Certified Kubernetes Security Specialist (CKS)
System Hardening
Minimize IAM roles
In this lesson, we explore how to implement the principle of least privilege using Identity and Access Management (IAM) on public cloud platforms like AWS. The "least privilege" strategy ensures that each user or service has only the necessary permissions to perform its tasks, thereby reducing the risk of unauthorized access.
Understanding Root and IAM User Roles
Earlier, we discussed the different types of accounts in Linux and why using a root user for daily operations is not advisable. Similarly, in public cloud platforms like AWS, the root account created during signup holds full administrative privileges. Although you initially access the AWS Management Console using the email associated with the root account, it's best practice to use this account only to create new IAM users and assign them the appropriate permissions. Once new IAM user accounts are set up, the root credentials should be securely stored and used only when absolutely necessary.
Note
Avoid using the root account for everyday tasks. Instead, delegate responsibilities using IAM users and groups to enforce the principle of least privilege.
Example: AWS Account Setup
Consider a scenario where a user named Mark ([email protected]) creates a new AWS account. Initially, Mark signs in using his root credentials, which grants him full administrative privileges. To secure his environment, Mark should create individual IAM users for team members rather than relying on the root account for daily operations.
Creating IAM Users and Groups
Let's create several new IAM users: Lucy, Shiva, Abdul, and Anita.
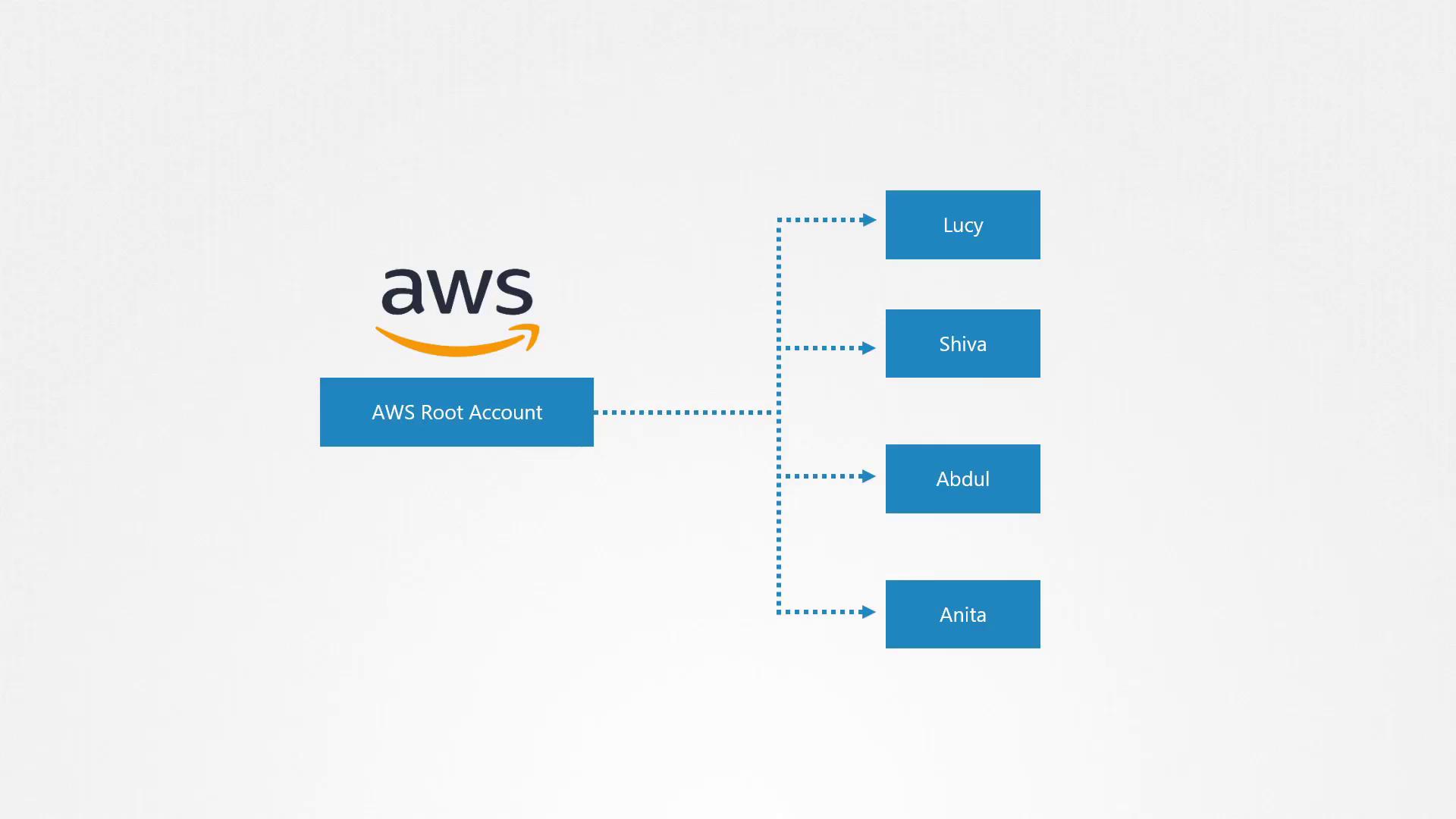
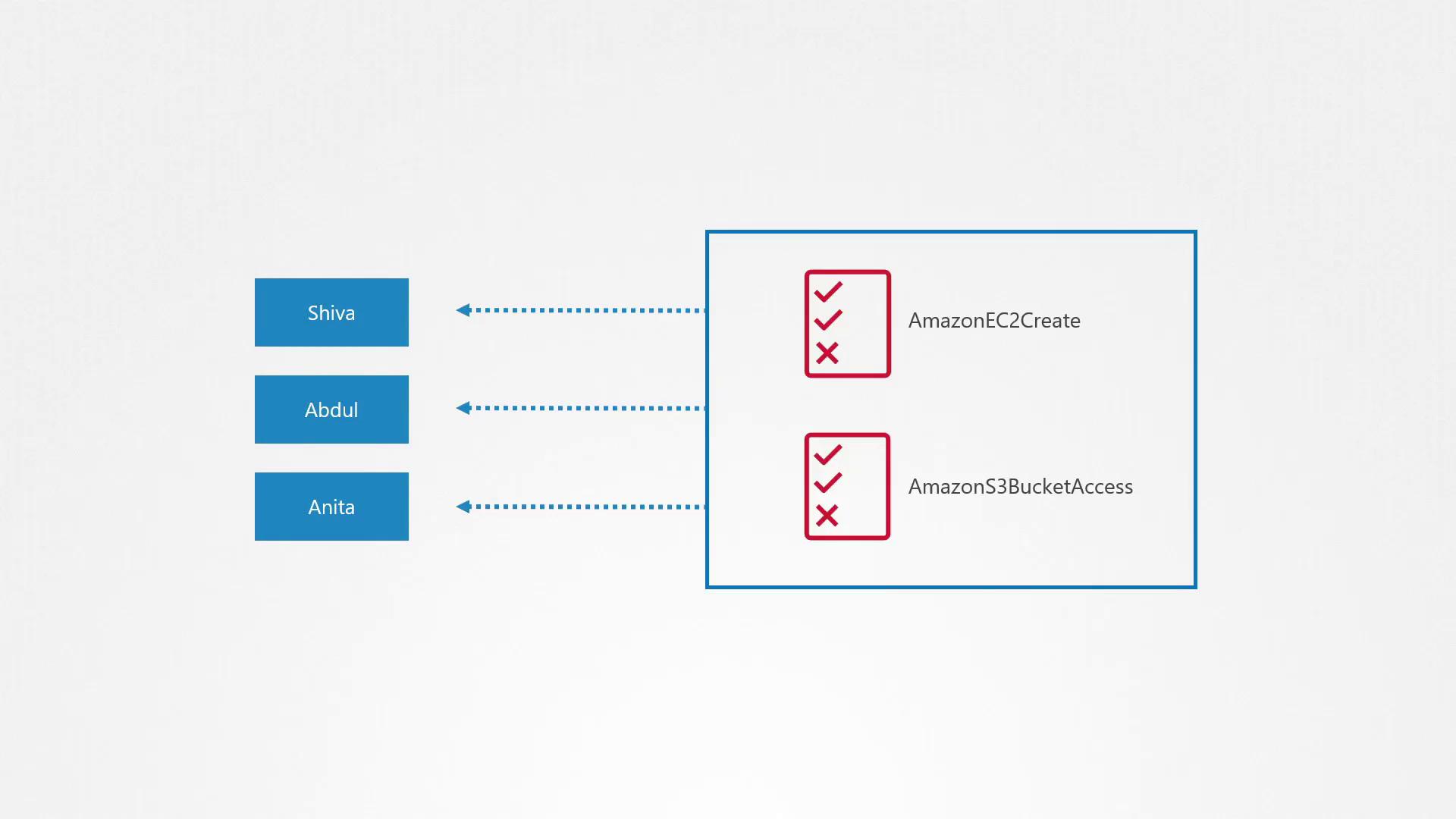
Cloud providers, by default, assign minimal permissions to new users. In AWS, a user's capabilities are determined by the permissions defined in their IAM roles. For example, if Shiva, Abdul, and Anita are developers needing to create EC2 instances and access S3 buckets, you would attach policies granting only these essential permissions.
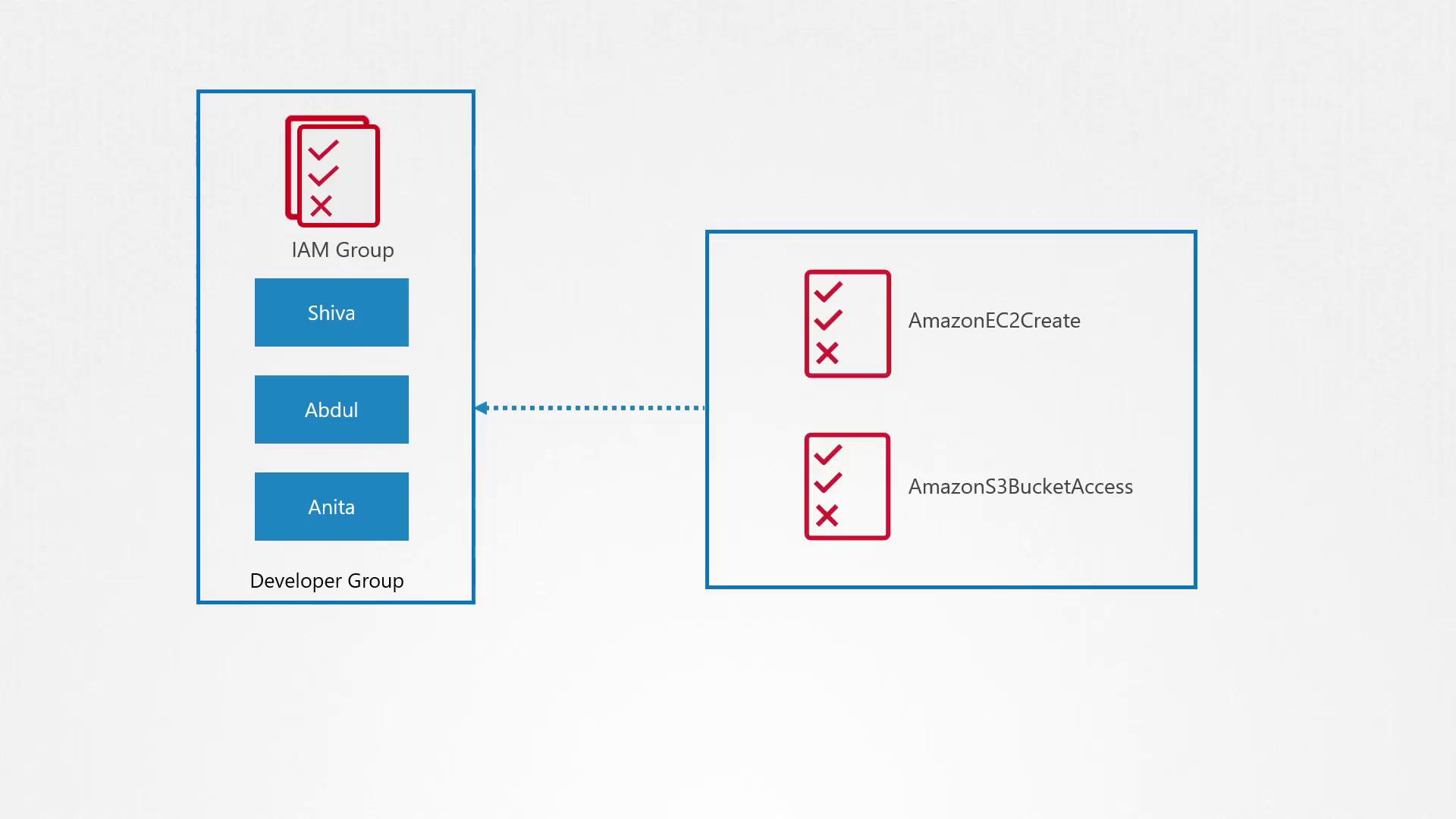
Simplifying Permissions with IAM Groups
For easier management, group users with similar roles into an IAM group. An IAM group allows you to grant the same set of permissions to multiple users by attaching policies directly to the group. For instance, create a "Developer Group" that includes Shiva, Abdul, and Anita, and attach the necessary policies for EC2 and S3 access.
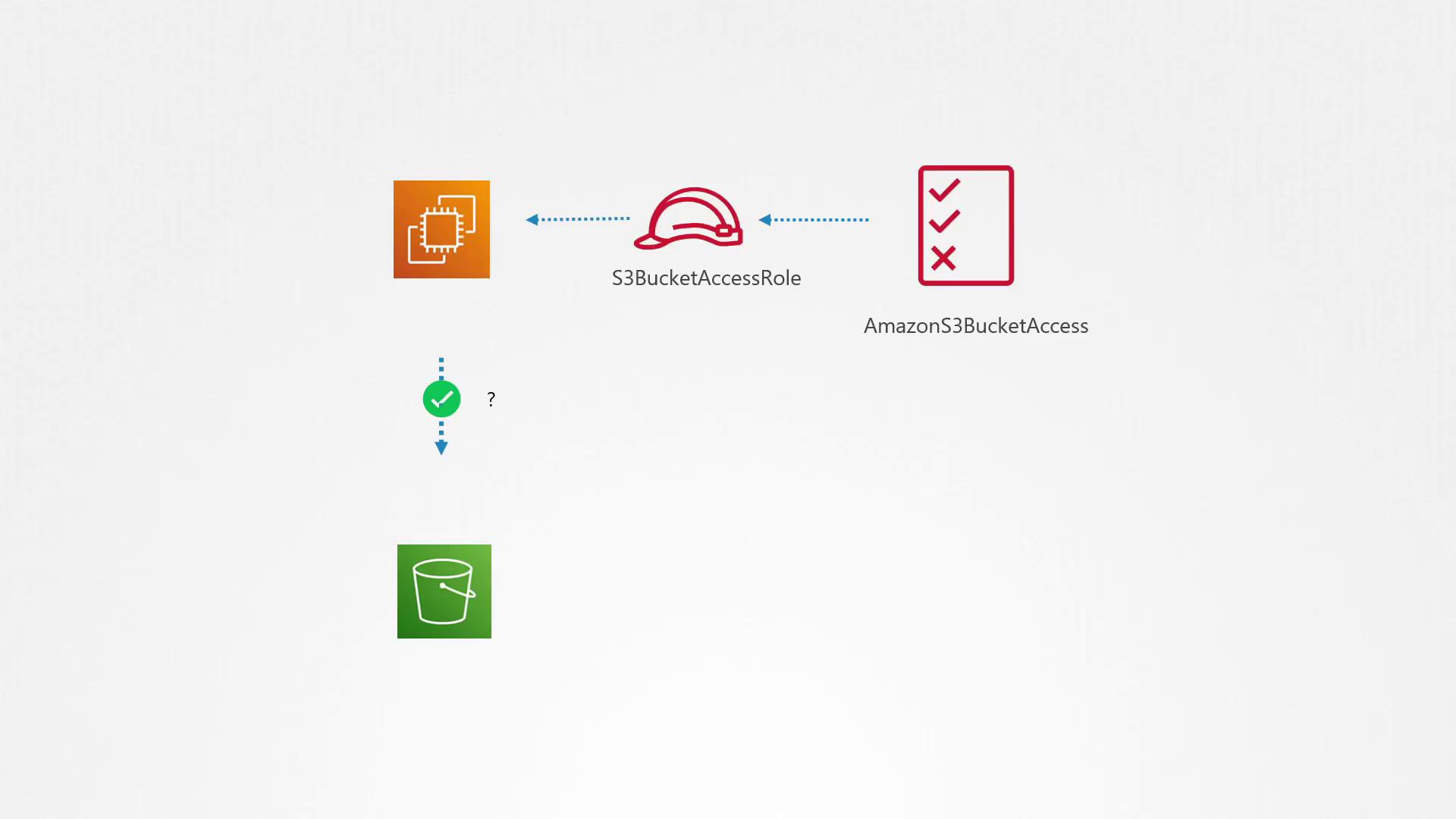
Managing Permissions for AWS Resources
Permissions management isn’t limited to human users; AWS resources also require explicit access controls. For example, an EC2 instance that needs to access S3 buckets does not have inherent permissions. To enable access, create an IAM role—such as "S3 Access Role"—and attach the same policies used for the developer group. This role should then be assigned to the EC2 instance.
It’s important to note that unlike user accounts, you cannot attach an IAM policy directly to an AWS resource. Always use IAM roles to ensure that AWS services operate with only the minimum required permissions.
Security Warning
Avoid alternative methods of granting access (like providing programmatic keys directly) as they are generally less secure. Use IAM roles to minimize risk and adhere to the principle of least privilege.
Continual Review and Auditing
Regular audits of your IAM policies and permissions are crucial to maintaining a secure environment. Periodically review and remove any unused permissions. AWS provides built-in tools like AWS Trusted Advisor for real-time security checks and recommendations. Equivalent tools include Security Command Center in Google Cloud and Azure Advisor in Microsoft Azure.
Conclusion
It is essential to understand and apply least privilege principles using IAM roles to safeguard your cloud infrastructure. While IAM details might not be the primary focus of certification exams, having a solid grasp of these concepts is beneficial.

Watch Video
Watch video content