CompTIA Security+ Certification
Security Management
Security Program Management and Oversight
Welcome to the final section of our CompTIA Security+ preparation series. In this segment, we dive into the critical components of security program management and oversight, covering essential topics such as security governance, risk management, compliance, audits and assessments, and security awareness practices. These subjects are vital for managing an organization’s security posture, regardless of size, and are especially significant for individuals preparing for the Security+ certification exam.

Below is an overview of the key elements in this domain.
Security Insight
Understanding and integrating robust security program management practices is essential for protecting your organization's digital assets and ensuring compliance with emerging regulations.
Security Governance
Security governance, as defined by CISA, represents a comprehensive cybersecurity strategy that aligns with an organization's operational framework to prevent activity interruptions caused by cyber threats or attacks. Effective security governance involves a blend of guidelines, policies, standards, procedures, and external factors like vendor management.
Key aspects of security governance include:
- Risk Management: Continuously identify and mitigate potential security risks.
- Organizational Structures: Leverage boards, committees, and regulatory agencies to facilitate oversight.
- Data Management: Understand roles and responsibilities related to the collection, processing, and storage of personal data.
It is crucial to continually monitor and adjust these measures, as the cybersecurity landscape is always evolving.
Guidelines, Policies, Procedures, and Standards
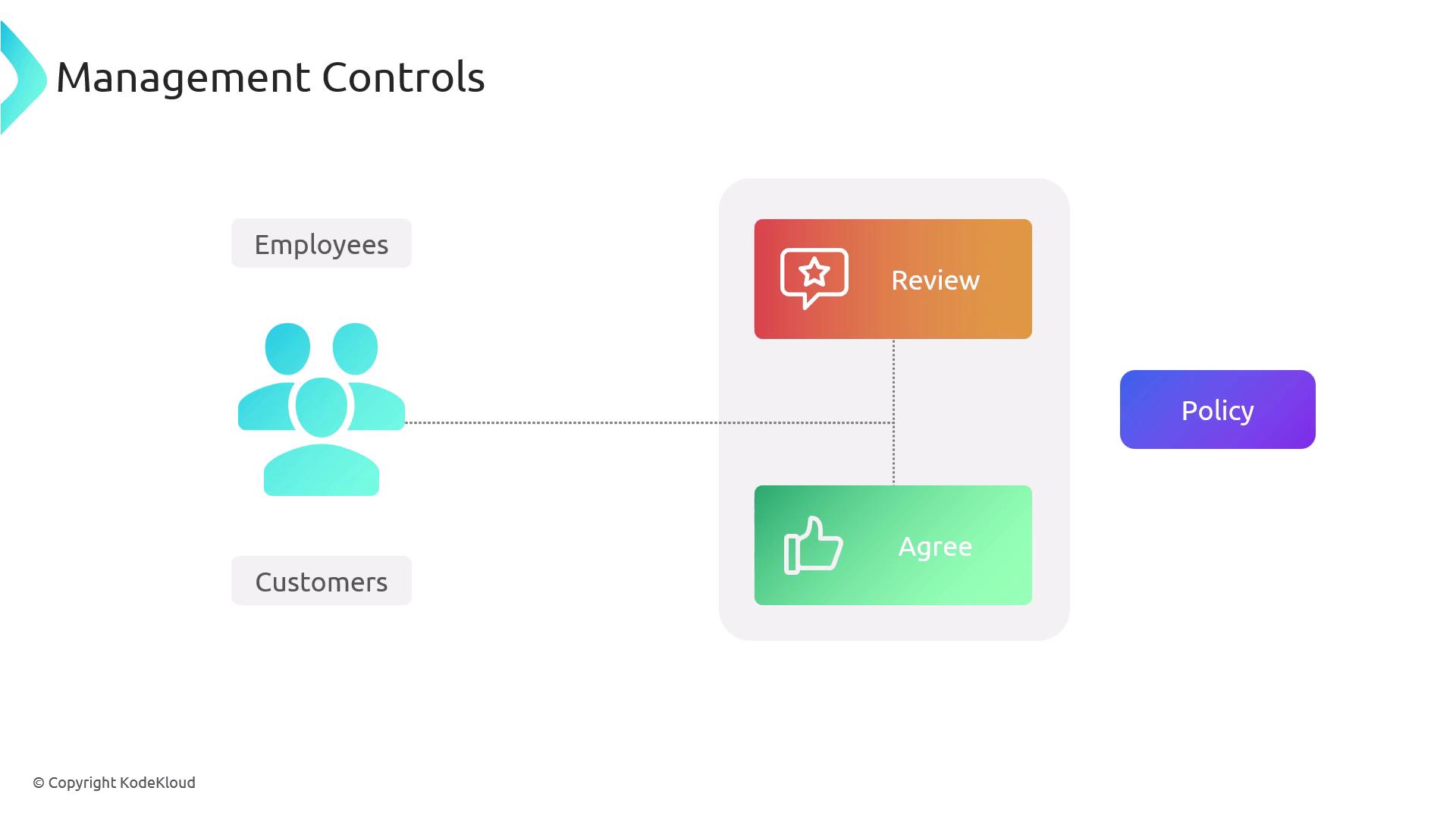
When establishing effective cybersecurity practices, organizations must develop comprehensive guidelines, policies, procedures, and standards. These components fall under various categories of controls, including management controls, which direct employee behavior and mitigate human-related vulnerabilities.

Management controls are vital because human error can often be the weakest link in an organization’s security chain. Implementing clear policies—such as an acceptable use policy—is key to guiding employees and, in some cases, customers to use systems and applications securely.
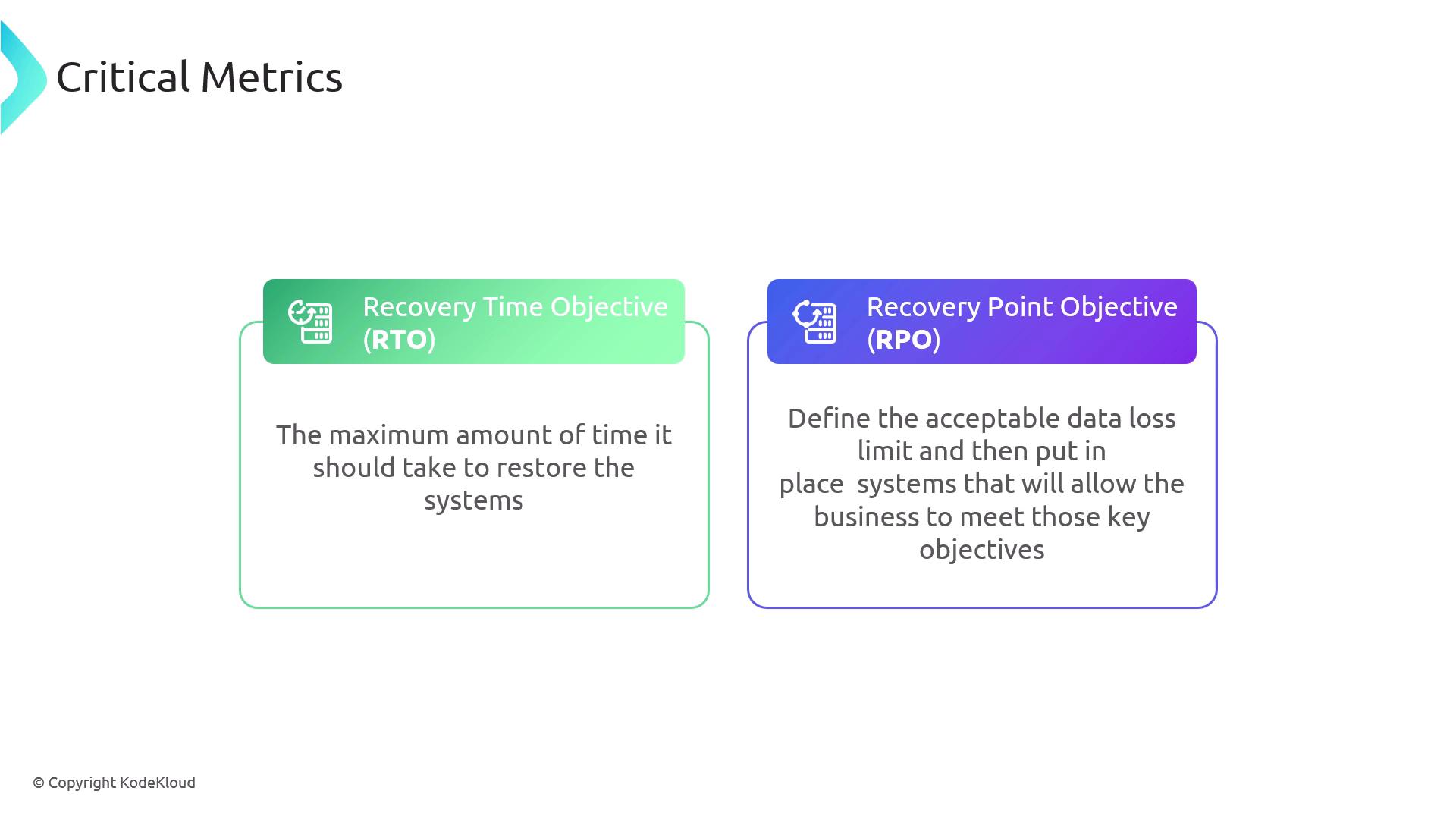
In addition to these measures, management should ensure the existence of business continuity and disaster recovery plans. Regular disaster recovery testing confirms that the organization can swiftly recover from unexpected disruptions. Key metrics include:
| Metric | Definition |
|---|---|
| Recovery Time Objective (RTO) | The maximum acceptable time to restore systems after a disruption. |
| Recovery Point Objective (RPO) | The acceptable limit of data loss measured in time. |
Disaster Recovery Tip
Scheduling regular disaster recovery tests and reviewing outcomes are essential practices to ensure that recovery plans remain effective and up to date.
Integrating the Software Development Lifecycle (SDLC) in Cybersecurity
Although the Software Development Lifecycle (SDLC) may seem unrelated to security at first glance, it is an integral component in mitigating application-related threats like SQL injection, buffer overflows, and vulnerabilities from outdated code. Incorporating security best practices—such as peer reviews and robust input validation—within the SDLC can significantly diminish these risks.
Integrating SDLC principles from the early stages of development—rather than addressing vulnerabilities post-deployment—is crucial for creating a secure coding environment. Equally important is the establishment of security incident playbooks to guide your team during cybersecurity events, thereby minimizing potential damage.
By adopting these practices, organizations not only enhance their cybersecurity posture but also ensure compliance and protection for sensitive data.
This concludes our comprehensive guide on Security Program Management and Oversight. Implementing these strategies is crucial to safeguarding your organization against evolving cyber threats while maintaining regulatory compliance. For more insights on security best-practices and certification prep, explore additional resources and stay updated with the latest industry trends.
Watch Video
Watch video content