CompTIA Security+ Certification
Security Operations
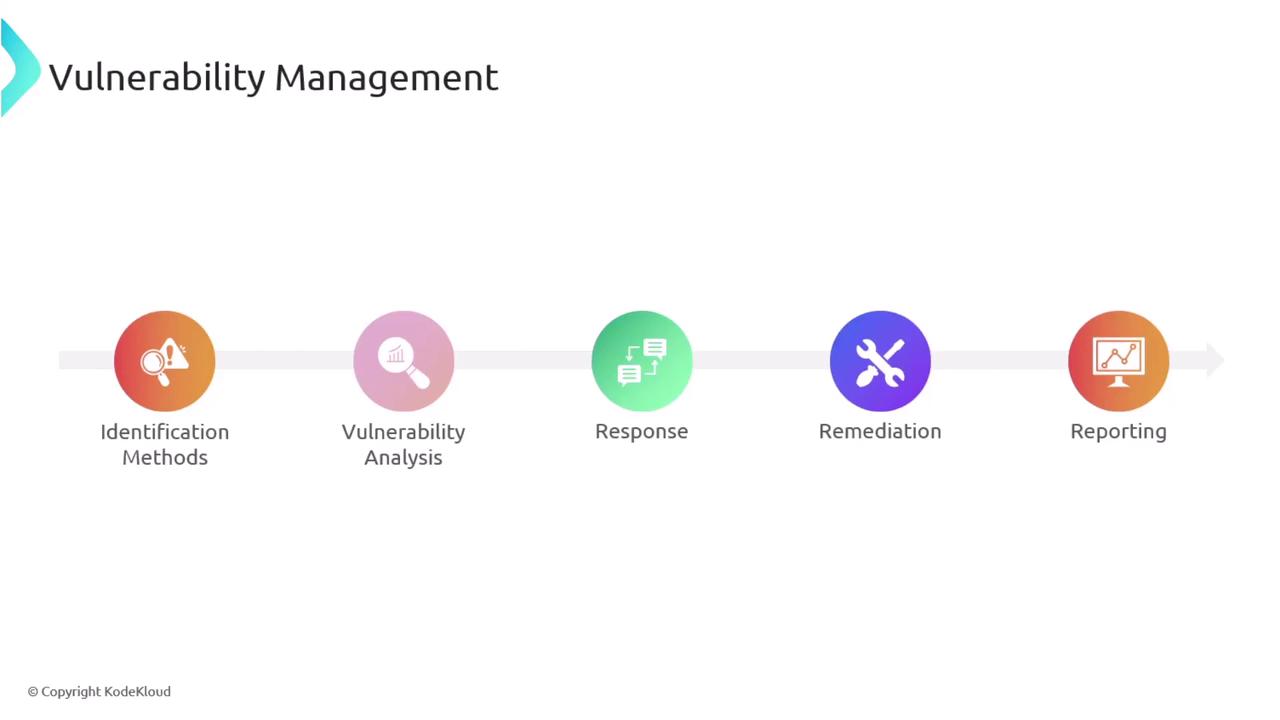
Vulnerability Management
In this guide, we delve deeper into vulnerability management by exploring key topics such as identification methods, vulnerability analysis, response, remediation, and reporting. Promptly identifying vulnerabilities is critical to prevent threat actors from exploiting system weaknesses.
Identifying Vulnerabilities
Vulnerability identification is the first line of defense. This process involves performing vulnerability scans using threat feeds, penetration testing, and other diagnostic techniques. Specialized software tools scan systems and networks to pinpoint potential weaknesses, revealing issues like missing patches, misconfigurations, and deviations from baseline security standards.
Vulnerability Scanning Tools
Two widely recognized tools in vulnerability scanning are Nessus and OpenVAS. These solutions are effective in detecting vulnerabilities and are trusted by security professionals worldwide.

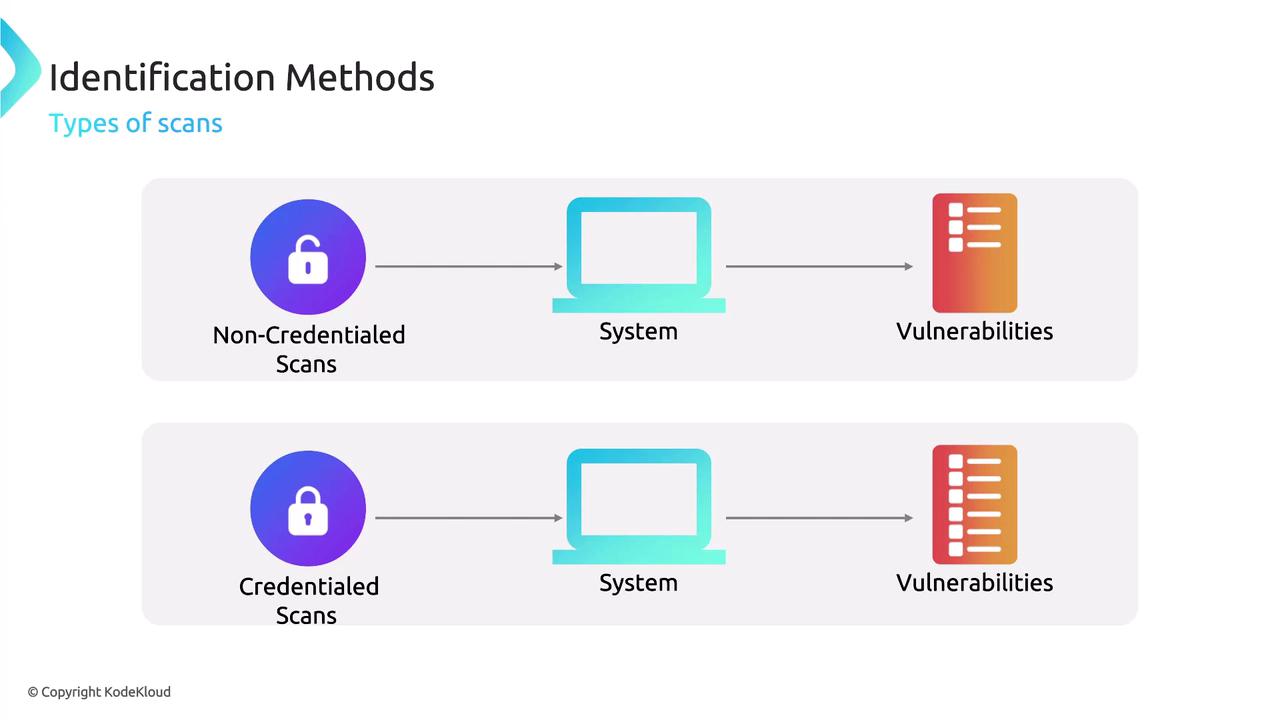
Types of Scans
There are several scanning approaches available:
- Non-credential scans: These scans do not require system login and provide an external view of vulnerabilities.
- Credential scans: These scans involve logging into the system, offering a detailed analysis of potential risks if user credentials were compromised.
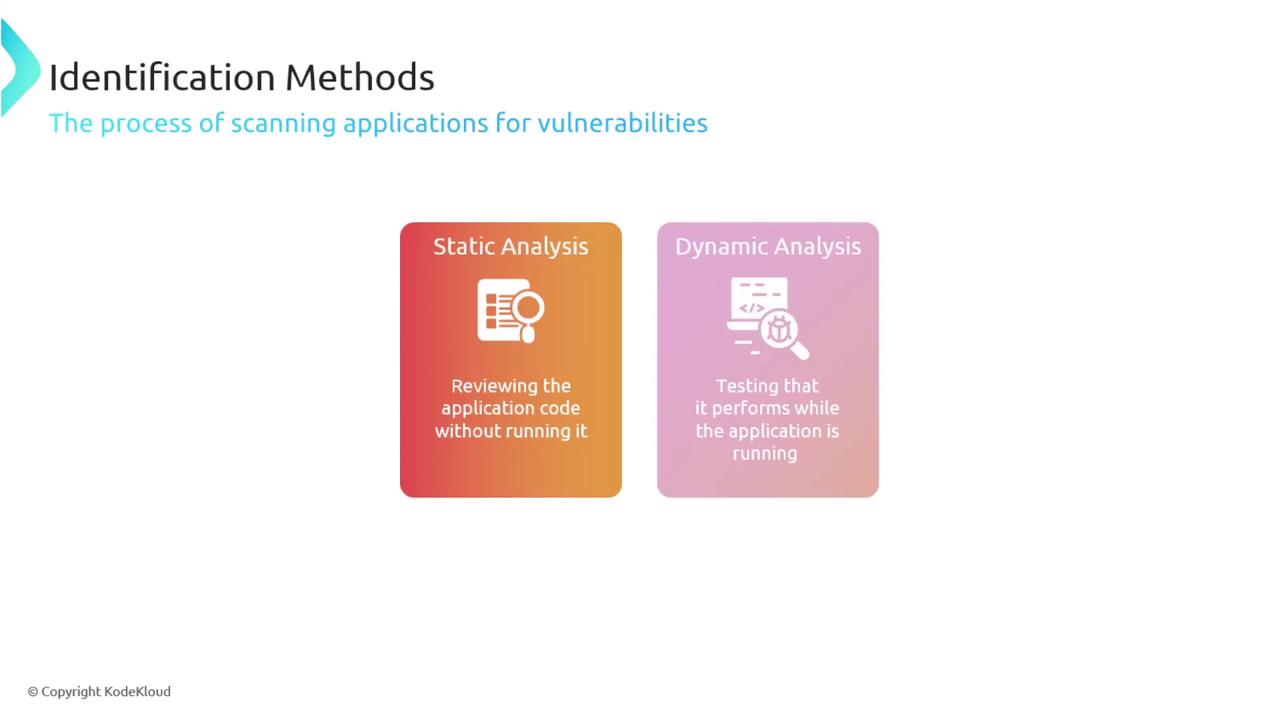
The vulnerability scanning process may also include both static and dynamic analyses:
- Static Analysis: Examines the application code without executing it.
- Dynamic Analysis: Tests the application behavior during runtime to detect vulnerabilities in real-world conditions.
Tip
Integrating both static and dynamic analyses provides a comprehensive view of an application's security posture.
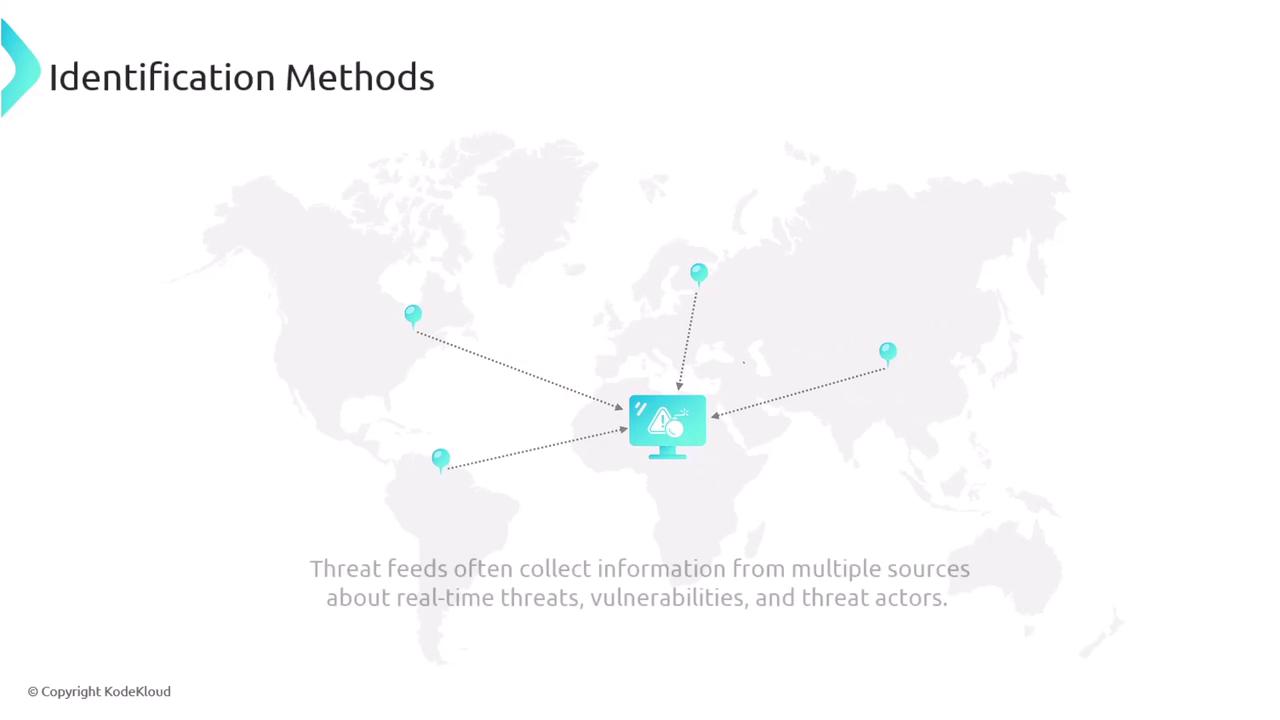
Threat Feeds
Threat feeds are crucial for continuous vulnerability identification. They consolidate information from diverse sources to keep organizations updated on real-time threats, vulnerabilities, and threat actor activities. One of the more popular examples is Open Source Intelligence (OSINT), which aggregates publicly available data from various organizations and independent contributors. Other prominent threat feeds include AlienVault's Open Threat Exchange, Recorded Future, IBM’s X-Force Exchange, and community-driven sources like the Cyber Threat Alliance or MISP.
Security Reminder
Regularly updating your threat feeds and monitoring their alerts is vital to preemptively address emerging security risks and enhance your overall defense strategy.
Watch Video
Watch video content