CompTIA Security+ Certification
Security Operations
Asset Management
Welcome to this in-depth guide on Security Operations with a focus on asset management. In this article, we discuss the security implications of managing hardware, software, and data assets. Effective asset management is essential for maintaining the security, integrity, and availability of an organization's resources.

We will explore key aspects of asset management including:
- Acquisition and procurement
- Assignment and accounting
- Monitoring and asset tracking
- Disposal and decommissioning of assets
By the end of this article, you will understand how each process contributes to a secure and well-managed IT environment.
Overview of Asset Management
Asset management involves a systematic approach to acquiring, maintaining, tracking, and disposing of an organization’s hardware, software, and data assets. This process not only optimizes resource usage but also minimizes vulnerabilities and ensures compliance with regulatory requirements. The journey begins with a careful acquisition and procurement phase.
Acquisition and Procurement
The acquisition phase involves selecting and purchasing the necessary resources. Key activities in this phase include:
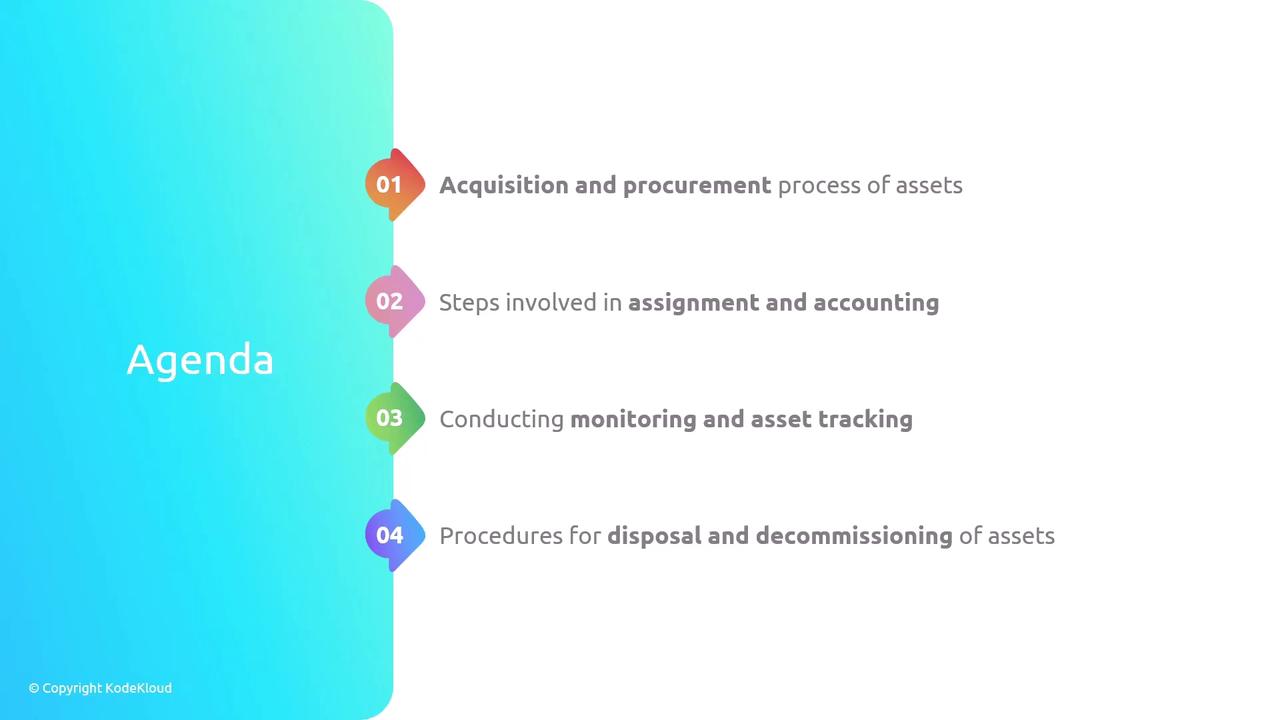
Vendor Evaluation:
Assess vendors to ensure they follow secure development practices and adhere to relevant security standards. A vendor's security posture has a direct impact on your organization's risk profile.Contract Negotiation:
Incorporate specific security requirements into contracts. This might include scheduled security updates, compliance with industry regulations, and tested incident response procedures.Compliance Verification:
Ensure that all acquired assets meet the necessary industry standards and regulatory requirements before finalizing the purchase.
Note
It is important to document each step of the acquisition process to maintain a strong audit trail and support future security reviews.
Assignment and Accounting
Once the assets are acquired, establishing ownership and accountability becomes crucial. This stage comprises:
Establishing Ownership:
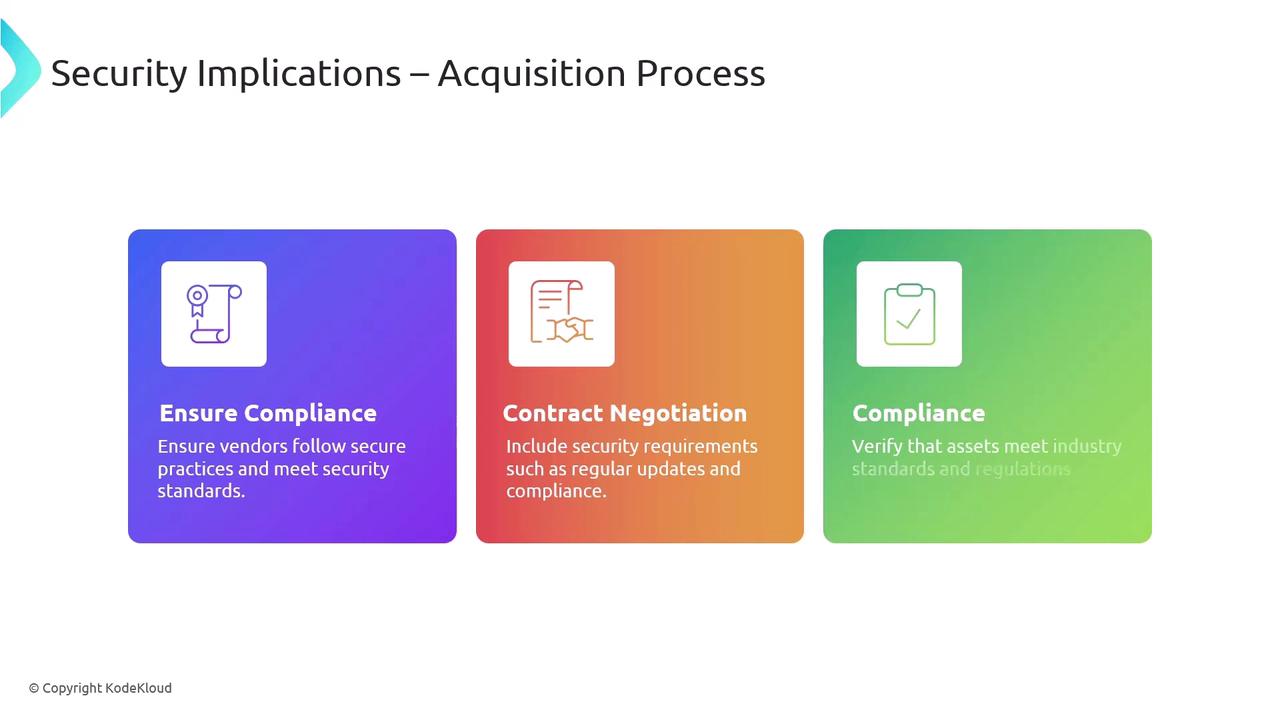
Assign clear responsibility for assets to specific individuals or departments. Typically, the IT department manages hardware while designated administrators are responsible for software and data assets.Classification of Assets:
Categorize assets based on their sensitivity and criticality (e.g., public, internal, confidential, and highly confidential). Customized classifications can be used to suit unique organizational needs, guiding security controls and access restrictions.
Monitoring and Asset Tracking
Continuous monitoring and tracking are vital once an asset is in use. This phase includes:
- Inventory Management:
Maintain a comprehensive list of all hardware, software, and data assets. Capture crucial details such as asset type, location, owner, and status.
![]()
- Asset Enumeration:
Systematically identify and catalog each asset to ensure nothing is overlooked. This step helps prevent unauthorized additions or losses.
![]()
- Regular Audits:
Conduct regular audits to verify that the asset inventory is accurate and compliant with security policies. This process helps detect any unauthorized changes or anomalies.
Note
Integrate automated monitoring tools where possible to streamline the auditing process and ensure consistent compliance.
Disposal and Decommissioning
The final phase of asset management is the safe disposal and decommissioning of assets that are no longer needed. This process helps prevent data breaches and ensures that outdated equipment does not become a security liability. Steps in this phase include:
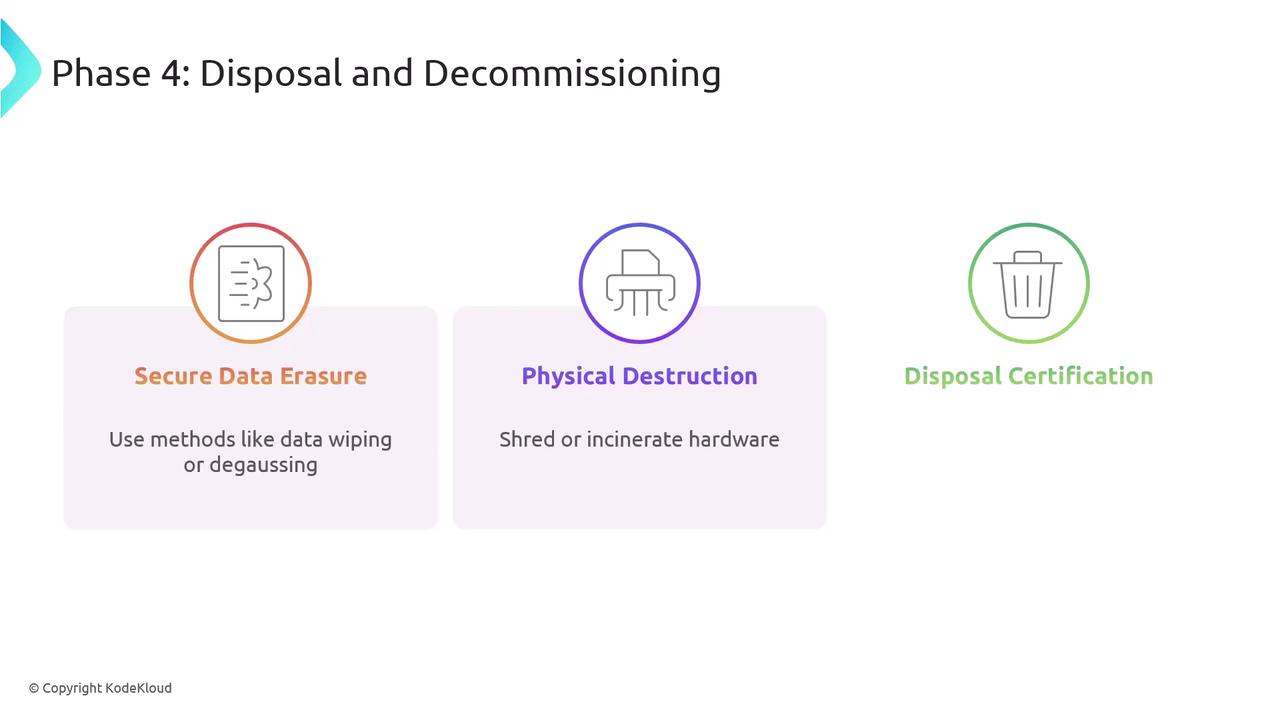
Secure Data Erasure:
Employ certified data wiping tools or degaussing methods to ensure that all sensitive data is completely removed before disposal.Physical Destruction:
In cases where degaussing is not sufficient, physically destroy hardware components by shredding or incineration to safeguard against data recovery.Disposal Certification:
Document the entire disposal process and secure a certification to confirm that both data erasure and hardware destruction were carried out in accordance with security policies and regulatory standards.
Example: Customer Database Lifecycle
To illustrate the asset management process, consider the lifecycle of a customer database used by a fictional retail company.
Phase 1: Acquisition and Procurement
Identifying Requirements:
The company determines its need for a new customer database to manage information such as customer names, addresses, purchase history, and contact details. Key requirements include high availability, scalability, regulatory compliance (e.g., GDPR), and robust security measures.
Vendor Evaluation:
Multiple database vendors are evaluated based on security practices, compliance, performance, and cost. The company selects a vendor with a strong track record in security.Contract Negotiation:
Security requirements integrated during procurement include:- Regular security updates and patches
- Data encryption at rest and in transit
- Compliance with industry standards and regulations
- Defined incident response and breach notification processes
Purchase and Deployment:
Once the procurement process is complete, the company purchases and deploys the database solution. The configuration is aligned with best security practices and vendor recommendations.
Phase 2: Assignment and Accounting
Assigning Ownership:
The IT department assigns a dedicated database administrator to manage the database's security, maintenance, and overall management.
Data Classification:
Customer data is classified as highly confidential, guiding the implementation of strict access controls and data protection measures.
Defining Access Controls:
Access controls based on role and data sensitivity are established and reviewed regularly to ensure ongoing compliance with security policies.
Phase 3: Monitoring and Asset Tracking
Inventory Management:
The customer database is included in the organization's asset inventory with detailed records such as type, version, location, owner, and classification.Monitoring Implementation:
Monitoring tools are deployed to track database performance, security, and usage. These tools help detect unauthorized access and unusual behavior.Regular Audits:
The database undergoes periodic audits to confirm that it aligns with security policies and regulatory requirements.
Phase 4: Disposal and Decommissioning
Identifying the Need for Decommissioning:
Over time, the company may decide to retire the old customer database in favor of a more advanced system that offers improved performance and security.
Secure Data Migration:
Prior to decommissioning, data is securely migrated to a new system. This step includes thorough data validation and verification to ensure integrity.Data Erasure and Hardware Destruction:
Following migration, the legacy database is securely erased using certified tools. If physical hardware is involved, it is destroyed through methods such as shredding or degaussing.Obtaining Disposal Certification:
The decommissioning process is fully documented, and a certification is obtained to confirm that data erasure and hardware destruction adhered to established security standards.
Conclusion
Effective asset management is a comprehensive process covering every stage from acquisition to disposal. By following industry best practices in procurement, assignment, monitoring, and decommissioning, organizations can safeguard the security, integrity, and compliance of their data assets. This systematic approach is essential for protecting sensitive information and maintaining a secure IT environment.

For further reading on robust security practices, consider exploring additional resources such as Kubernetes Basics, Kubernetes Documentation, and Docker Hub.
Watch Video
Watch video content