CompTIA Security+ Certification
Security Management
Security Governance
Welcome back. In this lesson, we explore the crucial elements of effective security governance. This framework ensures that your organization’s security strategies align with its business objectives and regulatory requirements. In particular, we will discuss three key procedures that underpin robust security governance: Change Management, Onboarding and Offboarding, and Playbooks. By the end of this lesson, you will understand how these procedures contribute to a strong security posture and how to implement them effectively.

Did you know?
Effective security governance not only protects your organization but also enhances operational efficiency by aligning security with business strategies.
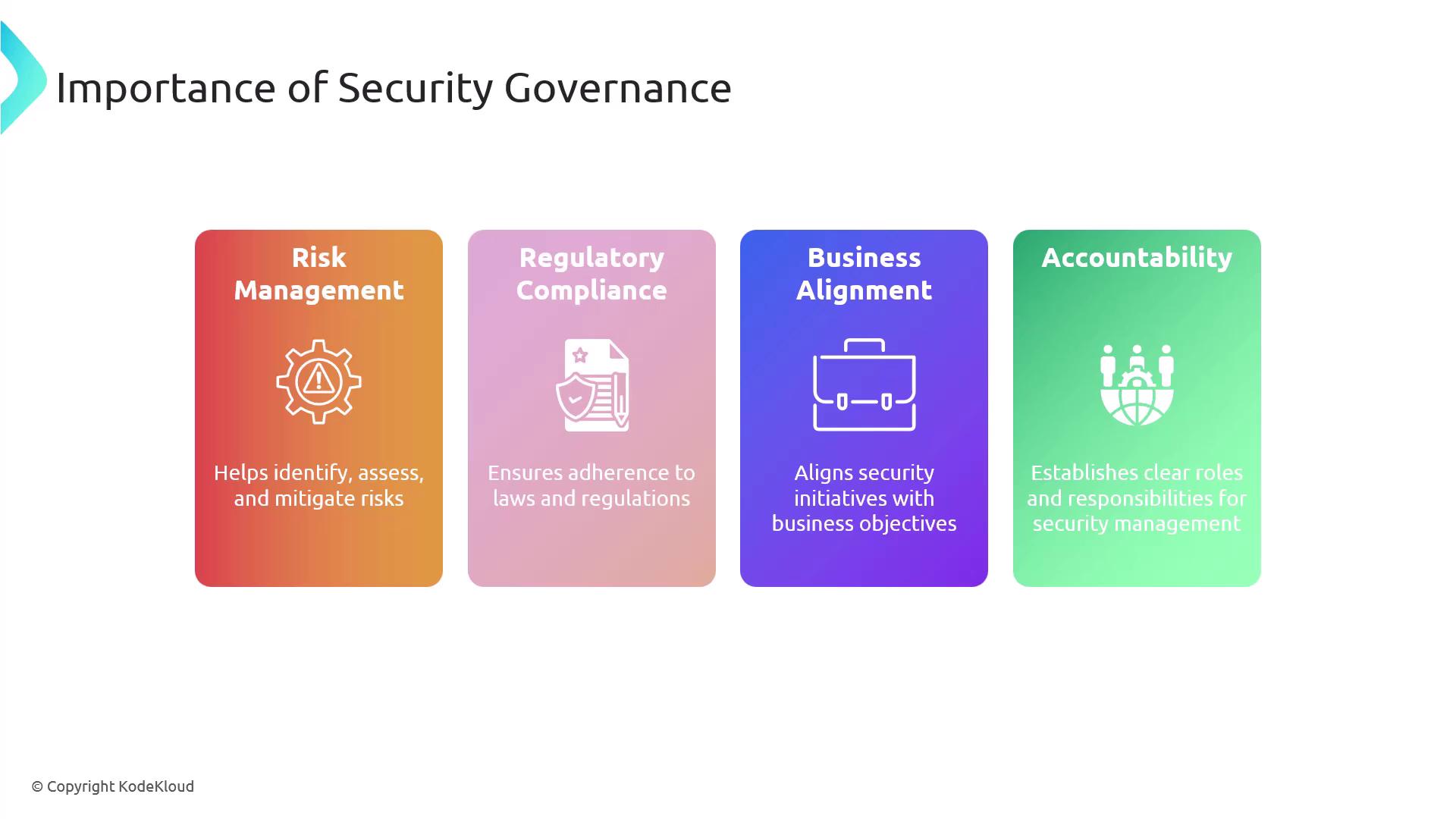
Importance of Security Governance
Security governance involves the practices essential for managing and guiding an organization’s security posture. It ensures that security strategies are aligned with business goals, comply with legal and regulatory mandates, and safeguard against potential risks. Key benefits include:
- Risk Management: Identifying, assessing, and mitigating risks in a proactive manner.
- Regulatory Compliance: Meeting legal and statutory requirements.
- Business Alignment: Ensuring that security initiatives support organizational objectives.
- Accountability: Clarifying roles and responsibilities in security management.
The three fundamental procedures that fortify security governance are:
- Change Management
- Onboarding and Offboarding
- Playbooks
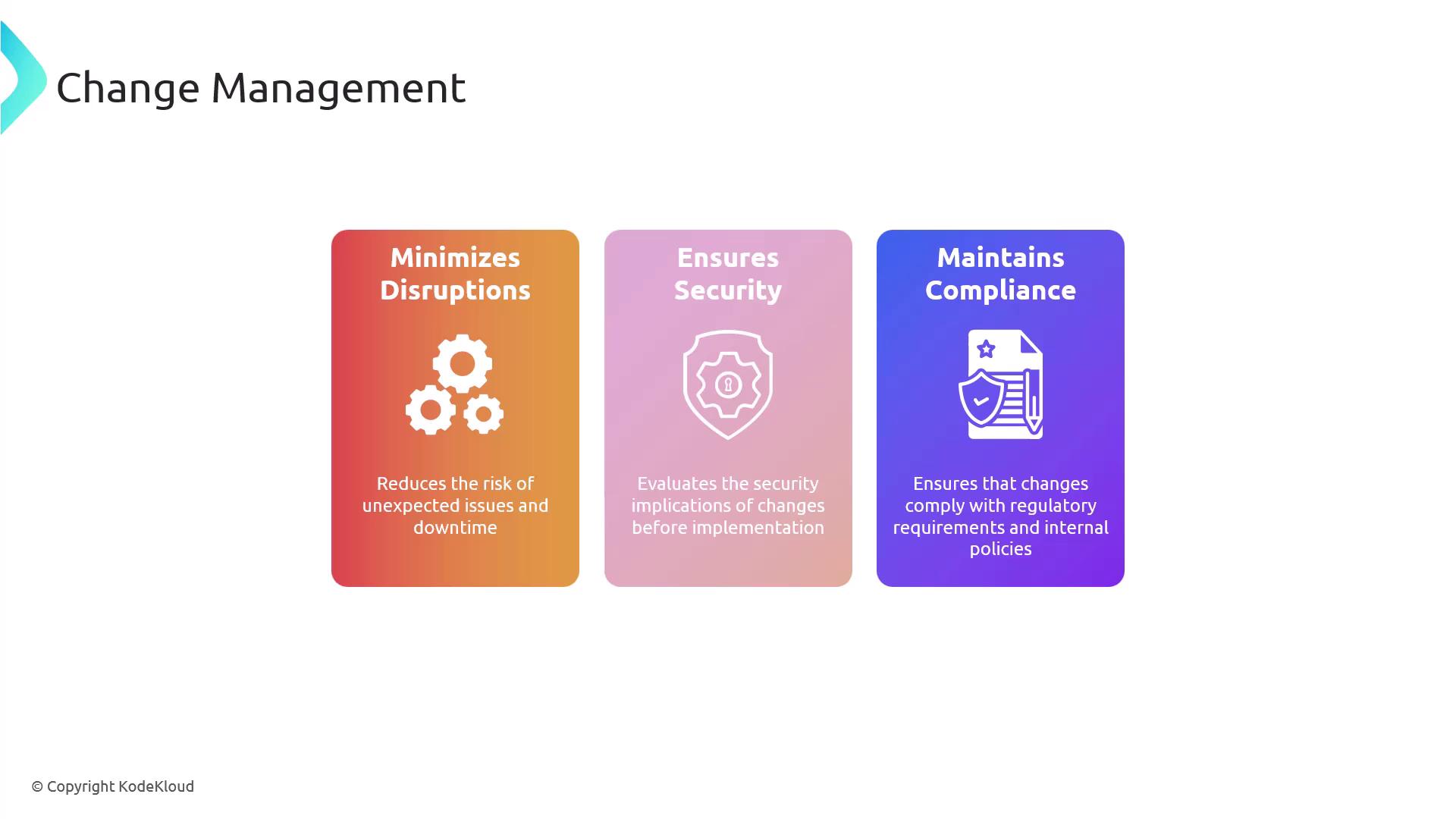
Change Management
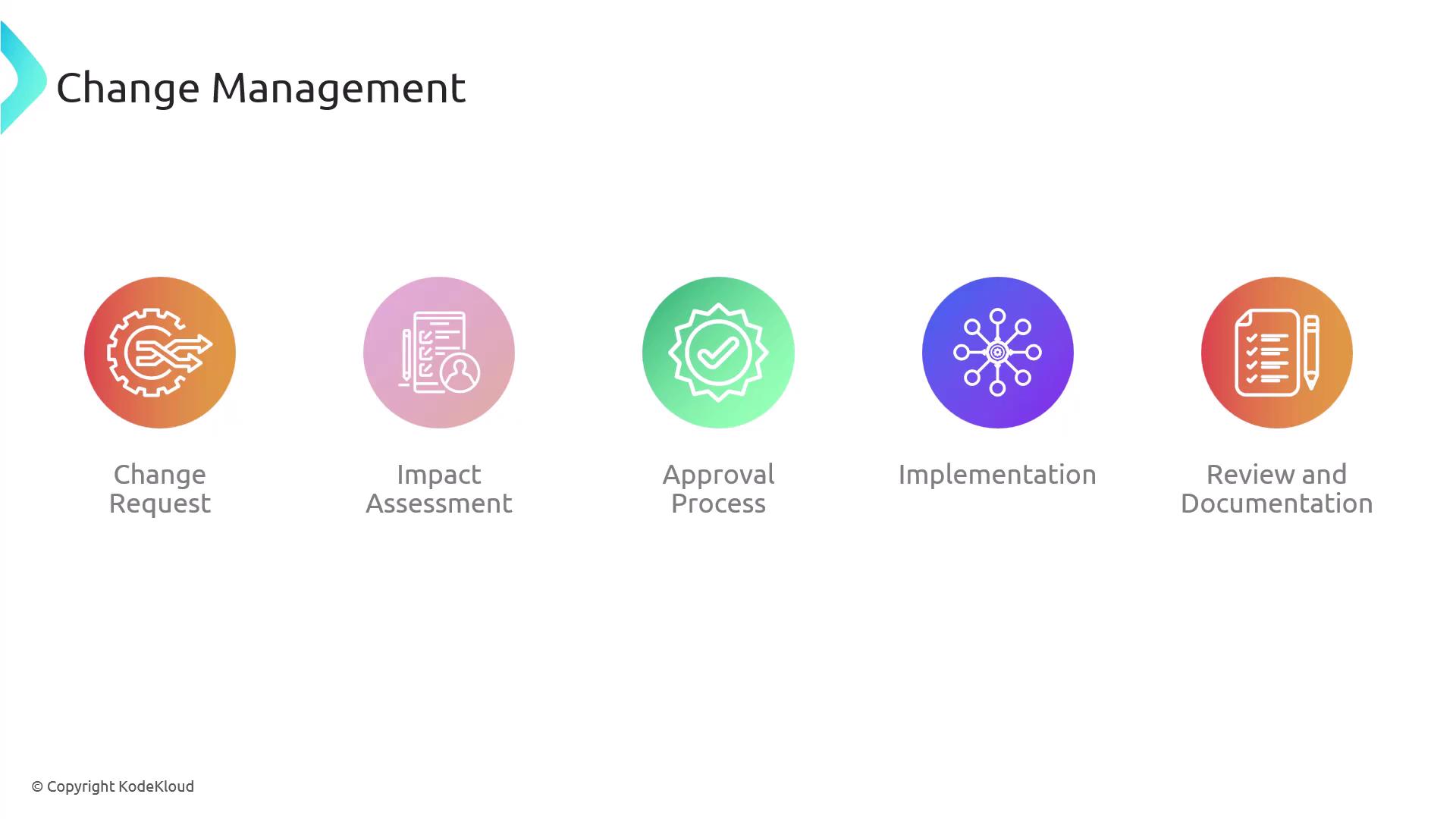
Change management is a structured process for managing updates and modifications to IT systems. It minimizes disruptions by evaluating the security implications of changes before implementation, thus maintaining system compliance and integrity. The key steps include:
- Change Requests: Formal documentation that describes the proposed change, its rationale, and the expected impact.
- Impact Assessment: Evaluating how the proposed change affects systems, security, and business operations.
- Approval Process: Involving relevant stakeholders to review and authorize the change.
- Implementation: Executing the change in a controlled and systematic manner.
- Review and Documentation: Performing a post-implementation review to document outcomes and assess the overall impact.
For example, during the deployment of software updates, a rigorous change management process ensures every update is tested, approved, and thoroughly documented.
Onboarding and Offboarding
Onboarding integrates new employees into the organization, while offboarding efficiently manages employee departures. Both processes are critical: onboarding ensures that new hires receive the proper access and training, and offboarding guarantees that departing employees no longer have access to sensitive systems. This not only satisfies regulatory requirements but also protects against insider threats and potential data breaches.
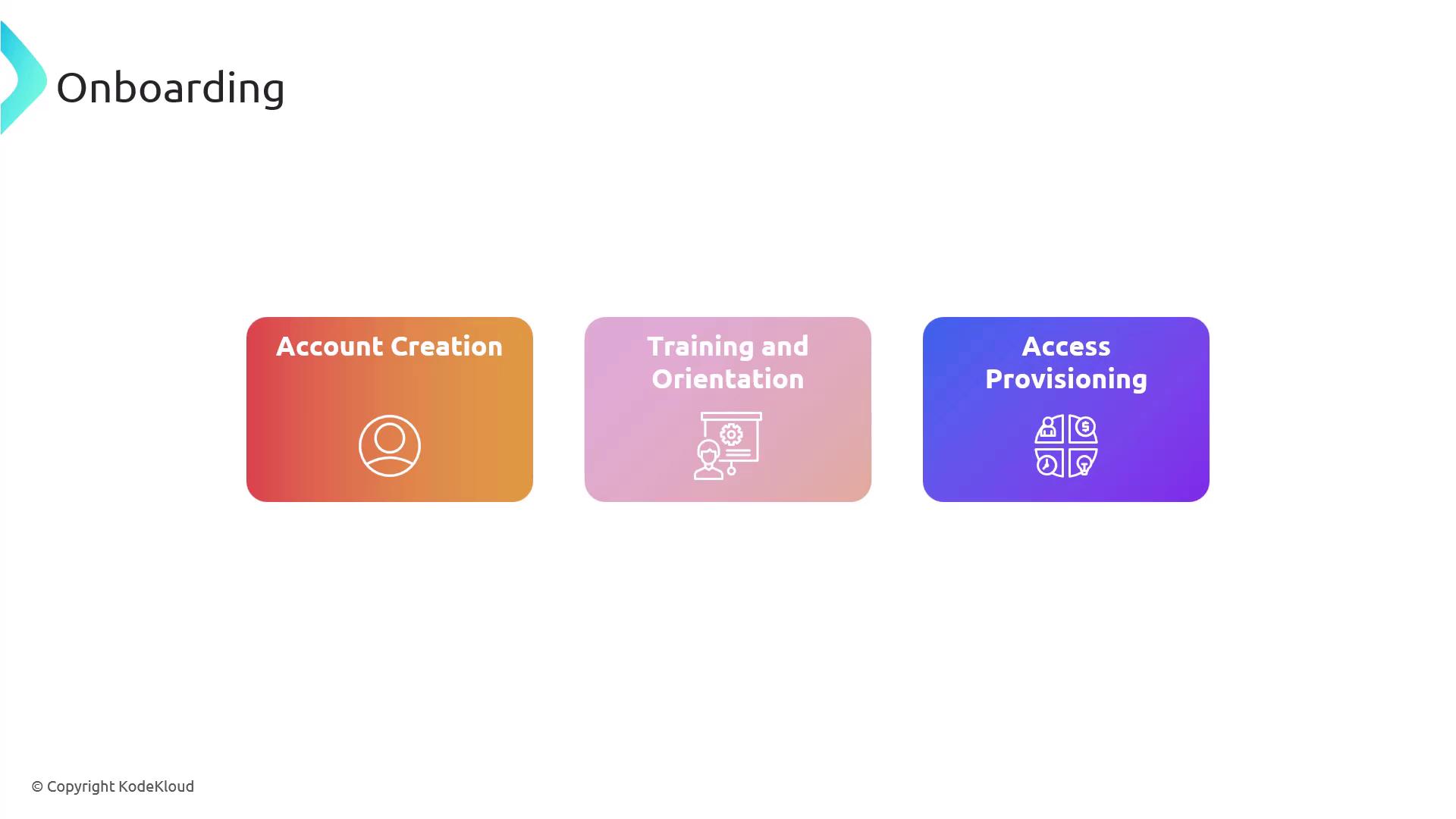
Onboarding Process
The typical onboarding process includes:
- Account Creation: Setting up user accounts and assigning the appropriate rights.
- Training and Orientation: Delivering security training and familiarizing new hires with company policies.
- Access Provisioning: Granting access to the resources and systems required for the job.
Offboarding Process
Key steps in the offboarding process involve:
- Access Revocation: Removing system access and disabling user accounts.
- Data Handling: Securing or transferring data managed by the departing employee.
- Exit Interview: Conducting an interview to address any security concerns and gather feedback.
Reminder
It is critical to revoke access immediately during offboarding to prevent potential data breaches and insider threats.
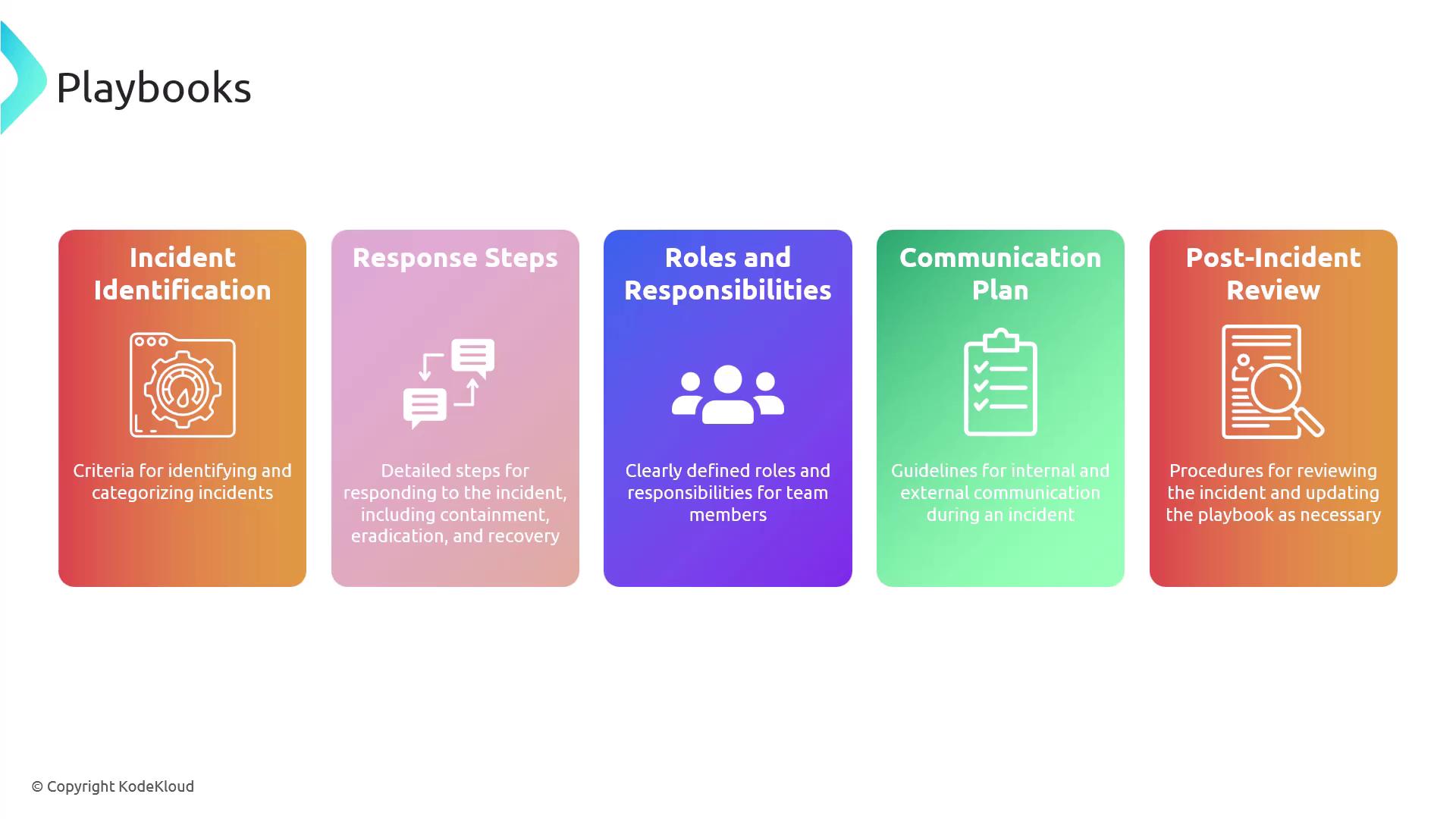
Playbooks
Playbooks are comprehensive guides that detail the step-by-step procedures for responding to specific security incidents or performing routine security tasks. They provide consistency in responses, facilitate quick action during incidents, and serve as a training resource.
Key elements of an effective playbook include:
- Incident Identification: Establishing criteria for recognizing and categorizing incidents.
- Response Steps: Detailing the actions required for containment, eradication, and recovery.
- Roles and Responsibilities: Clearly defining team roles during incident management.
- Communication Plan: Setting internal and external communication protocols during an incident.
- Post-Incident Review: Conducting a review after the incident to update and improve the playbook.
For example, a playbook tailored to a phishing attack would offer clear guidelines for an immediate response, mitigating potential damages effectively.
Conclusion
Effective security governance is essential for maintaining a robust organizational security posture. By implementing structured procedures such as change management, onboarding/offboarding, and playbooks, organizations can mitigate risks, ensure regulatory compliance, and enhance overall operational resilience.

Thank you for reading this in-depth lesson on security governance. For further information on establishing a secure operational framework, be sure to review our related guides and best practices.
Watch Video
Watch video content