CompTIA Security+ Certification
Controls and Security Concepts
Encryption
Welcome to this comprehensive guide on encryption, where we delve into how this critical technology protects data through confidentiality—a core principle of the CIA triad.
To begin, confidentiality ensures that even if an unauthorized party gains access to files or data, the information remains unreadable. Encryption achieves this by scrambling data so that only those with the proper key can decrypt and access it.

Encryption falls into two main categories: symmetric encryption and asymmetric encryption.
Symmetric Encryption
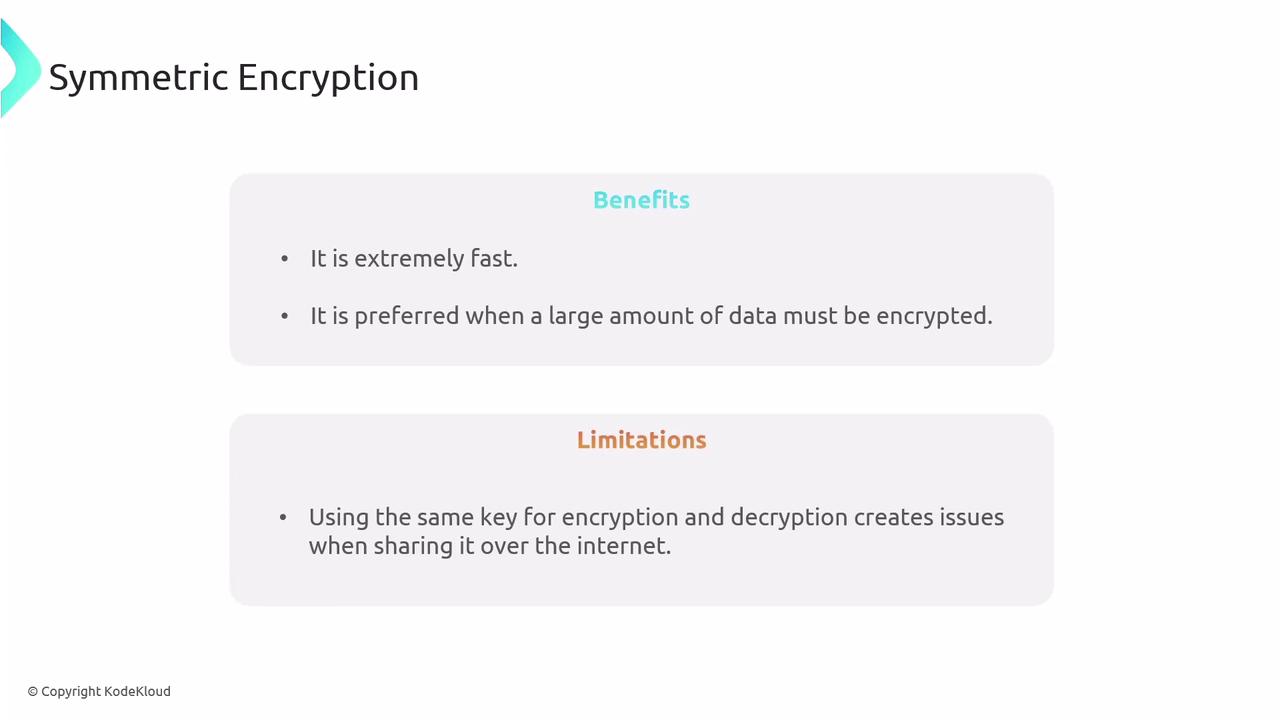
Symmetric encryption uses a single key for both encryption and decryption. For example, when sensitive information is transmitted over the internet, it is encrypted with a key that the recipient must also possess to decrypt and read the data. This approach offers rapid performance, making it ideal for large volumes of data, but poses challenges in securely exchanging the key.

![]()
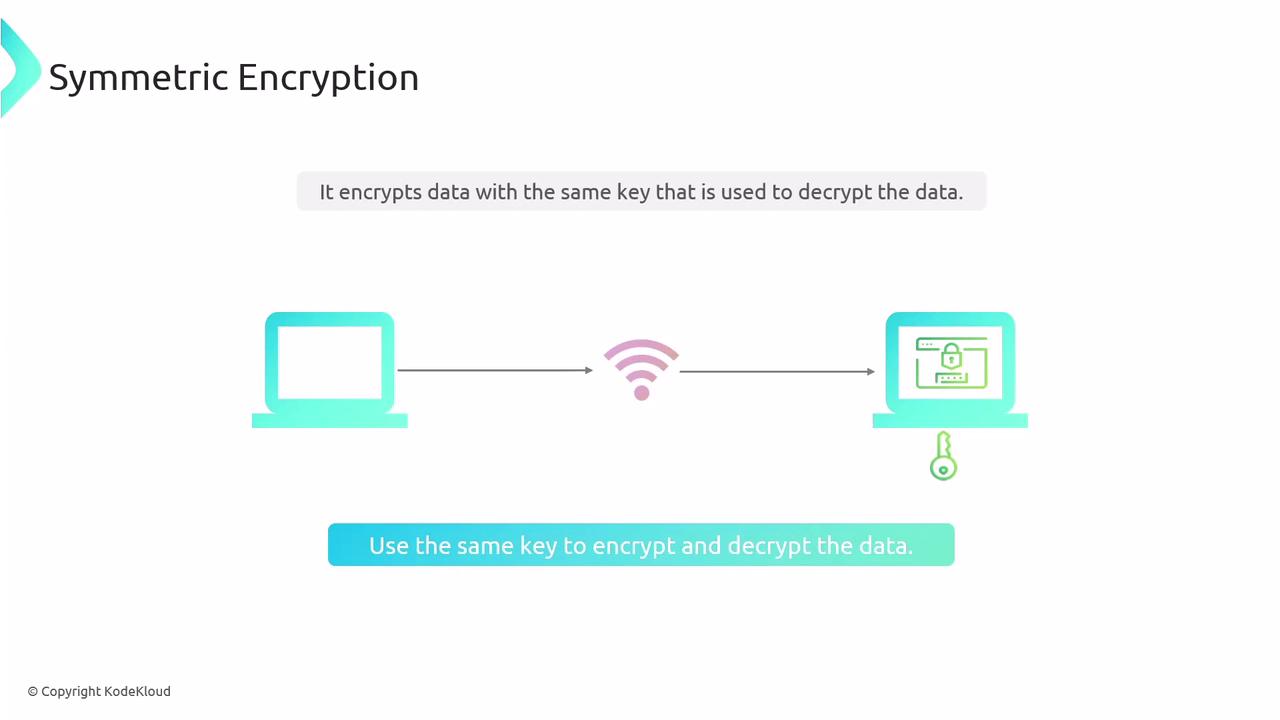
While the speed of symmetric encryption is a significant advantage, its major drawback is key management. Securely transmitting a shared key between sender and receiver can be difficult.
Below is a table summarizing common implementations of symmetric encryption:
| Encryption Method | Description | Examples |
|---|---|---|
| Disk or Volume Encryption | Encrypts entire drives, specific partitions, or volumes. | BitLocker, FileVault |
| File Encryption | Encrypts individual files using system tools. | NTFS Encryption |
| Database Encryption | Secures entire databases or specific records. | Custom Database Solutions |
Note
Selecting the right symmetric encryption method depends on the data's location and sensitivity, as well as the system's performance requirements.
Types of Symmetric Encryption
Symmetric encryption is applied in several contexts:
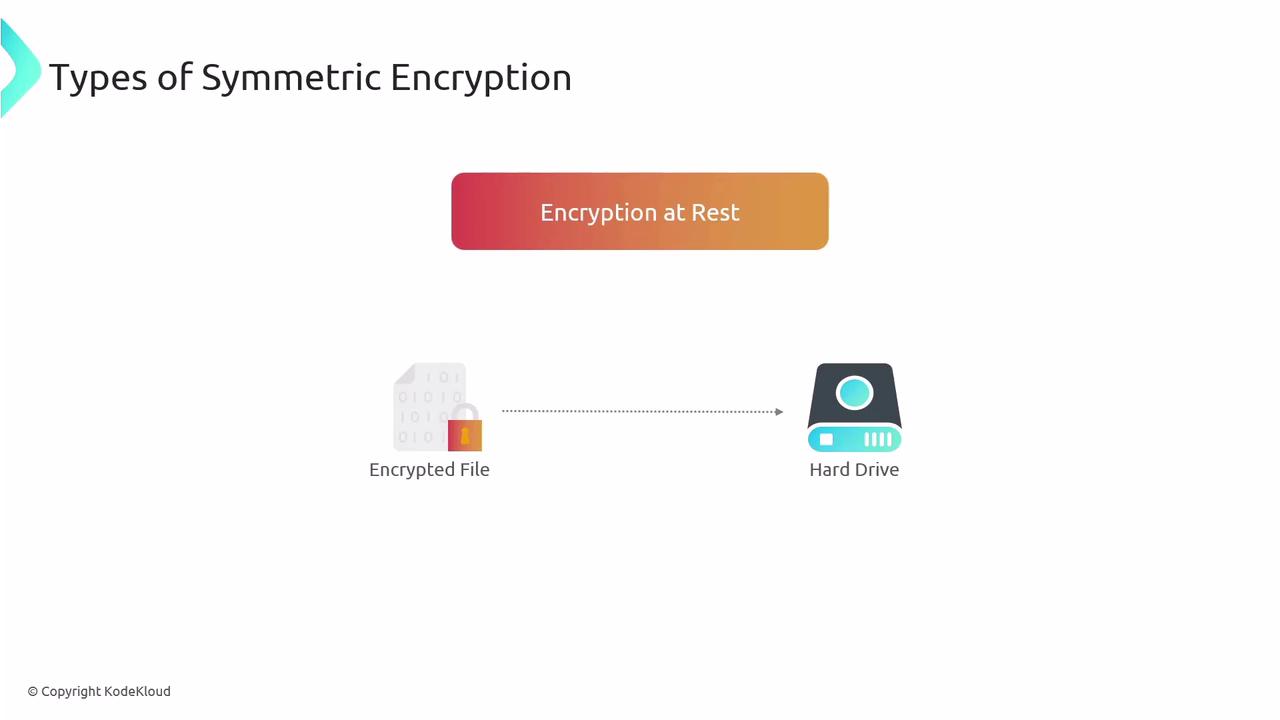
Encryption at Rest
Encryption at rest involves protecting stored data on physical media such as hard drives. This can include:
- Full Disk Encryption: Encrypting the entire drive, including free space and file metadata.
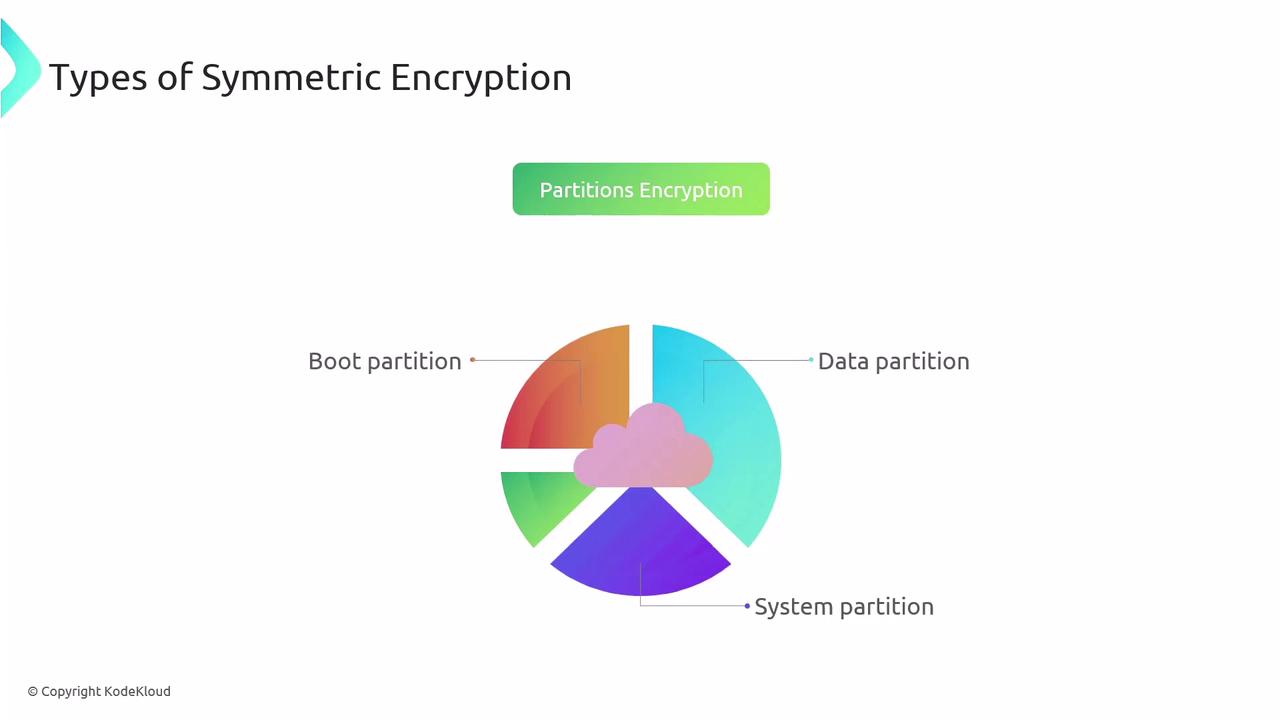
- Partition Encryption: Dividing the drive into segments (e.g., boot, system, and data partitions) and encrypting each separately with unique keys.
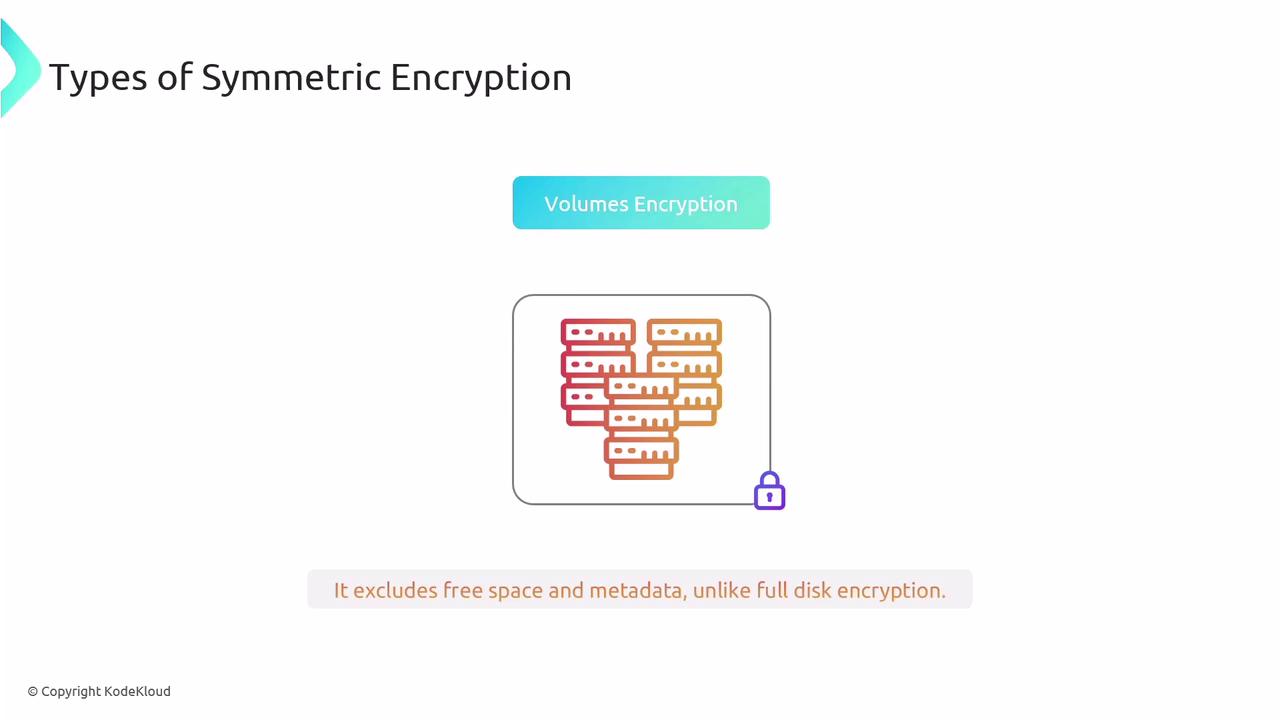
- Volume Encryption: Encrypting specific volumes while typically excluding free space and metadata. Popular examples include Microsoft BitLocker and Apple FileVault.
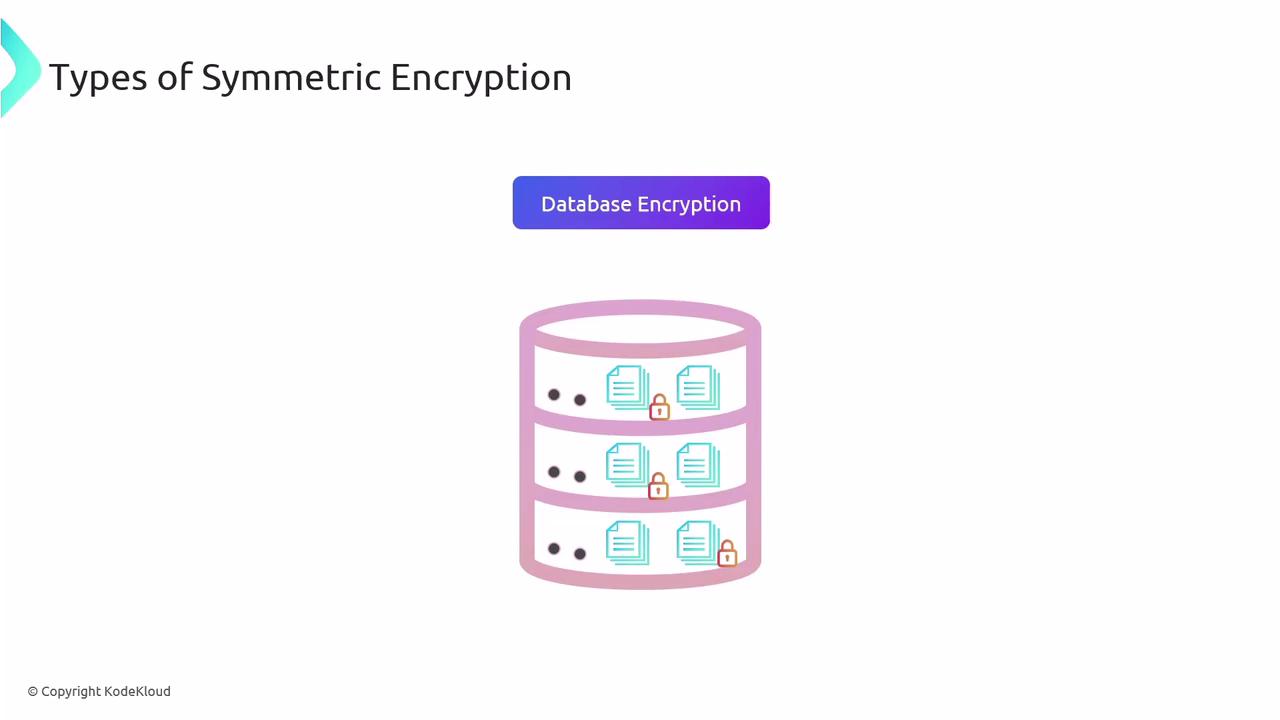
Database Encryption
Databases often contain highly sensitive information and may require encryption either for the entire database or for individual records to ensure confidentiality.
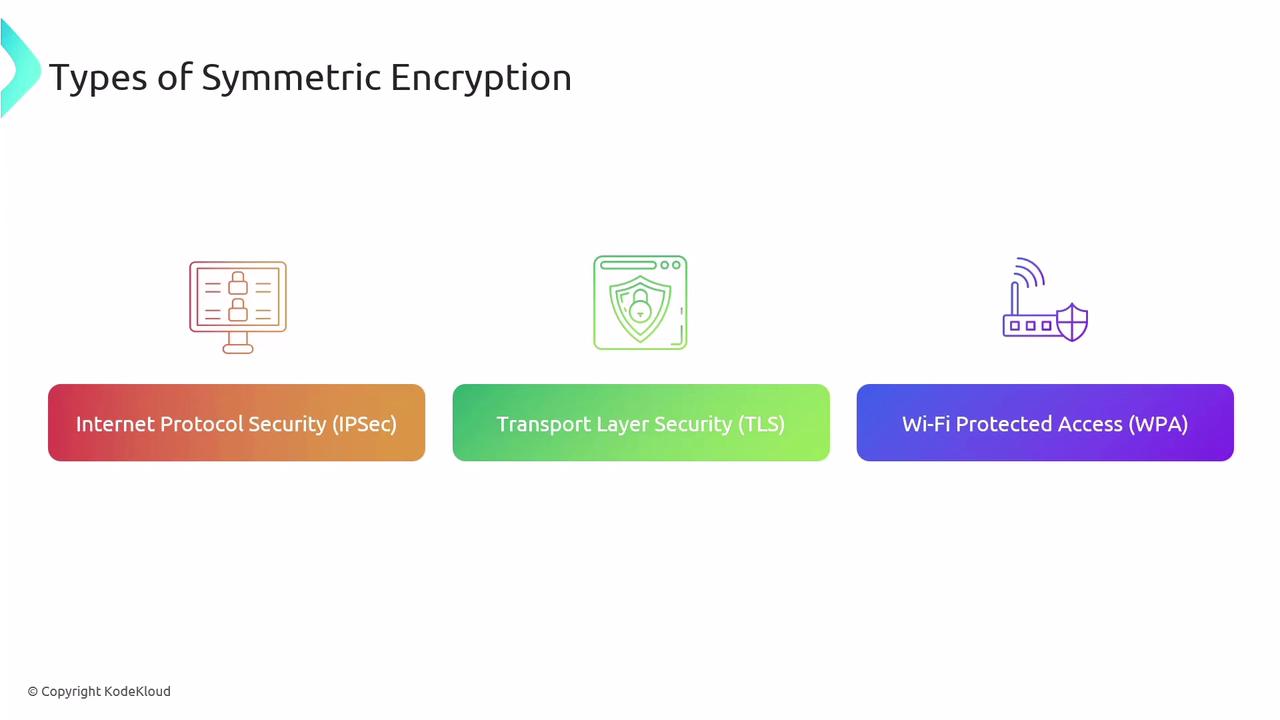
In addition to encryption at rest, protecting data in motion is crucial. Protocols such as IPSec, TLS, and Wi-Fi Protected Access (WPA) secure data as it moves across networks, ensuring that intercepted data remains indecipherable.
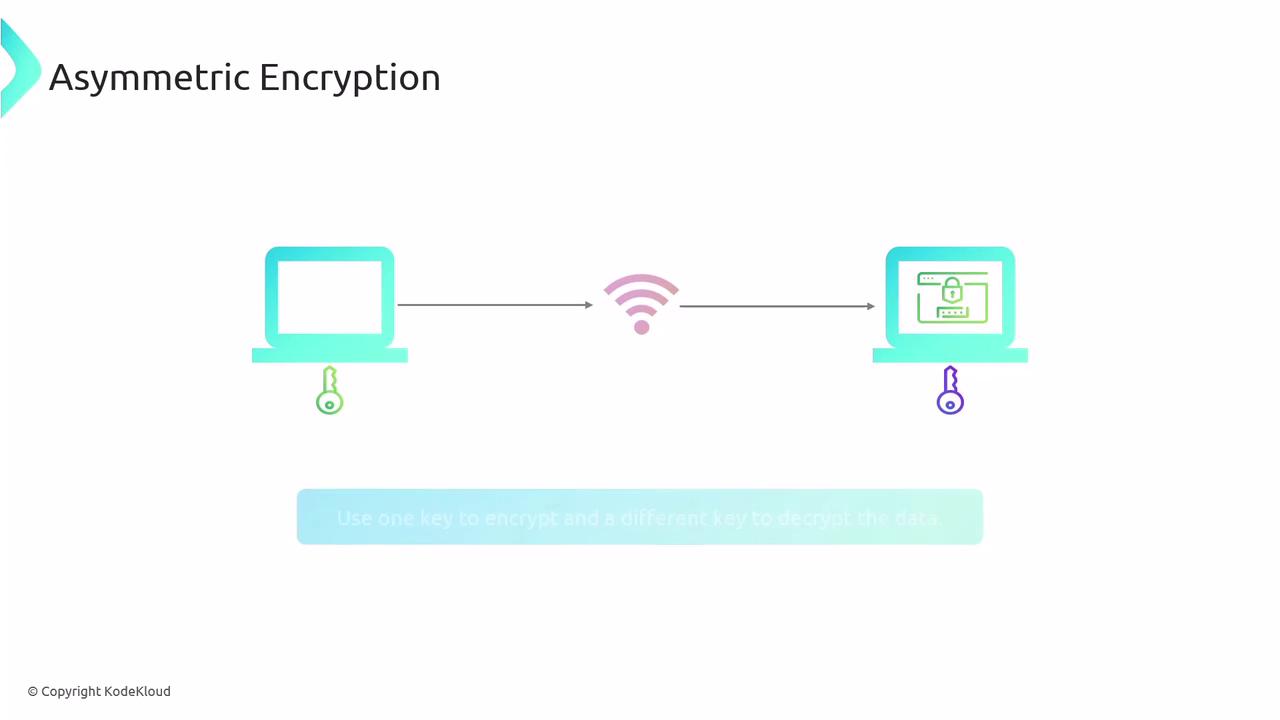
Asymmetric Encryption
Unlike symmetric encryption, asymmetric encryption uses a pair of keys—one for encryption and a different one for decryption. This method eliminates the need to share a common key and is a vital component of Public Key Infrastructure (PKI), facilitating secure communication without complex key exchanges.
Key Length and Encryption Algorithms
Choosing the correct encryption algorithm and key length is essential for robust data security. The Advanced Encryption Standard (AES) is the current benchmark for symmetric encryption. By using longer key lengths, AES makes brute-force attacks computationally infeasible.
AES with a 128-bit key already offers strong protection, with brute-force attackers facing an astronomical amount of time—often estimated in trillions of years—to breach it. Upgrading to 256-bit encryption further enhances security exponentially.

Note
While symmetric encryption delivers high performance, its key management issues mean that organizations must weigh its benefits against potential vulnerabilities when choosing an encryption strategy.
Conclusion
Encryption is a cornerstone of data protection, ensuring confidentiality both at rest and in transit. By understanding and correctly implementing either symmetric or asymmetric encryption—along with appropriate key lengths and algorithms—you can significantly bolster your data security measures.
For further reading and additional resources, consider exploring:
That concludes our in-depth exploration of encryption.
Watch Video
Watch video content