Before you dive into this course, please note that the CKS exam requires you to be a Certified Kubernetes Administrator (CKA). If you haven’t completed that course or need to strengthen your foundational skills, consider starting with our beginner courses such as Kubernetes for the Absolute Beginners - Hands-on Tutorial, Docker Training Course for the Absolute Beginner, or DevOps Pre-Requisite Course.
Course Structure and Key Topics
This course is meticulously structured to align with the CKS exam objectives, emphasizing both theoretical knowledge and practical security measures through real-world scenarios.1. Exploring the Kubernetes Attack Surface
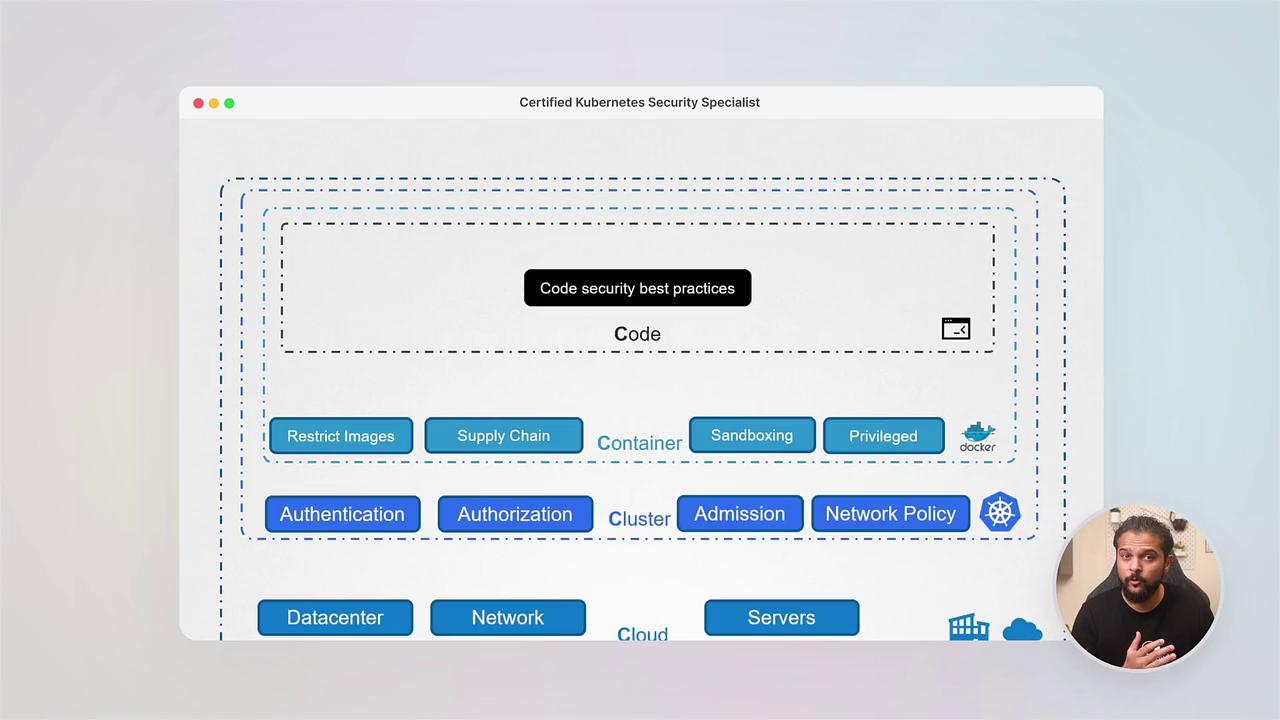
We begin by examining how various components of Kubernetes clusters can be exploited. This section introduces the four C’s of cloud-native security: cloud, clusters, containers, and code—providing a narrative that sets the stage for deeper exploration into security challenges.2. Hardening Your Kubernetes Cluster
In this segment, you will discover essential strategies to secure your Kubernetes clusters, including:- Implementing CIS Benchmarks
- Configuring authentication and authorization
- Managing Service Accounts
- Utilizing TLS certificates
- Securing the Kubernetes dashboard
- Enforcing network policies
- Conducting secure cluster upgrades
3. Securing the Underlying System
Securing the host system is as important as securing Kubernetes itself. This section covers methods such as:- Minimizing the operating system footprint
- Implementing SSH hardening and access controls
- Restricting kernel modules and open ports
- Using firewalls and Seccomp for system call restrictions
- Leveraging tools like AppArmor for additional protection
4. Reducing Vulnerabilities in Microservices
This section outlines techniques to protect microservices, including:- Managing Admission Controllers
- Implementing Pod Security Standards
- Utilizing policy engines such as the Open Policy Agent (OPA)
- Securing secrets and runtime sandboxes
- Applying mTLS for pod-to-pod encryption
5. Securing the Software Supply Chain
Securing your software supply chain is critical for maintaining a robust security posture. In this module, you will learn best practices such as:- Minimizing base image sizes
- Scanning container images for vulnerabilities
- Validating and signing deployments
6. Runtime Security
The final section is dedicated to runtime security, focusing on behavioral analytics and threat detection. You will explore tools like Falco that help establish a defense-in-depth strategy through monitoring and activity logging.Hands-On Labs, Examples, and Exam Preparation
Every module of this course includes comprehensive hands-on labs and real-world examples to bolster your practical skills. The course concludes with a realistic mock exam designed to build your confidence and ensure you are exam-ready. Since the CKS exam is hands-on and permits referencing the official Kubernetes documentation, we also teach you how to navigate these resources efficiently to quickly locate critical information during the exam.KodeKloud is a CNCF Silver member, a Certified Kubernetes Training Partner, and a CNCF Endorsed Content Provider. This certification is a significant milestone in your journey to become a true “KubeAstronaut.”