CompTIA Security+ Certification
Security Operations
Other Enterprise Security Methods
This article examines several essential enterprise security methods that supplement traditional network defenses. In this guide, you'll learn about host-based firewalls, application allow lists, file integrity monitoring (FIM), endpoint management software, and bug bounty programs. These methods help protect systems from unauthorized access and cyber threats.
Host-Based Firewalls and Application Allow Lists
Host-based firewalls function similarly to network firewalls but are installed directly on individual computers or servers. They allow administrators to configure rules that permit or deny traffic entering or leaving the system. These firewalls also monitor both incoming and outgoing connections, providing an additional layer of security.
In conjunction with firewalls, an application allow list restricts which applications can be executed on a host. Only approved applications are permitted, which minimizes the risk of running untrusted software, including malware. This preventive measure ensures that even if harmful software is inadvertently downloaded, it will not execute unless it is on the allow list.
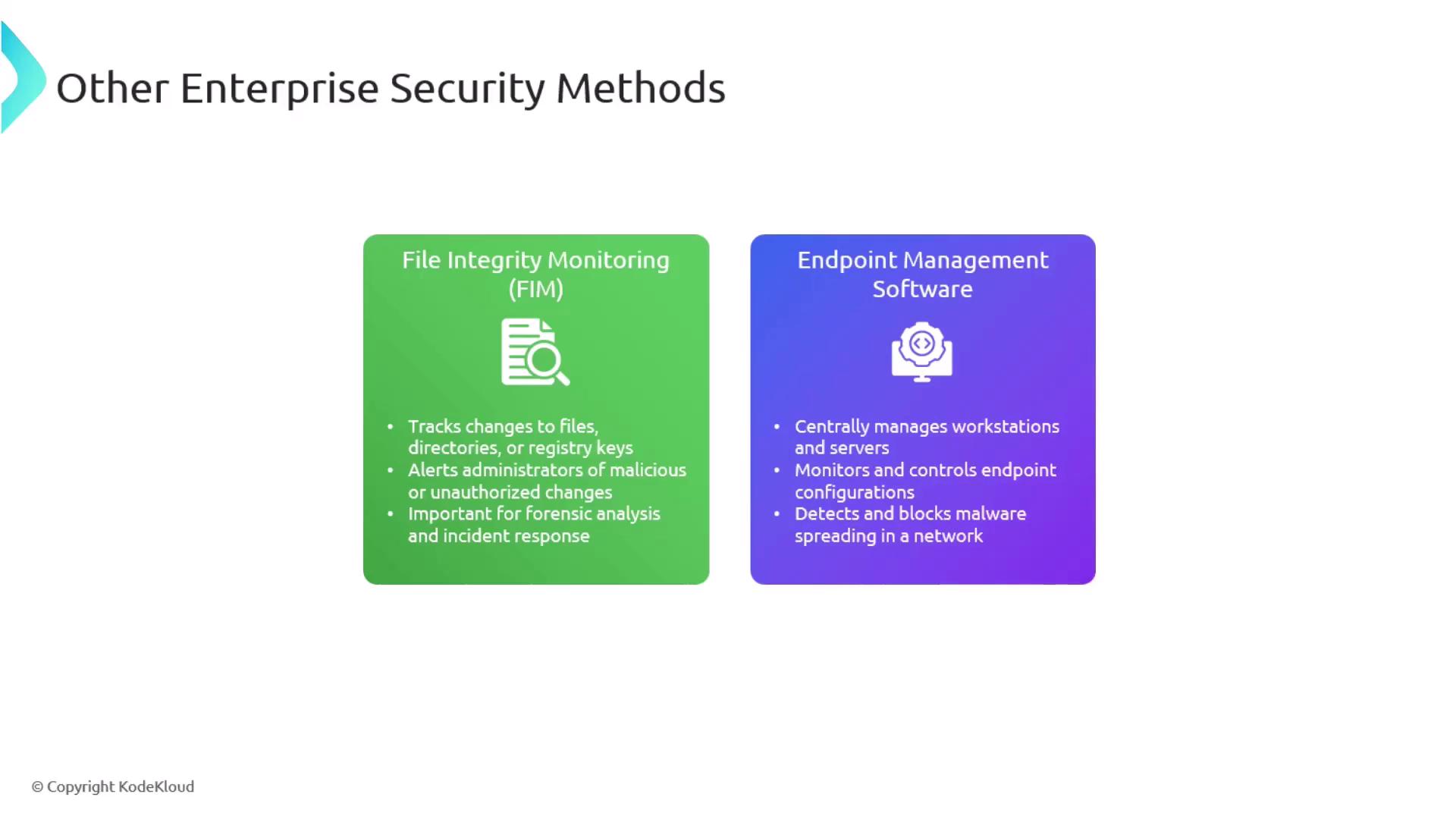
File Integrity Monitoring (FIM)
File integrity monitoring (FIM) plays a crucial role in modern security strategies by tracking modifications to files, directories, and Windows registry keys. Administrators use FIM to detect unauthorized or malicious changes that often prelude cyberattacks.
Note
When a change is detected, FIM systems provide detailed alerts about the source and time of the modification. This detailed logging is valuable for both forensic analysis and timely incident response.
Endpoint Management Software
Endpoint management software centralizes oversight of workstations and servers across the enterprise. It enforces standardized configuration policies, which helps in detecting any unauthorized attempts by malware to spread within the network. Additionally, this software can prevent the automatic execution of downloaded programs during malware attacks, thereby helping to contain potential threats effectively.
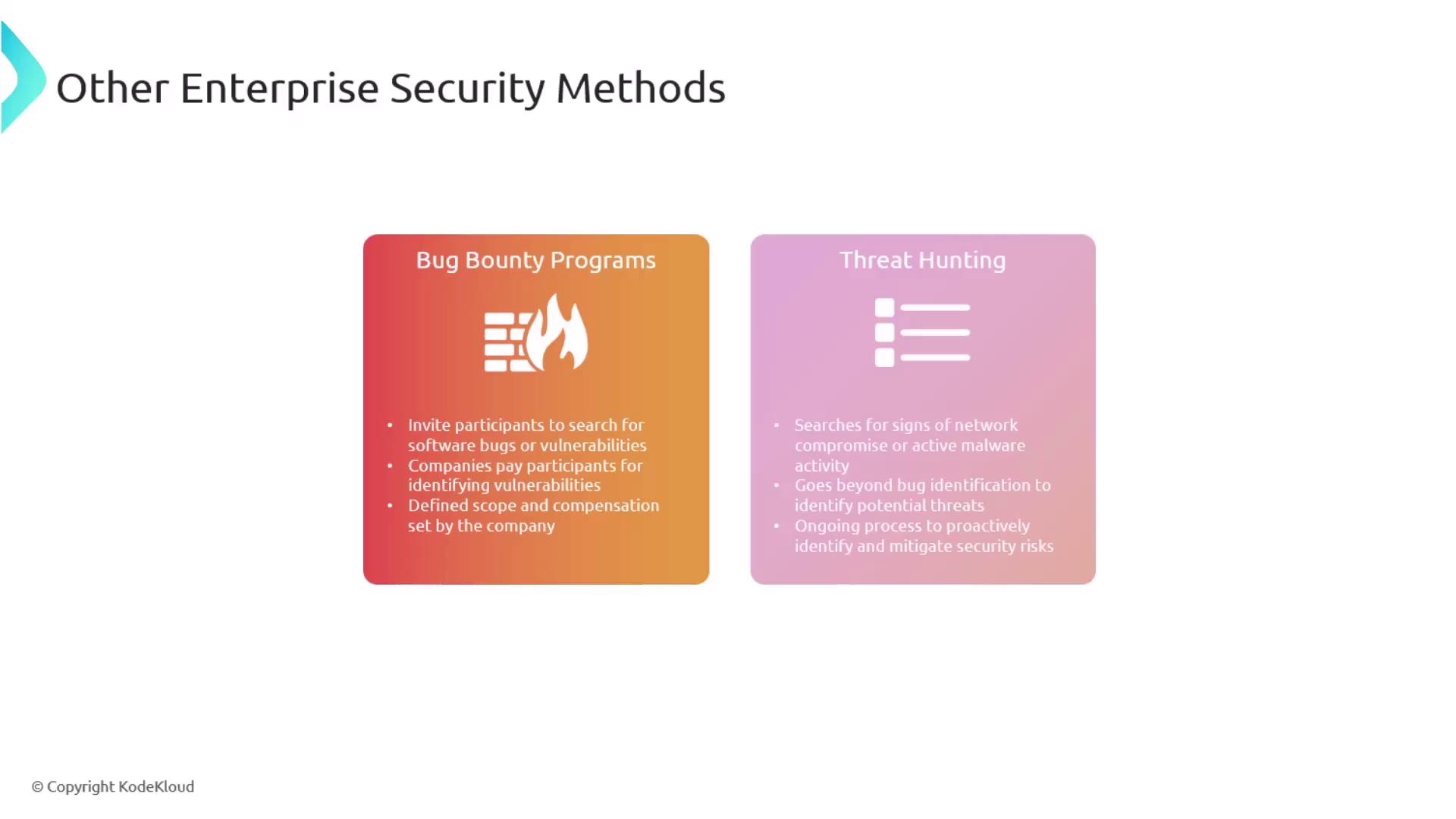
Bug Bounty Programs and Threat Hunting
Bug bounty programs have become a popular method for discovering vulnerabilities by inviting external security researchers to identify bugs that could be exploited by attackers. Companies provide clear guidelines and compensation for valid vulnerability reports, which incentivizes thorough testing and discovery.
It is important to differentiate bug bounty programs from threat hunting. While bug bounty initiatives focus on uncovering software bugs and vulnerabilities, threat hunting involves a proactive search for indicators of compromise or malware within the network.
Additional Insight
Engaging in both bug bounty programs and continuous threat hunting enhances an organization’s ability to identify and remediate risks quickly, offering a more robust security posture.
Watch Video
Watch video content