
-
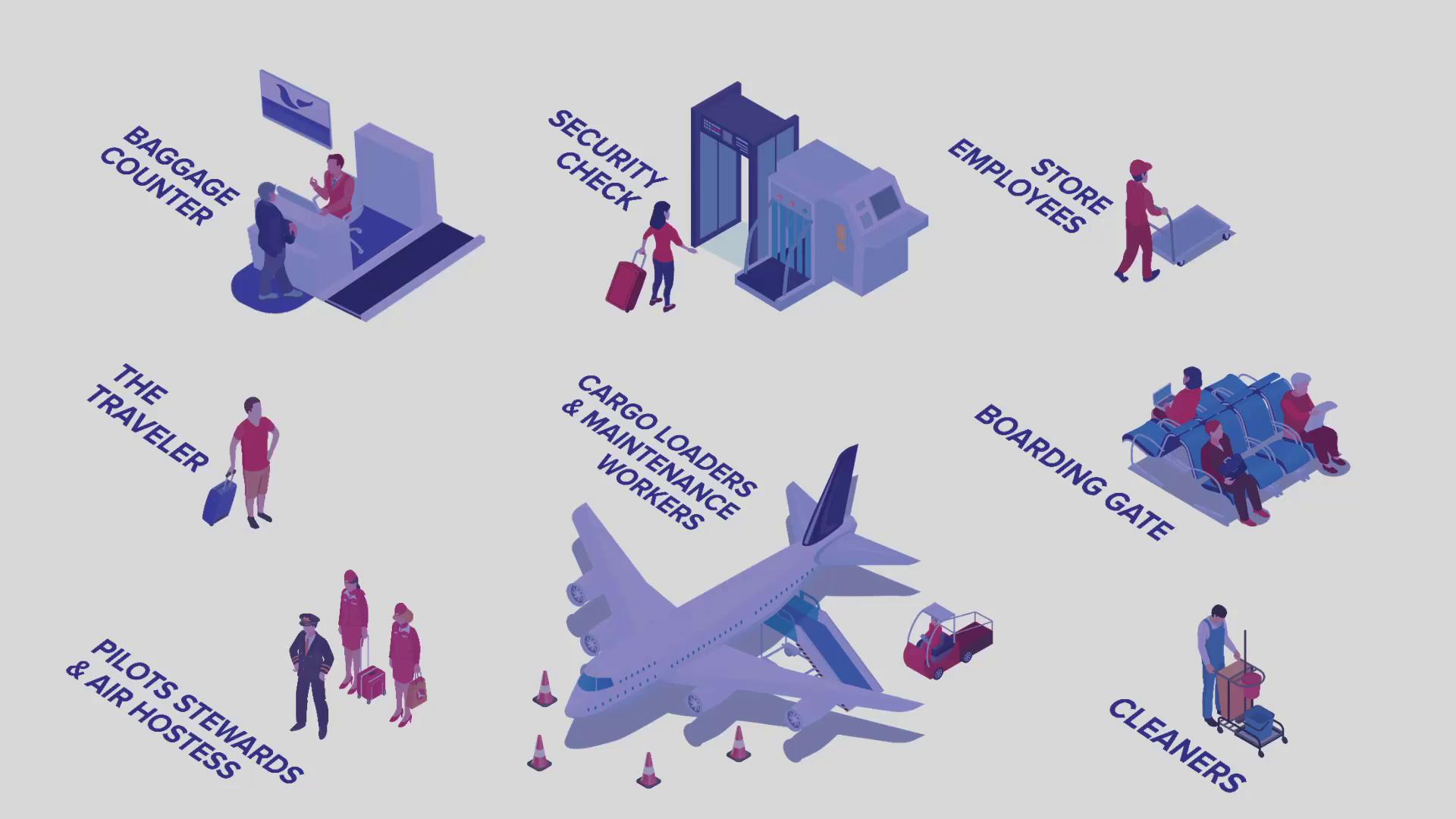
Baggage Drop-off:
At the check-in counter, you can only check in if your flight departs within a few hours. Luggage is dropped off at the specific airline’s counter, where an attendant verifies your valid ticket before you proceed further. -
Immigration Check:
An immigration officer checks your travel documents, and any lapse in valid documentation results in denied access. -
Security Screening:
During security, any prohibited or hazardous items in your carry-on must be discarded. -
Navigating the Departure Hall:
You then move through the departure hall to your boarding gate. Public areas and duty-free shops are accessible, but boarding is allowed only at the designated gate. Sensitive areas such as cargo bays and runways remain strictly off-limits.
- Traveler: Accesses public spaces after check-in and boards only at the designated gate.
- Baggage Counter Employees: Handle traveler and airline-specific information for check-in processes.
- Security Officers: Inspect belongings in the security area while also accessing some public spaces.
- Store Employees: Operate within public areas and may have extended access to backroom operations.
- Boarding Gate Staff: Assist travelers in boarding, similar to baggage counter staff.
- Cleaning Staff: Access designated areas, with some having permission for restricted zones such as terminals or cargo drop-off areas.
- Cargo Loaders and Maintenance Workers: Have access similar to cleaning staff and also unrestricted areas like the loading bay.
- Pilots, Stewards, and Flight Attendants: Possess specialized access to restricted zones, such as cockpits and specific aircraft-related areas, limited to their airline’s operations.
Applying the principle of least privilege means granting every role only the access they need, reducing potential risks and improving overall security.
| Security Measure | Description |
|---|---|
| Limit Node Access | Ensure nodes have restricted user permissions to prevent unauthorized modifications. |
| Role-Based Access Control (RBAC) | Define precise access rights for users and services within the cluster. |
| Remove Obsolete Packages | Keep systems updated by removing software that is no longer required. |
| Restrict Network Access | Limit network communication between components to reduce attack surfaces. |
| Restrict Kernel Modules | Load only essential kernel modules and block unnecessary ones. |
| Fix Open Ports | Identify and secure any open ports to prevent unauthorized entry points. |

- Only the required software is installed on the host.
- Unnecessary services do not expose the nodes.
- Unused kernel modules are not loaded after boot.
- Any open ports are identified and promptly secured.
In upcoming articles, we will delve deeper into securing Kubernetes environments, exploring how to fortify nodes, enforce RBAC, and apply additional security best practices.