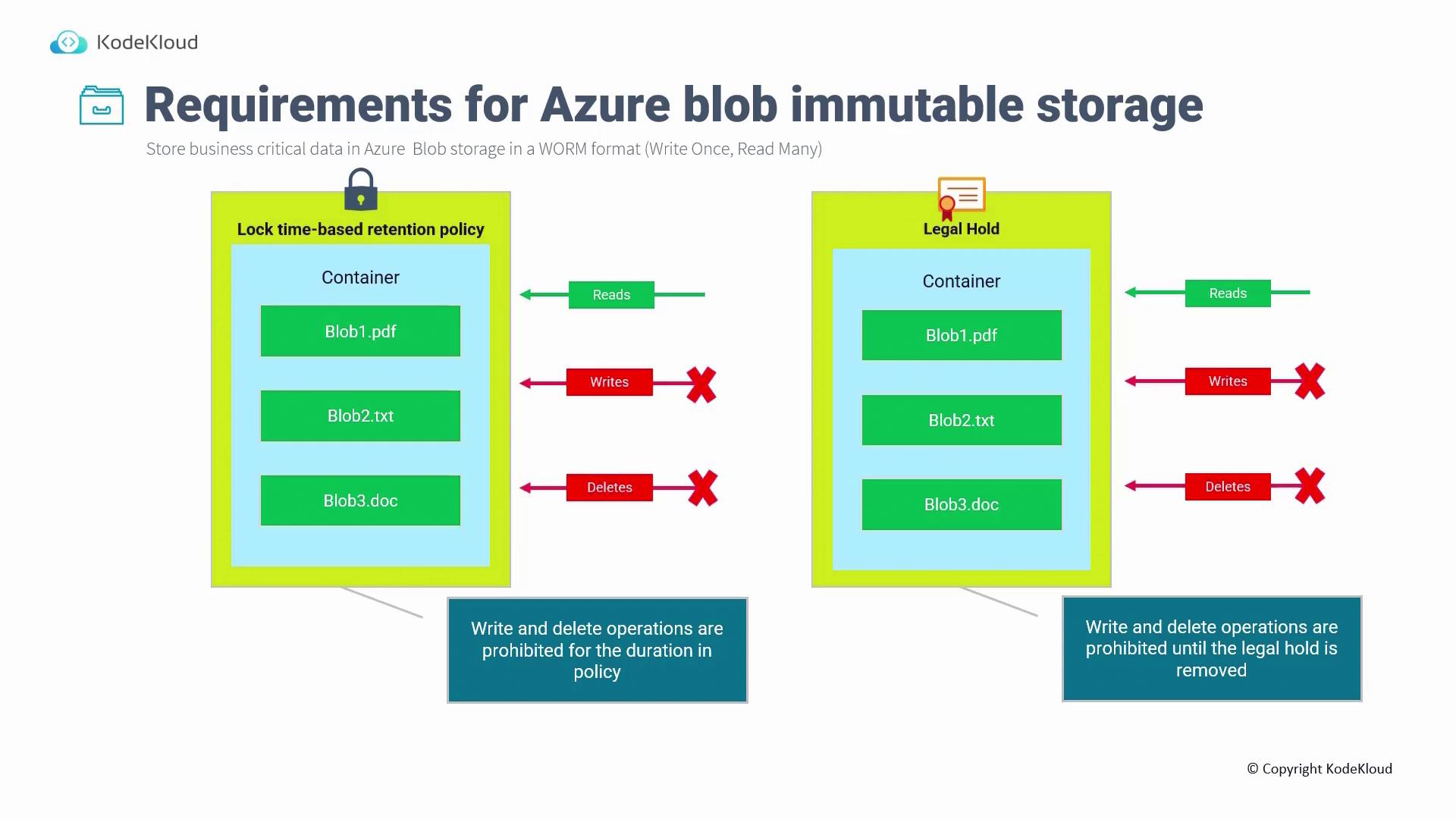
Two types of immutability policies can be applied:
Time-Based Retention Policy:
Enforces a prohibition on write and delete operations for a specified duration (e.g., 365 days), ensuring data remains unchanged throughout this period.Legal Hold:
Blocks write and delete operations indefinitely until the legal hold is manually lifted.
In both cases, read operations remain permitted. The diagram below illustrates that while reads are allowed, writes and deletes are blocked under these policies:
Setting Up Immutable Storage in the Azure Portal
Follow the steps below to configure immutable storage policies directly through the Azure portal:
Creating a Storage Account:
Begin by navigating to the Storage Accounts section and create a new storage account. Provide a unique name, select the standard performance tier, and choose Locally-redundant Storage (LRS).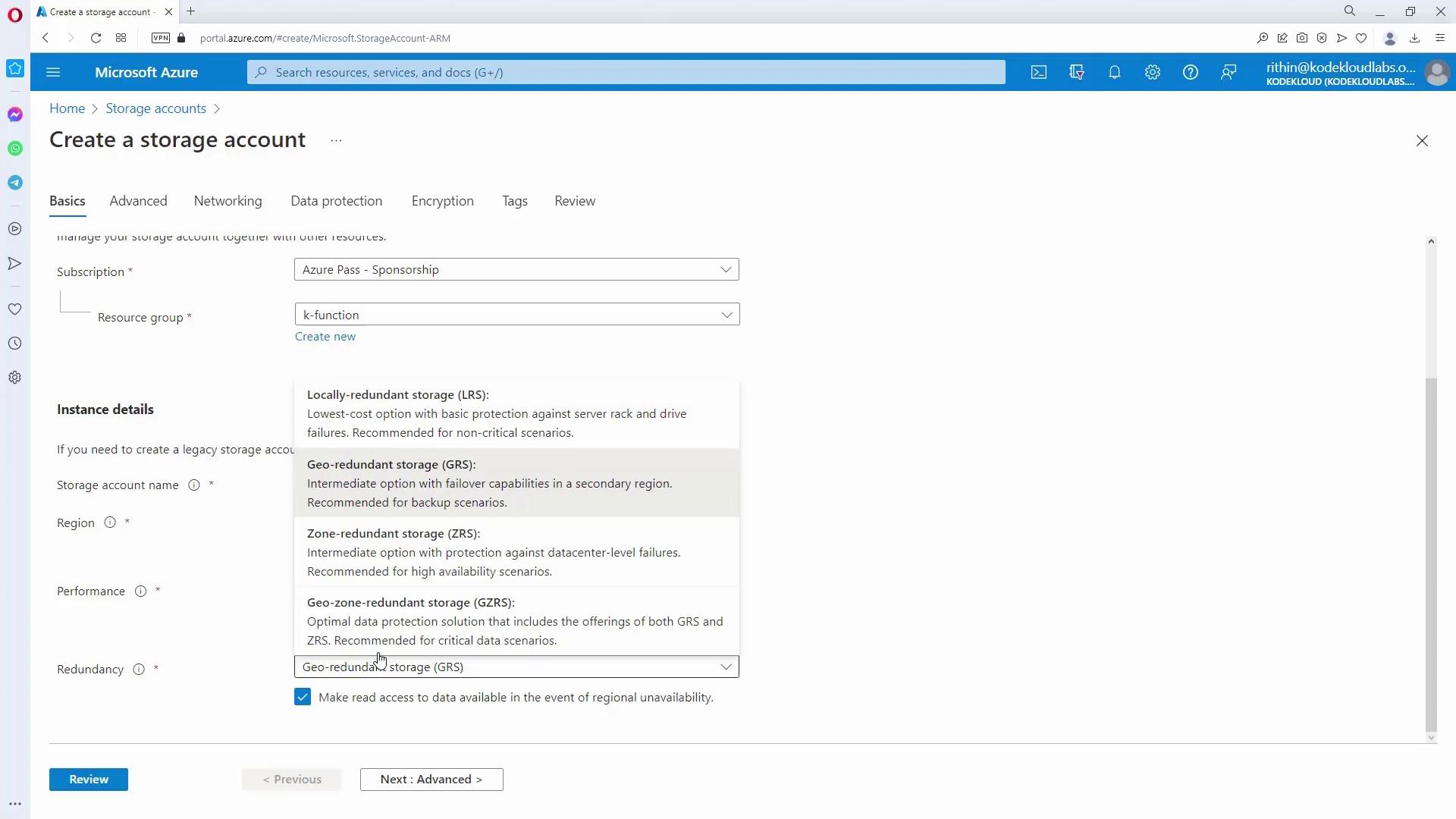
Advanced Options:
In the advanced settings, select an access tier. Remember, only hot and cool tiers are available at the account level.
Enabling Version-Level Immutability:
Switch to the Data Protection tab and enable "Enable version-level immutability support." This configuration allows you to set a default time-based retention policy at the account level for all blobs. Note that this option must be enabled during the initial creation of the account. If not enabled, you will need to configure immutability at the container level or for individual blob versions later.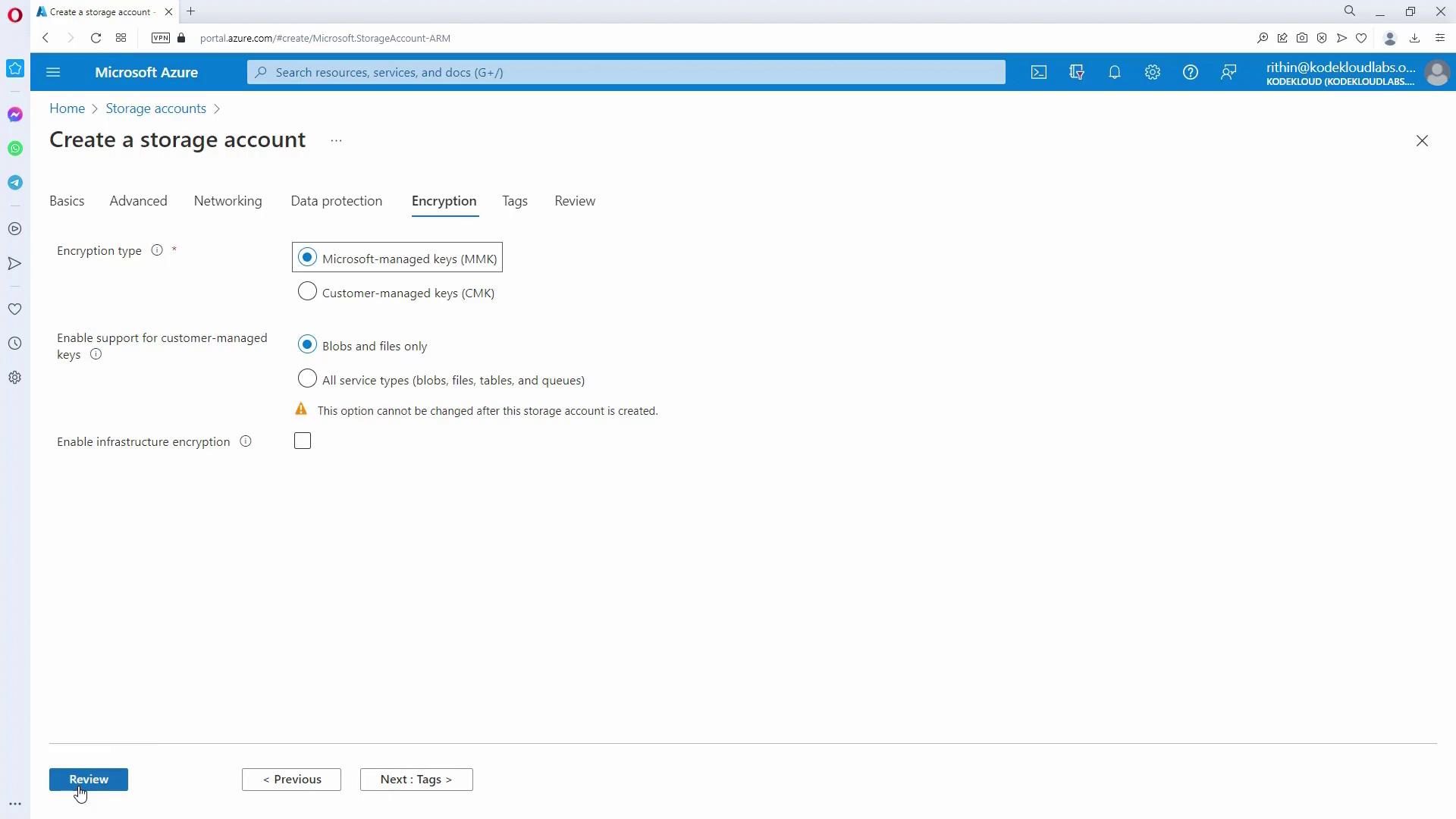
Verifying Immutable Settings Post-Creation:
After creating the storage account, inspect the Data Protection settings. In accounts without initial version-level immutability enabled, the option will be grayed out. In such cases, immutable policies can still be added at the container level.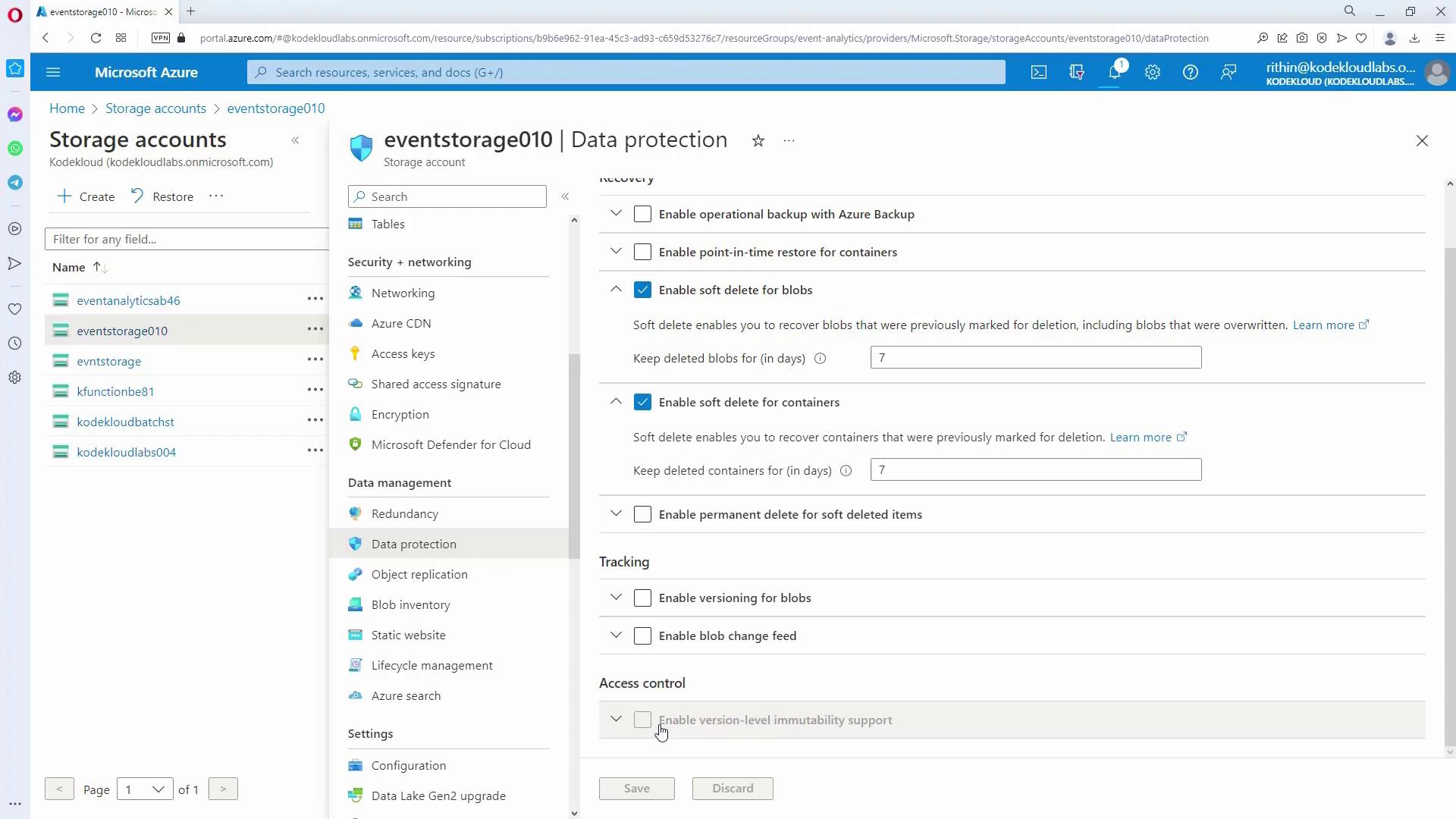
Configuring Container-Level Policies:
Create a new container (for example, "random") and set its access policy to add either a time-based retention policy or a legal hold. For a time-based retention policy, you might specify a duration of 365 days. You can also define whether this policy applies only to append blobs.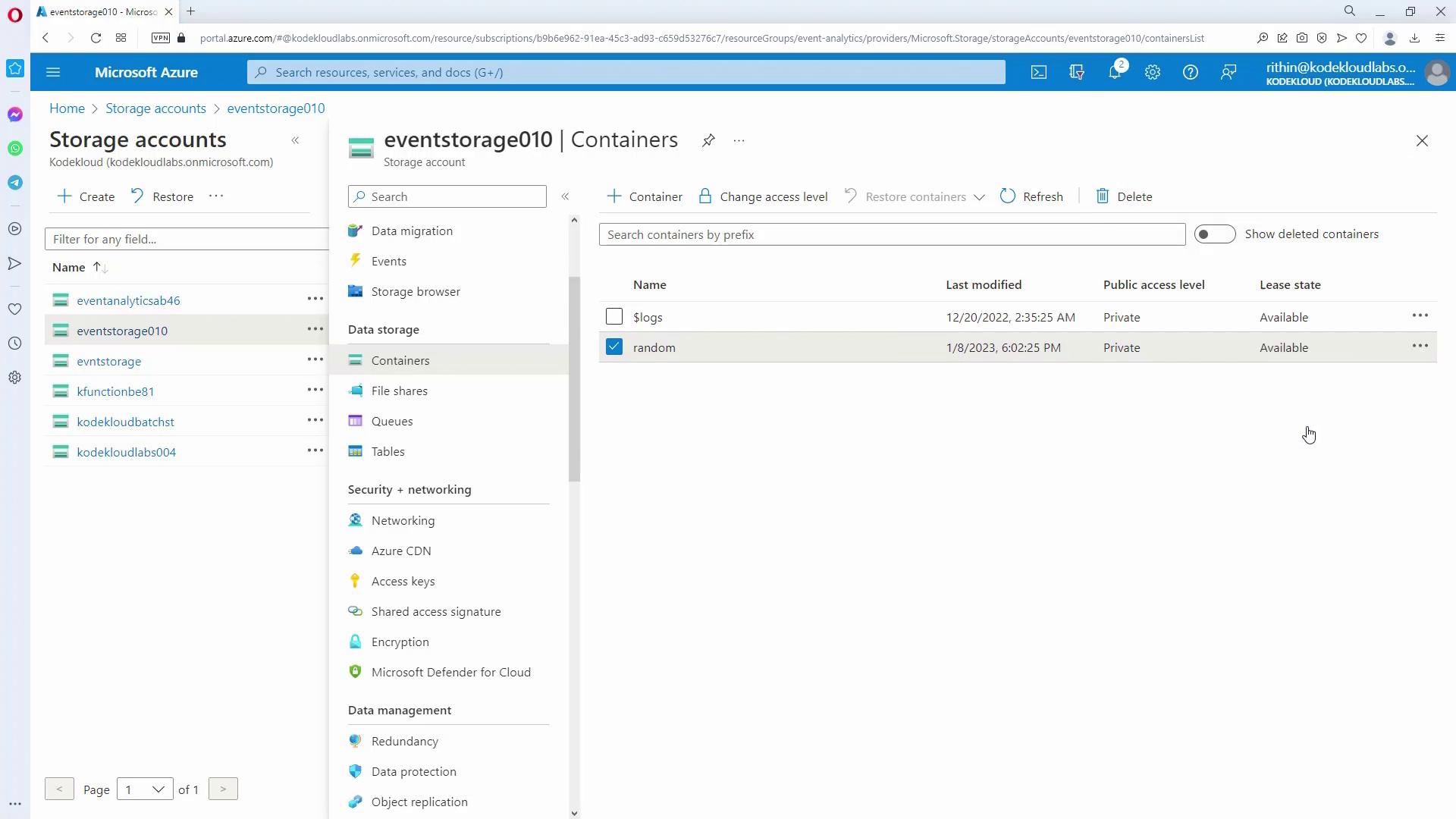
Managing Immutable Policy on a Newly Created Storage Account:
For storage accounts with immutability support enabled during creation, navigate to the Data Protection section and select "Manage Policy." Here, set a default account-level retention period (e.g., 365 days). Keep in mind that while time-based retention can be managed at the account level, legal holds must be applied at the container level.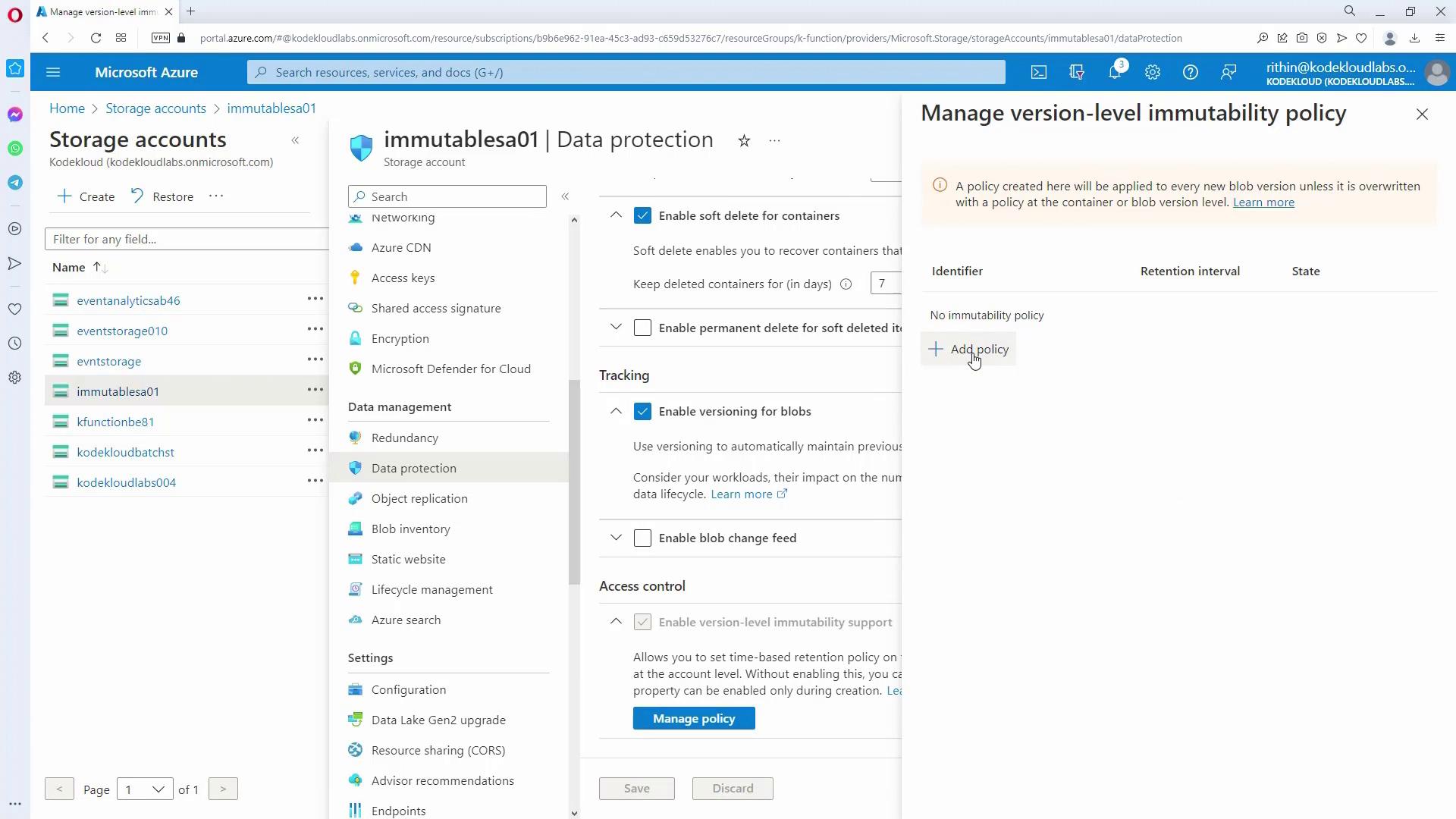
Testing the Immutable Policy:
To verify that the immutable policy is in effect, create a container (for example, "so random"), upload a file, and inspect its version details. The version ID will show the active immutability policy with a retention end date (e.g., until 1.8.2024, given a 365-day policy set on January 8, 2023). Any attempt to delete the blob will result in an error message indicating that the blob is immutable.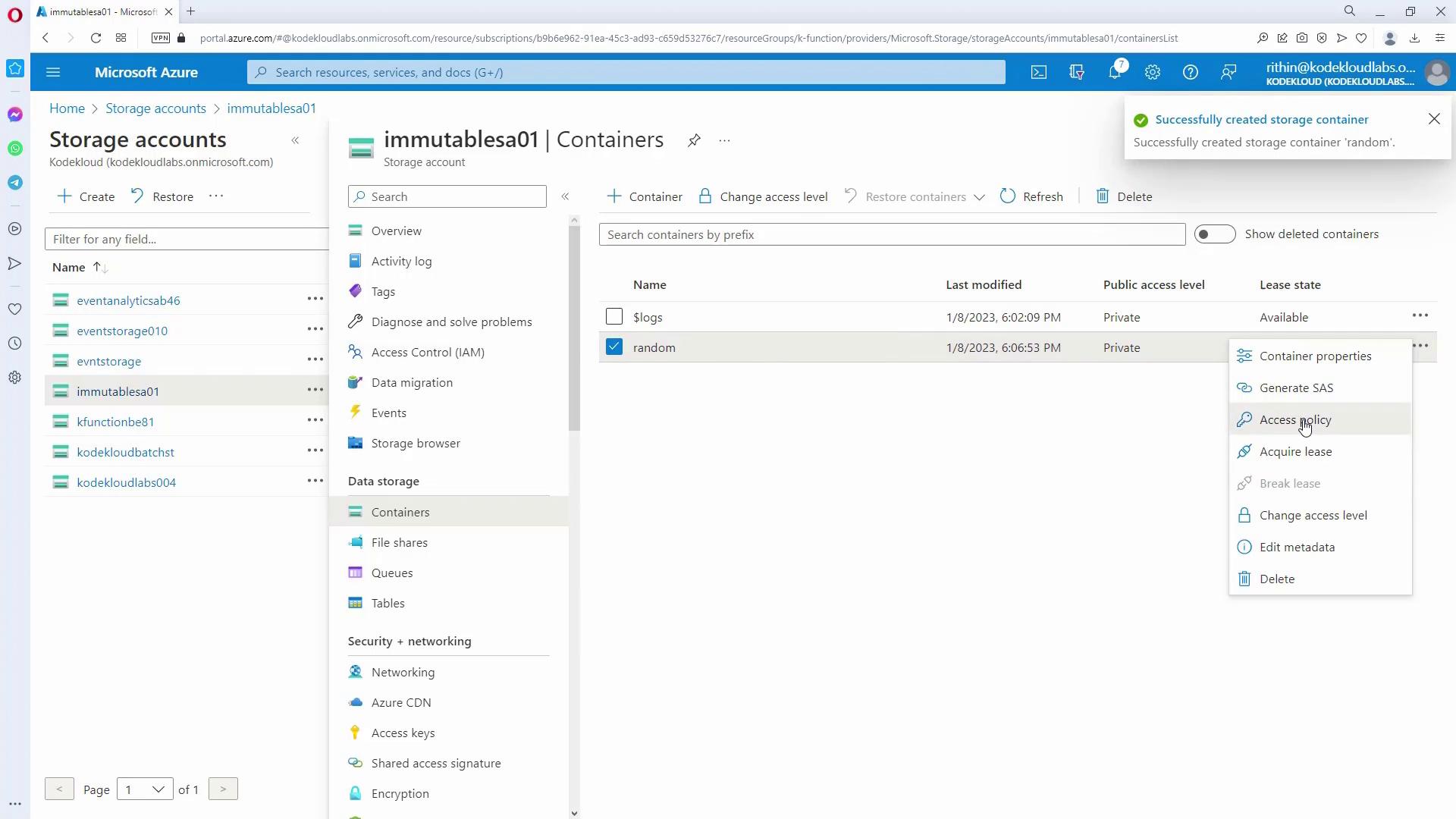
Conclusion
This article reviewed advanced design considerations for Azure Blob Storage, including the selection of optimal access tiers and the implementation of immutable storage policies for compliance and business-critical scenarios. By leveraging these configurations, you can optimize costs, performance, and data protection to meet your specific requirements.
Next, we will explore the design aspects for Azure Files.
Further Reading & Resources
Happy learning!
Watch Video
Watch video content