
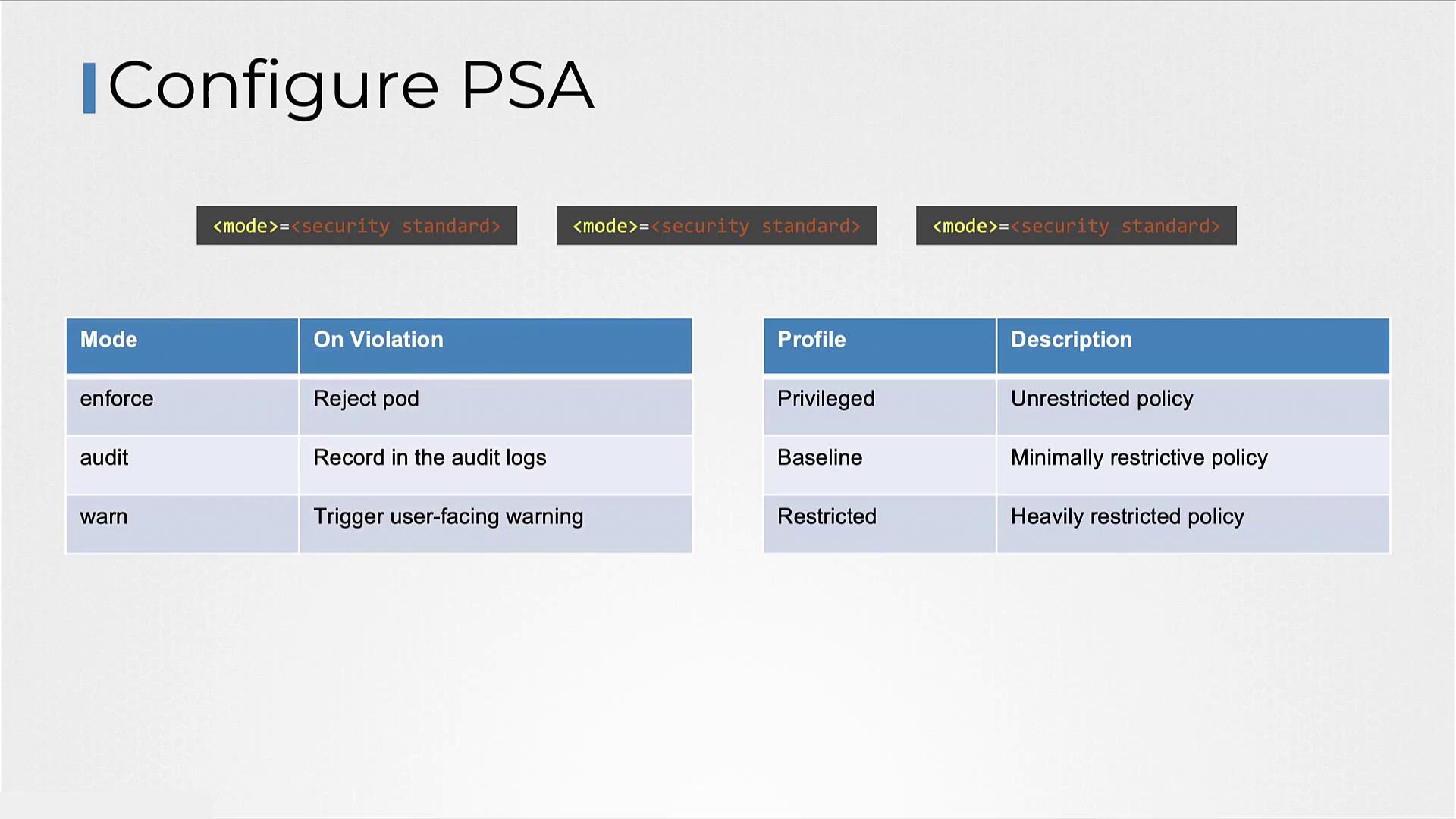
There are three built-in profiles provided by the Pod Security Standards:
- Privileged: Offers nearly no restrictions, allowing extensive permissions and potential privilege escalation.
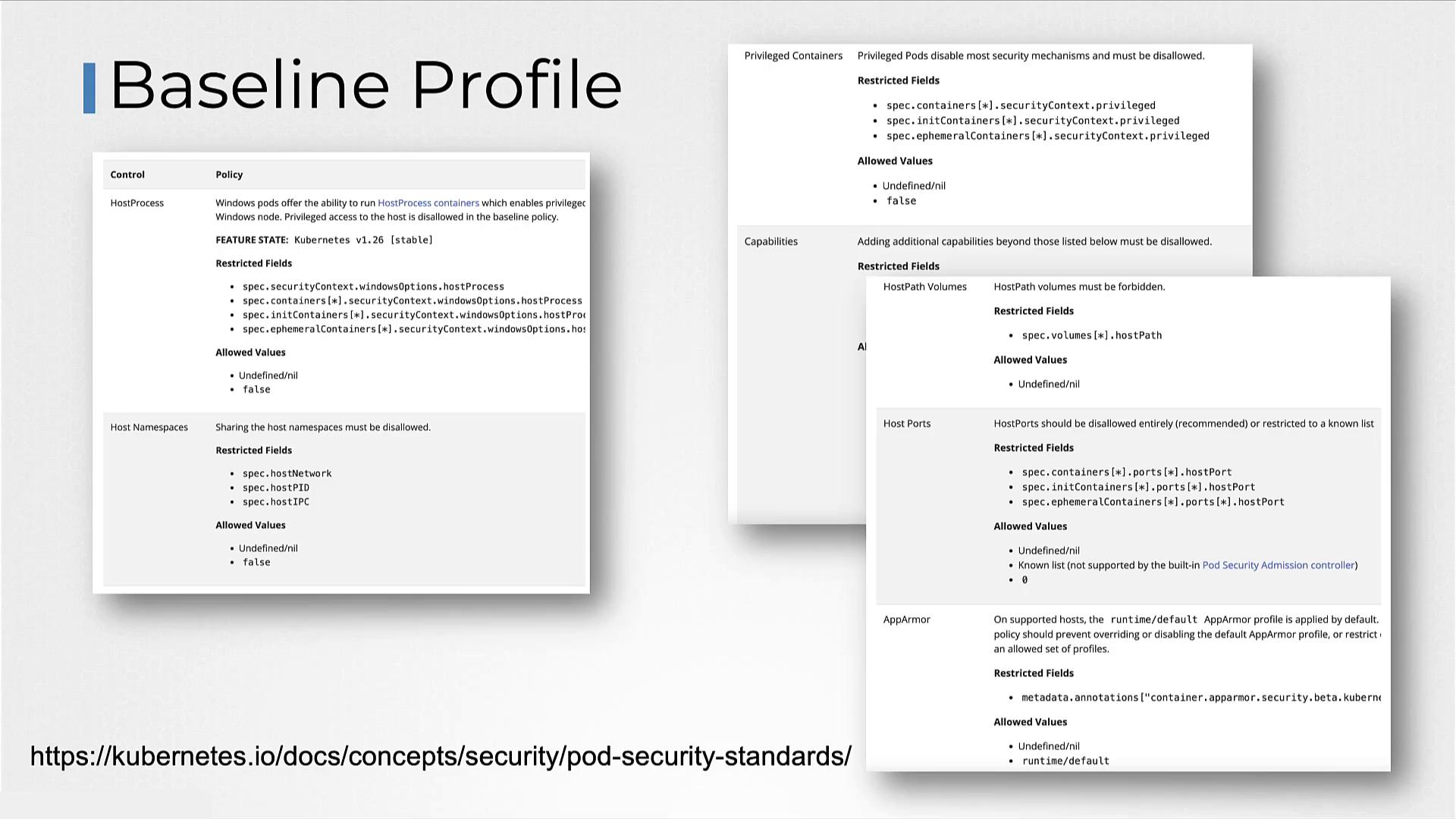
- Baseline: Balances security and functionality by preventing unauthorized privilege escalation while supporting most containerized applications.
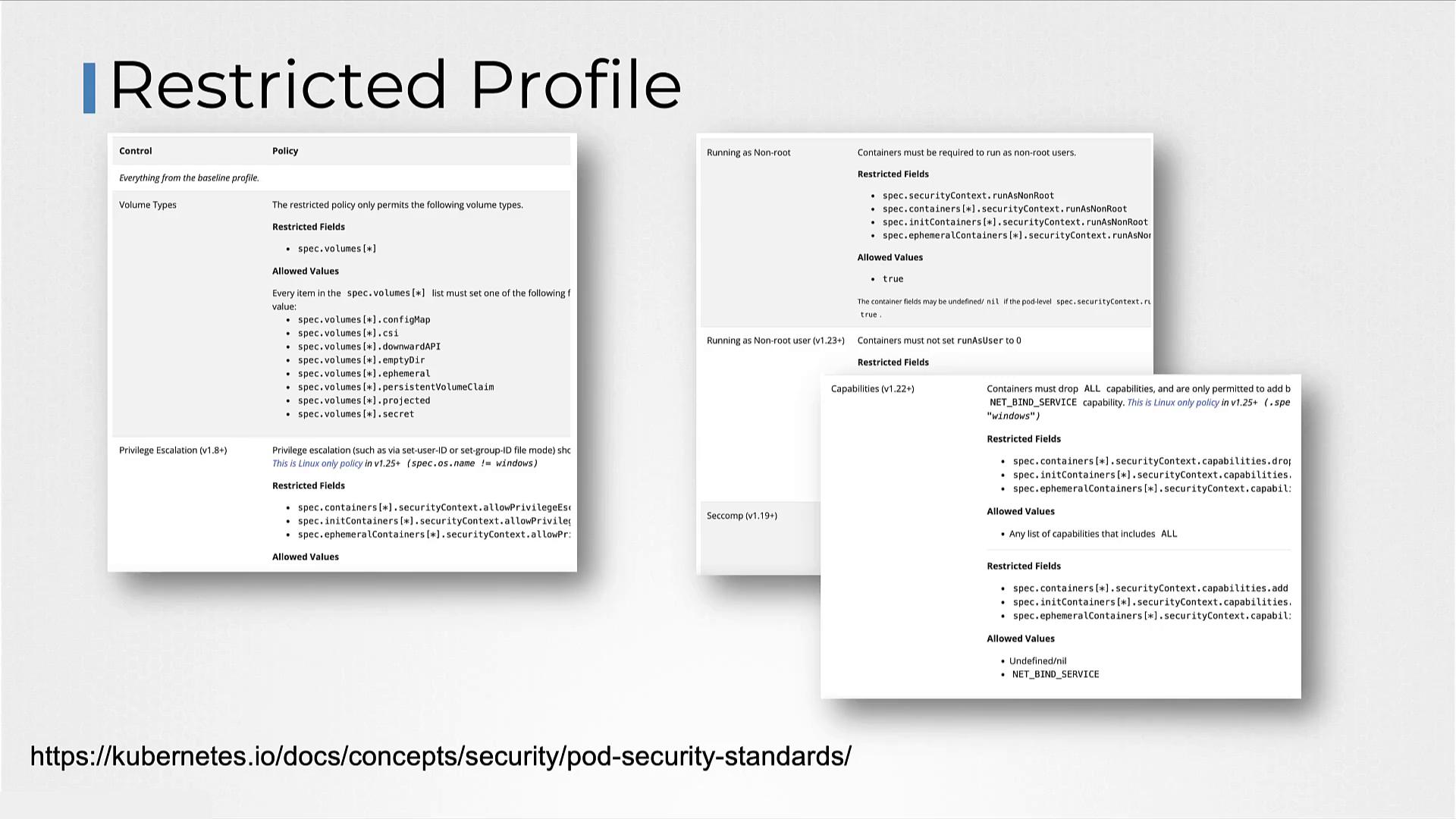
- Restricted: Implements strict security measures based on pod hardening best practices, ensuring high security at the cost of potential compatibility challenges.
- enforce: Rejects pod creation requests that do not comply with the specified policy.
- audit: Allows pod creation but logs the policy violation in the audit logs.
- warn: Permits pod creation and issues a warning to the user regarding the policy violation.
| Namespace | Mode | Profile | Description |
|---|---|---|---|
| payroll | enforce | restricted | Pods must strictly adhere to the restricted policy. |
| hr | enforce | baseline | Pods are expected to follow baseline security practices. |
| dev | warn | restricted | Pods receive warnings if they do not comply with the restricted policy. |
We encourage you to experiment with Pod Security Admission and Pod Security Standards to better understand how they enhance security in Kubernetes clusters. For additional information, visit the Kubernetes Documentation.