CompTIA Security+ Certification
Security Operations
Secure Baselines
Welcome to this lesson on secure baselines. This guide explains the concept of secure baselines and walks you through the processes of establishing, deploying, and maintaining them. These steps are essential for ensuring the security and integrity of IT systems and networks.
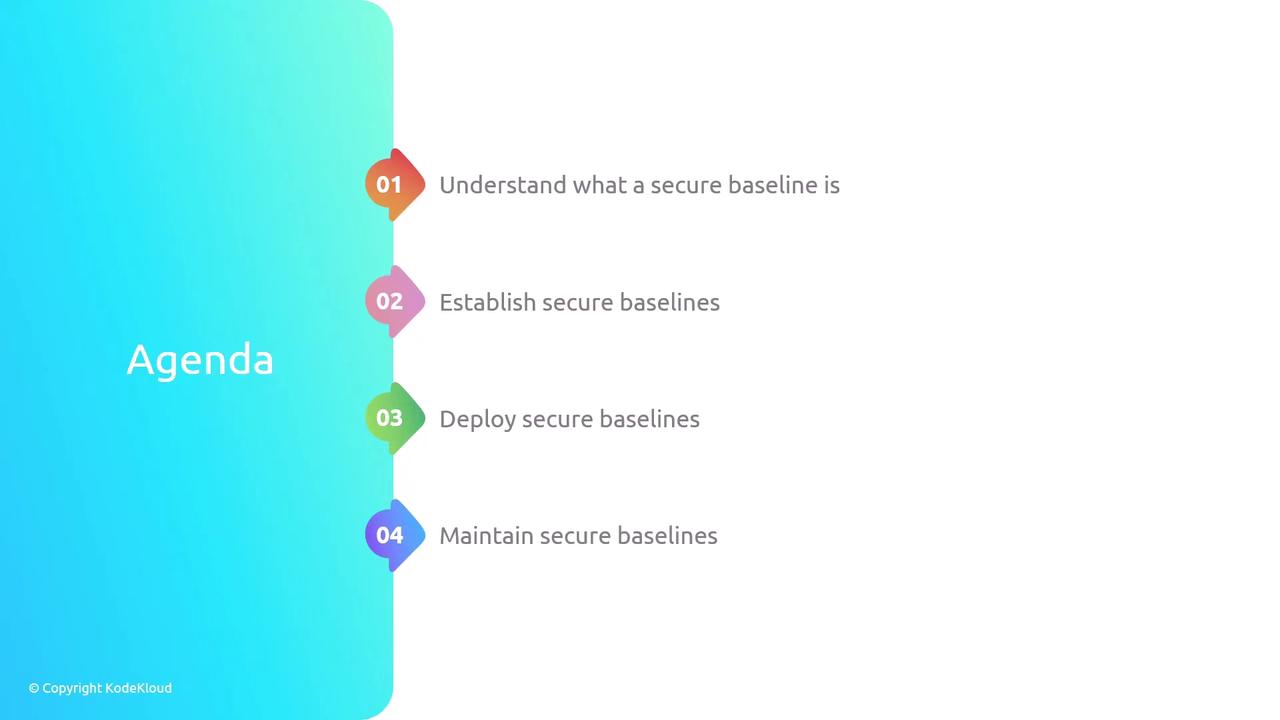
Introduction to Secure Baselines
A secure baseline is a comprehensive set of security configurations and settings that define a secure state for your systems, applications, and networks. It acts as a reference point, ensuring that every system adheres to a consistent and secure configuration. This baseline is used to compare actual configurations against the defined standard, enabling the identification of any deviations.
Without a secure baseline, determining whether a system is operating normally or has drifted into an insecure state becomes challenging.
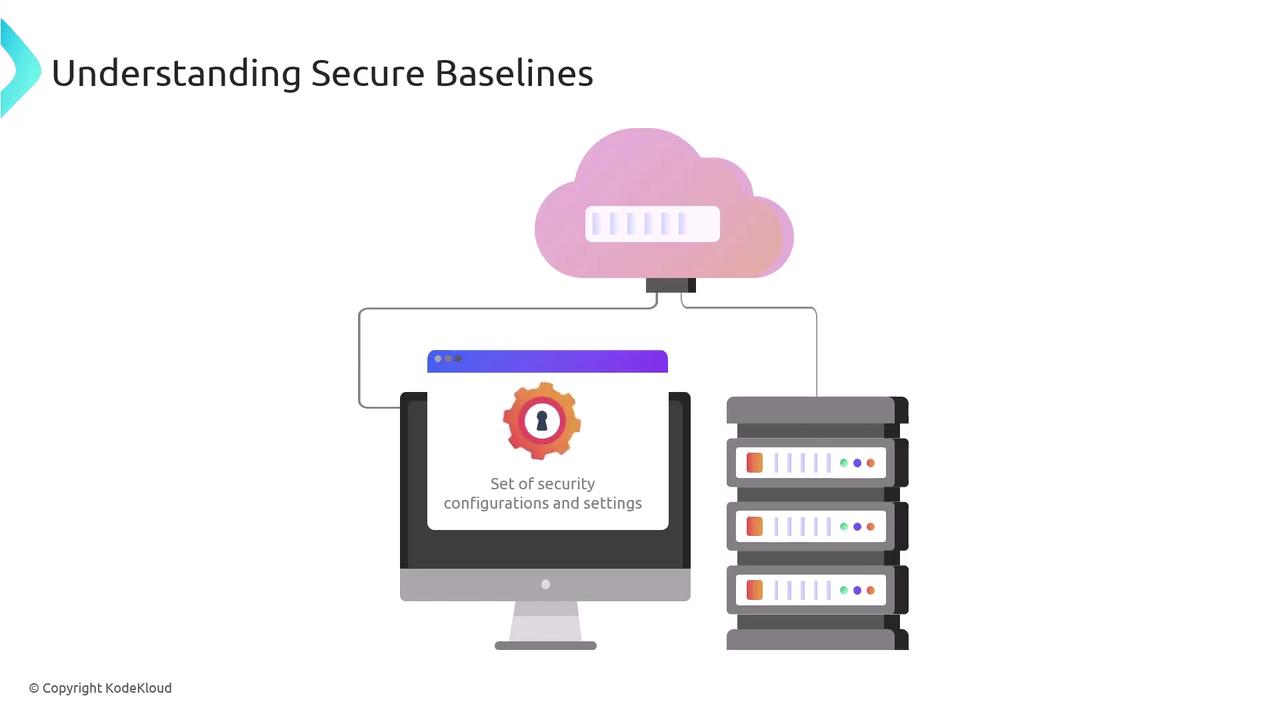
Key benefits of establishing a secure baseline include:
- Ensuring consistency across all systems.
- Supporting comprehensive security measures.
- Detecting unauthorized or abnormal changes.
- Enabling effective comparisons to the secure standard.
- Measuring deviations and potential threats.
Establishing a Secure Baseline
The first critical step is to establish your secure baseline. This involves setting up the fundamental security configurations and settings for every system in your organization. Follow these key steps:
- Identify Requirements: Determine the necessary security standards based on organizational policies, industry best practices, and regulatory mandates.
- Select Standards and Guidelines: Adopt relevant standards such as the CIS Benchmarks, NIST SP 800-53, or ISO/IEC 27001 to guide your baseline configurations.
- Define Configurations: Clearly specify the security settings for each system component—be it operating systems, applications, network devices, or databases.
- Document the Baseline: Thorough documentation is essential. Include detailed, step-by-step instructions for the configuration and verification processes.
Note
Ensure your documentation is easily accessible and regularly updated. This will facilitate efficient troubleshooting and future audits.
Deploying Secure Baselines
With the secure baseline established, the next phase is deployment. This phase ensures that your defined configurations are correctly applied to all systems. The deployment process includes the following steps:
- Preparing Systems: Back up critical data and verify system integrity to ensure readiness for configuration changes.
- Applying Configurations: Utilize automated tools and scripts—such as configuration management tools like Ansible—to implement baseline settings across your environment.
- Verifying Implementation: Compare current configurations against your documented baseline to verify that they have been correctly applied.
- Testing Systems: Execute thorough testing to ensure systems function as expected and no operational issues have been introduced.
Tip
Automating the deployment process can save time and minimize the risk of human error. Consider integrating continuous deployment pipelines where possible.
Maintaining Secure Baselines
Ongoing maintenance is vital for ensuring that the secure baseline remains effective over time. As threats evolve and system environments change, regular updates are necessary. Maintenance activities include:
- Continuous Monitoring: Keep an eye on system configurations to promptly identify deviations from your secure baseline.
- Review and Update Configurations: Periodically audit and update the baseline settings to mitigate new vulnerabilities and adhere to updated security standards.
- Conduct Audits: Regular audits help verify compliance with baseline configurations and document any discrepancies.
Warning
Neglecting routine reviews can lead to security gaps that attackers might exploit. Establish a regular schedule for monitoring and updating your benchmarks.
Conclusion
In summary, establishing, deploying, and maintaining secure baselines are fundamental to creating a resilient cybersecurity framework. By defining and enforcing these configurations, organizations can effectively mitigate risks, ensure regulatory compliance, and maintain robust defense measures.

This comprehensive approach to secure baselines not only solidifies your security posture but also assists in the early detection of deviations, thereby sustaining system integrity over time.
Watch Video
Watch video content