Azure Kubernetes Service
AKS Security
Azure Defender with AKS
In this guide, we explore how to secure Azure Kubernetes Service (AKS) using Azure Defender for Cloud—formerly known as Security Center. You’ll learn about its plans, core components for AKS integration, image scanning in Azure Container Registry (ACR), and advanced detection features.
What Is Azure Defender for Cloud?
Azure Defender for Cloud delivers unified security management and advanced threat protection for workloads across Azure, AWS, GCP, and on-premises environments. It provides:
- Continuous vulnerability assessment
- Advanced threat detection with Microsoft Threat Intelligence
- Security posture monitoring and actionable recommendations
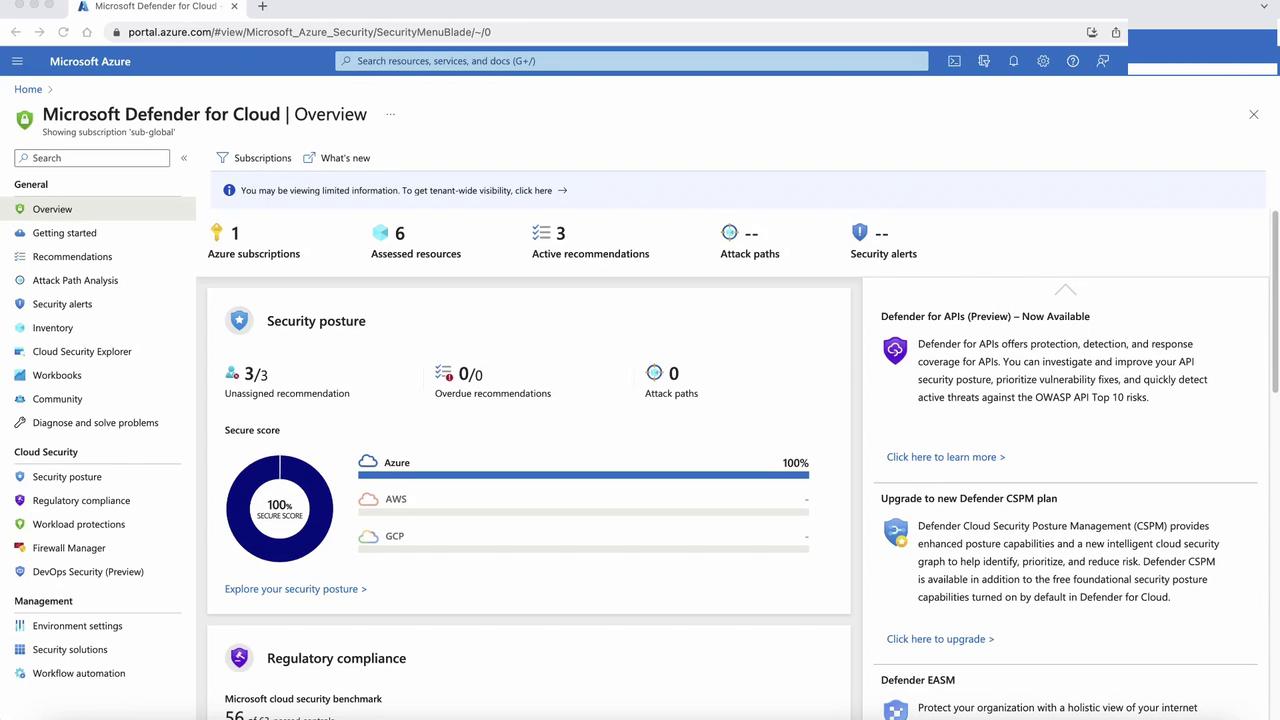
Defender for Cloud Plans
| Plan | Cost | Coverage | Key Features |
|---|---|---|---|
| CSPM Foundational (free) | Free | All resources | Basic posture management, compliance benchmarks |
| Defender (paid) | Per node | Selected workloads (e.g., Containers) | Continuous vulnerability scanning, threat detection |

Note
You can enable the Defender plan only for container workloads while keeping other services on the free CSPM tier.
- Continuous workload vulnerability scans
- Container-specific threat detection
- Posture assessment and remediation recommendations
Defender for AKS: Core Components
Azure Defender for Kubernetes leverages two native integrations:
Defender profile
A DaemonSet that runs on every AKS node, collects security events, logs, and inventory, then ships them securely to Defender for Cloud.Azure Policy add-on
Extends Gatekeeper to enforce built-in security policies managed by Azure Policy and Defender for Cloud. Can also be used standalone.
Defender Profile DaemonSets
The profile deploys three pods per node to capture and forward security data:
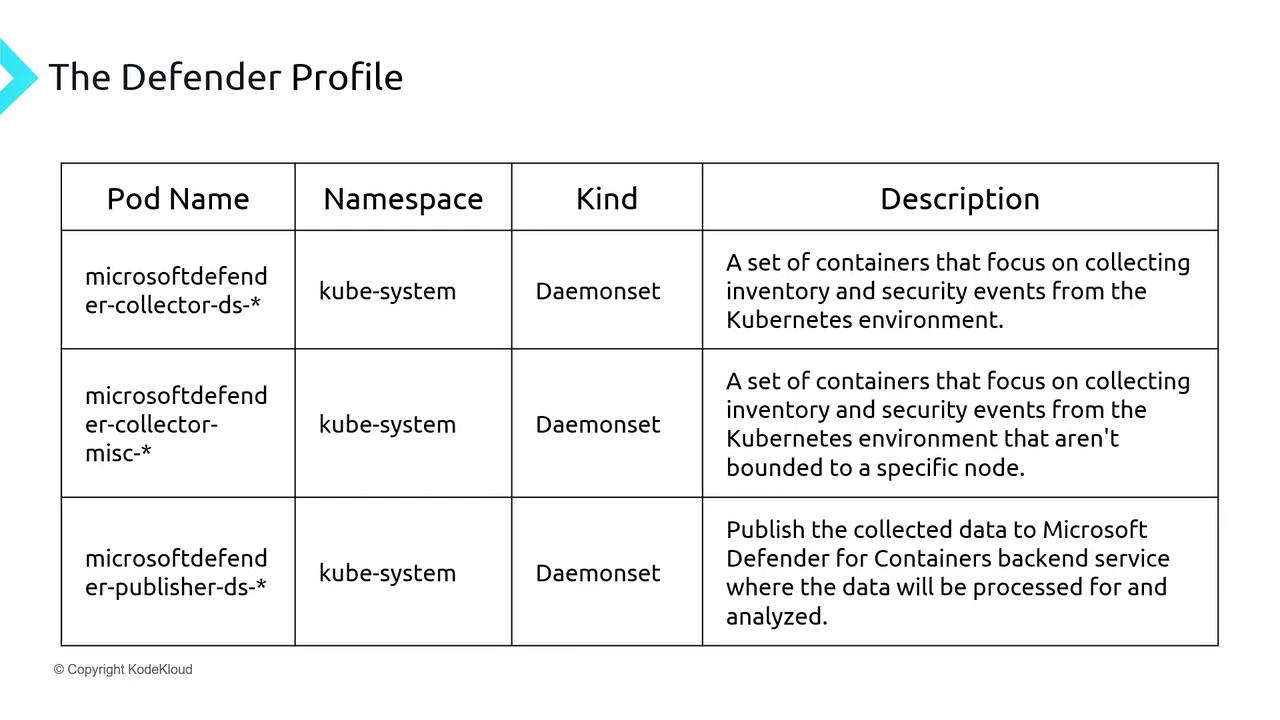
- Two pods collect and aggregate security events/logs.
- One pod sends aggregated data to Defender for Cloud (requires outbound HTTPS on port 443).
Warning
Ensure your network security groups and firewalls allow outbound port 443 from AKS nodes for Defender data upload.
At a glance, Defender for AKS will:
- Collect control-plane and workload logs
- Feed logs to the Defender engine for analysis
- Enforce and report on security policies via Azure Policy
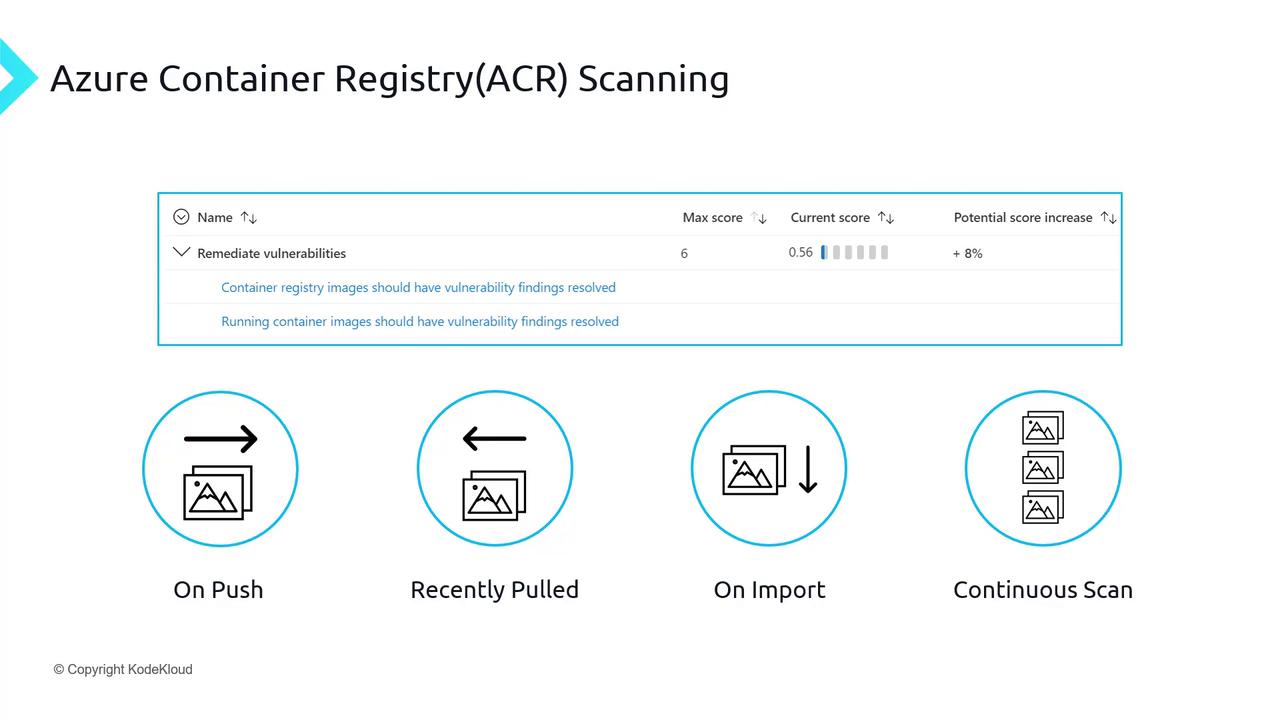
Azure Container Registry (ACR) Scanning
Azure Defender integrates with ACR to scan container images using Qualys. Scans are triggered:
| Trigger | Description |
|---|---|
| On Push | Immediately after an image is pushed |
| On Import | When importing external images into ACR |
| Recent Pull (weekly) | If an image is pulled and hasn’t been scanned in 30 days |
| Scheduled Continuous Scan | Recurring vulnerability assessments |
Defender pulls each image into a secure sandbox for Qualys to extract CVEs and severity data, then presents prioritized recommendations:
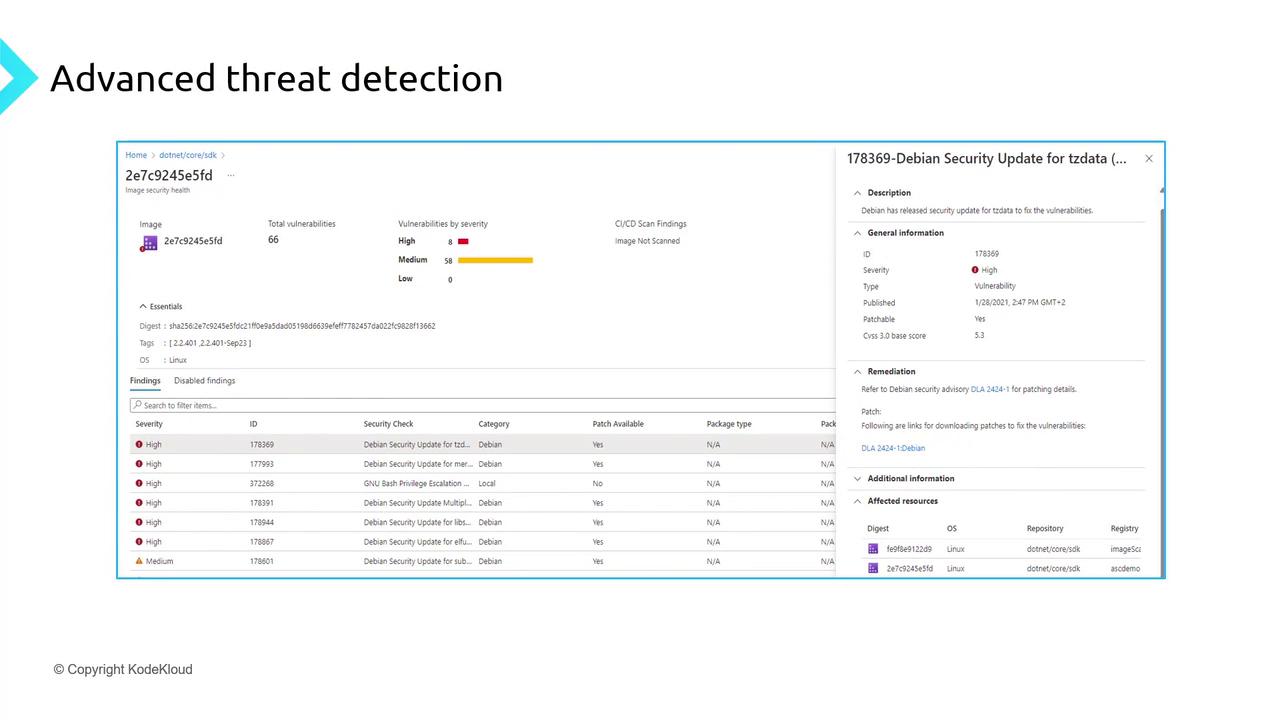
The report includes remediation steps, linked CVEs, and severity-based prioritization.
Features and Capabilities
Once Defender for Containers receives logs and scan results, you gain:
- AI-powered and anomaly-based threat alerts
- Mapping of alerts to MITRE ATT&CK tactics with Kubernetes context
- Integration with Logic Apps or webhooks for automated incident response
- Continuous export of security incidents and recommendations
Links and References
- Azure Defender for Cloud documentation
- Azure Kubernetes Service (AKS)
- Azure Container Registry documentation
- Microsoft Threat Intelligence
- Qualys
- MITRE ATT&CK Framework
Watch Video
Watch video content