
Why Backups Matter
Backups are copies of your data stored separately from the original source. They are essential for data protection, business continuity, and regulatory compliance by ensuring that information can be recovered in case of loss, corruption, or disaster. Backups mitigate risks from hardware failures, human errors, malware attacks, and natural disasters while helping maintain operational continuity.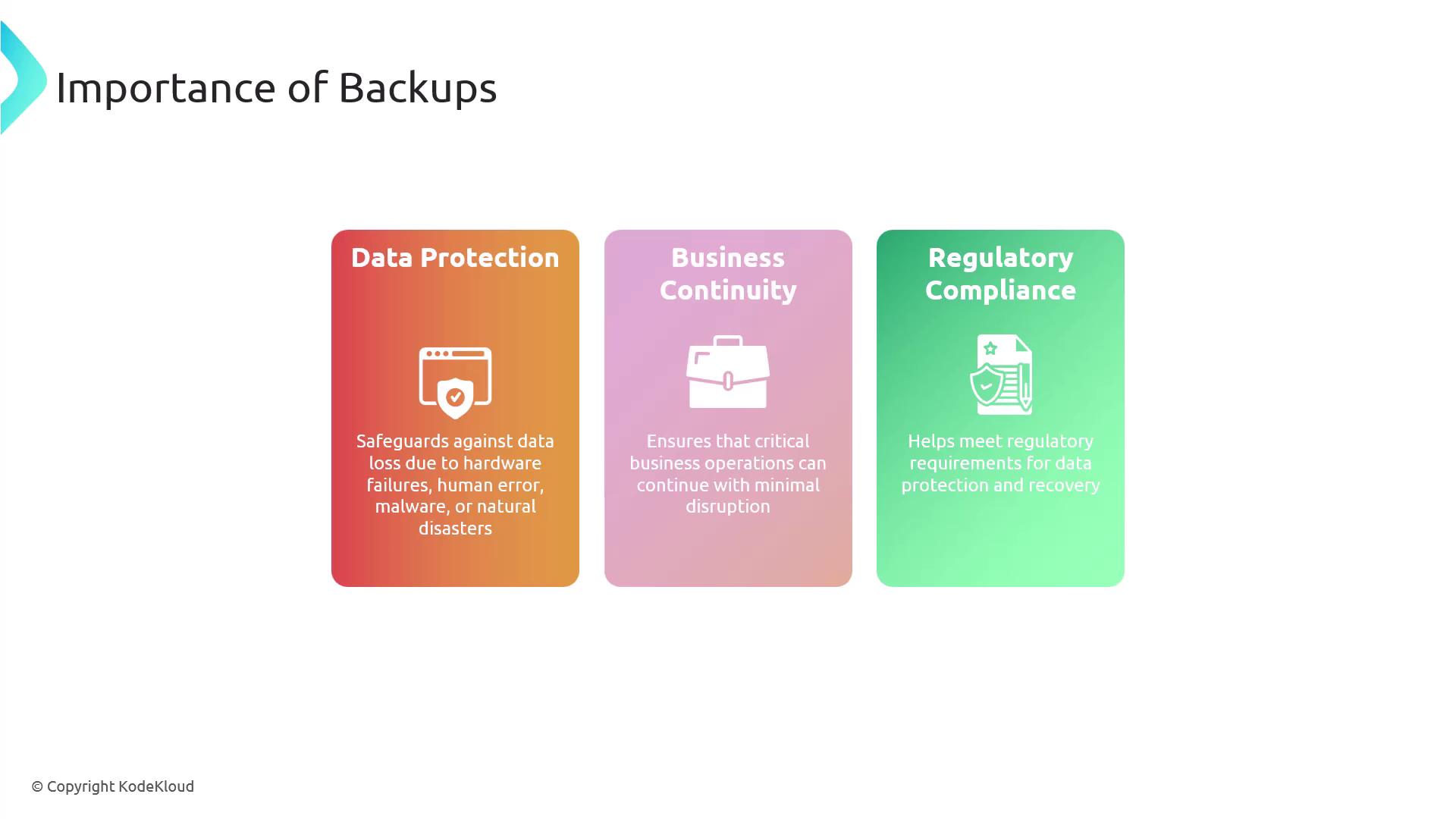
Incorporating routine backups into your data management strategy is essential to minimize downtime and data loss.
- On-site and off-site backups
- Backup frequency and data currency
- Encryption techniques
- Snapshots for rapid recovery
- Data recovery procedures
- Data replication for redundancy
- Journaling for tracking changes
On-site and Off-site Backups
On-site Backups
On-site backups are stored in the same physical location as your primary data. Their advantages include:- Quick access for faster recovery due to physical proximity.
- Greater control over the backup process and storage environment.
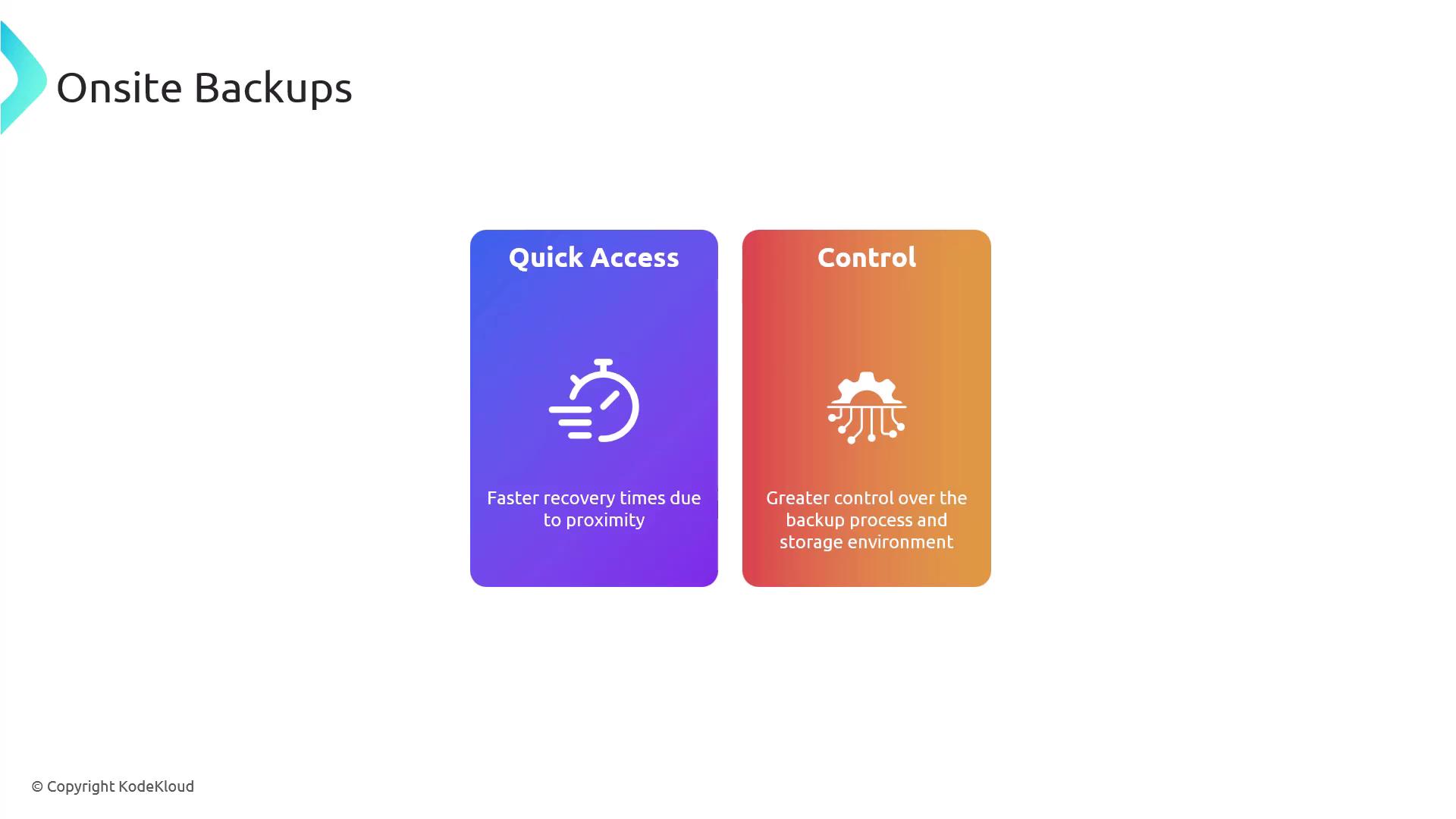
On-site backups are at risk of the same local disasters (e.g., fires or floods) that can impact your primary data.
Off-site Backups
Off-site backups are stored at a different location from your primary data. Their key benefits include enhanced disaster recovery and improved compliance, as they remain unaffected by local incidents. However, off-site backups may experience longer access and recovery times due to the distance involved.Backup Frequency
Backup frequency is the interval at which backups are created and directly influences the Recovery Point Objective (RPO) – the maximum acceptable amount of data loss measured in time. Maintaining high data currency minimizes potential data loss during a failure.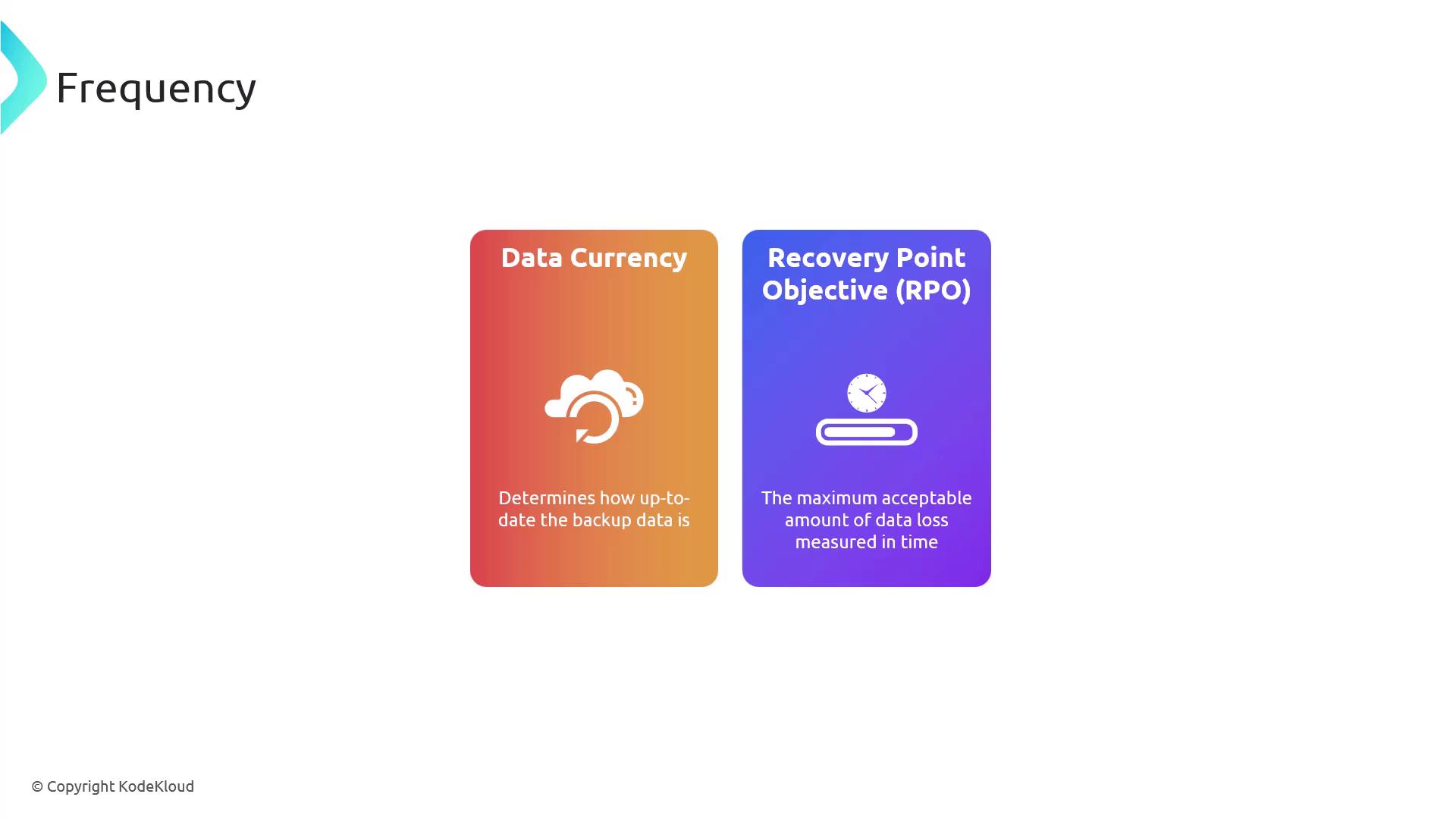
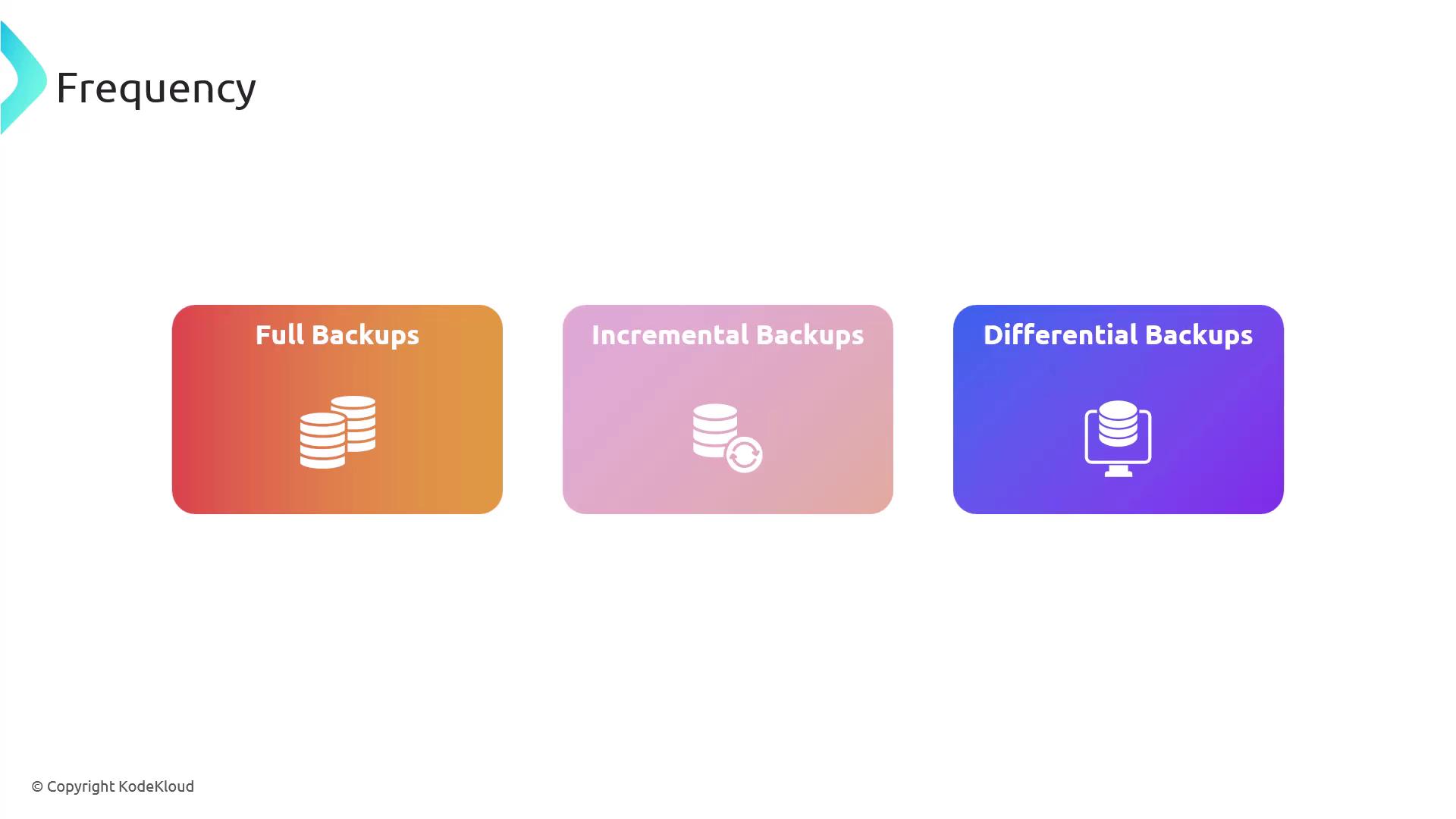
- Full Backups: A complete copy of all data.
- Incremental Backups: Copies only the data that has changed since the last backup.
- Differential Backups: Copies all data that has changed since the last full backup.
Backup Encryption
Encryption is a key component of backup security, protecting sensitive data from unauthorized access and helping meet regulatory standards. Backup encryption can be applied in two scenarios:- At Rest: Encrypting stored backup data on physical media or in the cloud.
- In Transit: Encrypting data during transfer to off-site locations.
Snapshots
Snapshots are point-in-time copies of your data, capturing the state of a system at a specific moment. This technique allows for rapid recovery without a significant impact on system performance. For instance, daily snapshots of virtual machines can quickly restore a system to a known good state in the event of data corruption or failure.Data Recovery
Data recovery is the process of restoring information from backups to its original location—or an alternative location—to resume normal operations. There are two primary recovery methods:- Full Recovery: Restores all data from the backup.
- Partial Recovery: Restores specific files or databases as needed.
Replication
Replication involves copying your data in real-time or near real-time to multiple locations, which enhances redundancy and reduces downtime. In the event of a primary system failure, replicated data ensures quick failover and continuous operations.
Journaling
Journaling is the process of recording changes to data in a log file, enabling point-in-time recovery. This detailed record of modifications supports data integrity and allows for granular recovery, especially useful for database transactions requiring precise recovery mechanisms.Conclusion
Robust backup strategies are indispensable for ensuring IT resilience and recovery. By integrating both on-site and off-site backups, determining optimal backup frequency, employing strong encryption, utilizing snapshots, establishing clear recovery procedures, and leveraging replication and journaling, you can build a resilient data protection framework that ensures business continuity and safeguards critical information.