Certified Kubernetes Security Specialist (CKS)
Cluster Setup and Hardening
Protection Strategies
In this article, we explore several protection strategies in Kubernetes security using a relatable hotel analogy. By comparing Kubernetes components to elements of a well-run hotel, you'll gain a clearer understanding of how access control, isolation, and monitoring work together to secure your cluster.
Imagine a hotel where different staff members have varying access levels. For instance, managers have complete access to all areas, including secure zones such as the data center or security room, whereas housekeepers are limited to guest rooms.
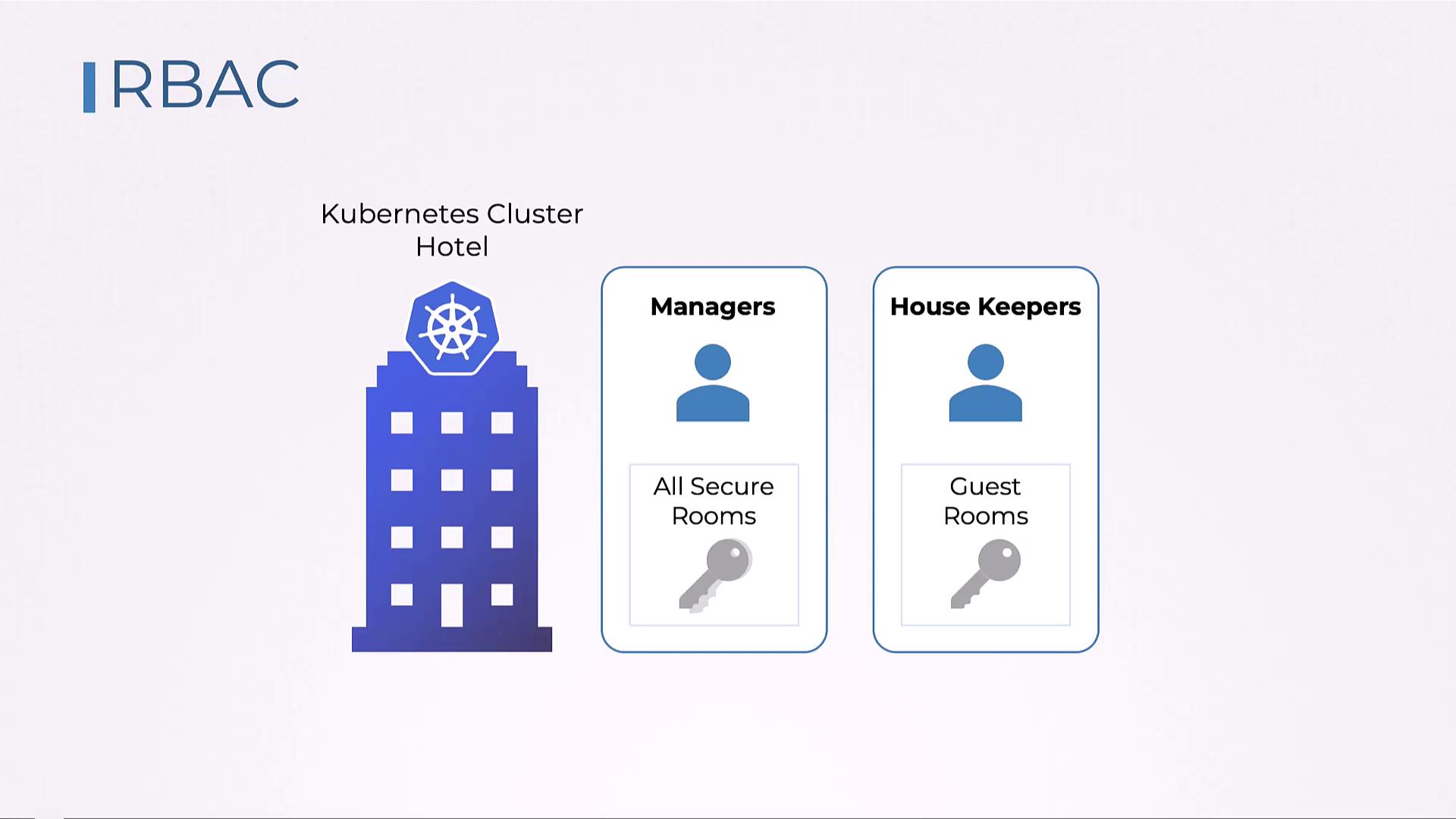
In Kubernetes, role-based access control (RBAC) mirrors this concept by determining who can access and modify node metadata. Specific roles come with defined permissions, ensuring that only authorized users can execute sensitive operations.
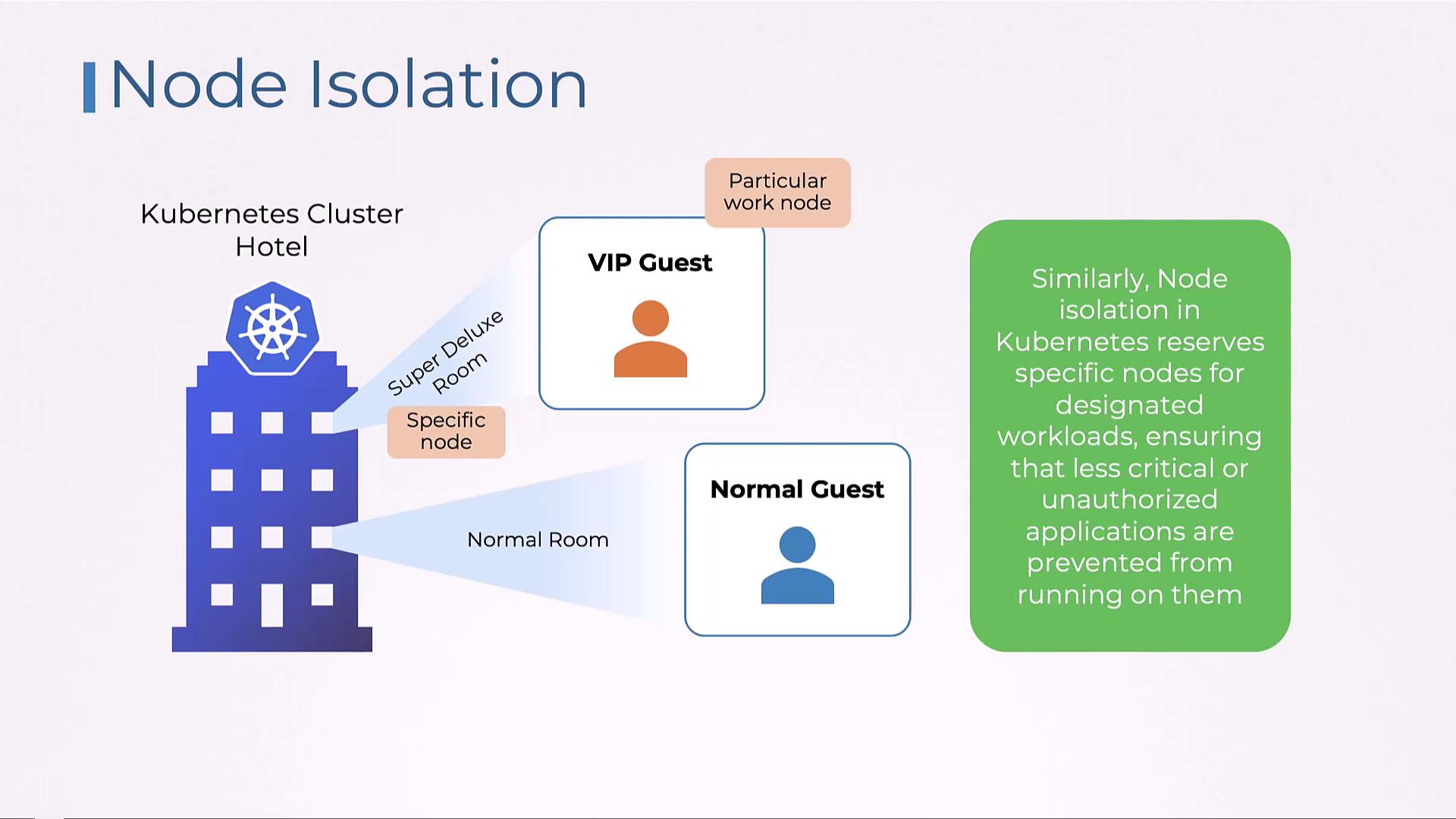
Just as a hotel caters to different guest types—offering VIP guests deluxe rooms and regular guests standard rooms—Kubernetes can reserve specific nodes for particular workloads. By isolating nodes, the system prevents non-critical or unauthorized applications from running on nodes dedicated to essential tasks.
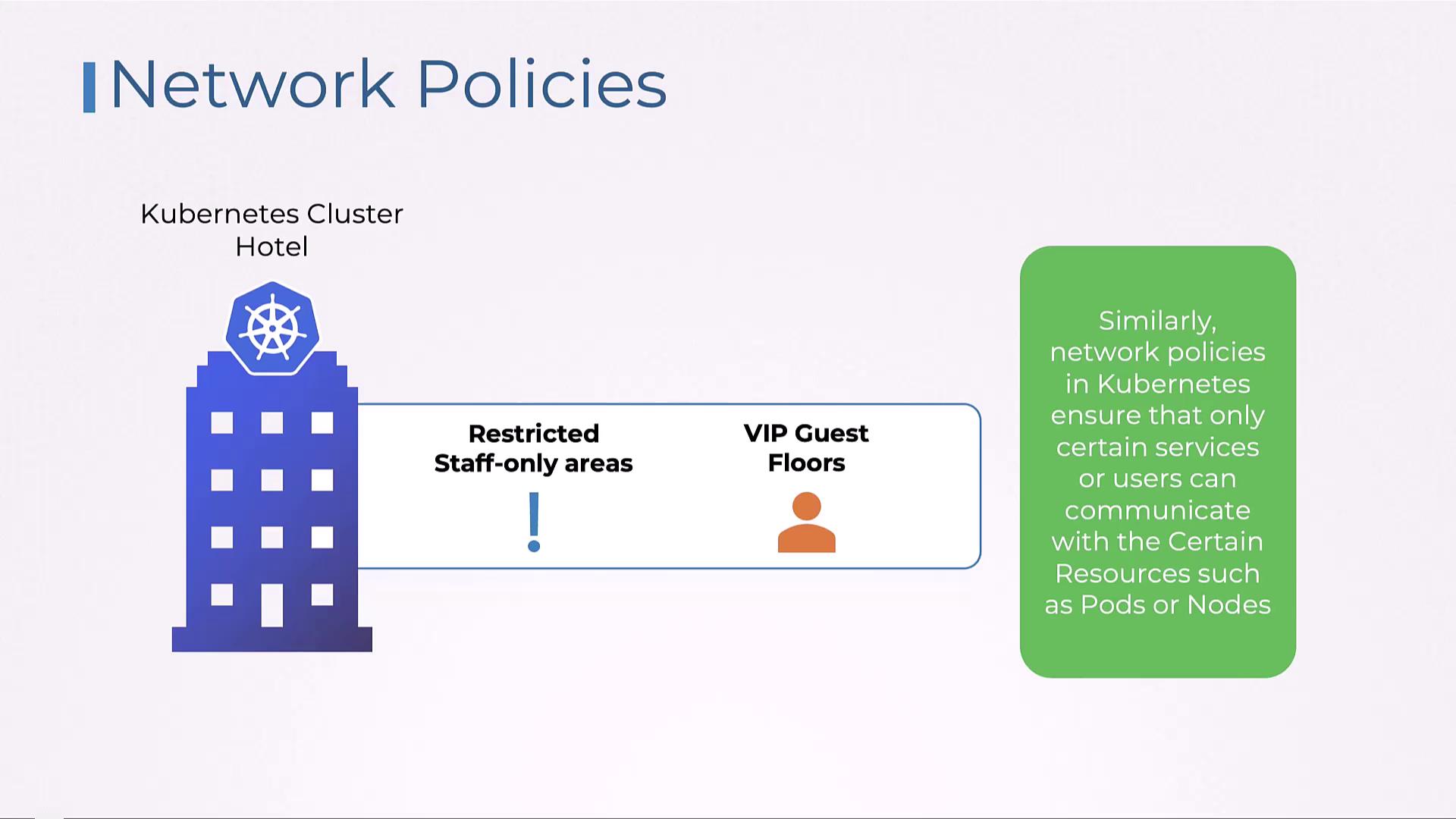
Another layer of protection is akin to having restricted staff-only areas and exclusive VIP guest floors. Within Kubernetes, network policies control communication between pods or nodes. This ensures that only select services or users can interact with designated resources.
Note
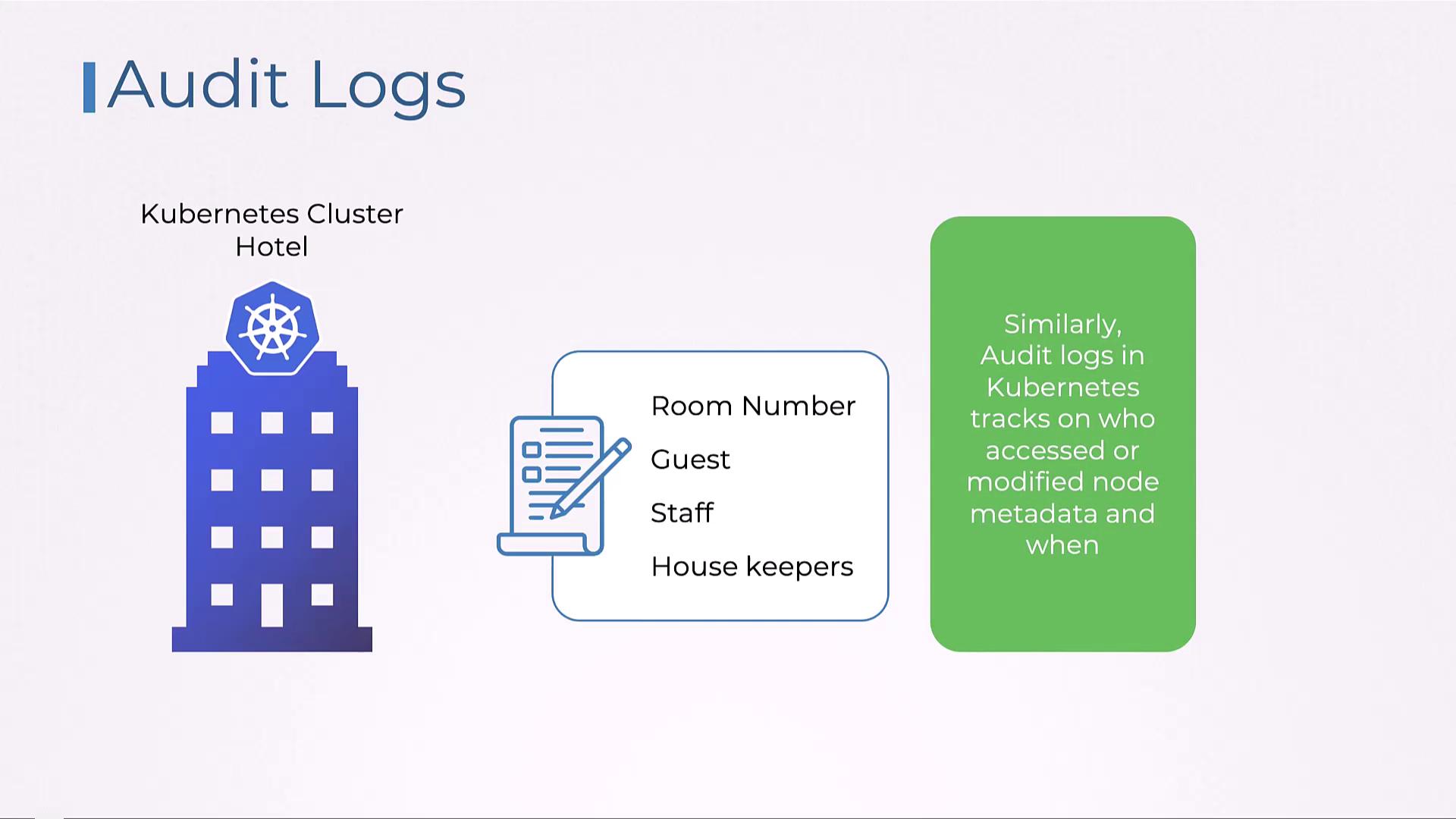
Audit logs in a hotel capture details about which room was accessed, by whom, and at what time. Similarly, Kubernetes maintains comprehensive audit logs to track access and modifications to node metadata, providing a detailed record that is essential for security monitoring and compliance.
Keeping security measures up-to-date is critical. Just like hotels upgrade their locks, cameras, and security systems regularly, Kubernetes nodes require systematic updates and patches. This ongoing maintenance helps to identify and mitigate vulnerabilities in a timely manner.
By understanding these analogies, you can better appreciate how protection strategies in Kubernetes work collectively to secure your environment, manage access robustly, and ensure workload integrity.
For additional information on Kubernetes security best practices, visit the Kubernetes Documentation.
Watch Video
Watch video content
Practice Lab
Practice lab