Azure Kubernetes Service
Just Enough Azure for AKS
Azure Landing Zone
Azure Scaffolding—formally known as the Azure Landing Zone—delivers a repeatable, compliant, and scalable framework for building your cloud infrastructure to meet organizational standards. While each enterprise customizes its landing zone, the core goal remains the same: establish foundational services before deploying workloads.
Note
An Azure Landing Zone isn’t one-size-fits-all. Tailor networking, identity, and security controls to align with your company’s policies and compliance requirements.
Key Infrastructure Domains
Think of a landing zone as the infrastructure “blueprint” for your cloud environment—much like a city plan that must exist before any buildings go up. Core areas include:
- Networking: Virtual networks and subnets create the “roads” that connect your resources.
- Identity & Access: Azure Active Directory, role-based access controls, and managed identities provision secure access.
- Security & Governance: Azure Policy, Blueprints, and resource locks enforce organizational standards, similar to building codes.
- Monitoring & Operations: Azure Monitor, Log Analytics, and automation scripts collect telemetry and handle incident response.
- Cost Management: Budgets, chargeback rules, and tagging strategies help track and optimize spend.
Landing Zone Domains at a Glance
| Domain | Purpose | Azure Service Examples |
|---|---|---|
| Identity & Access Management | Secure authentication and authorization | Azure AD, Privileged Identity Management (PIM) |
| Network Topology & Connectivity | Private and hybrid connectivity | Azure Virtual Network, VPN Gateway, ExpressRoute |
| Resource Organization & Tagging | Logical grouping and billing | Resource Groups, Management Groups, Tag Policies |
| Security Controls & Policy Enforcement | Compliance enforcement and threat protection | Azure Policy, Azure Security Center |
| Governance & Compliance Auditing | Continuous compliance monitoring | Azure Blueprints, Compliance Manager |
| Monitoring, Logging & Diagnostics | Health checks, alerts, and telemetry | Azure Monitor, Log Analytics, Application Insights |
| Cost Management & Chargeback | Budgeting and cost allocation | Azure Cost Management, Budgets, Tags |
| Automation & DevOps Integration | CI/CD pipelines and infrastructure as code | Azure DevOps, GitHub Actions, ARM Templates, Terraform |
Warning
Skipping proper scaffolding can lead to inconsistent deployments and security gaps. Always validate your landing zone against Azure’s Well-Architected Framework.
AKS-Specific Landing Zone
When deploying Azure Kubernetes Service (AKS), you’ll extend the general landing zone with AKS-specific scaffolding. This ensures that:
- Virtual networks and subnets are preconfigured for pod-to-pod and pod-to-service traffic.
- Route tables, network security groups (NSGs), and Azure Firewall rules enforce network segmentation.
- Managed identities and Azure Key Vault integrate for secure secret management.
- Log and metric pipelines feed into Azure Monitor and a centralized SIEM for observability.
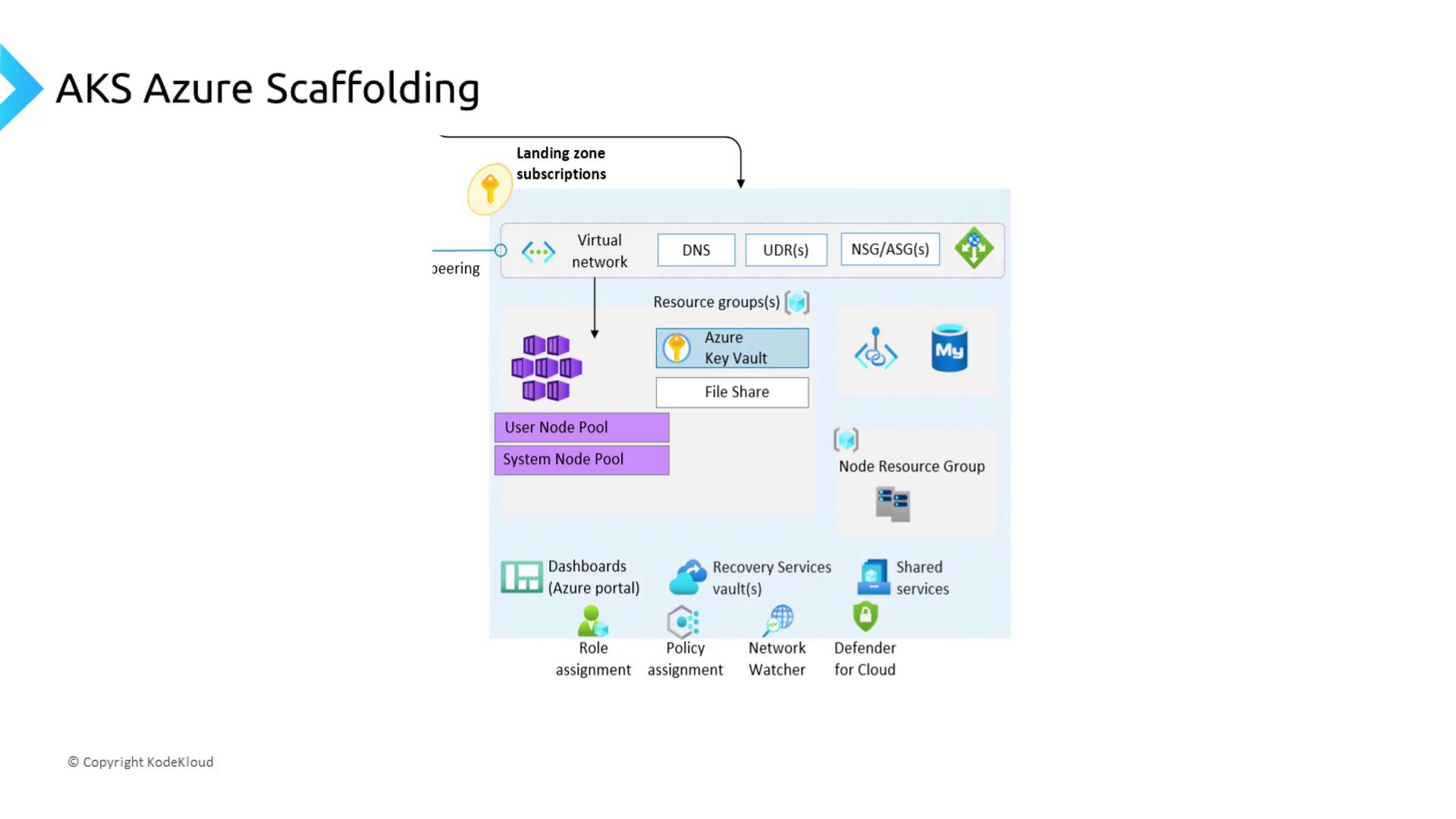
By leveraging an AKS landing zone, your clusters gain predictable connectivity, robust security controls, and seamless integration with other Azure services—accelerating your path to production.
Links and References
- Azure Landing Zones Overview
- Azure Kubernetes Service (AKS) Documentation
- Azure Well-Architected Framework
Watch Video
Watch video content