Understanding Node Metadata Through an Analogy
Imagine a Kubernetes cluster as a hotel. Each room in the hotel represents a node, and just like rooms possess various details (room type, occupancy, service notes), nodes have associated metadata. This metadata includes essential attributes such as the node’s unique identity, configuration details, and operational status. In Kubernetes, node metadata is broken down into several components:- Node Name/Unique ID: The unique identifier for each node.
- Labels: Key-value pairs used to group nodes, such as by geographic region.
- Annotations: Additional data used for debugging, logging, or monitoring.
- Architecture: Information on the hardware architecture (e.g., x86-64).
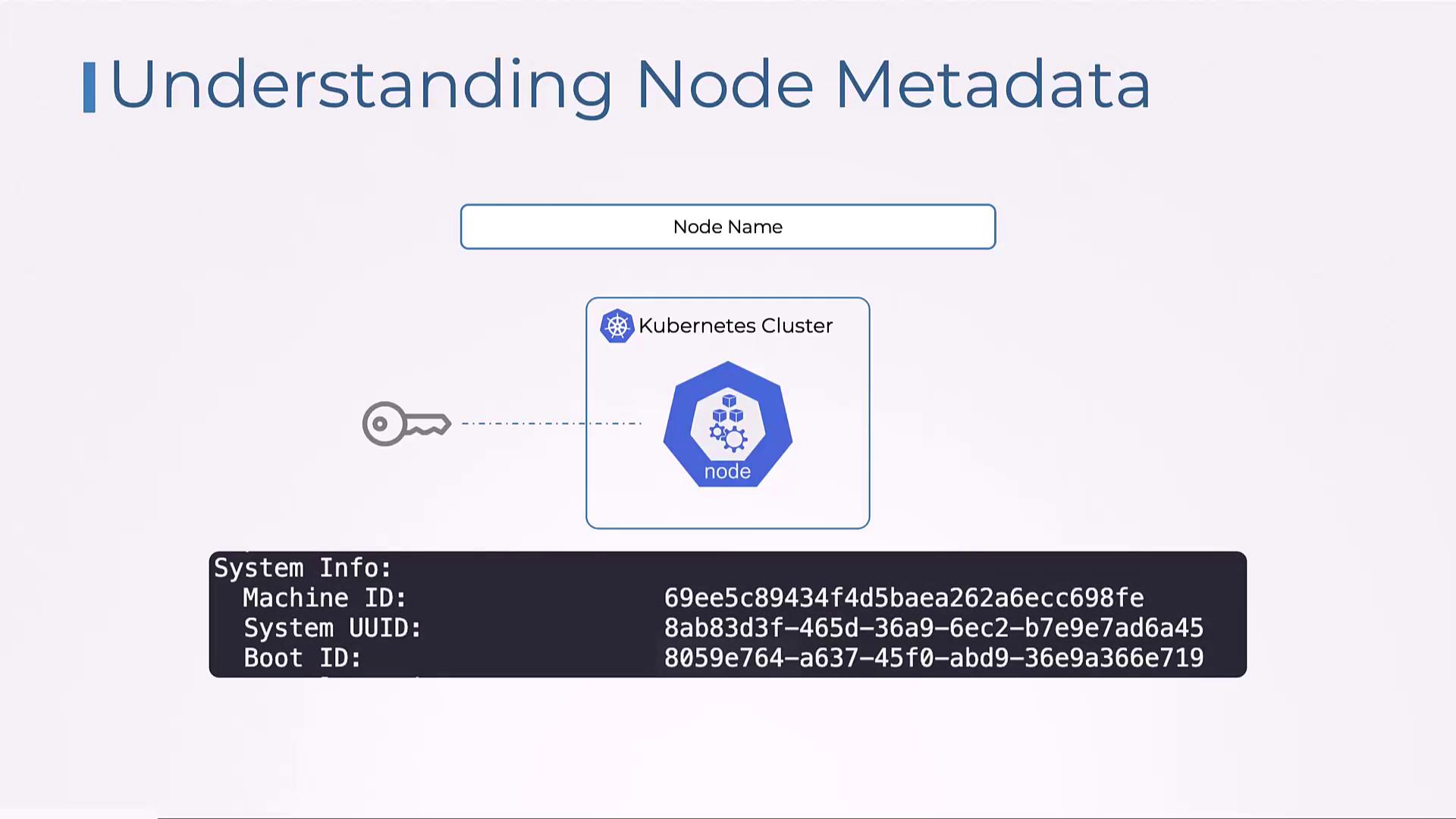
- System Info: Detailed system data including machine ID, system UUID, boot ID, kernel version, OS details, container runtime version, and Kubernetes component versions.
- Addresses: Lists internal and external IP addresses.
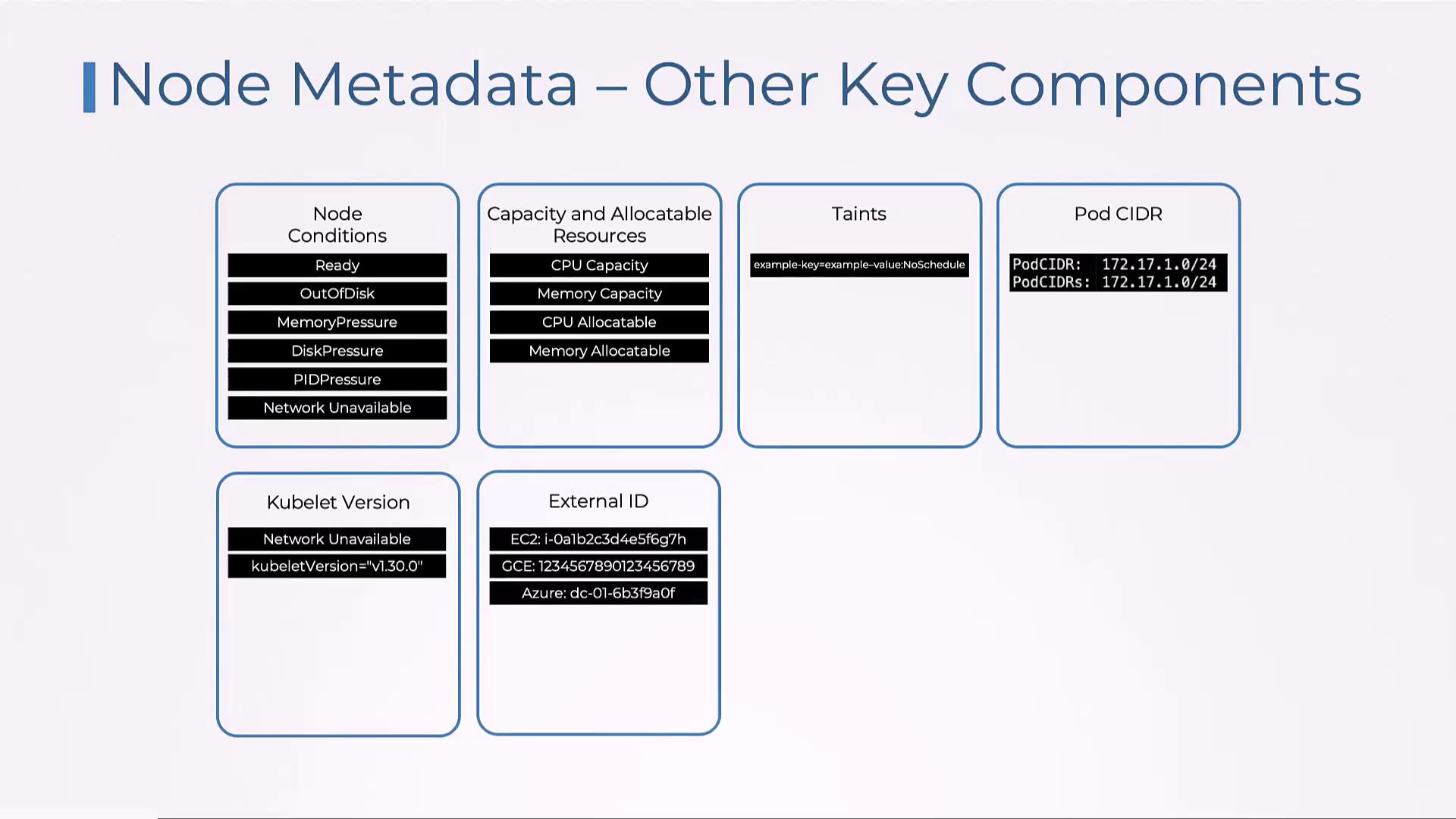
- Other Key Components: Node conditions (e.g., Ready, OutOfDisk), resource capacities, taints and tolerations, CIDRs, kubelet version, and cloud-provider-specific IDs.
Node metadata not only helps in managing the Kubernetes cluster effectively but also plays a critical role in securing your infrastructure.
Detailed Breakdown of Node Metadata
The diagram below illustrates some of the metadata components associated with a Kubernetes node:
Node Components
- Node Name: The unique identifier for a node.
- Labels: Used to categorize nodes. For example, labels can group nodes by region in a cloud environment. An example of node labels:
- Annotations: These provide additional context for debugging, logging, and monitoring. For instance, the networking tool Flannel uses annotations for its internal configuration:
- Architecture: Indicates the underlying hardware, such as x86-64.
- System Info: Detailed information about the node’s system including operating system, kernel version, container runtime, and more. For example:
- Addresses: Each node has both internal and external IP addresses.
- Other Details: These include node conditions (such as Ready, OutOfDisk, MemoryPressure), resource capacities, configured taints and tolerations, pod CIDRs, kubelet version, and cloud provider-specific external IDs.
Securing node metadata is a critical step in safeguarding your Kubernetes environment. Ensure that you follow best practices to restrict access and monitor metadata for any unauthorized modifications.