Infrastructure Considerations
A secure infrastructure starts with robust architectural planning. Key considerations include:- Defining and enforcing security zones.
- Minimizing the attack surface to reduce vulnerabilities.
- Physically isolating resources to limit potential risks.
- Designing the network with careful attention to routing and switching.
Ensure that security zones are clearly defined and maintained. This limits lateral movement in the event of a breach and significantly improves your overall security posture.
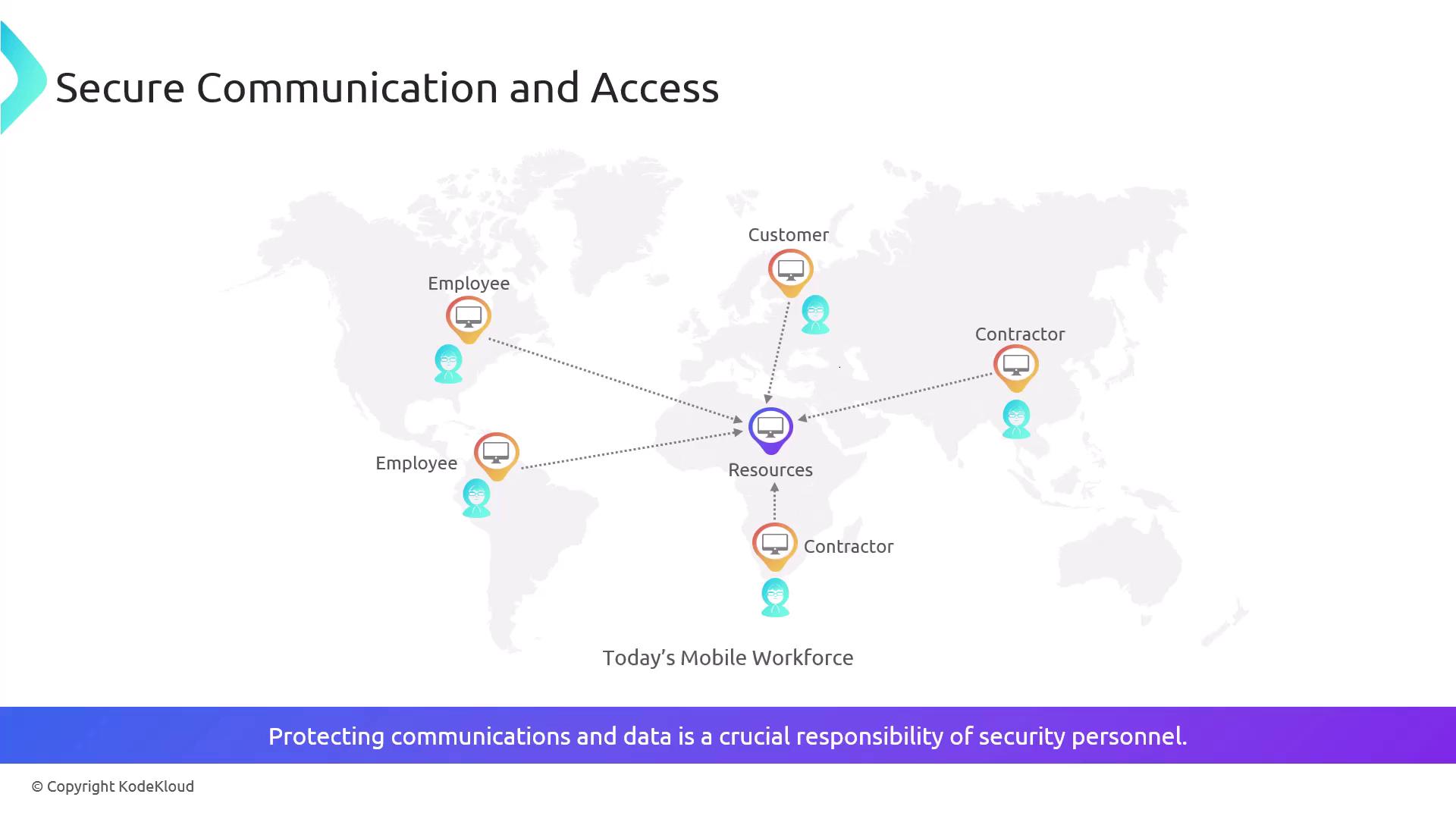
Secure Remote Access
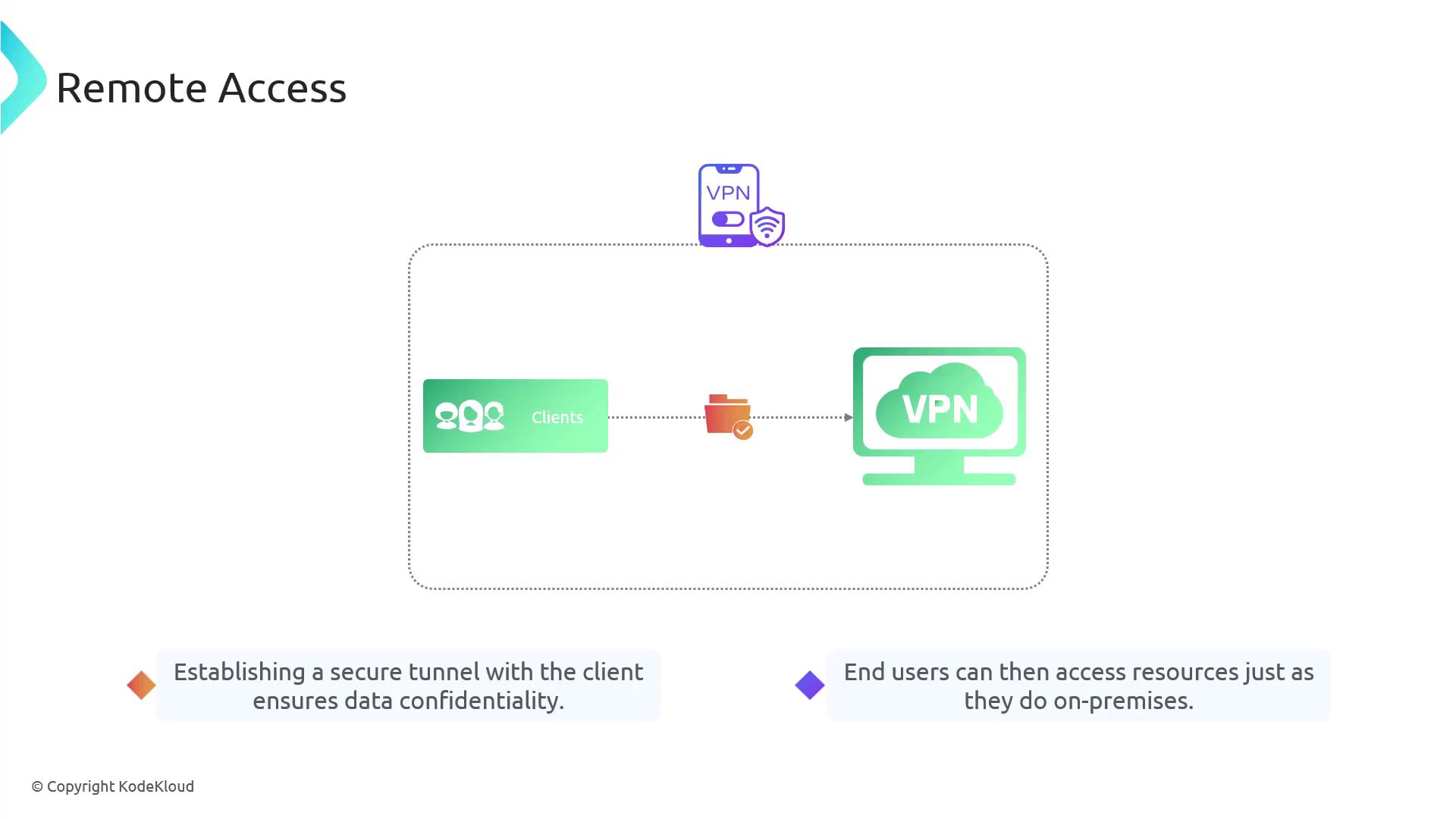
Remote access allows users to connect to internal network resources from external locations. Modern remote access is typically secured with Virtual Private Networks (VPNs). In a remote access VPN arrangement:- Clients establish a connection with a VPN gateway or another designated edge device.
- A secure tunnel is created between the client and the gateway, ensuring data confidentiality.
- Once the tunnel is established, users access internal resources as if they were directly on the internal network.
Always verify that your VPN solution is up to date and properly configured to prevent unauthorized access.
In-Band vs. Out-of-Band Management
Efficient network management hinges on understanding the two methods for device management: in-band and out-of-band.In-Band Management
In-band management uses the same communication channel that carries regular data traffic to manage network devices. For example, an administrator might SSH into a router over the same network used for business operations.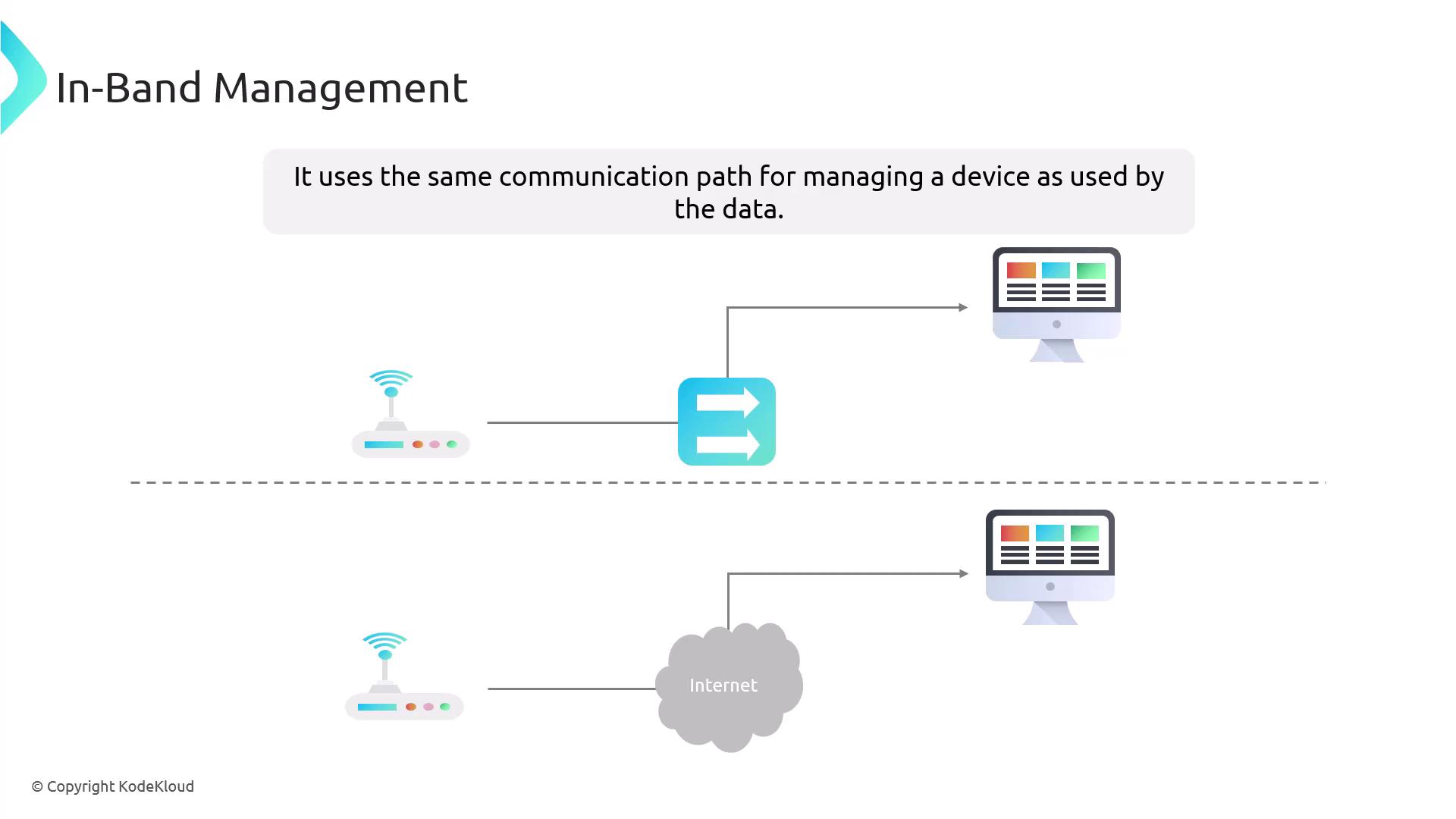
Out-of-Band Management
Out-of-band management provides a solution by using a dedicated communication channel separate from the primary data network. This independent channel, which can involve a modem or a serial connection, ensures that network management remains accessible even if the main IP network experiences issues.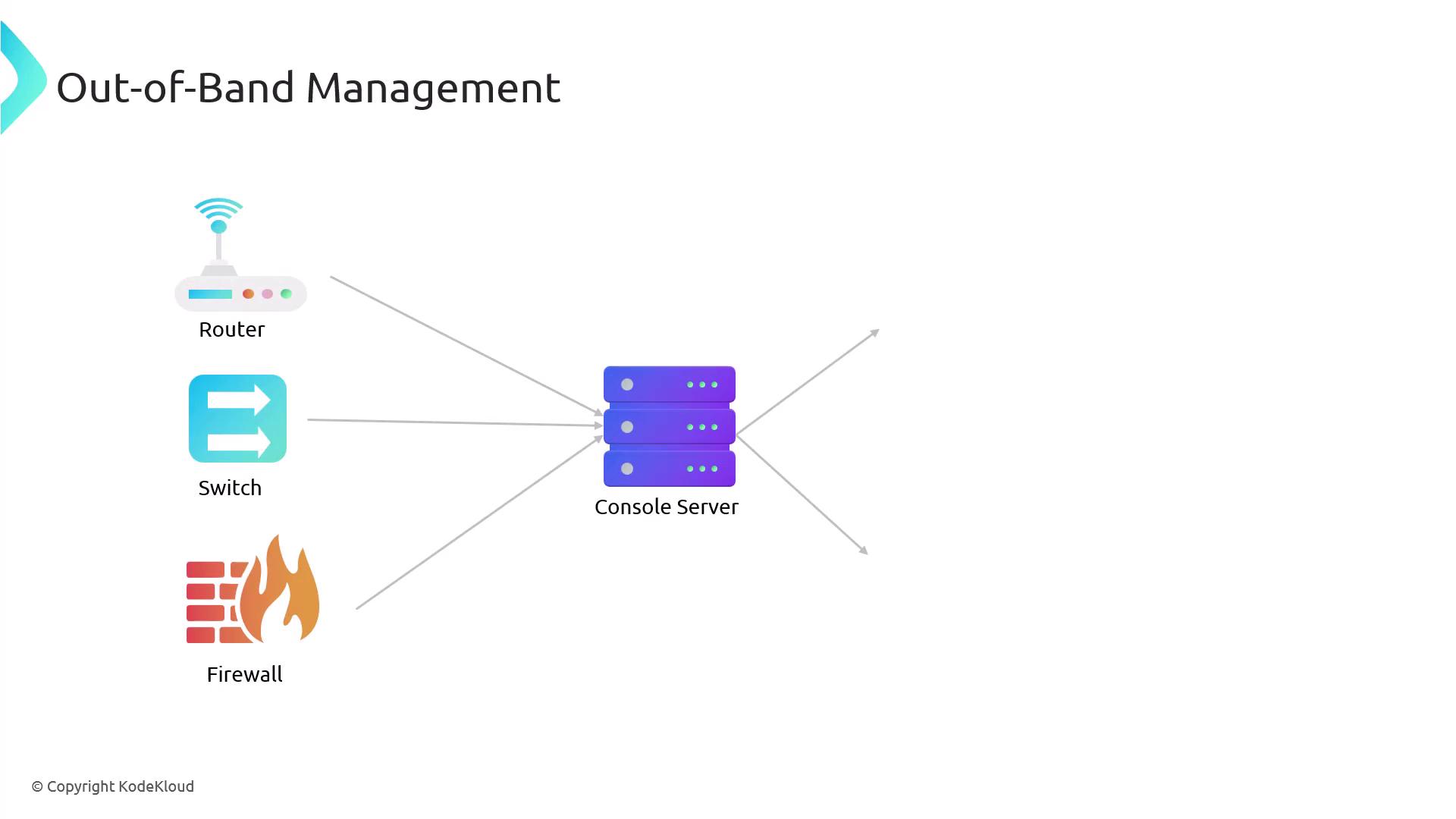
Out-of-band management is especially valuable in high-security environments where maintaining continuous access to management interfaces is crucial.
Jump Servers
Jump servers add an extra layer of security by acting as controlled gateways between users and internal network resources. Instead of granting direct access to sensitive systems, users first connect to the jump server, which then provides restricted and monitored access to the desired resources. This strategy limits exposure and secures access to sensitive ports such as RDP and SSH.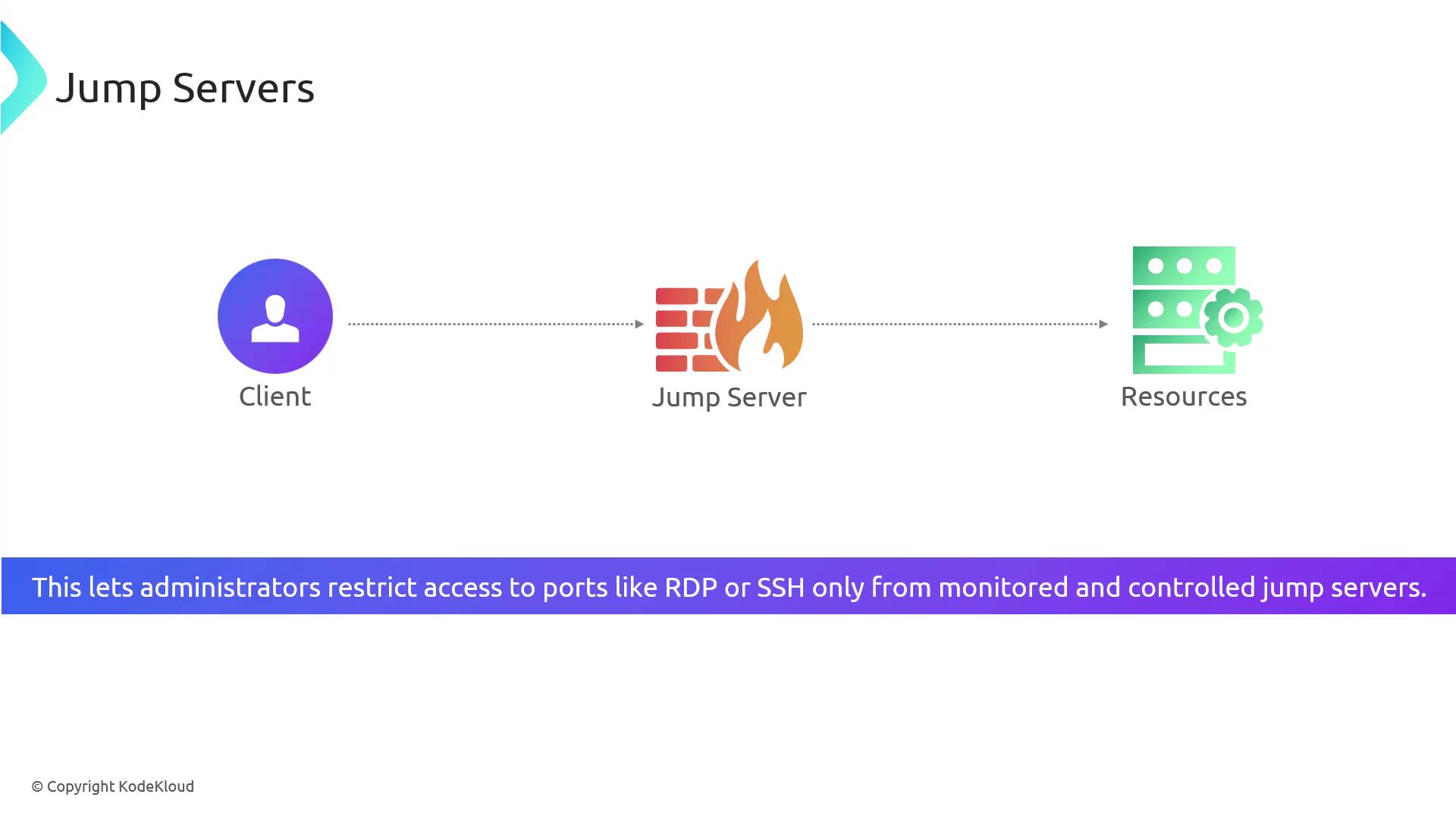
Always ensure that jump servers are hardened and securely configured to prevent them from becoming a vulnerability themselves.