secure pods to unsecure pods). Kubernetes Network Policies fill this gap by enabling label-based, pod-to-pod traffic controls.
Limitations of Azure NSGs in AKS
- Pod IPs are ephemeral; NSG rules must be constantly updated.
- NSGs cannot reference Kubernetes constructs like namespaces or labels.
- Fine-grained policy (e.g., “allow traffic only from pods with label
app=frontend”) requires a native Kubernetes mechanism.
Kubernetes Network Policies
ANetworkPolicy is a native Kubernetes API object for controlling pod traffic. You define policies in YAML, selecting pods by labels and specifying allowed ingress and egress flows.
| Policy Type | Description |
|---|---|
| Ingress | Controls incoming traffic to selected pods |
| Egress | Controls outgoing traffic from selected pods |
When at least one
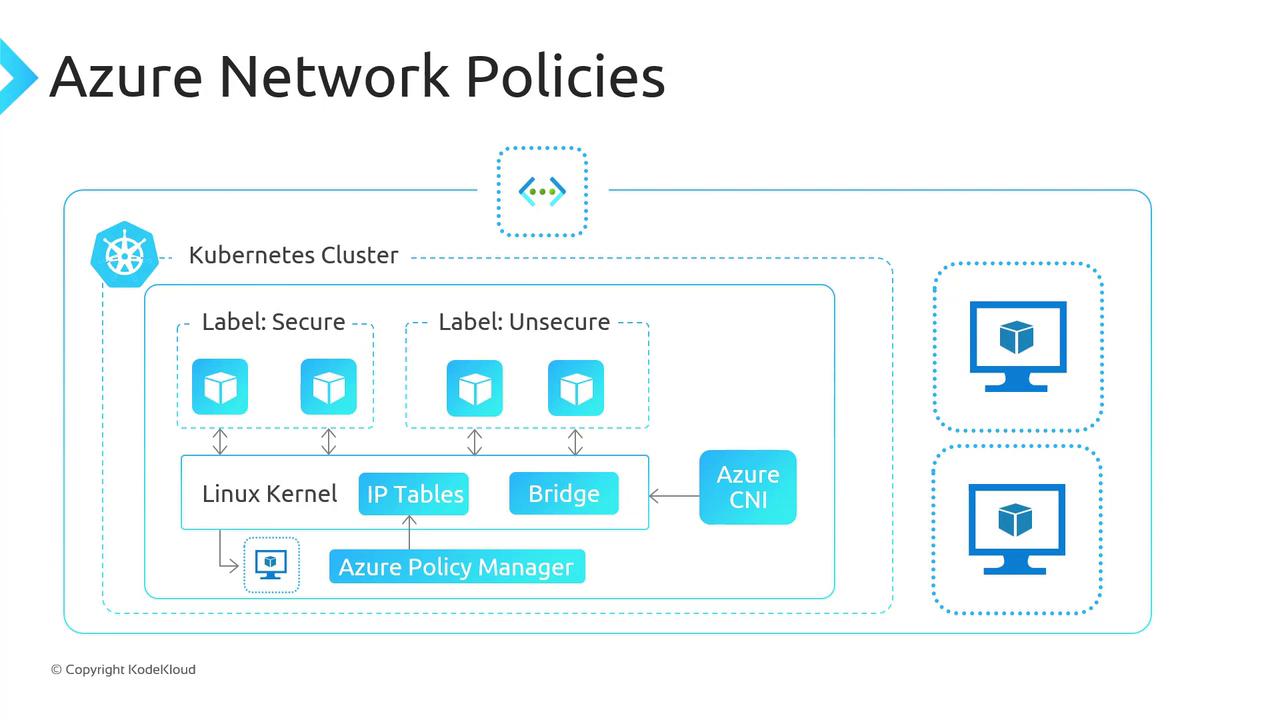
NetworkPolicy selects a pod, all other traffic is denied by default. Be sure to explicitly allow the flows your application requires.Azure Network Policy Engine
Azure’s built-in network policy engine runs as a DaemonSet on every node. It watchesNetworkPolicy objects and enforces rules using:
- Linux nodes: iptables + Linux bridge
- Windows nodes (preview): Host Networking Service (HNS) ACLs
Calico Network Policies
Calico by Tigera is an open-source networking and network security solution. It implements the KubernetesNetworkPolicy API and extends it with additional features:
- GlobalNetworkPolicy for cross-namespace rules
- NetworkSets and ServiceSets for object grouping
- Integrated logging and compliance profiles
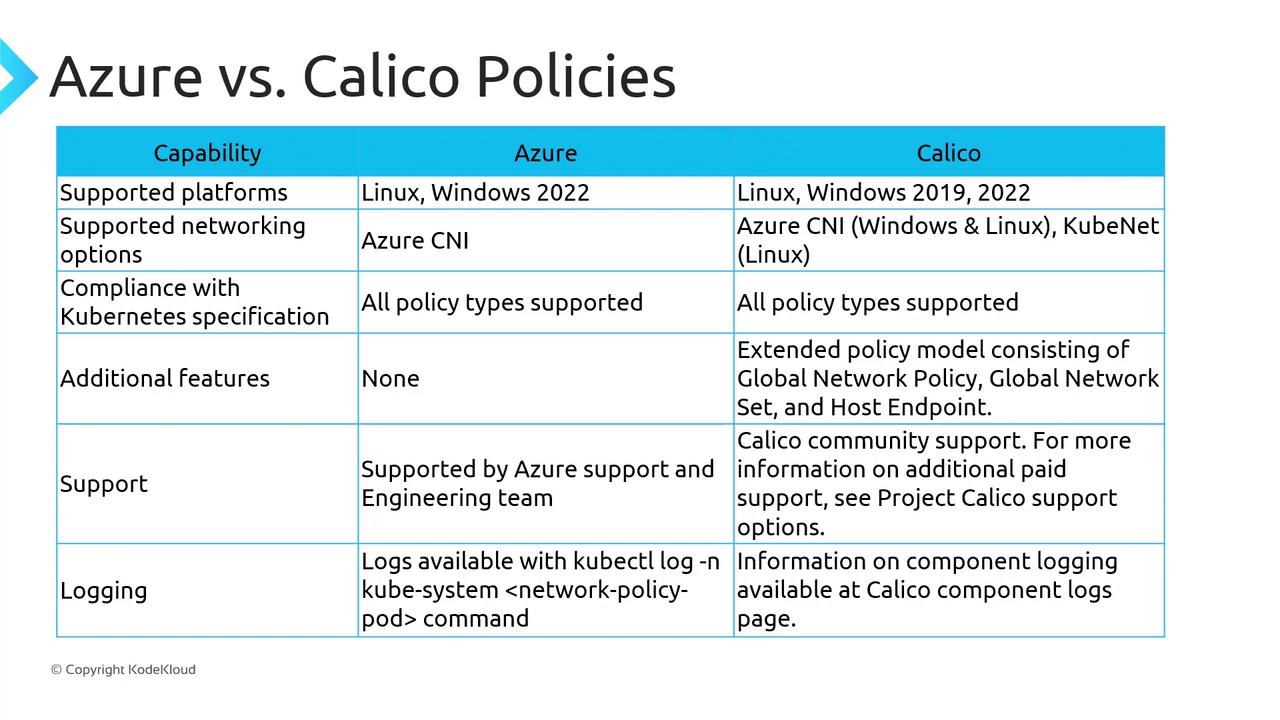
If you choose Calico, Microsoft support engineers may not diagnose issues stemming from Calico components. For troubleshooting, refer to the Calico documentation.
Troubleshooting Network Policies
To view policy enforcement logs for either engine:<network-policy-pod> with the DaemonSet pod name (e.g., azure-npm-daemonset or calico-node-xxxxx).