1. Risk Registers
A risk register is a vital tool for documenting and tracking risks, their potential impacts, and the measures taken to mitigate them. It centralizes risk information, enforces accountability, and facilitates continuous monitoring. A well-maintained risk register ensures that all identified risks are visible, that responsibilities are clearly assigned, and that risk mitigation strategies are reviewed on an ongoing basis.
2. Key Risk Indicators
Key risk indicators (KRIs) are quantifiable metrics that help monitor and evaluate the level of risk exposure in real time. KRIs provide early warning signals of emerging issues, enabling organizations to act swiftly before risks escalate into significant problems. By tracking these measurable indicators, organizations can assess risk levels more accurately and take proactive steps to mitigate potential impacts.3. Risk Owners
Assigning risk owners is crucial for clear accountability within a risk management framework. Risk owners, whether individuals or teams, are tasked with the responsibility of monitoring and managing designated risks. For example, appointing the Chief Information Security Officer to oversee cybersecurity risks ensures timely corrective action is taken. This approach reinforces proactive management and continuous oversight.
4. Risk Threshold
The risk threshold defines the level of risk an organization is willing to tolerate before initiating mitigation measures. It plays a critical role in decision-making and prioritization by guiding when to escalate risk management efforts. By establishing a clear threshold, organizations can determine which risks require immediate attention based on their potential impacts.
5. Risk Tolerance
Risk tolerance describes the acceptable degree of variability in outcomes an organization is prepared to endure while pursuing its objectives. It provides clear guidelines on the level of risk that can be assumed in different scenarios and helps balance risk with potential rewards. For instance, an organization with a high tolerance for risk may engage in high-risk, high-reward projects, whereas a conservative organization might prefer more secure investments.
6. Risk Appetite
Risk appetite refers to the overall amount and type of risk an organization is prepared to pursue or retain in order to achieve its strategic objectives. It aligns risk-taking with organizational goals and plays a key role in resource allocation. There are three primary risk appetite categories:-
Expansionary:
Organizations with an expansionary risk appetite embrace high levels of risk for aggressive growth and innovation. For example, a tech startup might invest heavily in cutting-edge research and development, accepting significant financial risk for the potential of breakthrough products. -
Conservative:
A conservative risk appetite indicates a preference for stability and capital preservation. Such organizations focus on proven strategies and incremental growth, carefully limiting exposure to risks.

- Neutral:
Organizations adopting a neutral risk appetite strike a balance between risk and reward. They pursue opportunities that promise steady growth while maintaining a careful approach to risk management.
7. Integrating Risk Management Processes
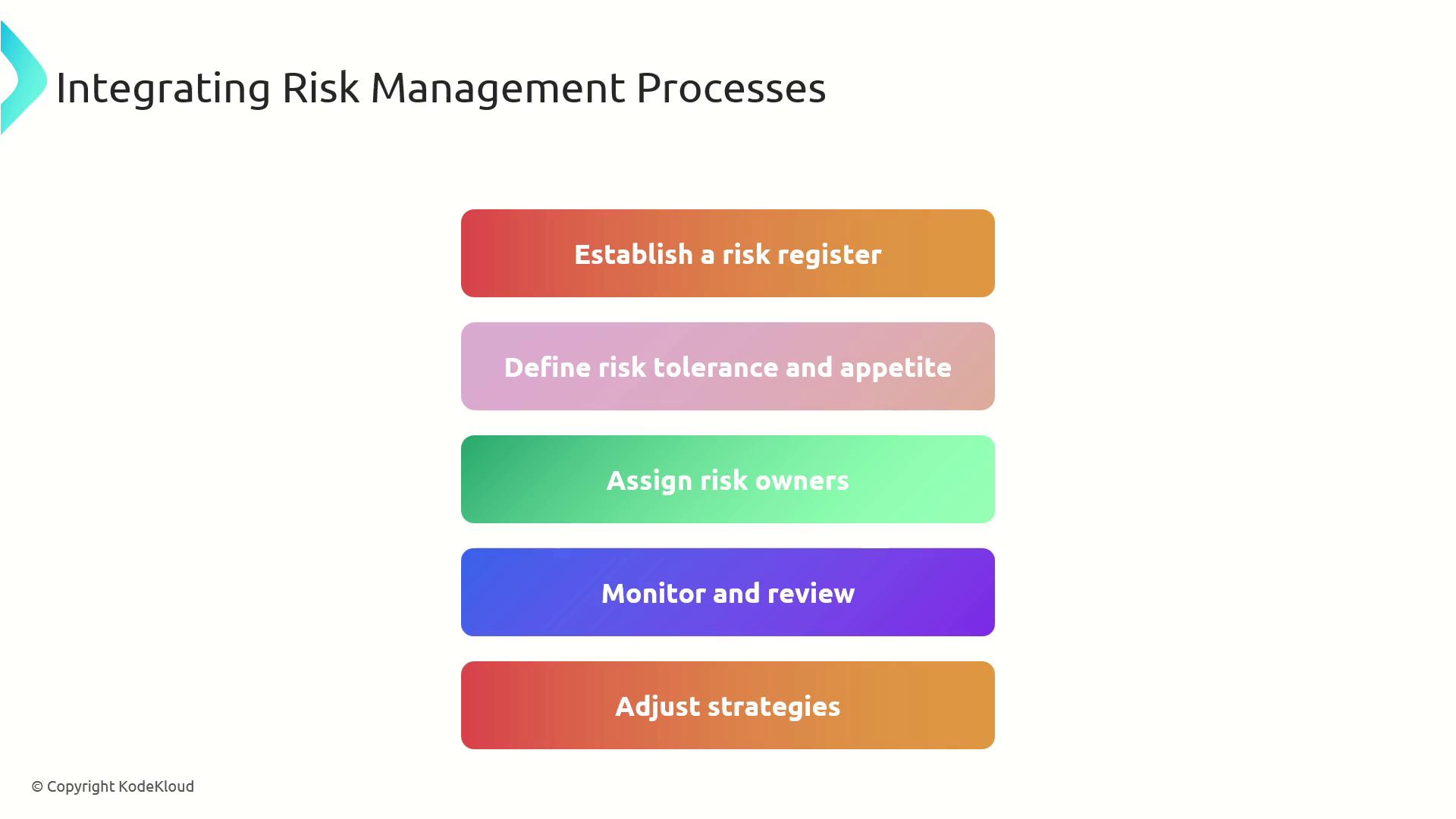
Integrating risk management processes into organizational strategy involves the following key steps:-
Establish the Risk Register:
Document all identified risks along with their key risk indicators, risk owners, and respective thresholds. -
Define Risk Tolerance and Appetite:
Clearly articulate the organization’s acceptable levels of risk to steer decision-making. -
Assign Risk Owners:
Allocate specific risks to individuals or teams responsible for their management and mitigation. -
Monitor and Review Risks:
Continuously track risk indicators and perform regular reviews of the risk register to ensure ongoing effectiveness. -
Adjust Strategies:
Update and refine risk management strategies based on evolving risks and changing organizational priorities.
Conclusion
Effective risk management hinges on understanding and integrating several key components—maintaining a detailed risk register, monitoring key risk indicators, and assigning clear accountability through risk owners. Additionally, defining risk thresholds, risk tolerance, and risk appetite ensures that risk-taking aligns with strategic objectives. With these processes in place, organizations can proactively identify, assess, and mitigate risks, ensuring resilience in the face of uncertainties.
For additional insights into risk management best practices, consider exploring related resources such as Kubernetes Documentation and Docker Hub.