CompTIA Security+ Certification
Security Operations
Hardware Software and Data Asset Management
Effective management of hardware, software, and data assets is essential to protect your organization's sensitive information. In this lesson, we review the best practices for asset management, covering secure data disposal methods, proper decommissioning techniques, and the implementation of a robust data retention policy.
Data Sanitization
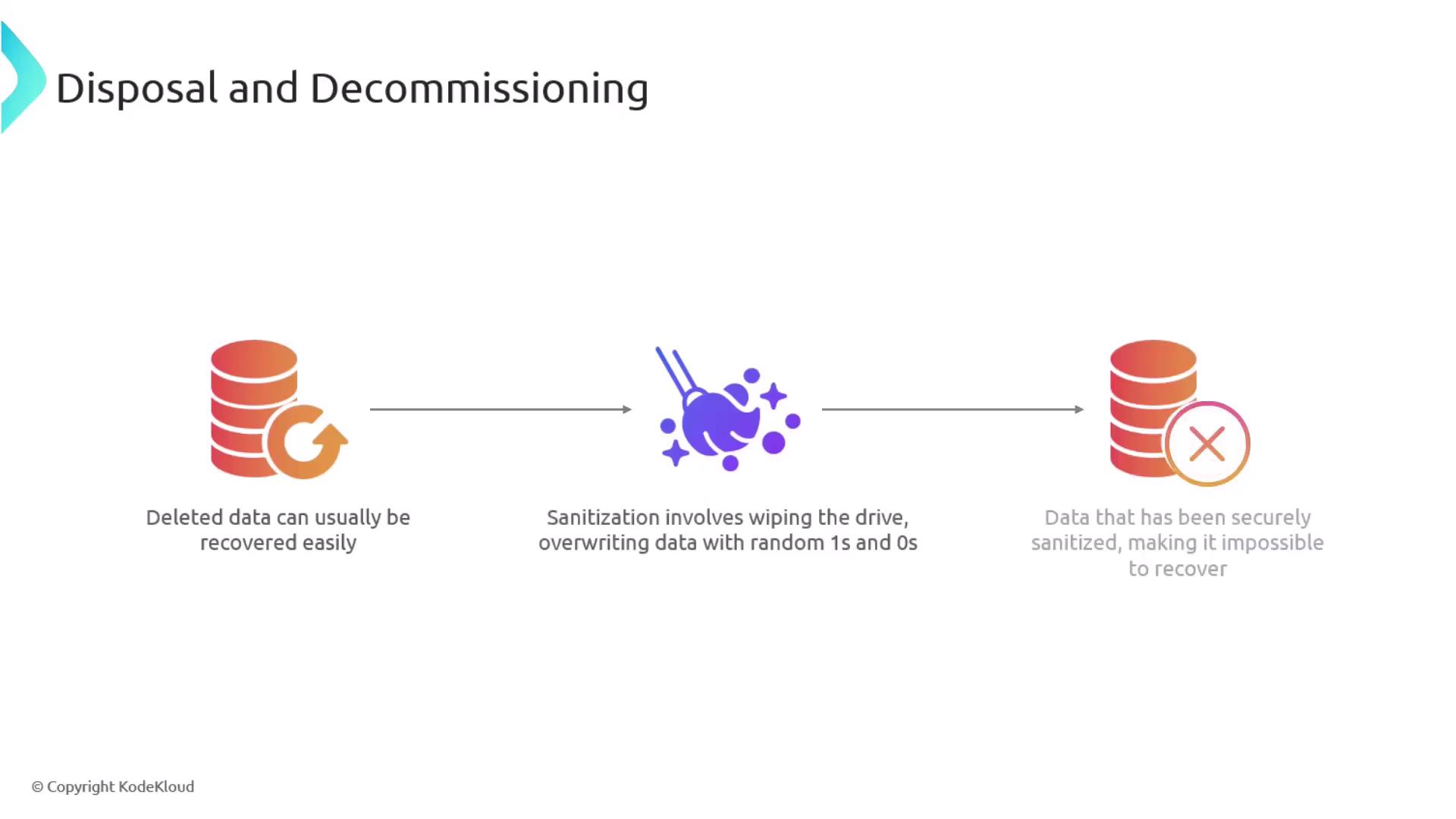
Data sanitization is the process of completely erasing data from a storage device before it is disposed of or repurposed. Often, files on hard drives appear to be deleted but can be recovered using specialized tools if not properly sanitized. The standard sanitization process involves overwriting existing data with random bits (ones and zeros), making it virtually impossible to retrieve the original information.
Note
Ensure that your data sanitization practices comply with industry standards and regulatory requirements to mitigate risks related to data leaks.
Data Destruction
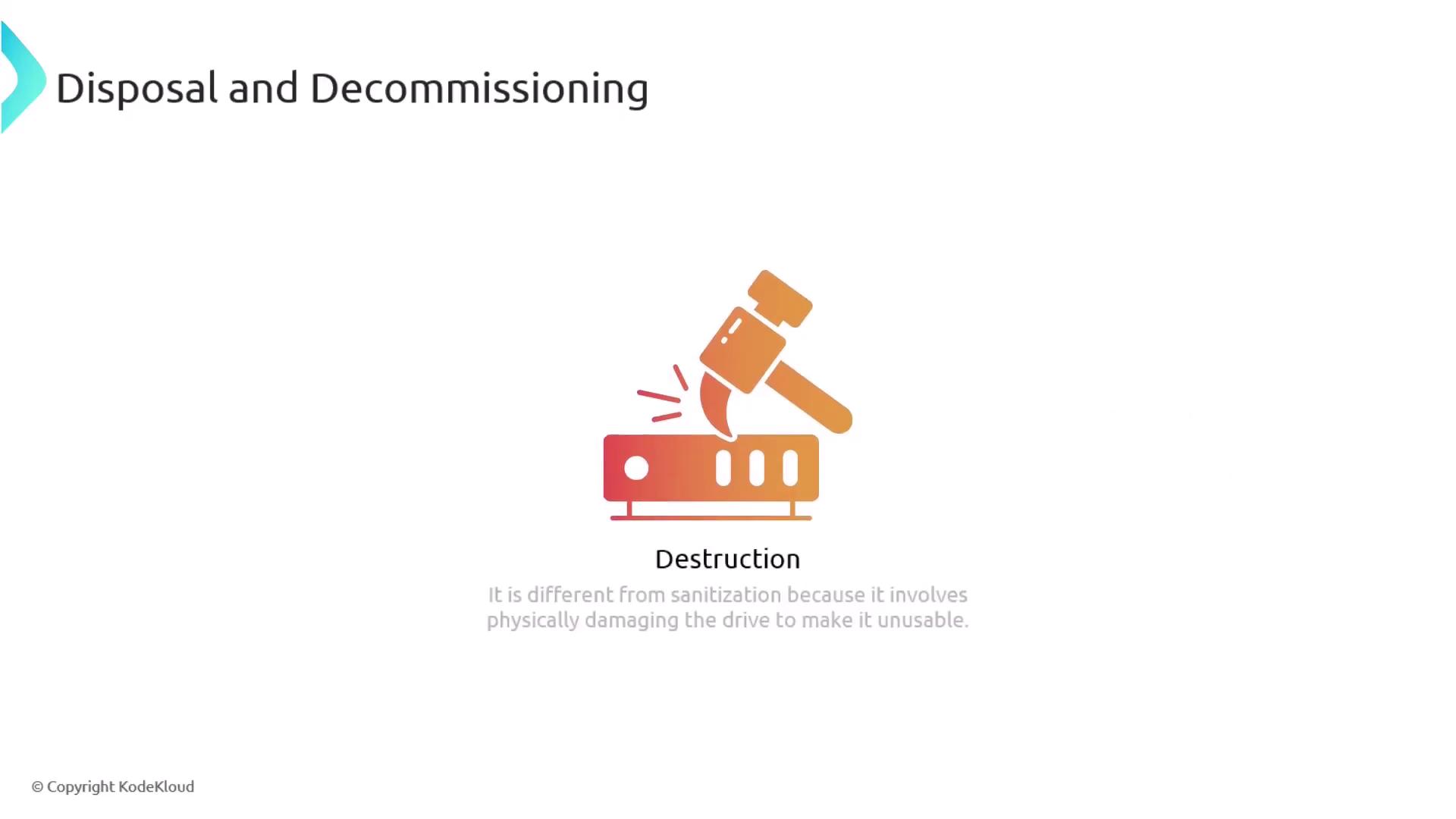
In contrast to data sanitization, data destruction permanently damages the storage hardware to prevent any possibility of data recovery. Physical destruction methods, such as using a hammer to smash the hard drive, are employed when maximum security is needed and the device must be rendered entirely unusable.
Warning
Physical destruction should only be used when data sensitivity is extremely high, as the device becomes irrecoverable and cannot be repurposed or recycled.
Establishing a Data Retention Policy
A comprehensive data retention policy is a cornerstone of effective asset management. This policy clearly defines how long data should be retained and specifies the conditions under which it should be securely deleted. For instance, organizations may be legally required to store customer transaction records for a predetermined period before disposing of them securely.
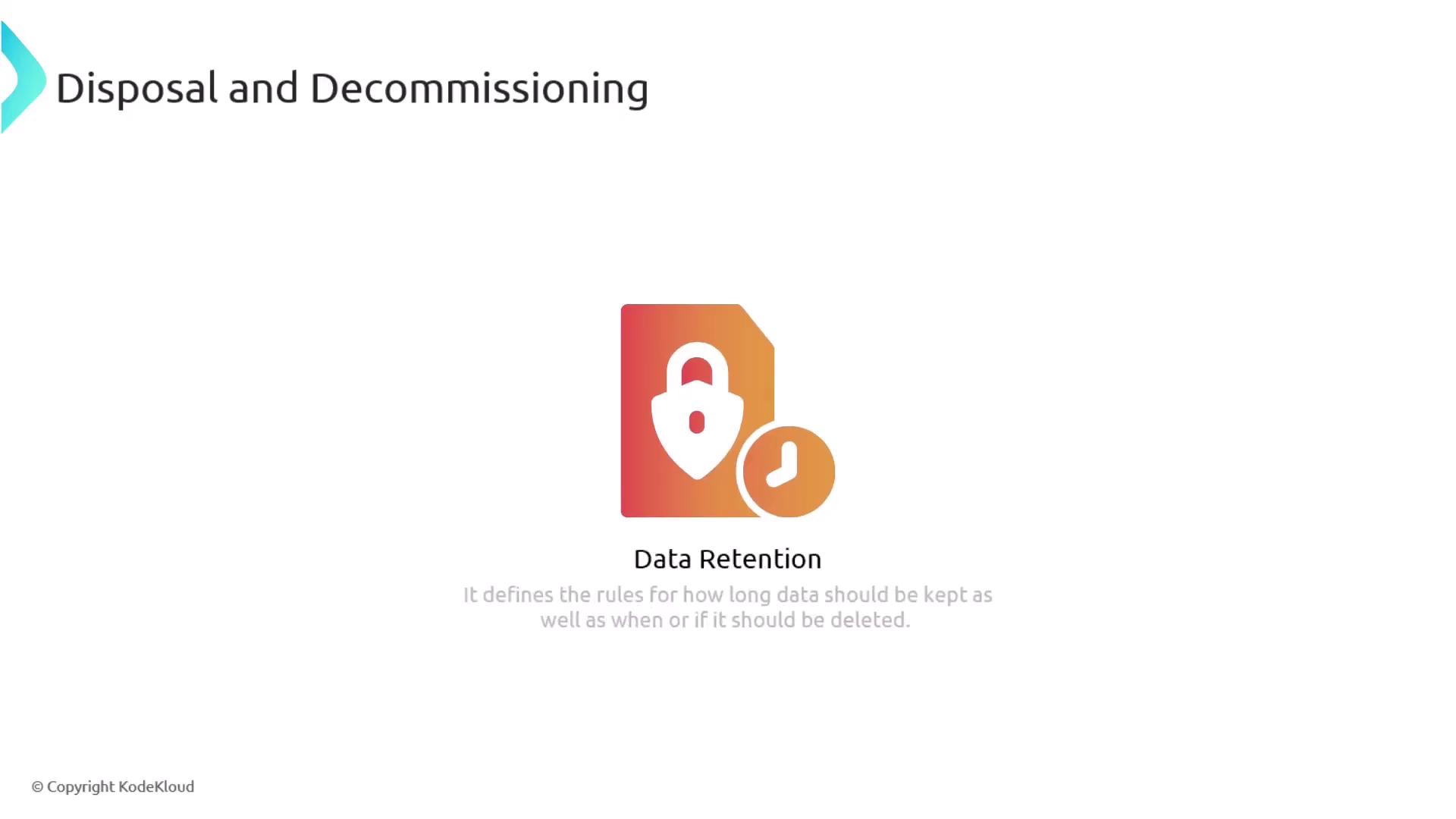
Implementing these best practices not only helps protect your assets but also ensures compliance with legal and regulatory requirements, thereby strengthening your overall security operations.
Watch Video
Watch video content