Certified Kubernetes Security Specialist (CKS)
Supply Chain Security
Introduction to KubeLinter
In this lesson, we explore KubeLinter—an essential tool that enhances your Kubernetes deployments by identifying configuration issues and ensuring adherence to best practices. KubeLinter scrutinizes your manifest files, highlighting potential risks and offering guidance to improve security, efficiency, and reliability.
Below is a sample Kubernetes deployment manifest used to deploy an application named "myapp" with the image my-app-image:latest. Note that this example contains several common misconfigurations:
- It deploys only a single replica, which eliminates redundancy.
- It uses the "latest" tag for the image, which is discouraged in production environments.
- It lacks recommended configurations such as resource requests, resource limits, security contexts, and liveness/readiness probes.
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app
spec:
replicas: 1
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
containers:
- name: app-container
image: my-app-image:latest
ports:
- containerPort: 8080
KubeLinter helps you address these issues through automated checks and tailored recommendations. Its capabilities include:
- Suggesting the addition of liveness and readiness probes when missing.
- Flagging deployments that use only a single replica.
- Recommending the inclusion of necessary security contexts.
- Enforcing rules that disallow the use of the "latest" tag for container images.
- Validating resource definitions by ensuring proper requests and limits.
All of these checks are configurable, empowering you to enforce custom policies that align with your organization's security and operational standards. After analyzing your Kubernetes manifest files based on these policies, KubeLinter generates a comprehensive report with actionable recommendations.
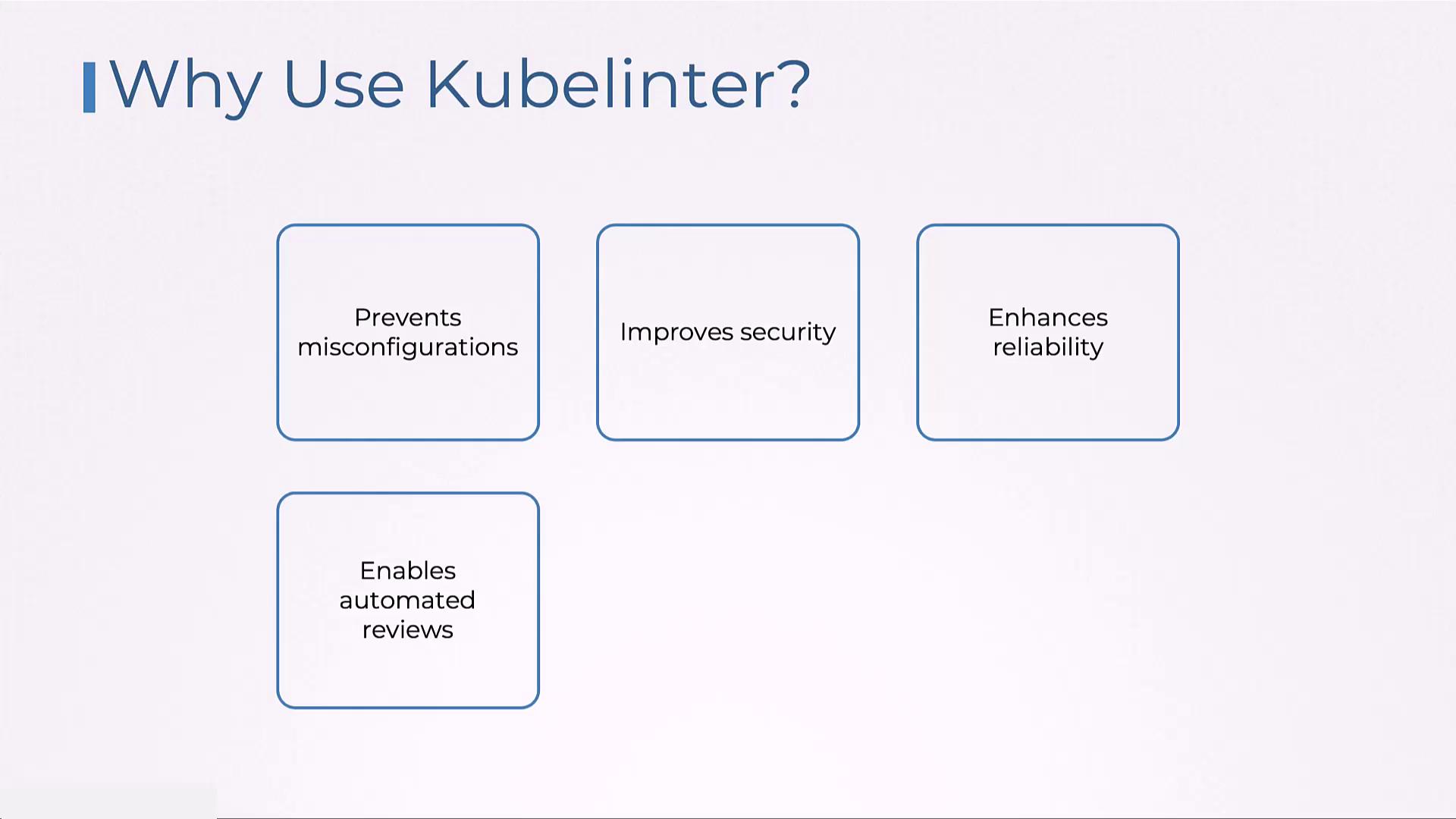
Key Benefits
• Prevents misconfigurations
• Enhances security through customizable rules
• Improves the reliability of your Kubernetes deployments
• Automates reviews, helping to achieve cost efficiency and compliance
Installation and Basic Usage
Start by downloading and installing KubeLinter from the official repository with the following commands:
curl -Lo kube-linter.tar.gz \
https://github.com/stackrox/kube-linter/releases/download/0.2.3/kube-linter-linux-amd64.tar.gz
tar -xzf kube-linter.tar.gz
sudo mv kube-linter /usr/local/bin/
After installation, navigate to the directory containing your Kubernetes configuration files, and run KubeLinter to analyze them:
cd path/to/k8s-configs
kube-linter lint .
KubeLinter then audits your configurations and flags any detected issues with detailed report outputs.
Integration with CI/CD Pipelines
Embedding KubeLinter within your CI/CD pipeline ensures that Kubernetes manifests meet security and best practices before deployment. Whether you use Jenkins, GitHub Actions, or any similar platform, integrating KubeLinter helps catch mistakes early on.
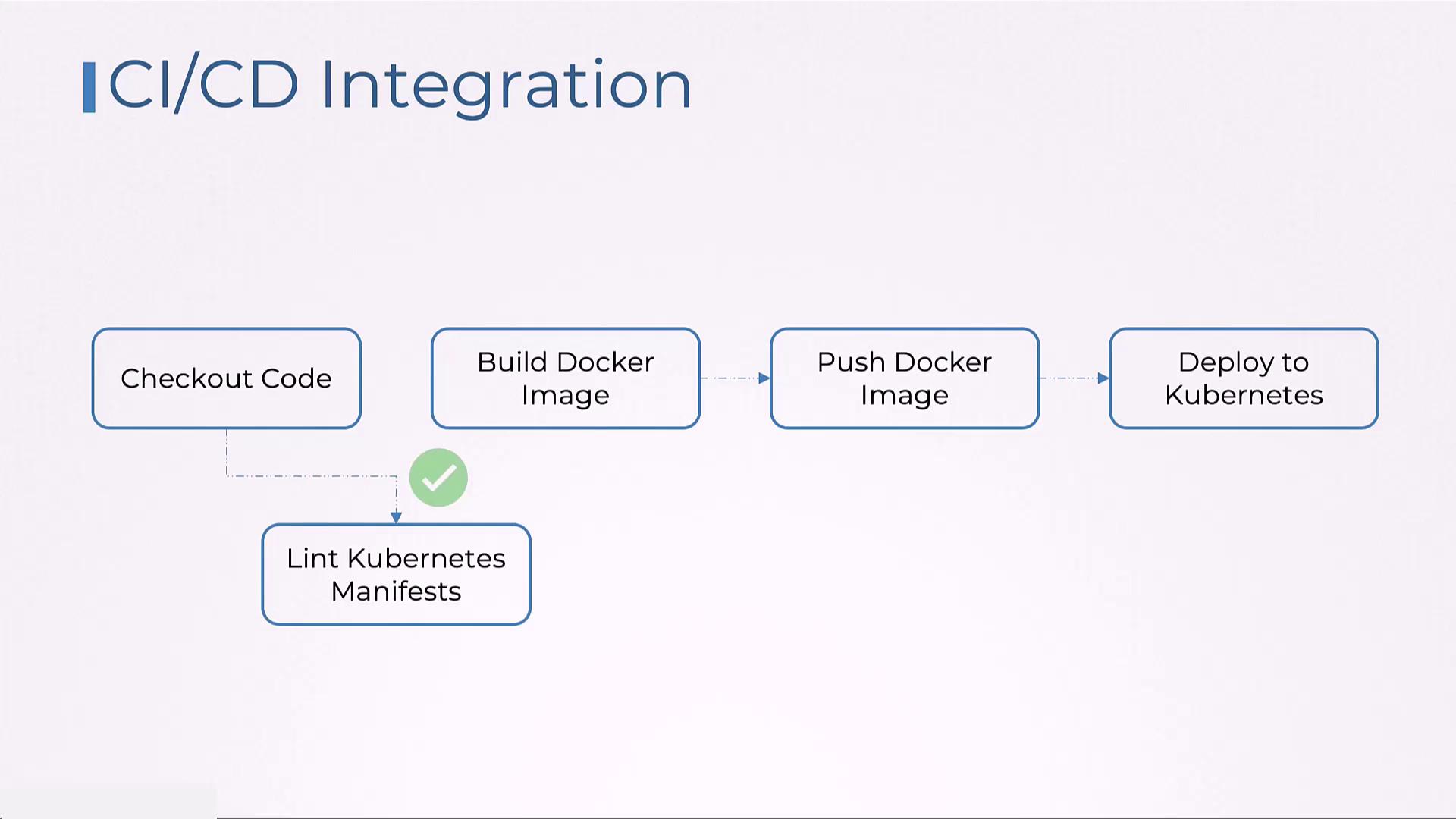
Here’s how the typical process works:
- Check out the code from your repository.
- Run KubeLinter to lint your Kubernetes configurations.
- Build Docker images and proceed with subsequent CI/CD tasks if linting passes.
- Publish test results and issue notifications if problems are detected.
Jenkins Integration
The following Jenkins pipeline example demonstrates how to incorporate KubeLinter into your CI/CD process:
stages {
stage('Checkout') {
steps {
checkout scm
}
}
stage('Install KubeLinter') {
steps {
sh 'curl -sSfL https://raw.githubusercontent.com/stackrox/kubelinter/main/scripts/install.sh | sh -'
}
}
stage('Lint Kubernetes Manifests') {
steps {
sh 'kube-linter lint .'
}
}
}
GitHub Actions Integration
Below is an example GitHub Actions configuration for running KubeLinter:
name: Lint Kubernetes Manifests
on: [push]
jobs:
lint:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Run KubeLinter
run: kube-linter lint .
Integrating KubeLinter into your CI/CD workflow guarantees that your Kubernetes configurations undergo thorough validation before deployment, reducing misconfigurations and enhancing your clusters' overall security and stability.
For further details and advanced configuration options, refer to the KubeLinter documentation.
Watch Video
Watch video content
Practice Lab
Practice lab