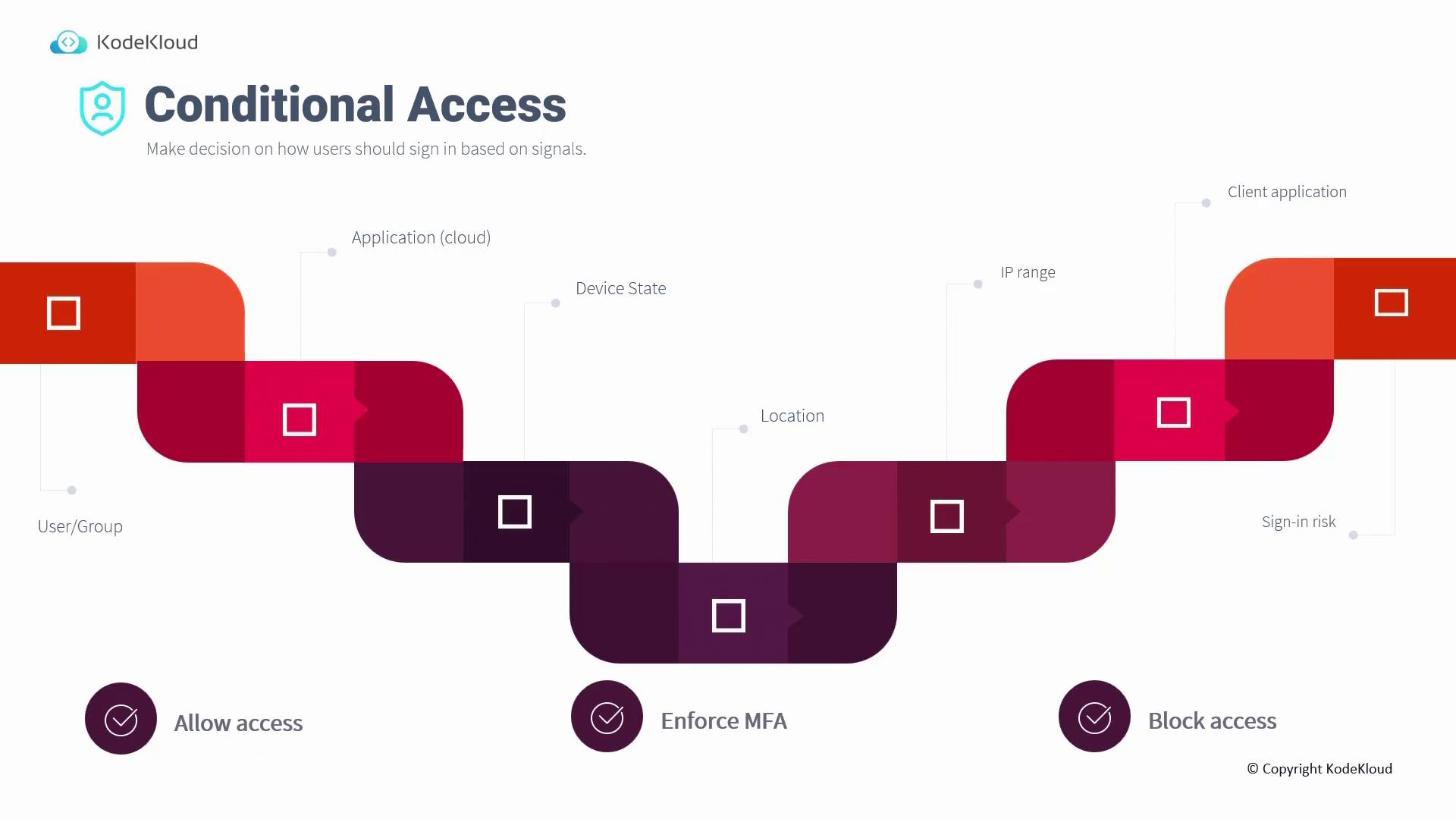
Understanding Conditional Access Signals
Conditional access policies utilize a variety of signals to determine the necessary level of security during the sign-in process. The key signals include:-
User or Group
The identity of the user or the associated group is fundamental. For example, if a high-risk user or group is signing in, additional verification may be required. -
Application
The specific cloud-hosted application being accessed also serves as a signal. Different applications can have tailored access policies. -
Device State
The compliance state of the device is crucial. Devices managed via solutions like Intune (whether hybrid AD joined, domain joined, or compliant) determine if further checks are needed. -
Location
The geographical location from which the user is signing in influences access control. For instance, if your organization is headquartered in Singapore, you might restrict access from regions outside Singapore. -
IP Ranges
Trusted IP ranges can be specified. If sign-in attempts originate from an IP address outside these ranges, access may be denied. -
Client Application
The type of client—such as Safari, Firefox, or a mobile app—can affect the decision to prompt for additional verification. -
Sign-In Risk
Provided by Microsoft Identity Protection, this signal assesses the risk associated with a sign-in attempt. If elevated risk is detected, measures such as MFA or a password reset can be executed.
These signals are applicable when using Azure AD authentication, where properties like location, device compliance, and client application are evaluated to dictate access levels.
Access Decisions Based on Signals
Based on these conditional access signals, there are three primary actions:- Allow Access
For example, signing in from a trusted location (e.g., Singapore) can permit access without additional security prompts.
-
Enforce MFA
Consider an internal IP range (e.g., 52.11.11.0/27). If a sign-in originates from within this trusted range, access is granted. However, requests from outside this range trigger MFA via an authenticator app or text message to verify the user’s identity. -
Block Access
When a user signs in from an untrusted location—for instance, accessing from Japan when your organization exclusively operates in Singapore—access is blocked outright.
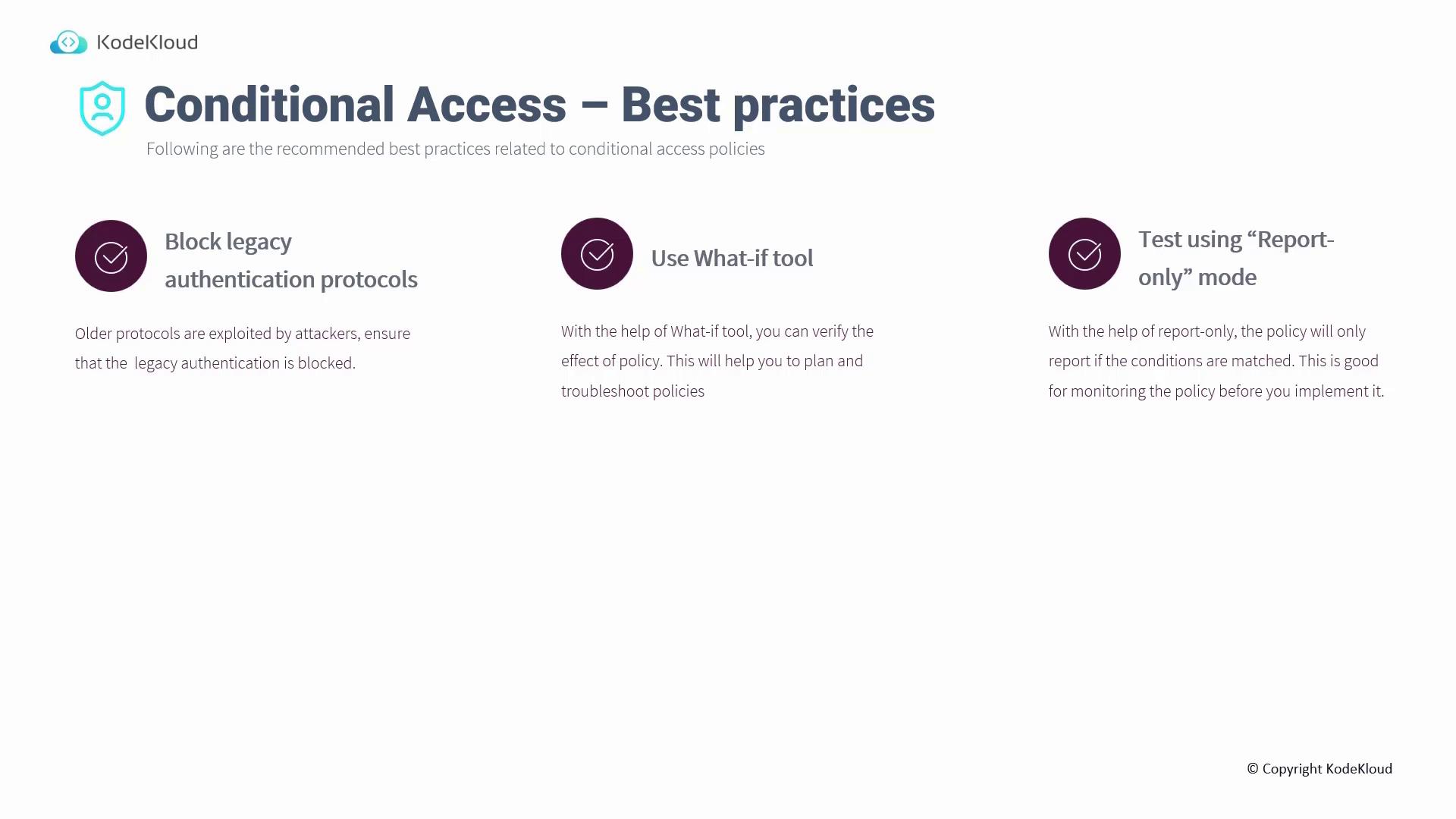
Best Practices for Implementing Conditional Access
Implementing conditional access policies successfully involves adhering to several best practices:-
Enable MFA for Privileged Users
Enforce MFA for administrators and high-privilege accounts. This safeguards against risks if credentials are compromised. -
Require Managed Devices
Only allow access from devices that are managed and compliant with organizational policies (e.g., via Intune), reducing the risk associated with personal or unmanaged devices. -
Access Approved Client Applications Only
Restrict access to corporate resources to approved client applications. For instance, allow personal devices to access Outlook and OneDrive, but limit access to Microsoft Teams.

-
Exclude Specific Countries
Exclude sign-ins from irrelevant geographical regions. For organizations based in Singapore, blocking sign-ins from other countries enhances security. -
Respond to Compromised Accounts
Utilize Identity Protection to monitor and flag suspicious sign-in activities. In cases of compromised accounts, enforce MFA and prompt for an immediate password change. -
Block Legacy Authentication Protocols
Prevent the use of legacy authentication methods, which rely solely on username and password and bypass MFA. -
Use the “What-If” Tool
Leverage the What-If tool to simulate sign-in scenarios based on user attributes, location, IP address, and device state. This helps troubleshoot and refine policies before production deployment. -
Test Using Report-Only Mode
Utilize report-only mode to evaluate the impact of conditional access policies before enforcing them widely. This mode generates audit logs for genuine sign-in attempts, helping to identify potential issues without locking users out.
Demonstrating Conditional Access Configuration in Azure
In this section, we present a step-by-step process to configure conditional access policies using the Azure Portal.1. Navigating to Azure Active Directory
- Log in to the Azure Portal and navigate to Azure Active Directory.
- Select “Users” to view all users and filter by type to distinguish between guest accounts and members.
2. Resetting a User’s Password
- Choose a user account (e.g., Adam).
- Reset the user’s password if required.
- Open an incognito browser window, go to portal.azure.com, and sign in as the user.
(The sign-in process may prompt for a password update and configuration of the Authenticator app if self-service password reset (SSPR) is enabled.)
3. Creating a Conditional Access Policy
- In the Azure Portal, go to the Conditional Access section.
- Click on ”+ New policy” to initiate a new policy.
- Configure assignments by selecting relevant users or groups, choosing cloud apps, and defining conditions.
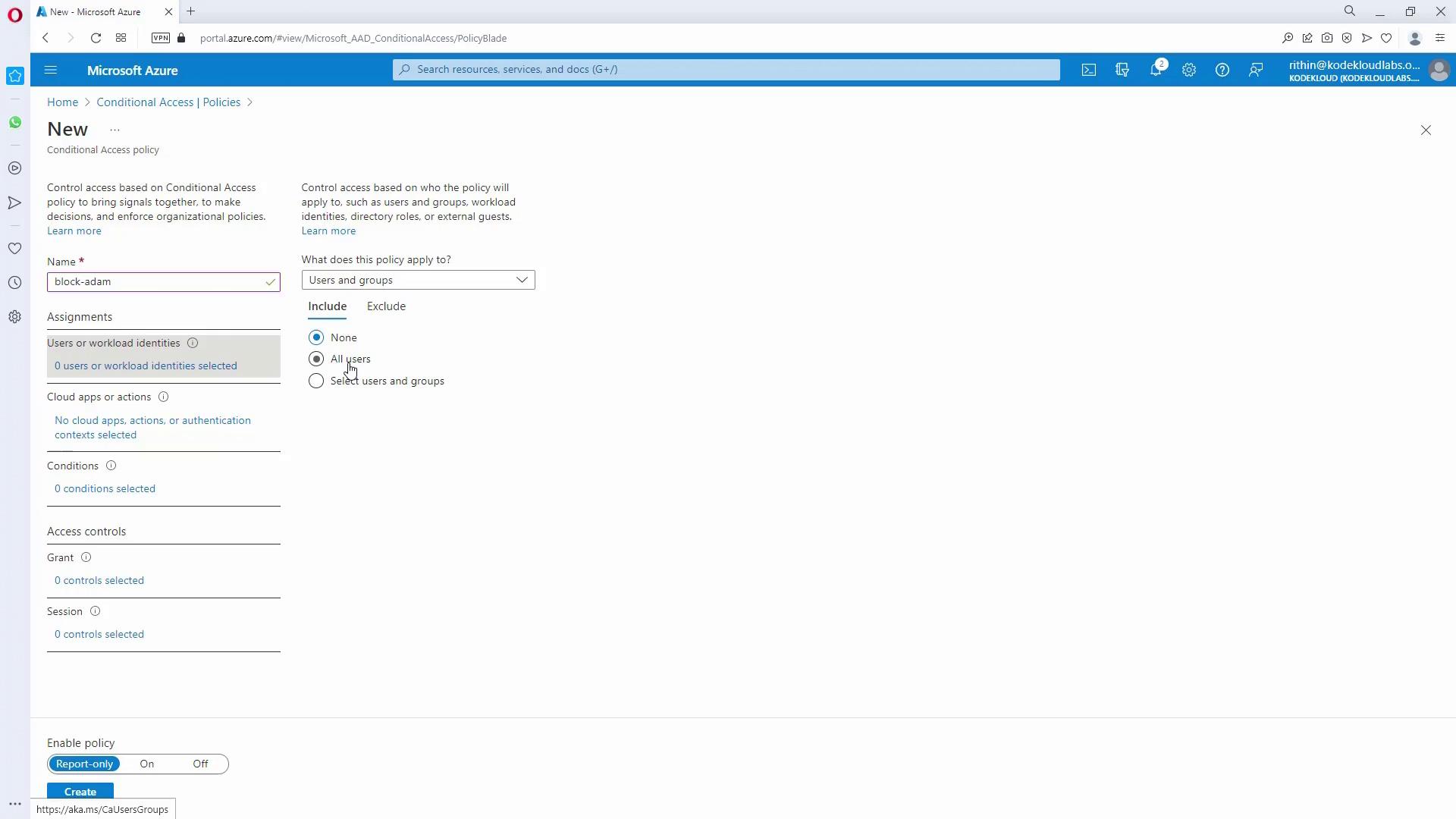
- You can create a policy, for instance, named “block-adam” to apply specific restrictions for certain users or groups.

4. Reviewing Policy Settings and Testing
- Finalize your policy by reviewing settings related to cloud apps, conditions, and access controls (e.g., enforcing MFA).
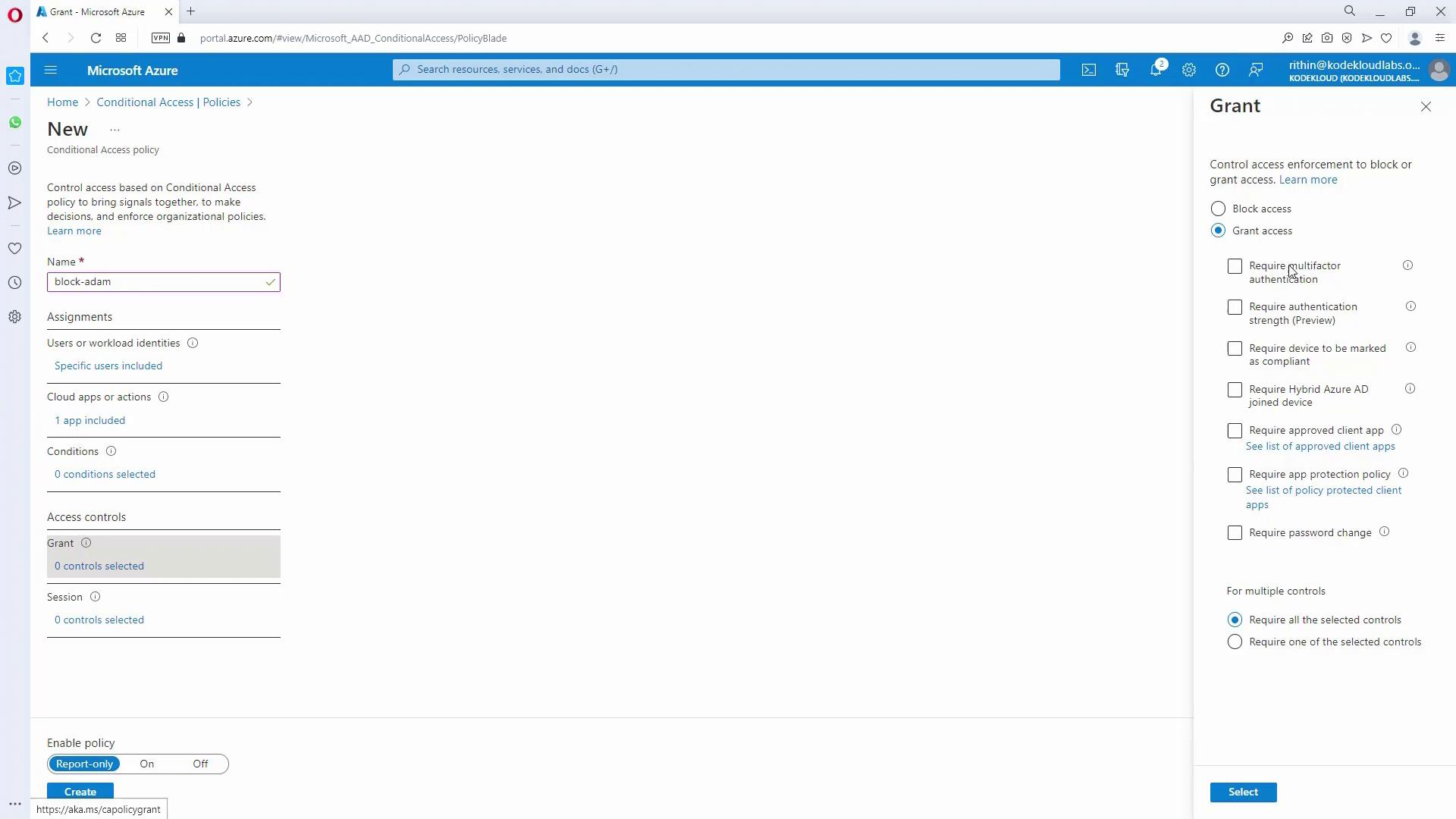
- Return to the Conditional Access Policies page to view and manage your active policies.
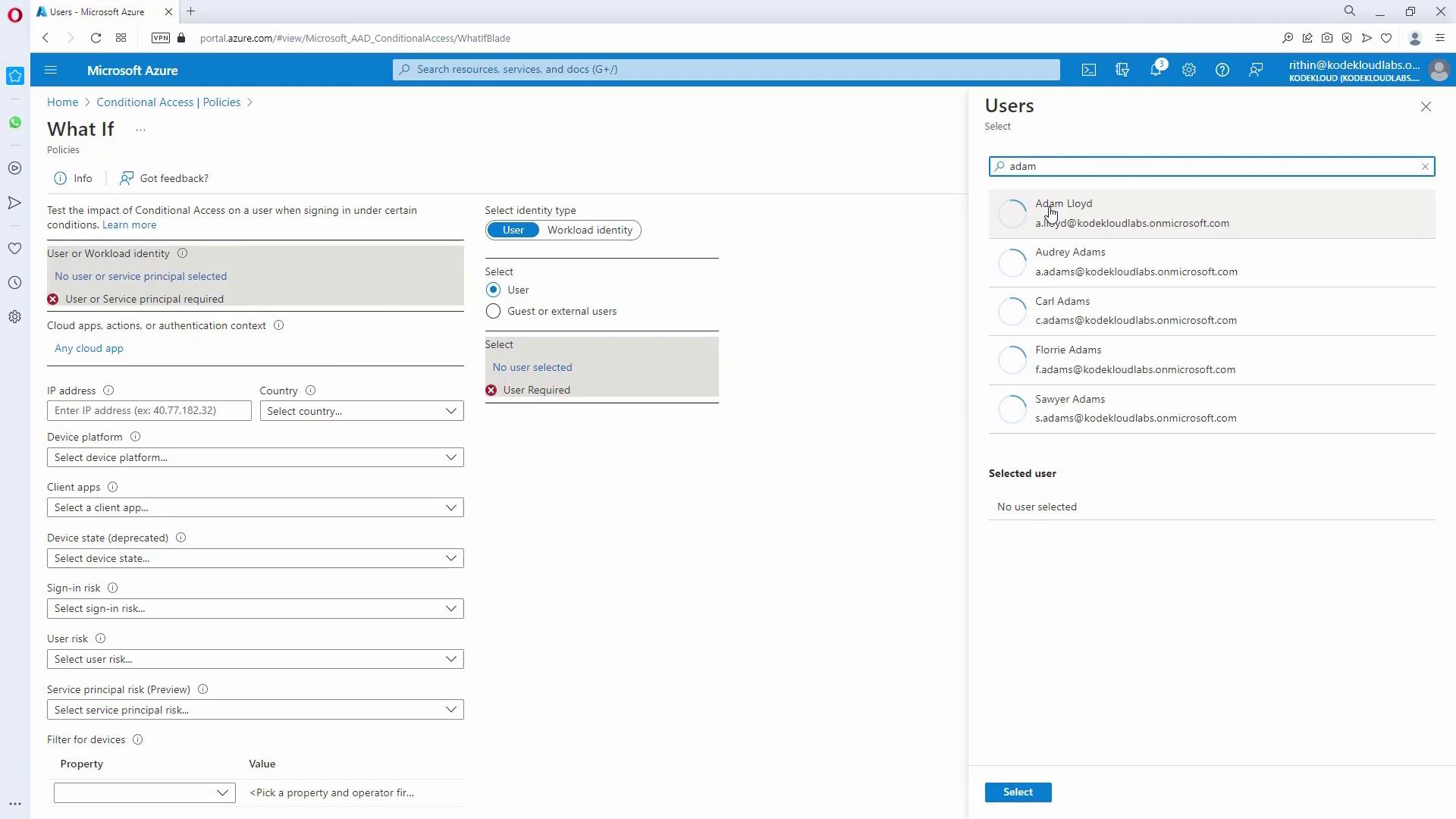
5. Testing the Policy
- Utilize the built-in “What-If” tool to simulate various sign-in scenarios.
- Select a user and configure conditions (such as IP address, device platform, and location) to validate the efficacy of your policies.
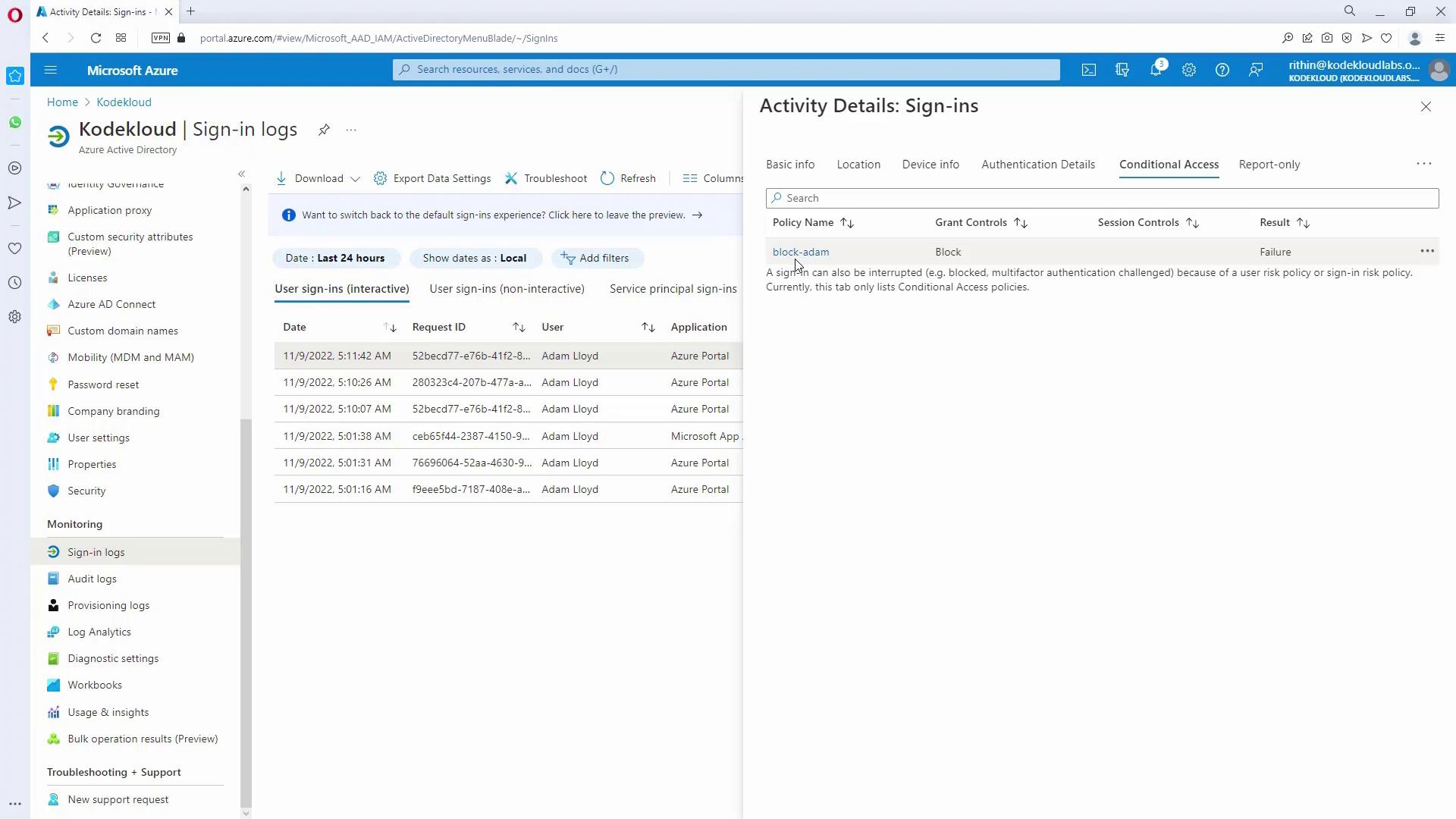
6. Reviewing Sign-In Logs
- Finally, inspect the sign-in logs to confirm that the conditional access policy functions as expected. For example, review logs for a user such as Adam Lloyd to analyze any blocked sign-in attempts.
By following these steps and adhering to best practices, you can design an effective conditional access strategy that safeguards your critical applications while ensuring seamless access for trusted users and devices. For further insights, consider exploring additional resources such as Azure Active Directory documentation and Microsoft Identity Protection.
Testing your policies in report-only mode before full enforcement is critical. It helps identify any potential issues without impacting user productivity.