Understanding Encryption Methods
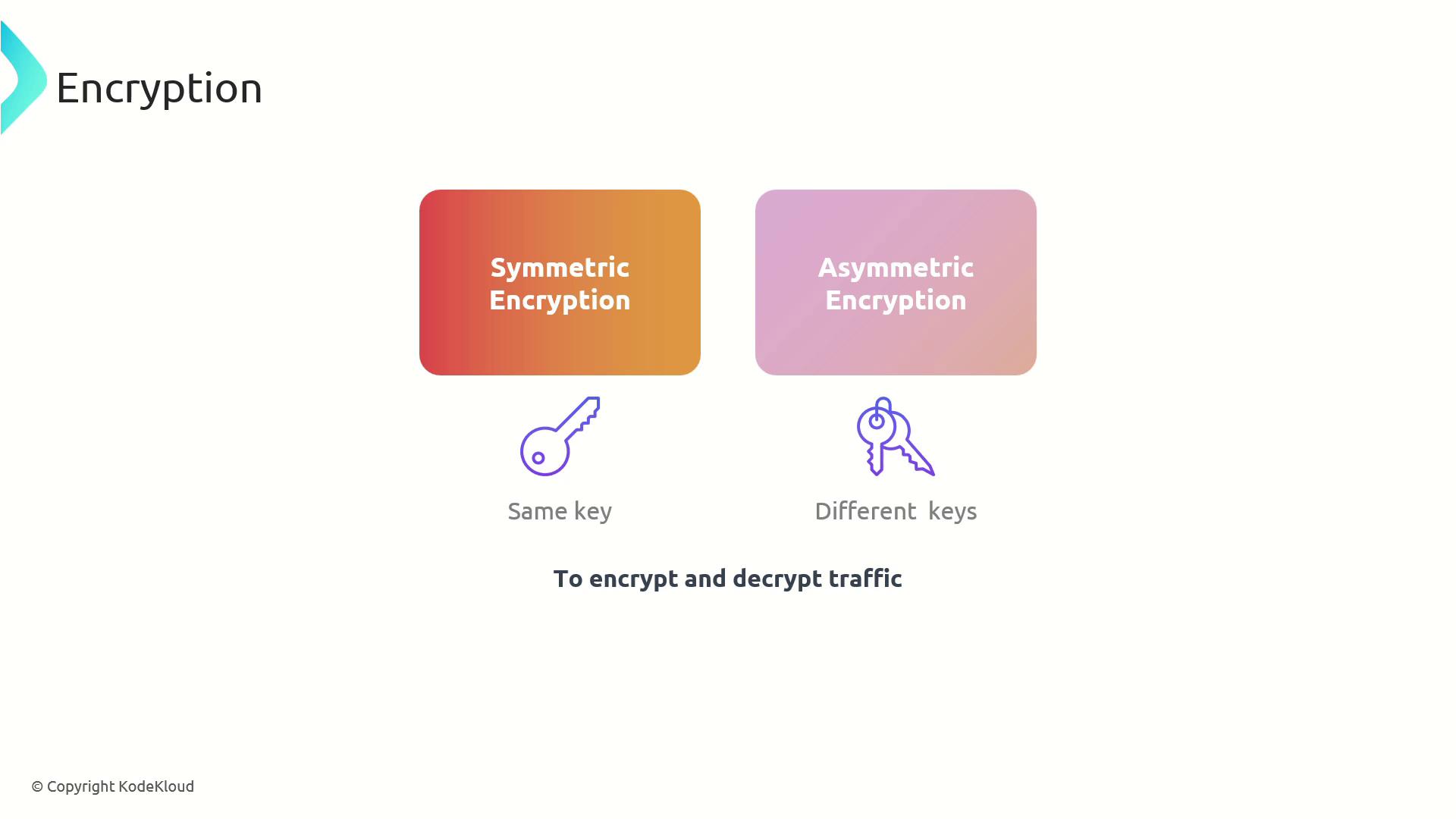
Earlier, we examined two fundamental encryption methods:- Symmetric Encryption: Uses the same key for both encryption and decryption.
- Asymmetric Encryption: Utilizes a pair of keys—one public and one private—for encryption and decryption respectively.
How Asymmetric Encryption Works in PKI
In asymmetric encryption, one key encrypts the data while a different key decrypts it. The two keys are defined as follows:- Public Key: Shared openly and often made available on the Internet.
- Private Key: Kept confidential and stored securely.
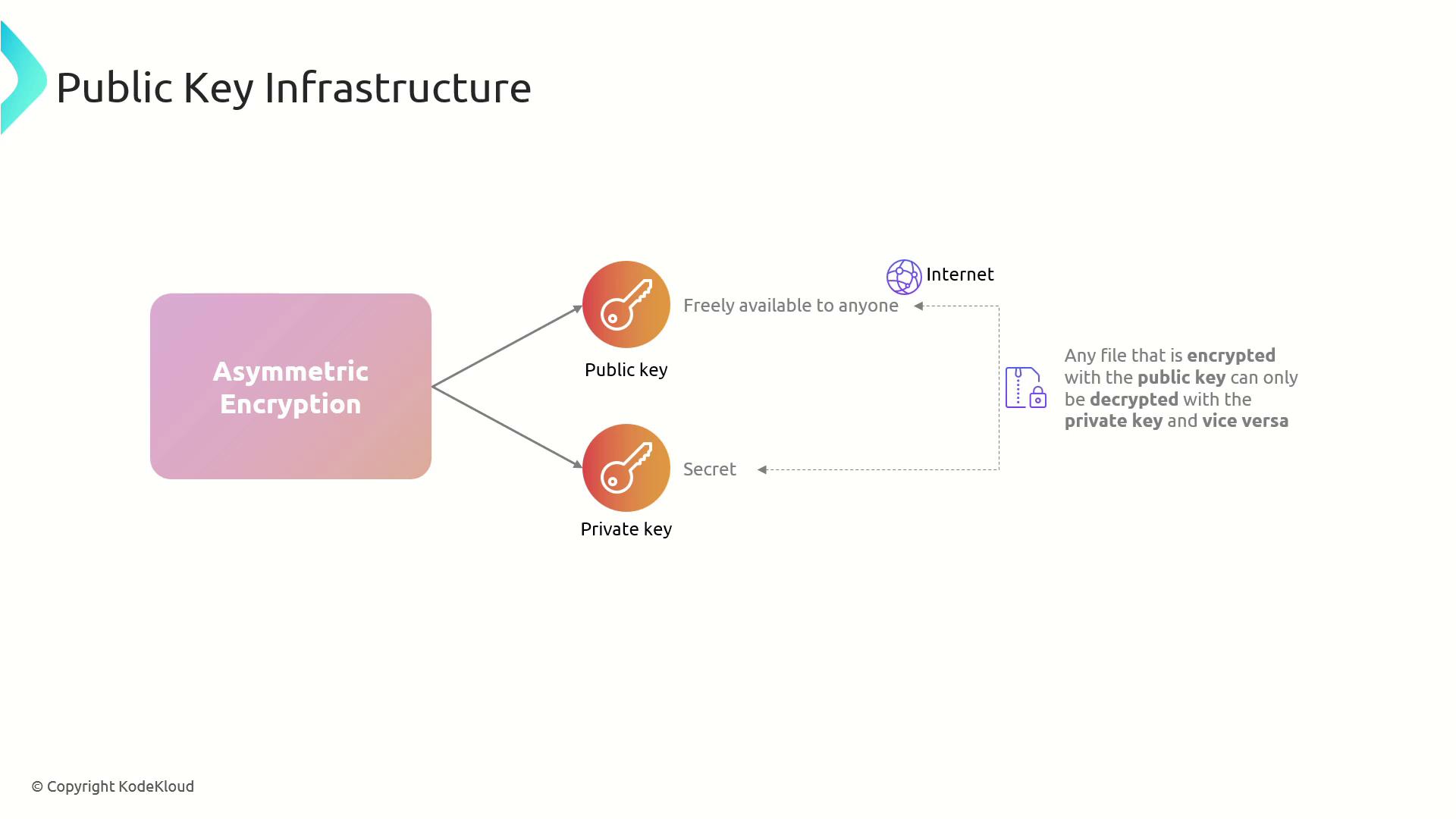
Keep your private key secure at all times to maintain the integrity of your encrypted communications.
Verifying Authenticity with Digital Signatures
Digital signatures are a crucial application of PKI. They allow users to verify the authenticity and integrity of shared files. For example, when distributing software, you can generate a digital signature by processing the file with your private key. Recipients can then use your public key to verify:- The file’s authenticity, confirming it originates from you.
- That the file has not been altered.
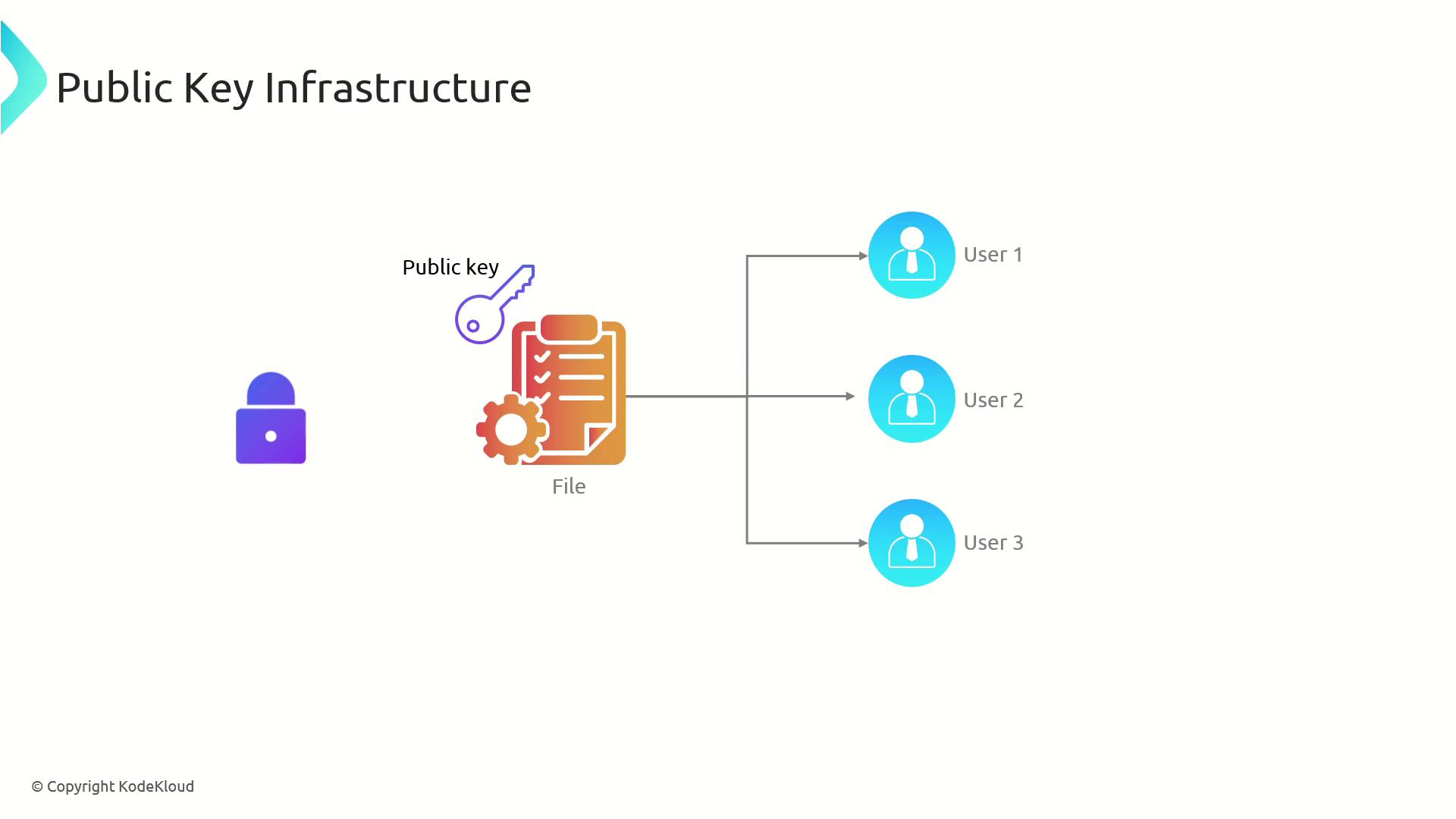
Secure File Exchange
PKI also enables secure file transmission. When you make your public key available, anyone can encrypt a file for you. Only you can decrypt it with your private key, ensuring secure communication.Never share your private key. Its confidentiality is essential for protecting your encrypted data.
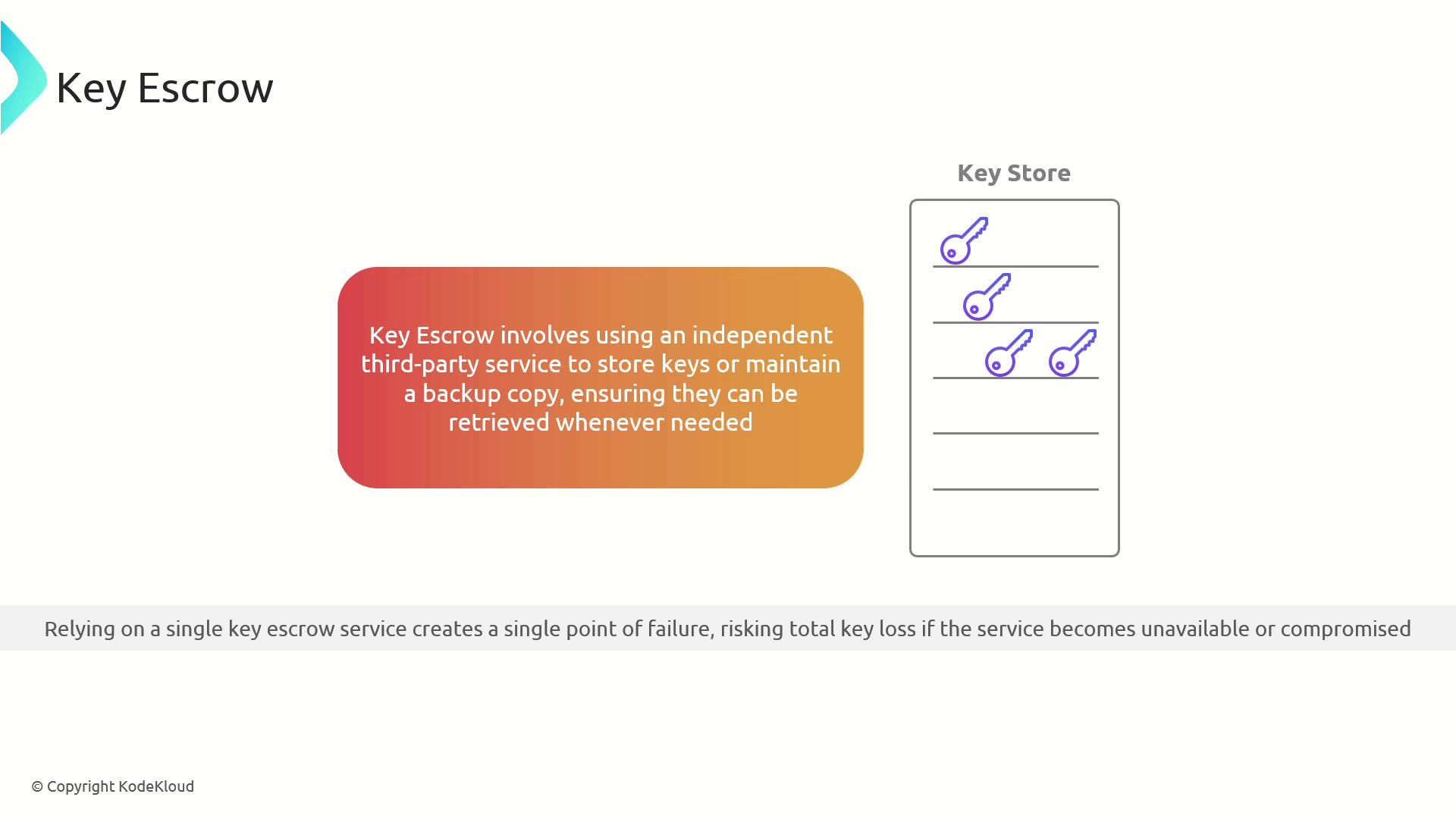
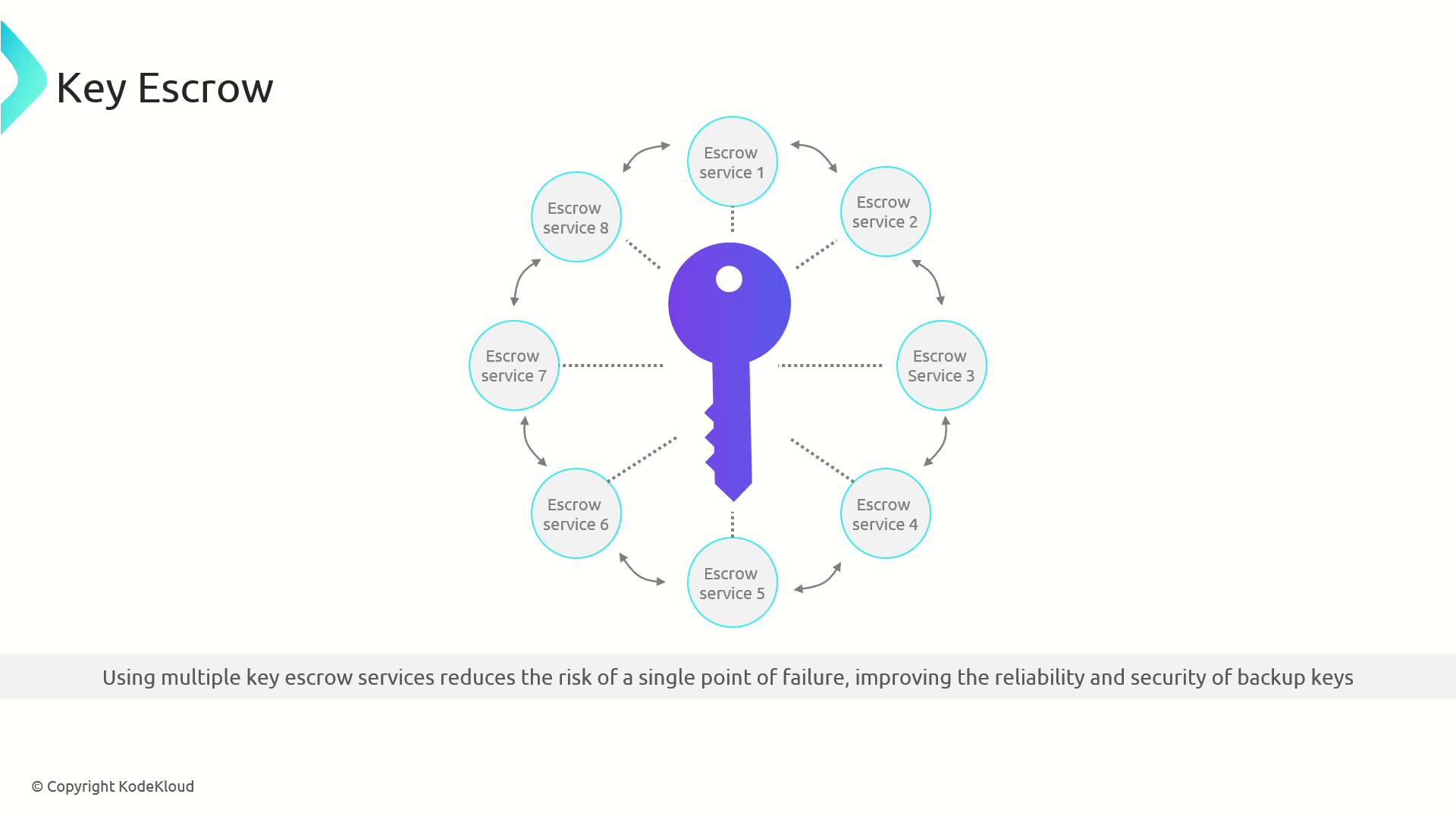
Key Management and Key Escrow
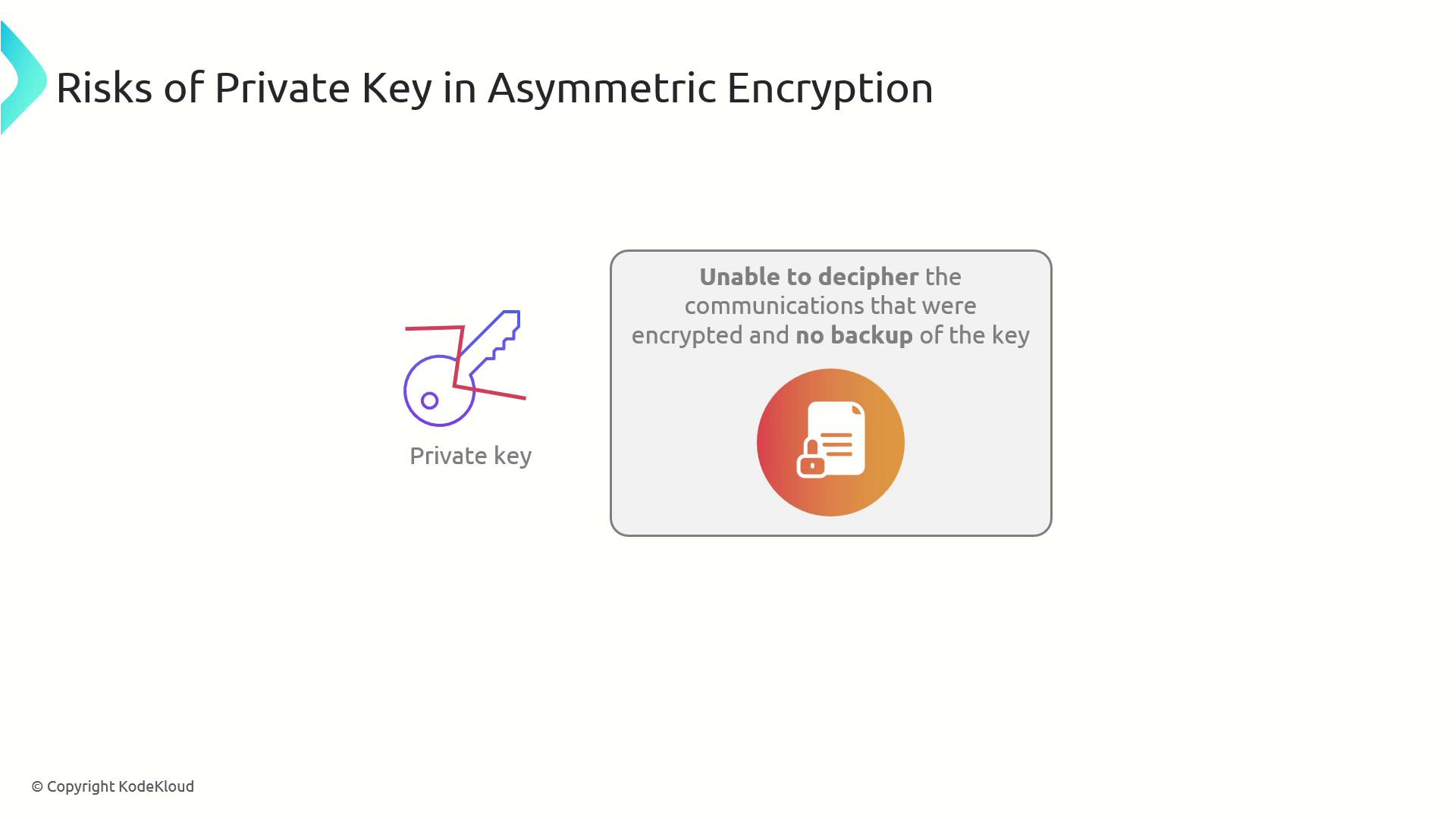
Managing private keys is critical. If a private key is lost or damaged without a backup, any data encrypted with its associated public key becomes inaccessible.