Device Placement
Device placement involves positioning network devices in a manner that maximizes both security and performance. Two critical concepts to keep in mind are segmentation and defense in depth. Segmenting your network isolates sensitive data, while a layered security approach enhances overall resilience.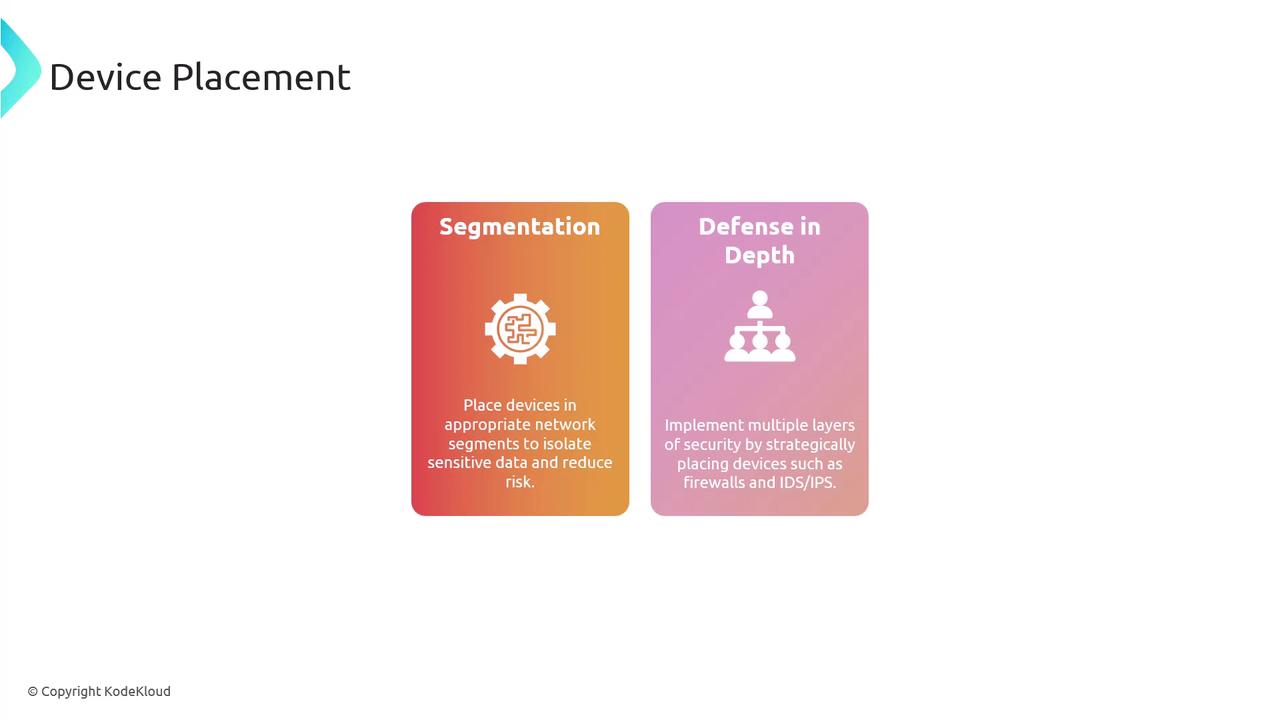
Attack Surface and Attack Vectors
Understanding your organization’s attack surface is essential. The attack surface encompasses every possible entry point that an attacker could exploit. In contrast, an attack vector is the specific method or pathway—such as phishing, social engineering, or SQL injection—used to breach security.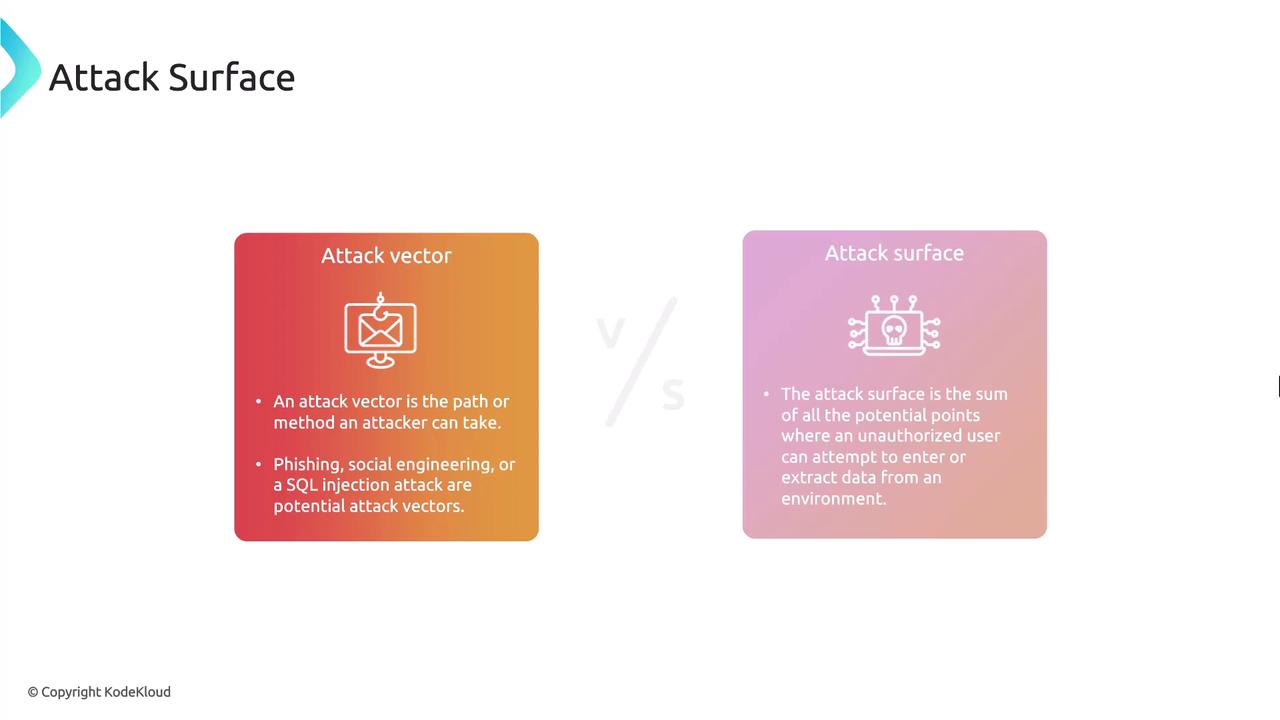
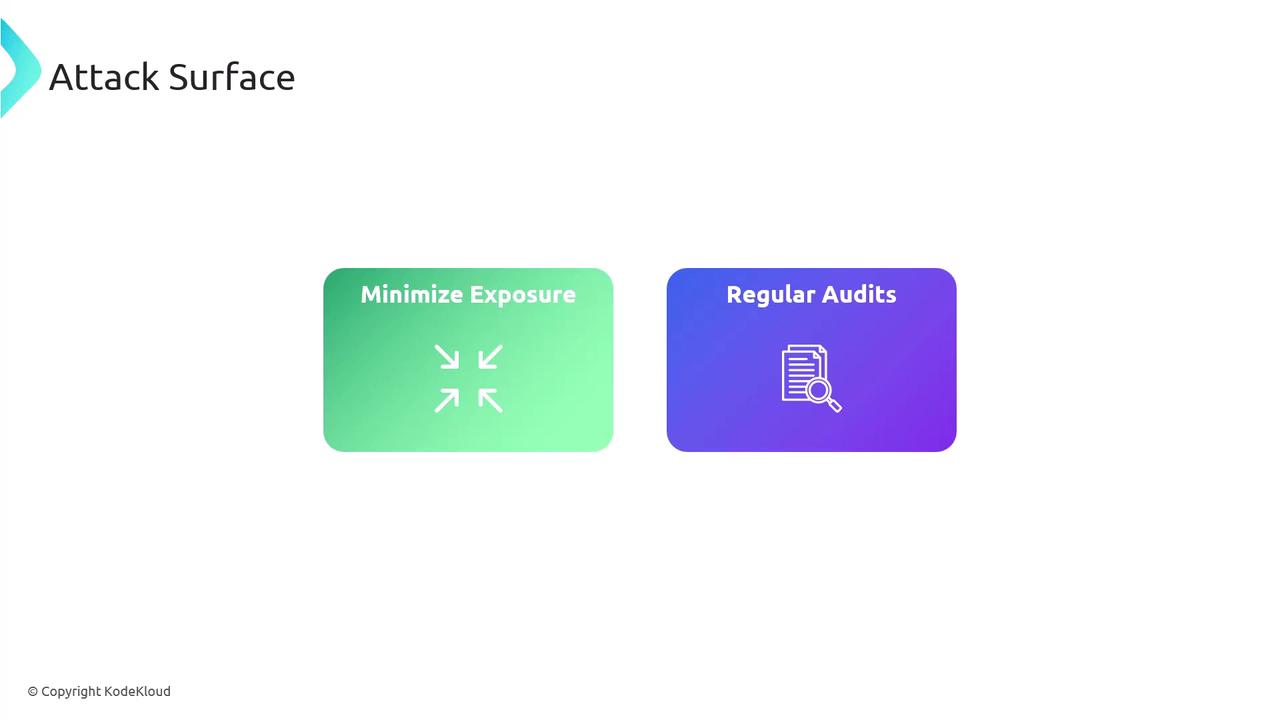
- Reduce the number of exposed services.
- Eliminate unnecessary entry points.
- Conduct regular security audits.
Connectivity
Connectivity defines how devices and systems interact within your network. It is crucial to establish secure communication channels—such as VPNs or TLS—to safeguard data during transit. Additionally, restrict access strictly to those users and systems that require it. For instance, implementing a VPN ensures that remote access is both secure and limited to authorized personnel only.Failure Modes
It’s important to understand the two primary failure modes that impact security during system disruptions:-
Fail Open:
In this configuration, the system remains accessible during a failure, potentially allowing unauthorized access. A common example is a firewall that, when it fails, permits all traffic. -
Fail Close:
Here, the system blocks access when a failure occurs, thereby preventing unauthorized entry. For example, a firewall that shuts down traffic completely upon failure operates in a fail-close manner.

Device Attributes
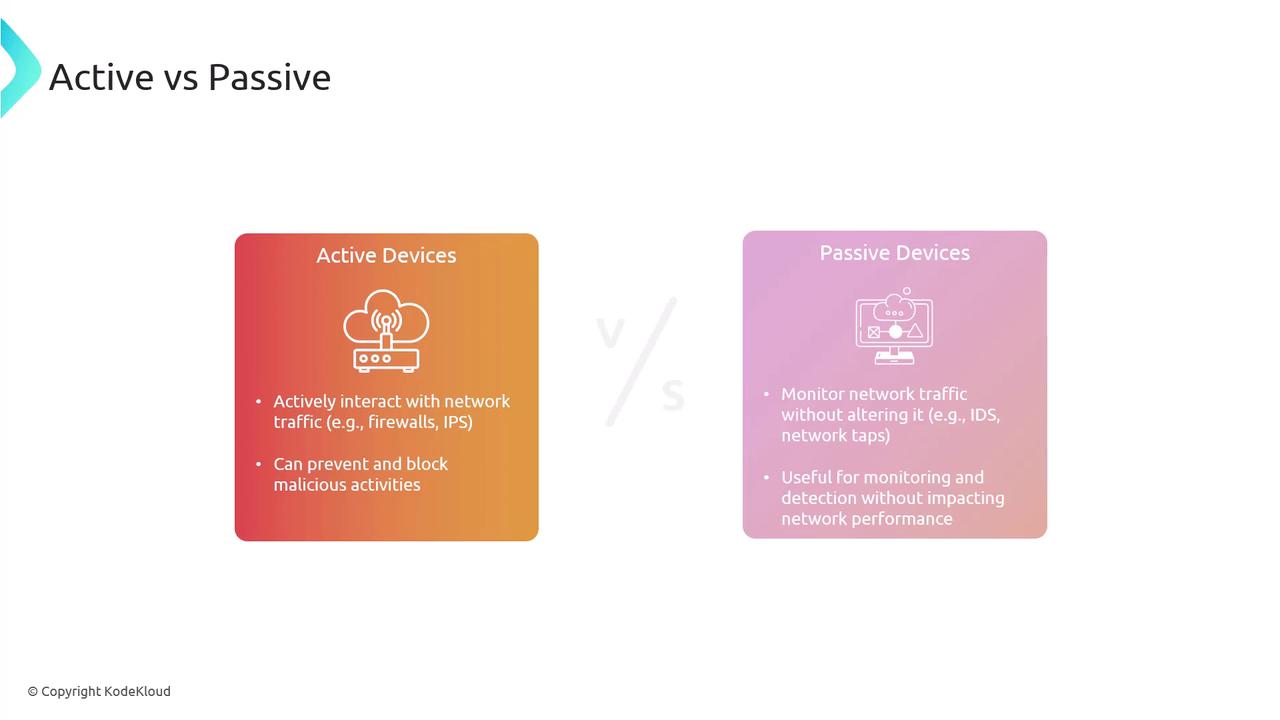
Devices in a network can be categorized based on operational characteristics. Two main distinctions include:- Active vs. Passive Devices:
Active devices, such as firewalls and IPS systems, engage with network traffic to block malicious actions. Passive devices, like intrusion detection systems and network taps, observe traffic without interfering, offering essential situational awareness.
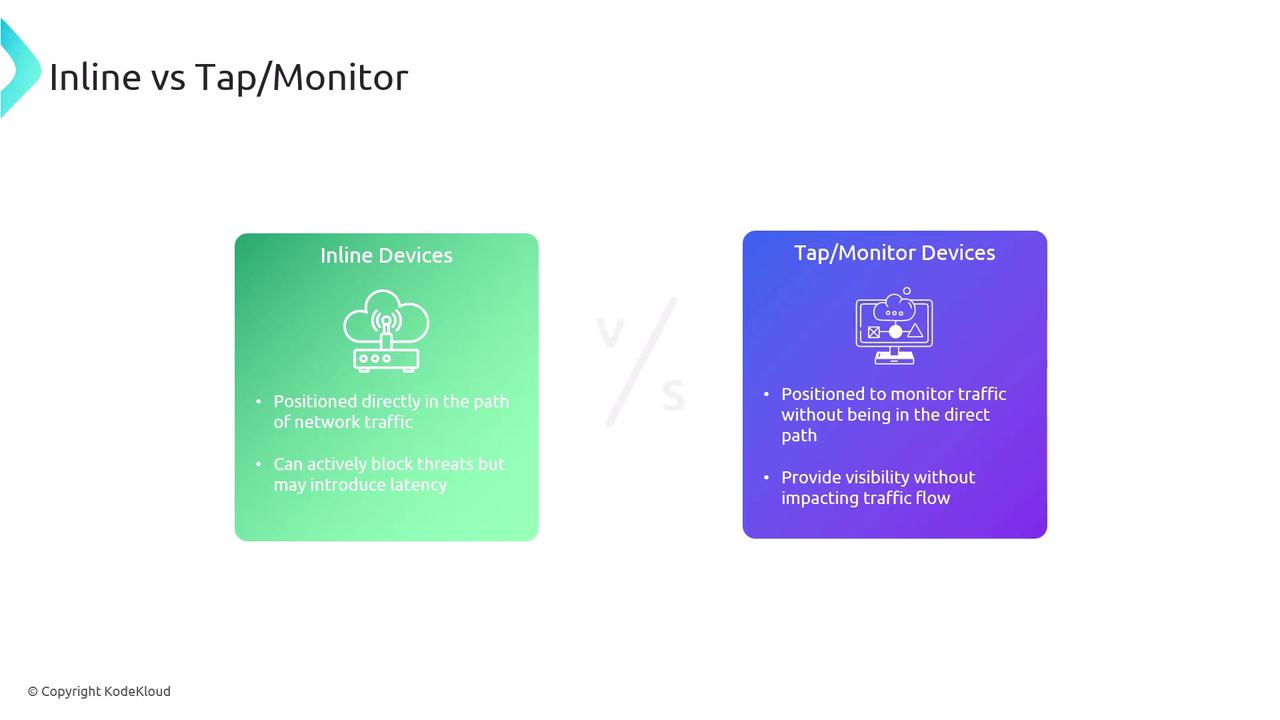
- Inline vs. Tap/Monitor Devices:
Inline devices are installed directly into the network traffic flow and actively block threats, though they may introduce latency. In contrast, tap/monitor devices observe the traffic without affecting its flow, making them ideal for passive surveillance.
Network Appliances
Network appliances are specialized devices that enhance both security and operational efficiency. Key types include:- Jump Servers:
Jump servers act as secure intermediaries, enabling controlled access to devices in segregated security zones. They are particularly useful for accessing systems within a demilitarized zone (DMZ).

- Proxy Servers:
Proxy servers serve as intermediaries between clients and the internet, providing anonymity for users while enforcing security policies. They help administrators monitor and control web traffic effectively.
- Load Balancers:
Load balancers distribute incoming network traffic across multiple servers, ensuring high reliability and performance through redundancy. They play a vital role in maintaining balanced traffic distribution among web servers.
- Sensors:
Sensors are designed to collect and analyze network data in real time. They help detect anomalies that might indicate a security breach, offering early warnings of potential threats.
Firewall Types
Firewalls are a cornerstone of network defense, and understanding their various types is key to deploying effective security measures. The primary categories include:- Web Application Firewall (WAF):
WAFs focus on protecting web applications by filtering and monitoring HTTP traffic. They defend against attacks like SQL injections and cross-site scripting (XSS).
- Unified Threat Management (UTM):
UTM devices combine multiple security features—including firewalling, antivirus, and intrusion prevention—into a single solution. This integration simplifies the management of complex security needs.
- Next-Generation Firewalls (NGFW):
NGFWs enhance traditional firewall capabilities with features like application awareness, integrated intrusion prevention, deep packet inspection, and advanced threat protection. They effectively counter modern cyber threats.
-
Layer Four Firewalls:
These firewalls manage traffic based on transport layer information, such as ports. -
Layer Seven Firewalls:
Operating at the application layer, these firewalls provide granular control over application traffic, which allows them to block specific application-level threats.
Conclusion
In conclusion, securing enterprise infrastructure requires a holistic approach that encompasses device placement, attack surface minimization, secure connectivity, understanding failure modes, categorizing device attributes, leveraging network appliances, and selecting the right firewall technologies. Implementing these best practices will not only safeguard your critical assets but also strengthen your organization’s overall security posture.
For more detailed information on implementing these security strategies, consider exploring additional resources like Kubernetes Documentation and Docker Hub.