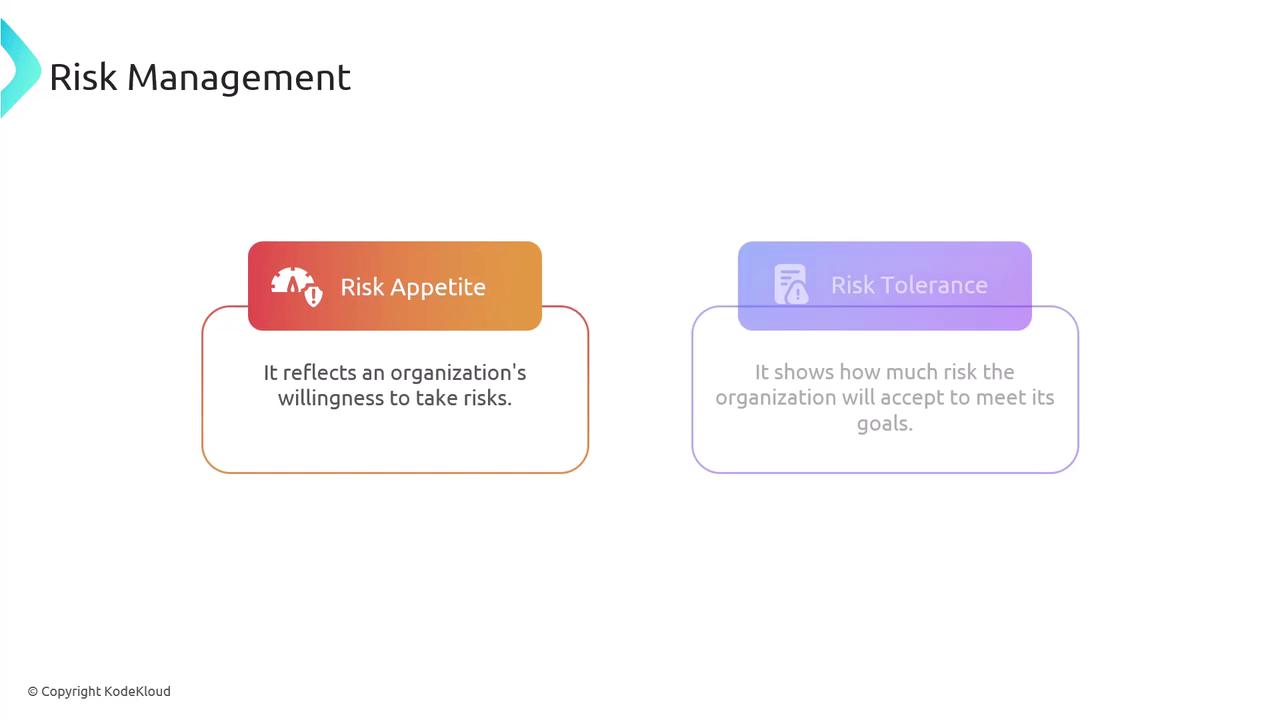
There are four primary risk management strategies: transfer, accept, avoid, and mitigate. Each strategy plays a unique role in addressing the various types of risks an organization may encounter.
Risk Management Strategies Explained
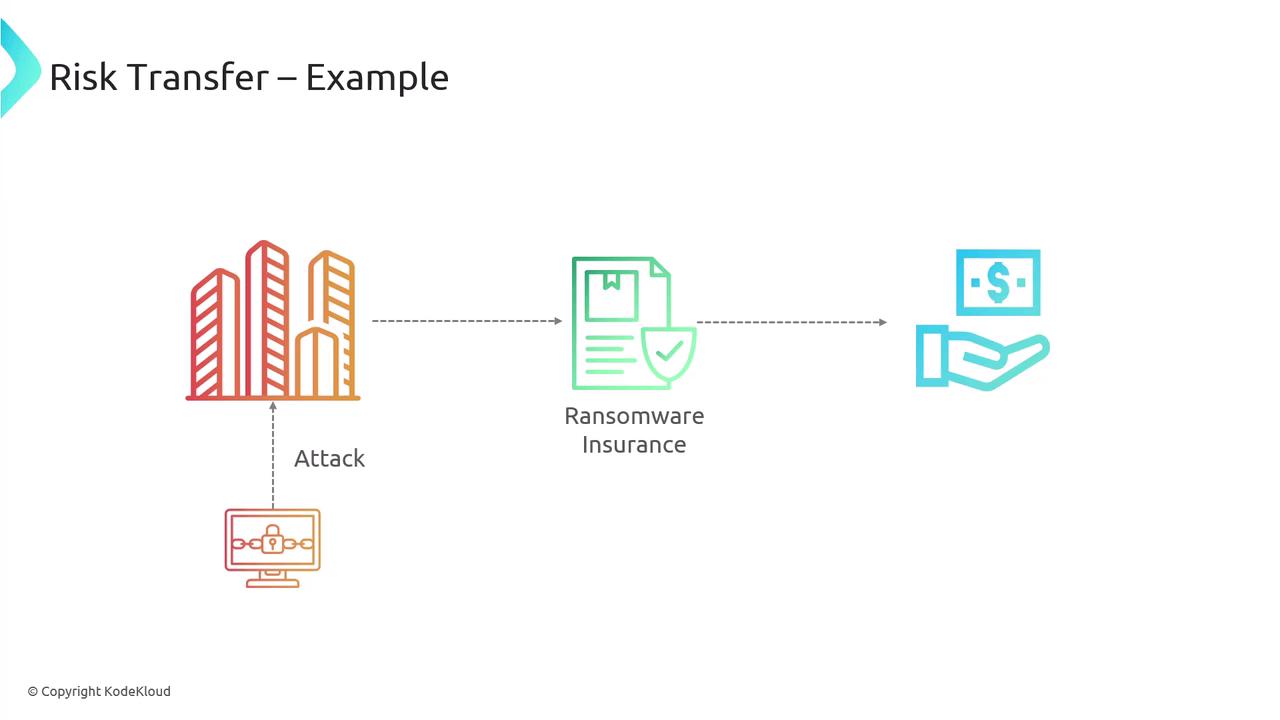
- Risk Transfer
This strategy involves shifting the risk to a third party. A common example is purchasing insurance. For instance, many companies buy ransomware insurance to cover any costs associated with a cyber-attack, effectively transferring the financial risk.
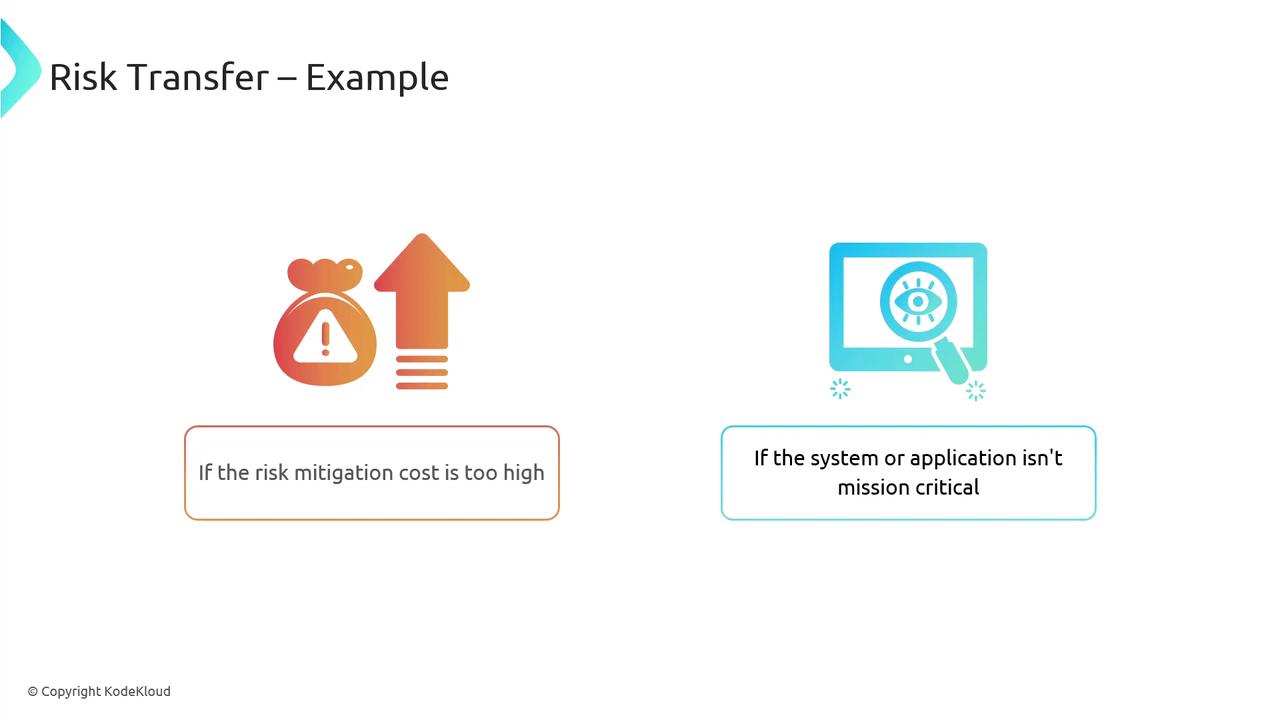
- Risk Acceptance
When the cost of mitigating a risk is too high or the asset is not critical, the organization might decide to accept the risk. This means recognizing the possibility of a threat and choosing not to invest further in risk reduction.
-
Risk Avoidance
In this approach, an organization opts out of using a technology, process, or system that may expose it to potential risks. By avoiding the risky element altogether, the organization sidesteps associated vulnerabilities. -
Risk Mitigation
Mitigation focuses on reducing either the likelihood or the impact of potential risks. For example, deploying a web application firewall that works alongside input validation and code reviews can significantly decrease the chance of suffering a SQL injection attack.

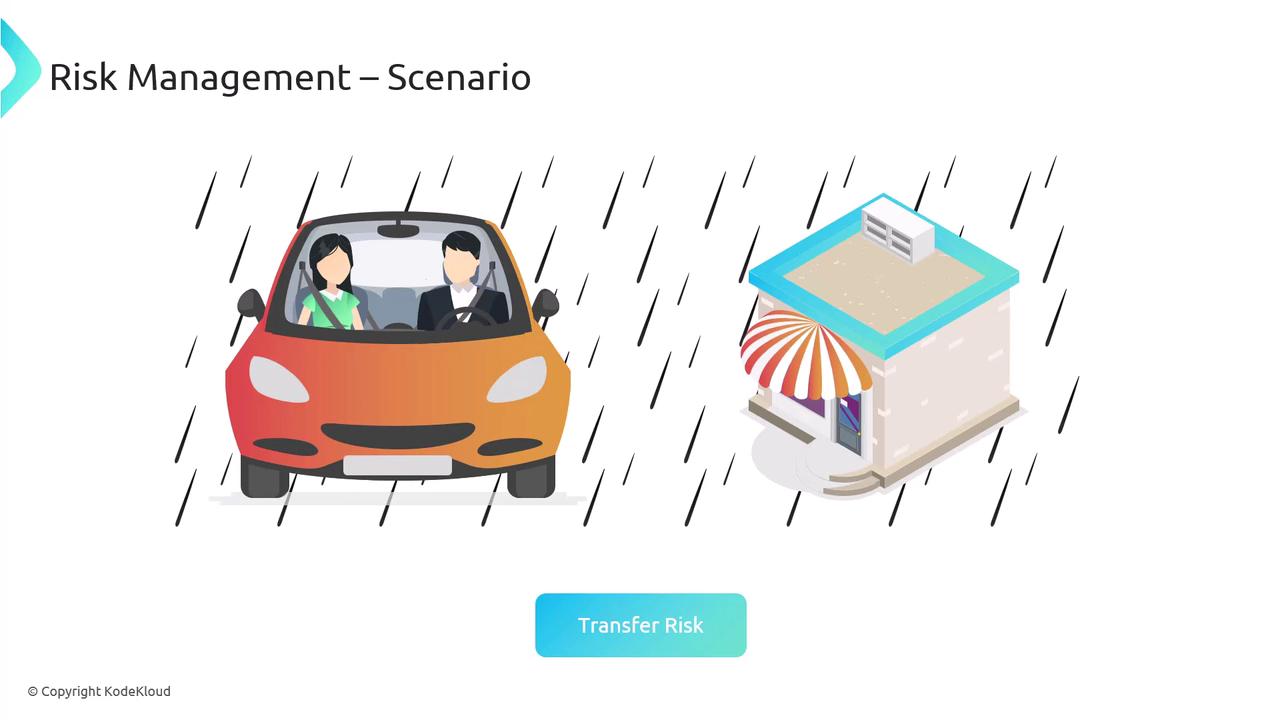
An Illustrative Scenario
Imagine you are dressed in your finest attire for an important event where you will be honored and photographed. On your way, you plan to stop by a store. Suddenly, a heavy rainstorm starts before you can get out of the car. Exiting the car in the rain poses a risk to your appearance. Here are your options:- Avoid the Risk: Do not stop at the store and continue driving.
- Accept the Risk: Exit the car despite the rain and get wet.
- Mitigate the Risk: Use an umbrella or other protective measures before stepping out.
- Transfer the Risk: Have a passenger or someone else run the errand on your behalf.