Chaos Engineering
Introduction to Real life Application
Demo Pre requisite to Deploy Application
In this lesson, you will perform the manual steps required to install and configure an EC2 environment when Cloud9 IDE is not available. You’ll create an IAM role, launch and prepare an EC2 instance, clone repositories, configure your AWS environment, and deploy with AWS CDK.
Note
These steps mimic the Cloud9 IDE setup by granting the EC2 instance permissions via an IAM role and installing all required CLI tools, Docker, Kubernetes clients, and CDK.
1. Create an IAM Role for EC2
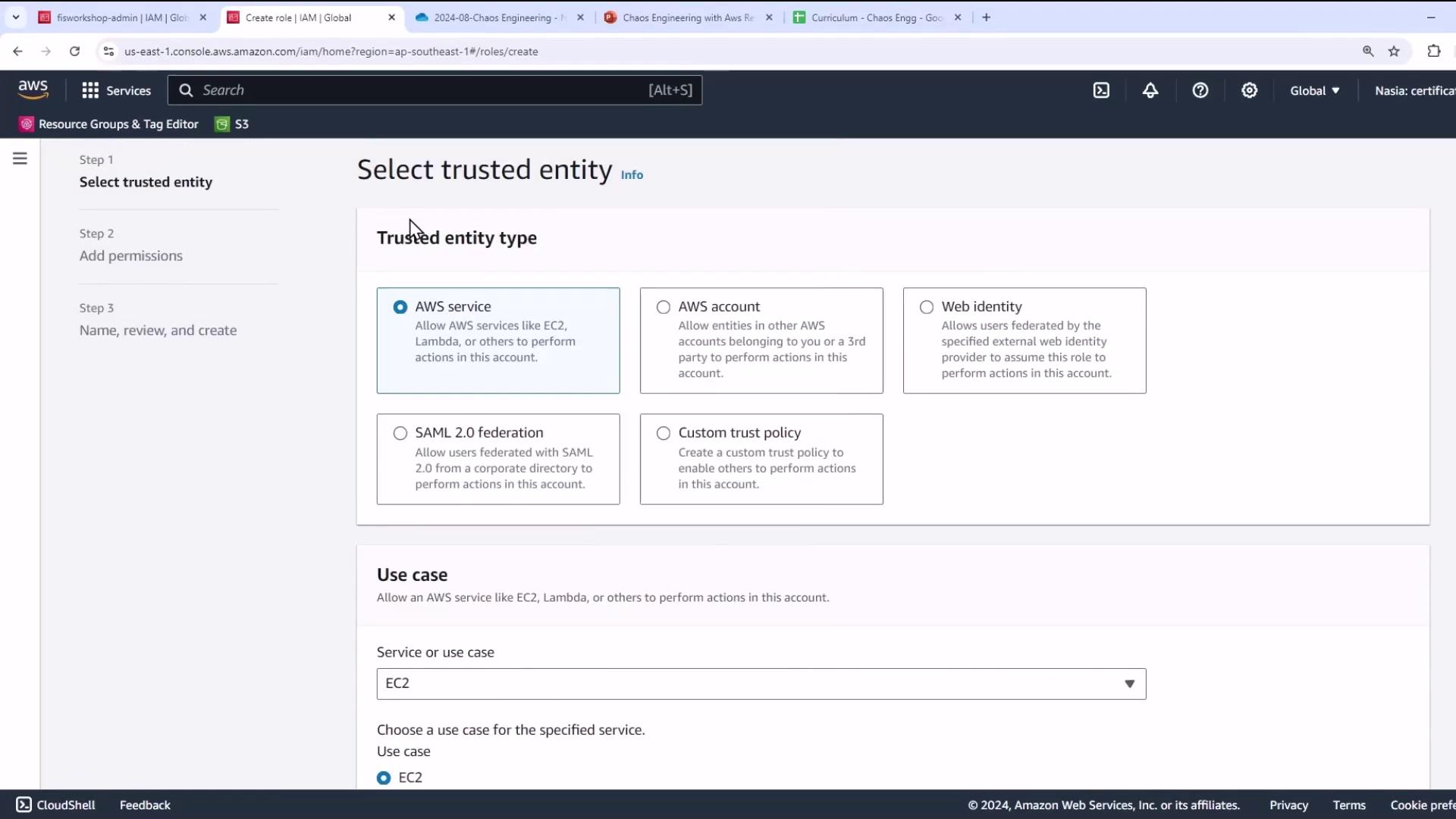
- Open the IAM console, choose Roles → Create role.
- Select AWS service and EC2 use case, then Next.
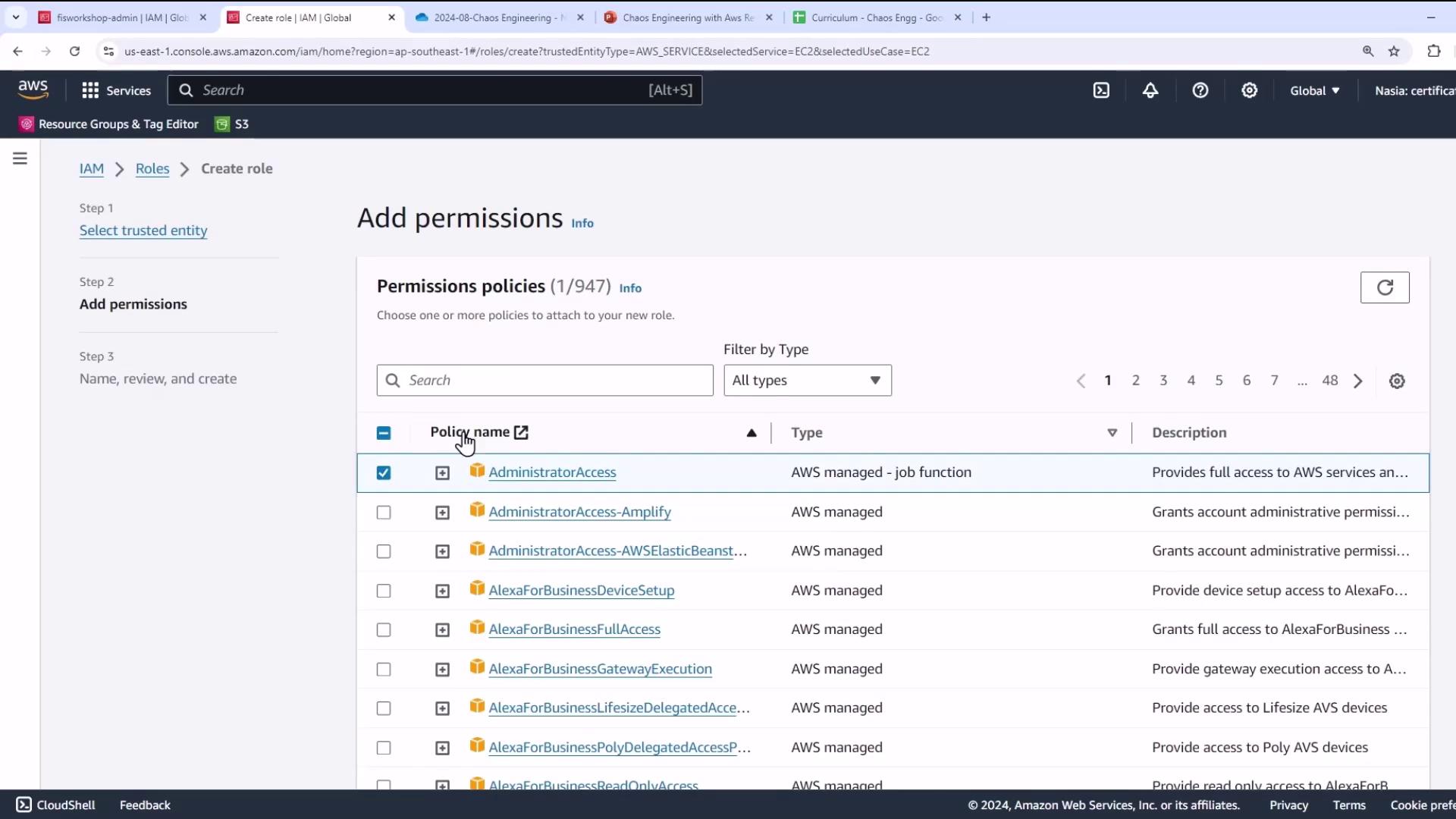
- Attach these AWS managed policies:
| Policy Name | Description |
|---|---|
| AdministratorAccess | Full administrative access |
| AmazonSSMManagedInstanceCore | Systems Manager permissions for instances |
- Use the exact trust policy and name from the GitHub repo (e.g.,
fisworkshop-admin):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
- Complete the role creation.
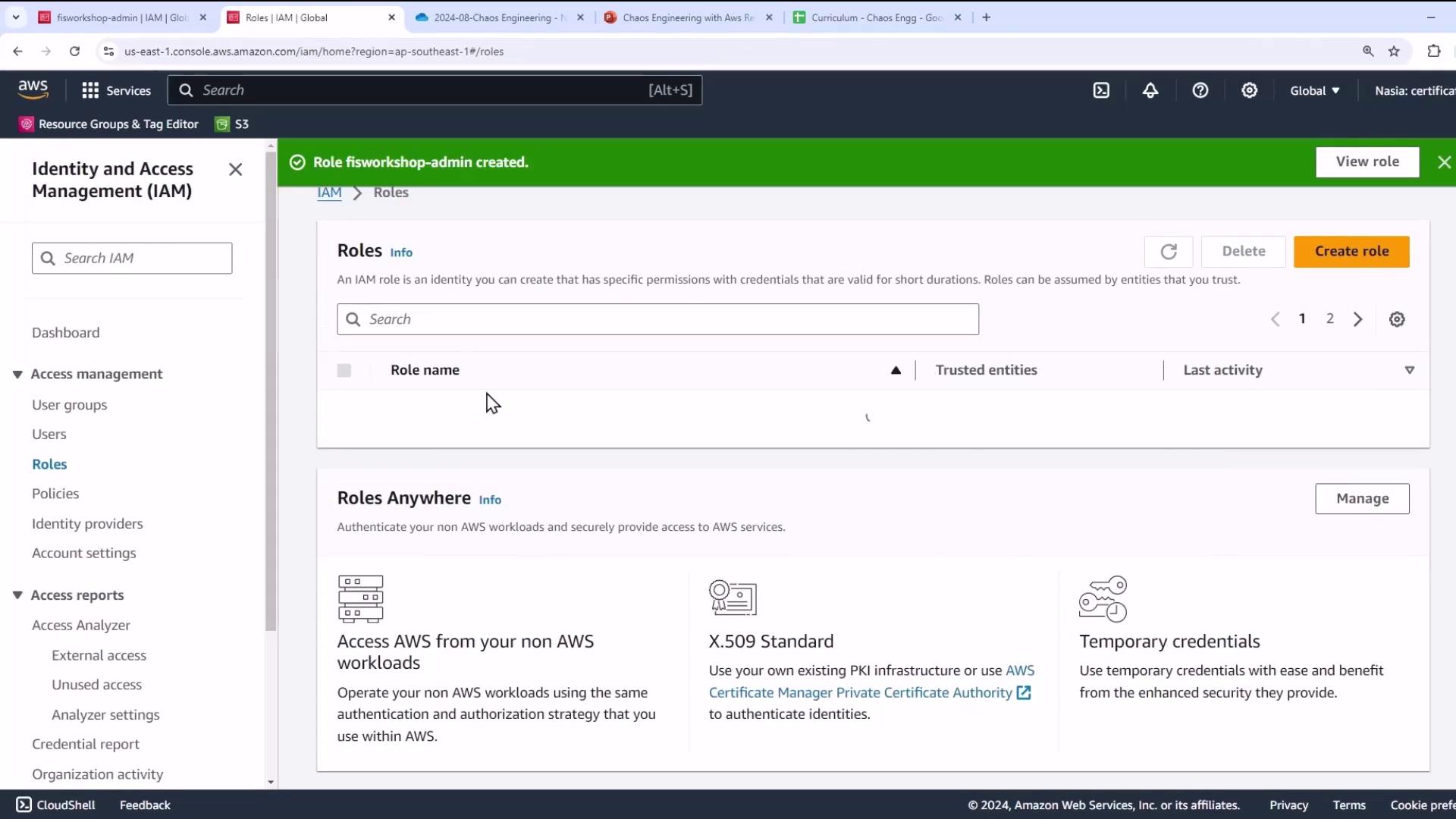
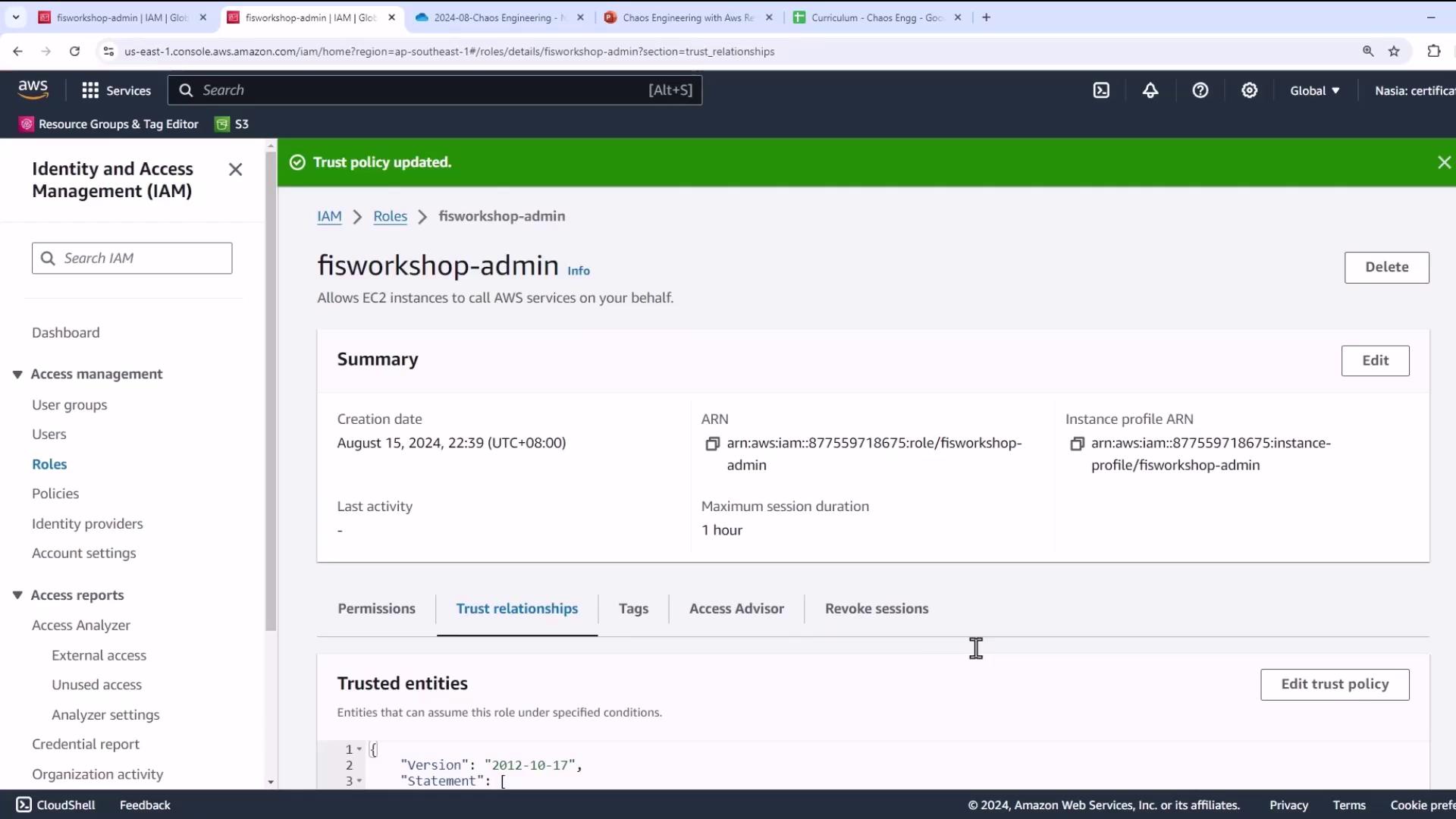
- (Optional) Verify the role’s summary and trust relationships.
2. Launch an EC2 Instance
- In the EC2 console, click Launch instance.
- Name the instance, choose Amazon Linux AMI, and select an instance type (e.g.,
m5.xlargefor CDK deployments).

- (Optional) Create or choose an SSH key pair for shell access.
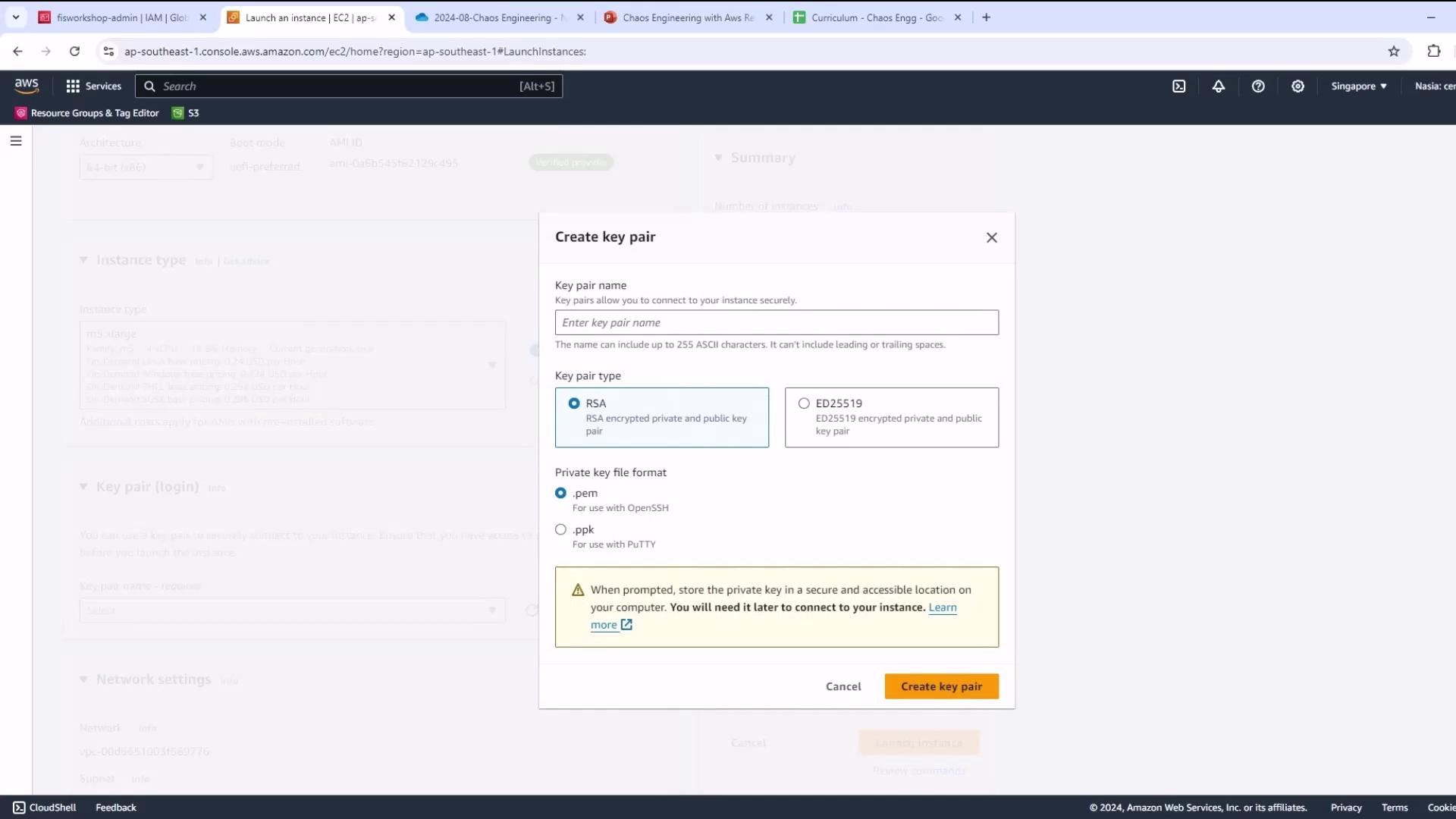
Warning
Opening SSH (port 22) to 0.0.0.0/0 is insecure. Restrict to your IP range where possible.
- Keep default VPC/subnet and allow SSH access.
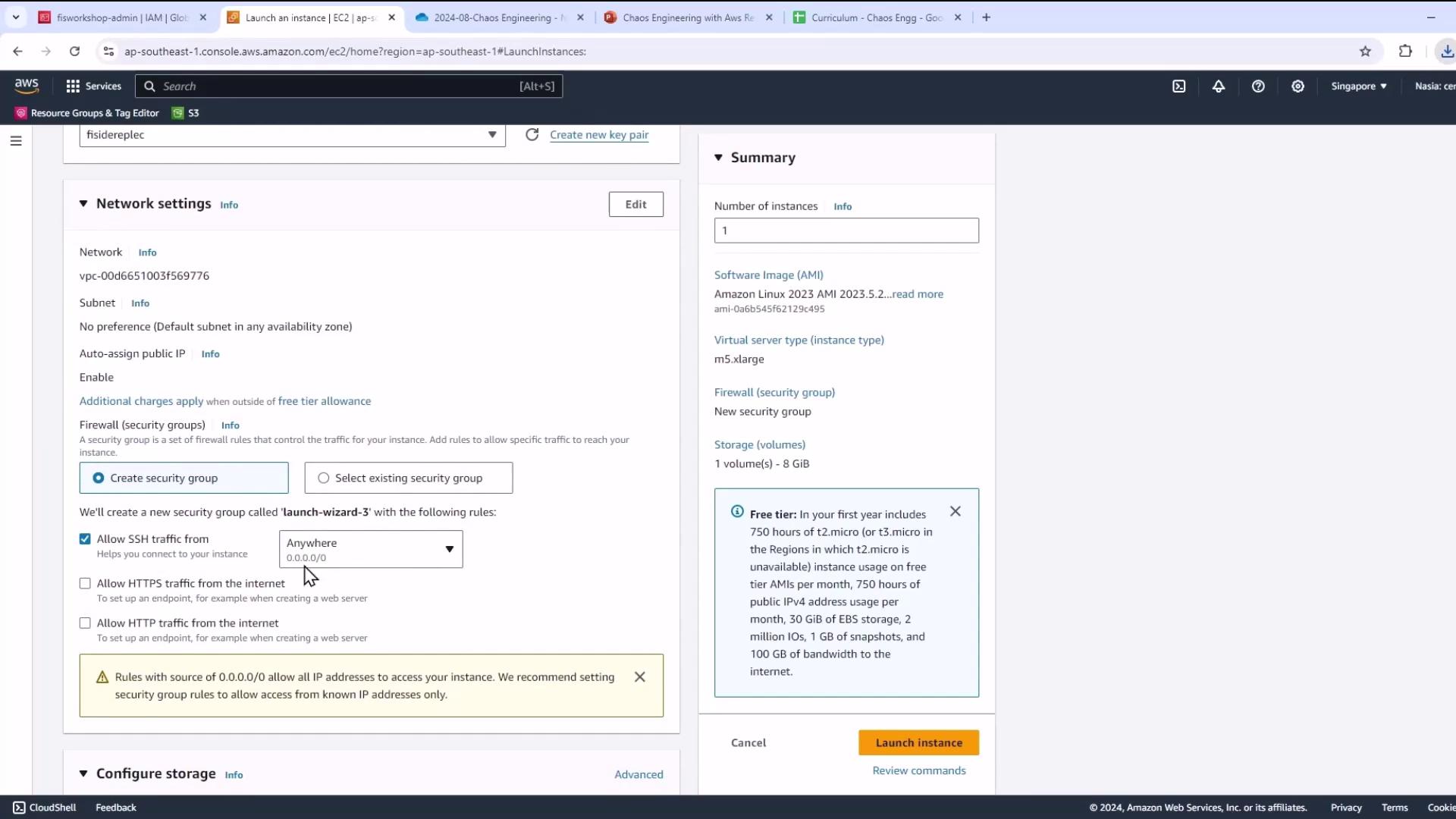
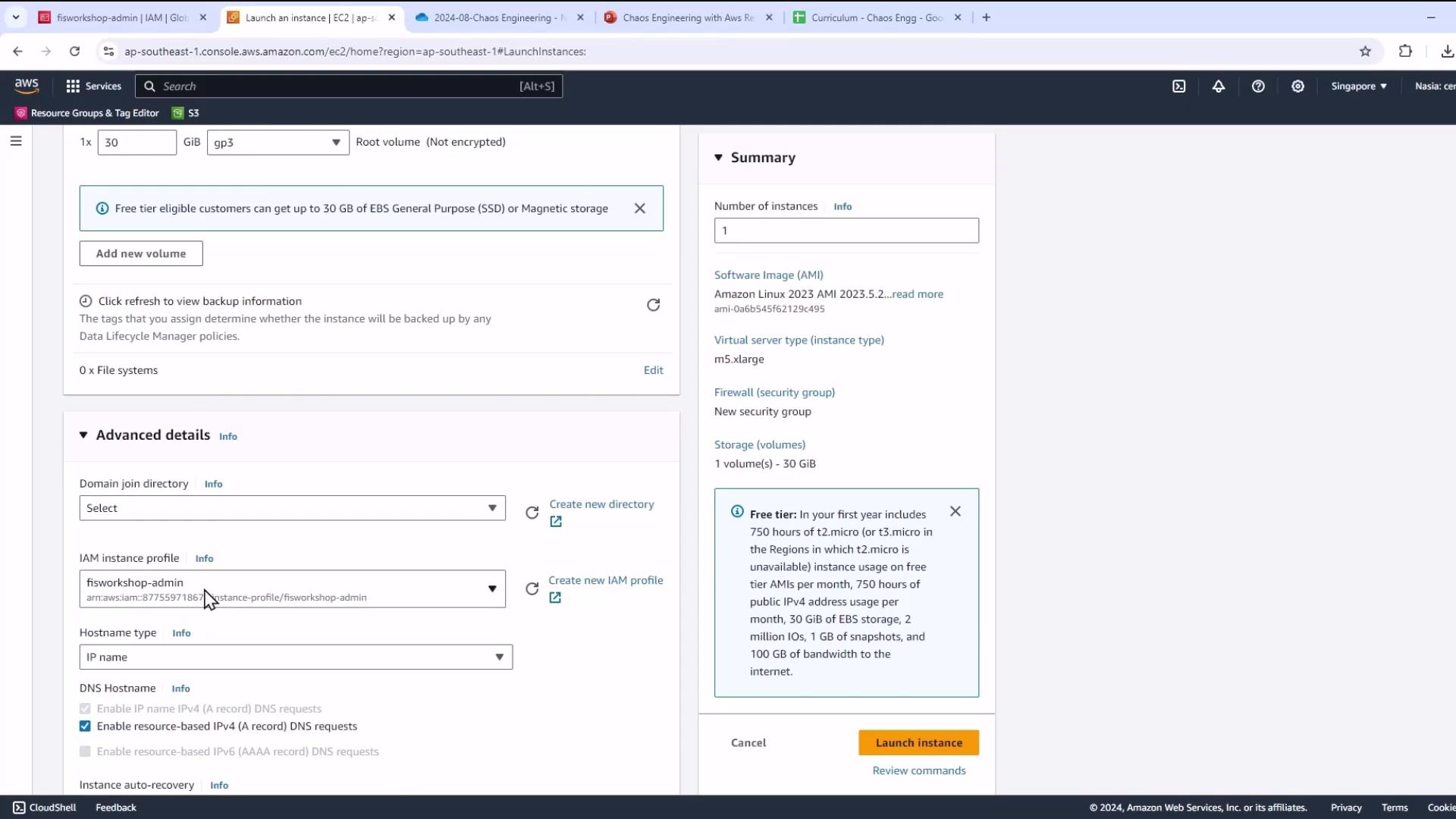
- Under Storage, increase the root volume size to meet lab requirements.

- In Advanced Details, select the IAM instance profile you created (
fisworkshop-admin) to grant AWS API permissions.
- Launch and confirm success.
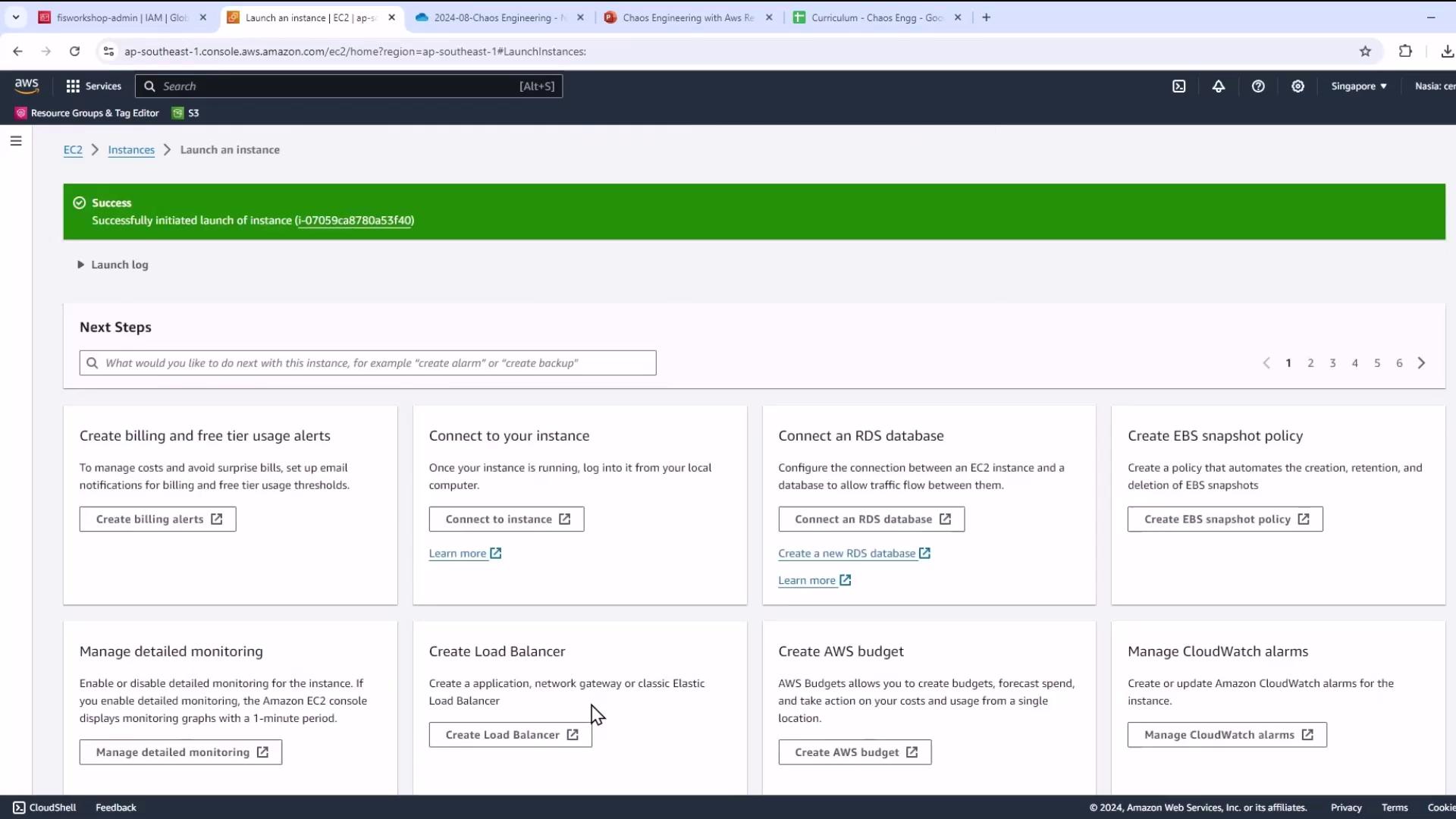
- Wait until your instance is running & passes 2/2 status checks.
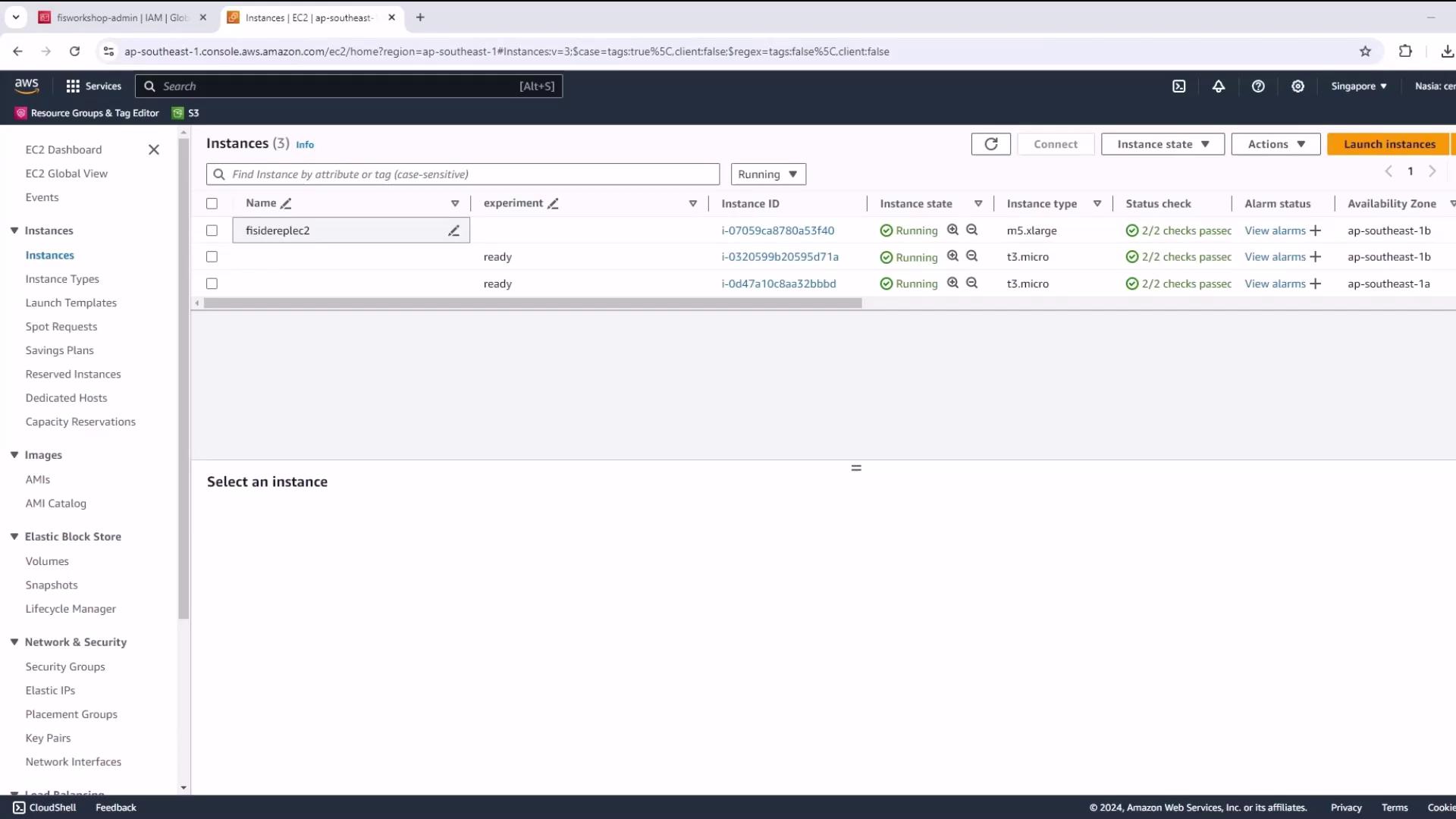
3. Connect and Prepare the EC2 Environment
- Select your instance, click Connect → EC2 Instance Connect.
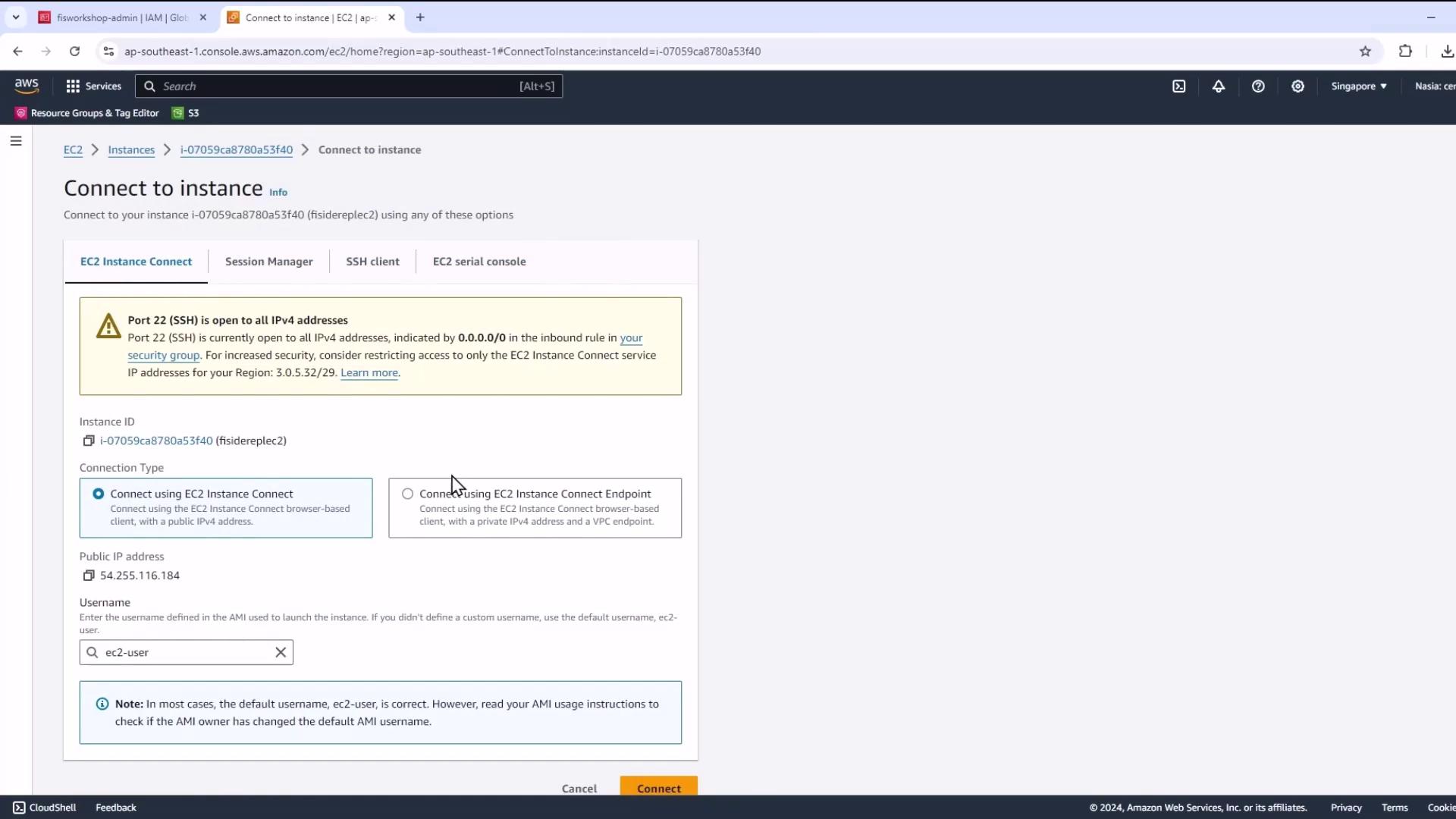
Note
If EC2 Instance Connect isn’t available, use your SSH key pair and ssh -i <key.pem> ec2-user@<public-ip>.
- Switch to root:
sudo su -
clear
- Install Git and clone the repository:
yum install -y git
git clone https://github.com/nasiauallas/FaultInjectionSimulator-KodeKloud.git
- Run the prerequisites script:
cd FaultInjectionSimulator-KodeKloud/Manual_IDE
chmod +x pre-req-manual-ide.sh
./pre-req-manual-ide.sh
This installs Docker, kubectl, Helm, eksctl, Node.js, AWS CDK, and more. You should see versions such as:
Git version: 2.40.1
Docker version: 25.0.6
AWS CDK version: 2.6.0
kubectl version: v1.29.0
Helm version: v3.13.0
eksctl version: 0.180.0
Node.js version: v22.6.0
4. Clone the AWS FIS Workshop
Create a workspace and clone the official AWS Fault Injection Simulator workshop:
mkdir -p ~/environment/workshopfiles
git clone https://github.com/aws-samples/aws-fault-injection-simulator-workshop-v2.git ~/environment/workshopfiles/fis-workshop
5. Configure AWS Environment Variables
Set your account ID and region for all CLI calls:
export AWS_PAGER=""
export ACCOUNT_ID=$(aws sts get-caller-identity --output text --query Account)
export AWS_REGION=$(aws ec2 describe-availability-zones --output text --query 'AvailabilityZones[0].RegionName')
echo "export ACCOUNT_ID=${ACCOUNT_ID}" >> ~/.bash_profile
echo "export AWS_REGION=${AWS_REGION}" >> ~/.bash_profile
aws configure set default.region "${AWS_REGION}"
aws configure get default.region
Validate your IAM role assignment:
aws sts get-caller-identity --query Arn \
| grep fisworkshop-admin -q \
&& echo "You're good. IAM role IS valid." \
|| echo "IAM role NOT valid. DO NOT PROCEED."
6. Deploy the Application with AWS CDK
- Navigate to your CDK project (e.g.,
pet_stack), install dependencies, and fix audits:
cd pet_stack
npm install
npm audit fix
- Bootstrap the CDK environment:
cdk bootstrap
You should see output like:
Bootstrapping environment aws://123456789012/us-east-1...
Building Docker image for AWS Lambda...
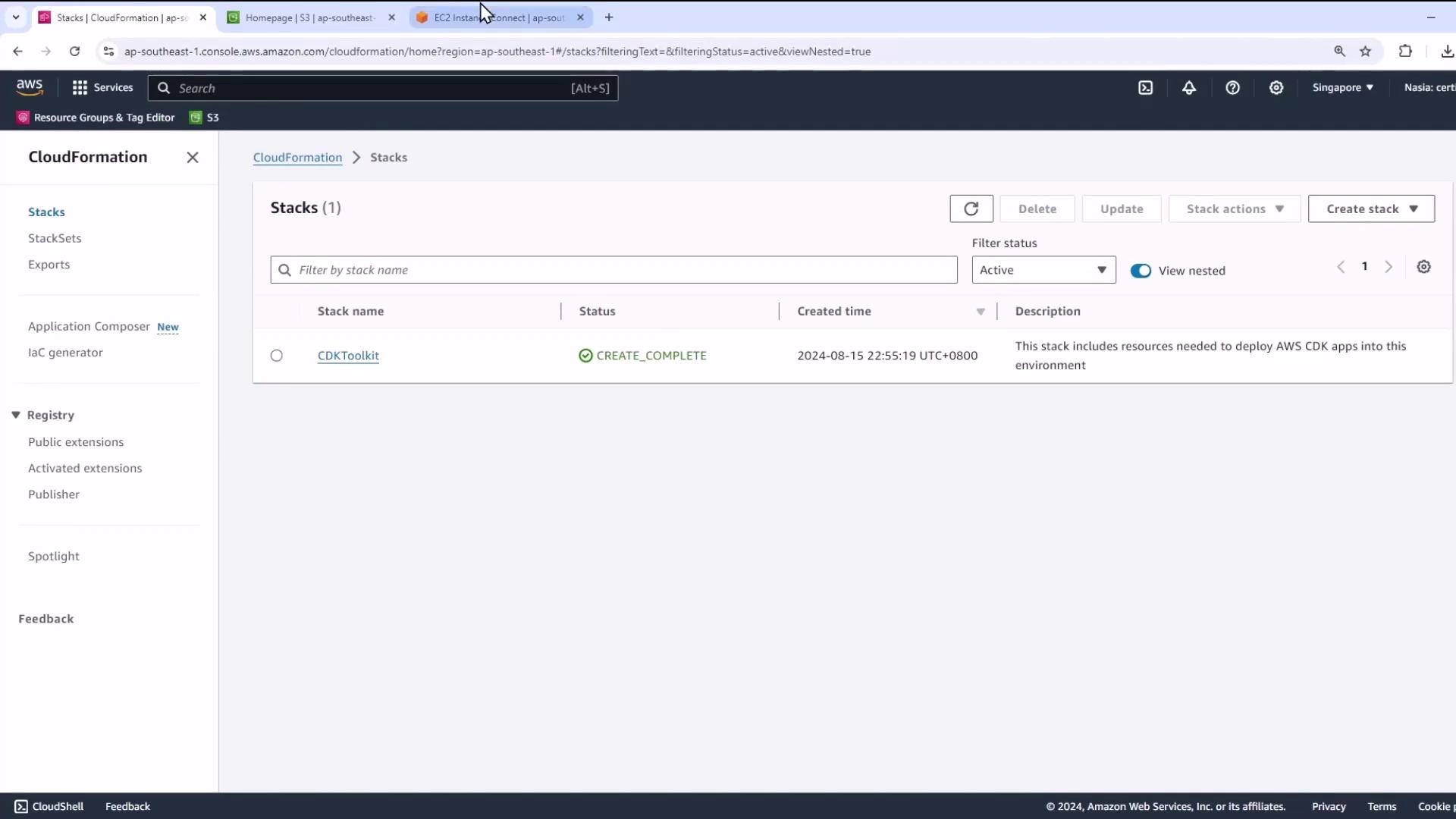
Deploying CDKToolkit stack...
CREATE_COMPLETE CloudFormationStack CDKToolkit
- Confirm in CloudFormation that CDKToolkit is in
CREATE_COMPLETE.
7. Final Deployment Steps
- Export your current role ARN and deploy the full stack (may take ~30 minutes):
export CONSOLE_ROLE_ARN=$(aws sts get-caller-identity --query Arn --output text)
echo $CONSOLE_ROLE_ARN
cd pet_stack
cdk deploy --require-approval never
- After deployment completes, explore the next experiments in:
~/environment/workshopfiles/fis-workshop.
Links and References
- AWS IAM Documentation
- Amazon EC2 User Guide
- AWS CDK Developer Guide
- AWS Fault Injection Simulator Workshop
- Docker Hub
Watch Video
Watch video content