Understanding Man-in-the-Middle (MITM) Attacks
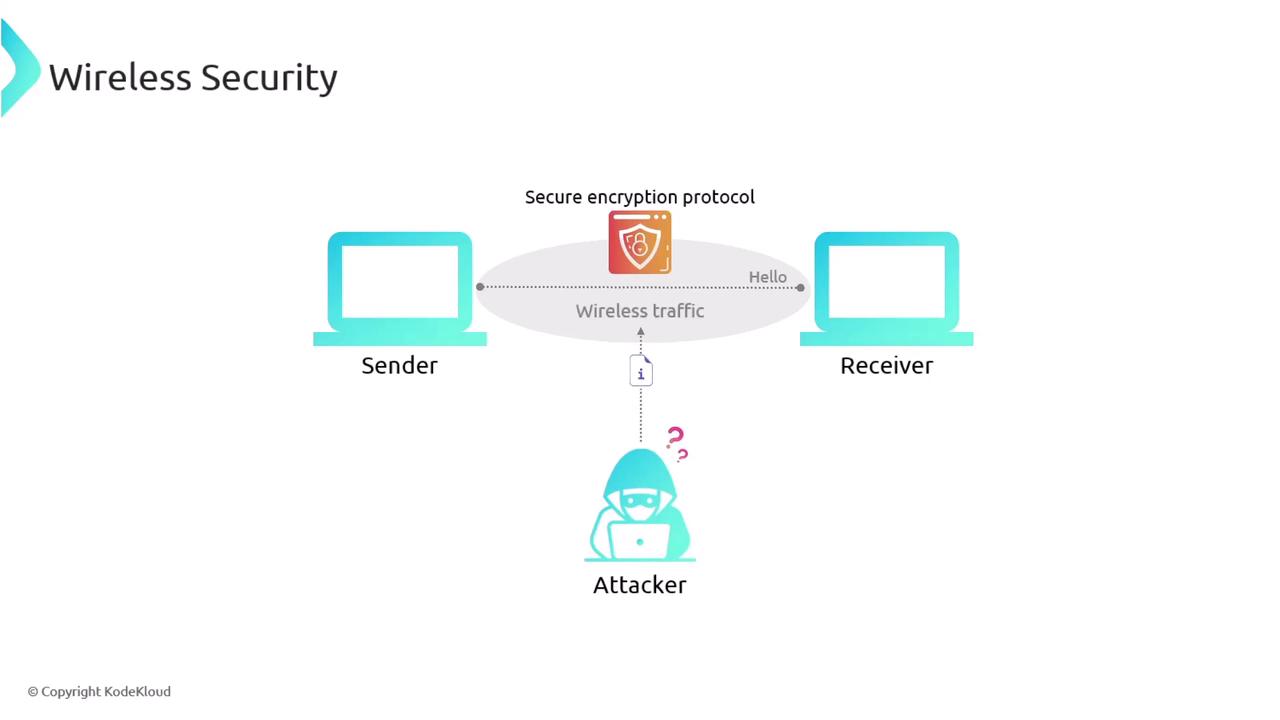
In a MITM attack, an unauthorized third party intercepts the communication between two legitimate parties. By capturing or even altering the data transmitted between Parties A and B, the attacker (Party C) can impersonate one of the parties or modify the information without detection.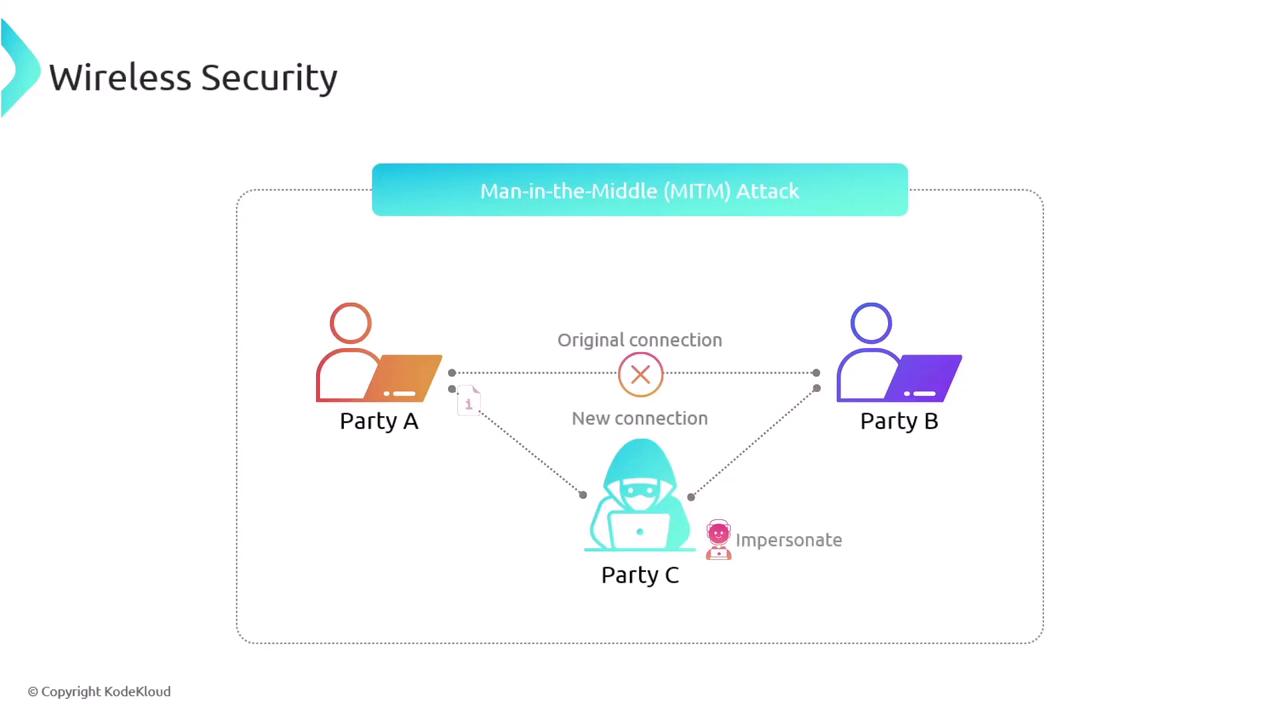
Understanding MITM attacks is critical as it helps in designing countermeasures that ensure secure communications even in open wireless environments.
Rogue Access Points: A Coffee Shop Scenario
Consider a coffee shop offering free Wi-Fi. Patrons, including our friend Alan, believe they are connected to the cafe’s legitimate network. However, unbeknownst to them, a rogue DHCP server has been set up by an attacker named Charlie. As customer data is routed through Charlie’s access point, he is able to intercept and potentially manipulate the network traffic.
The Role of Wireless Access Points (APs)
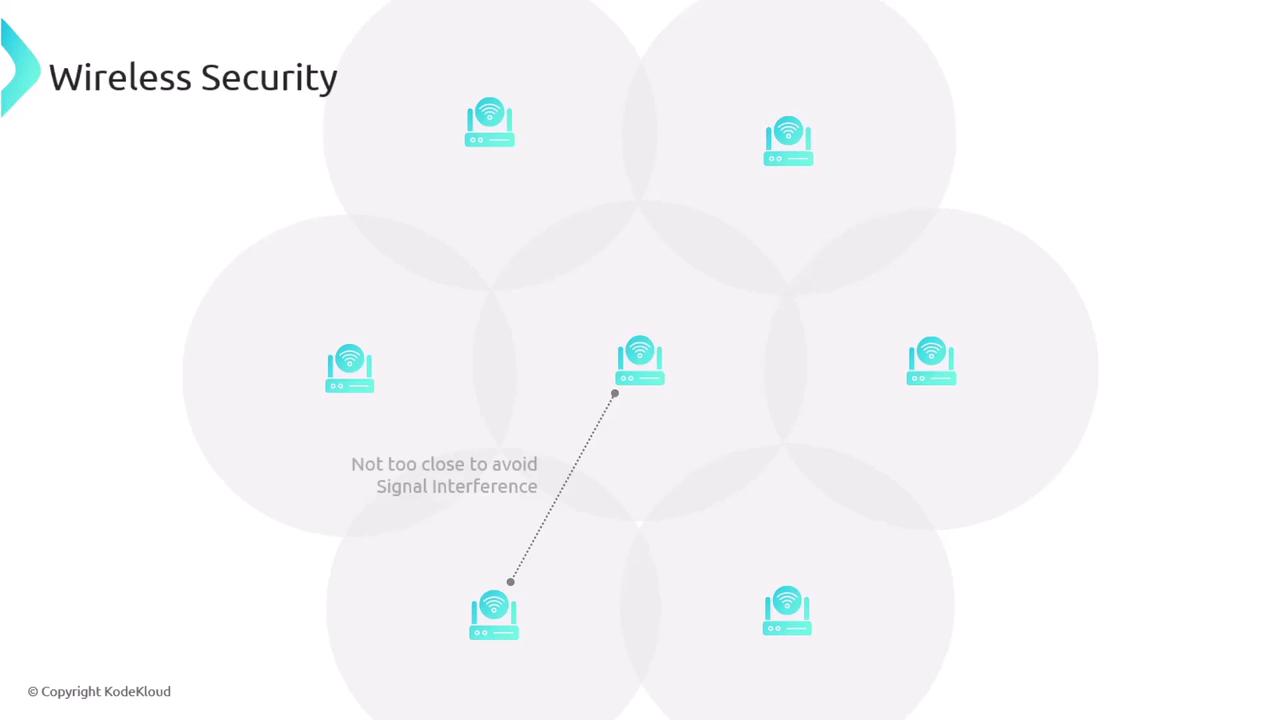
Wireless access points (APs) serve as the bridge between wireless devices and wired networks. They not only enable data transmission but also provide the network access essential for connecting to the Internet. Due to the limited coverage of each AP, it is often necessary to install multiple APs to ensure seamless connectivity while avoiding signal interference.
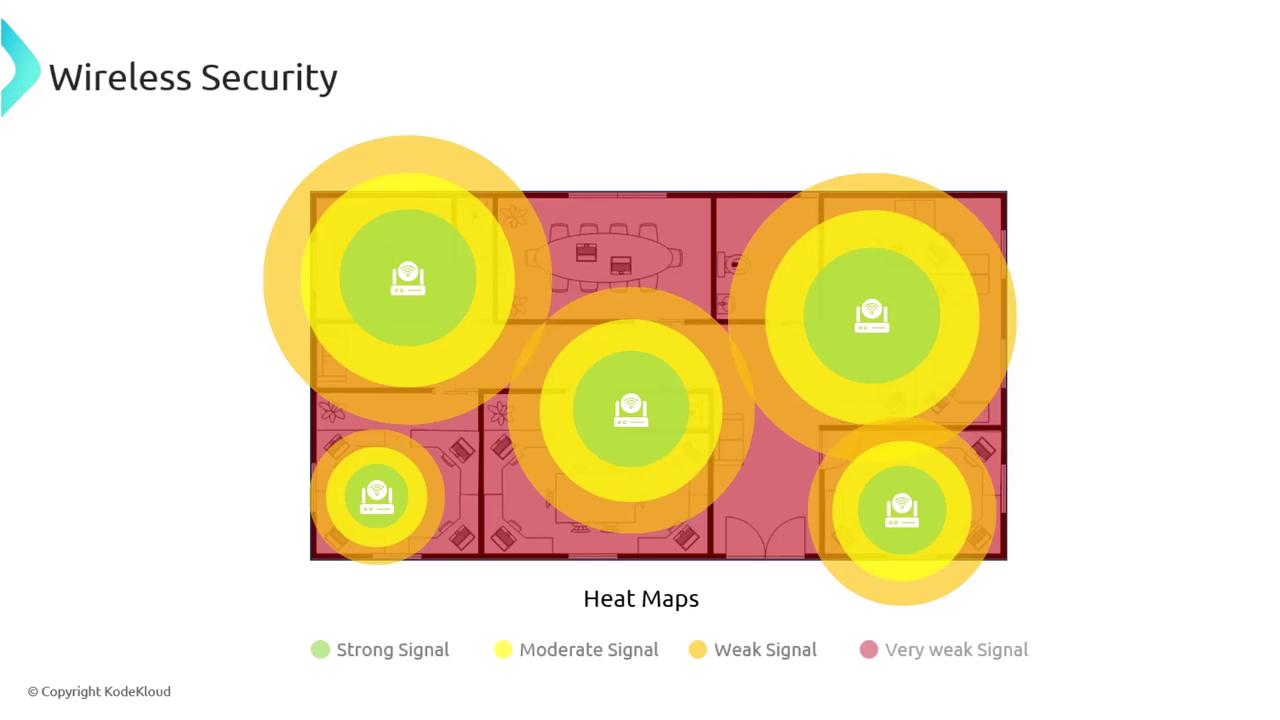
Maintaining the CIA Triad in Wireless Networks
Given that wireless signals travel through an open medium, it is crucial to protect the confidentiality, integrity, and availability (CIA) of transmitted data. Ensuring that only authorized users access the network is paramount to preserving these security aspects.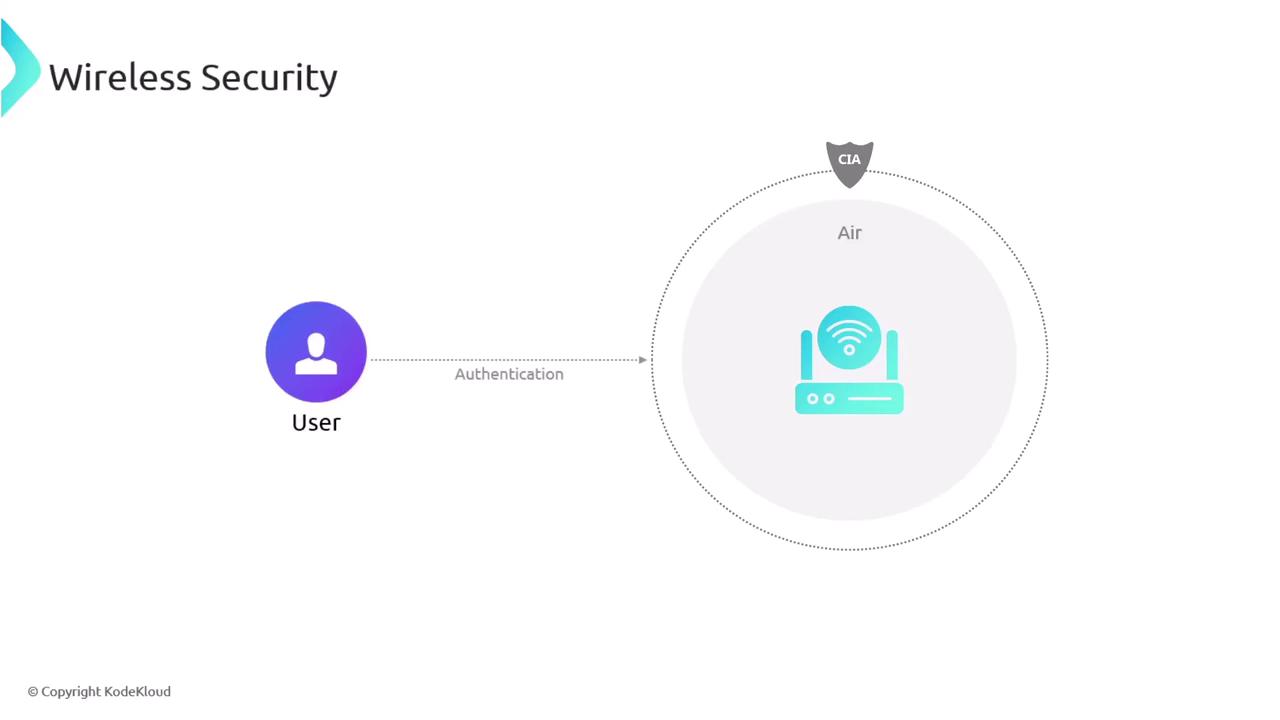
Implementing AAA: Authentication, Authorization, and Accounting
The principles of Authentication, Authorization, and Accounting (AAA) are foundational to wireless security:- Authentication: Confirms the identity of users.
- Authorization: Dictates what an authenticated user is permitted to do.
- Accounting: Monitors and logs user activity for auditing purposes.

Data Integrity and Hashing
Data integrity ensures that information remains unaltered during transmission. For example, when Alan sends an electronic check to his friend Beth, an attacker like Charlie could potentially intercept and modify critical details such as the recipient’s name or the amount. Integrity verification through checksums and hashing algorithms detects any alterations. Before the data is transmitted, a hashing algorithm generates a unique hash value from the original data. Alan sends both the data and its hash to Beth. Upon receipt, Beth recalculates the hash; if it does not match the original, she is alerted that the data integrity has been compromised.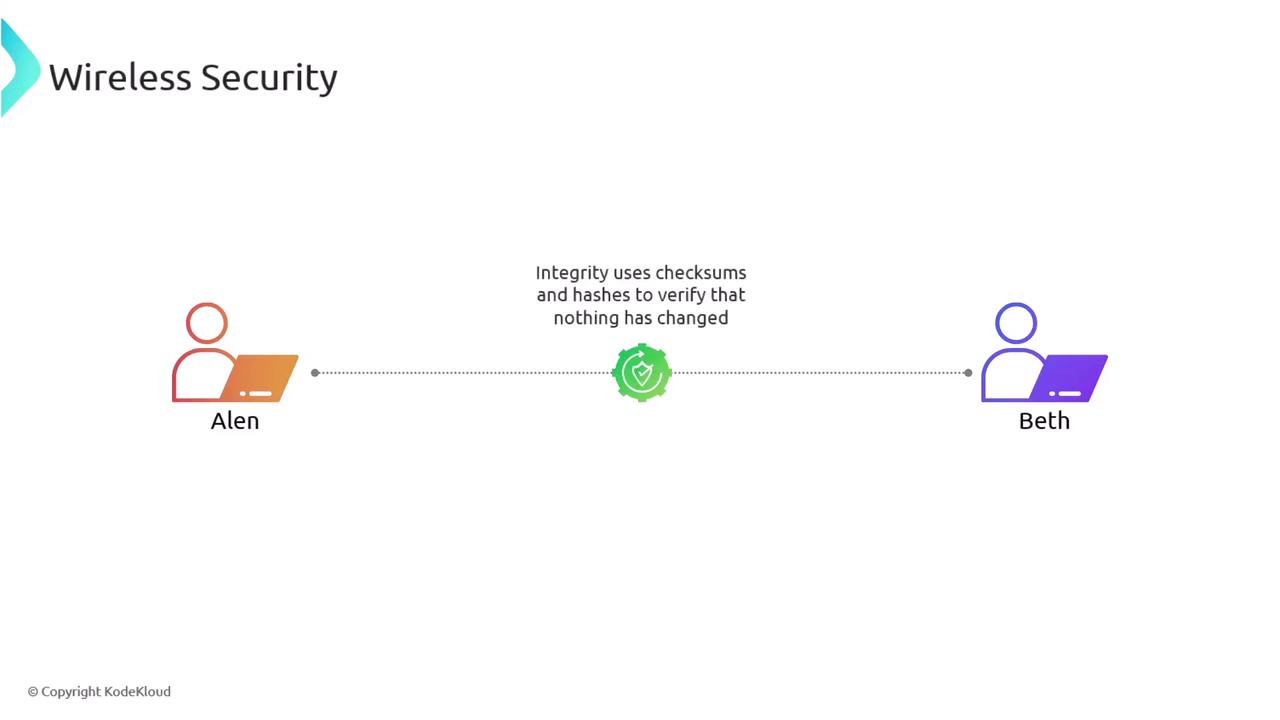
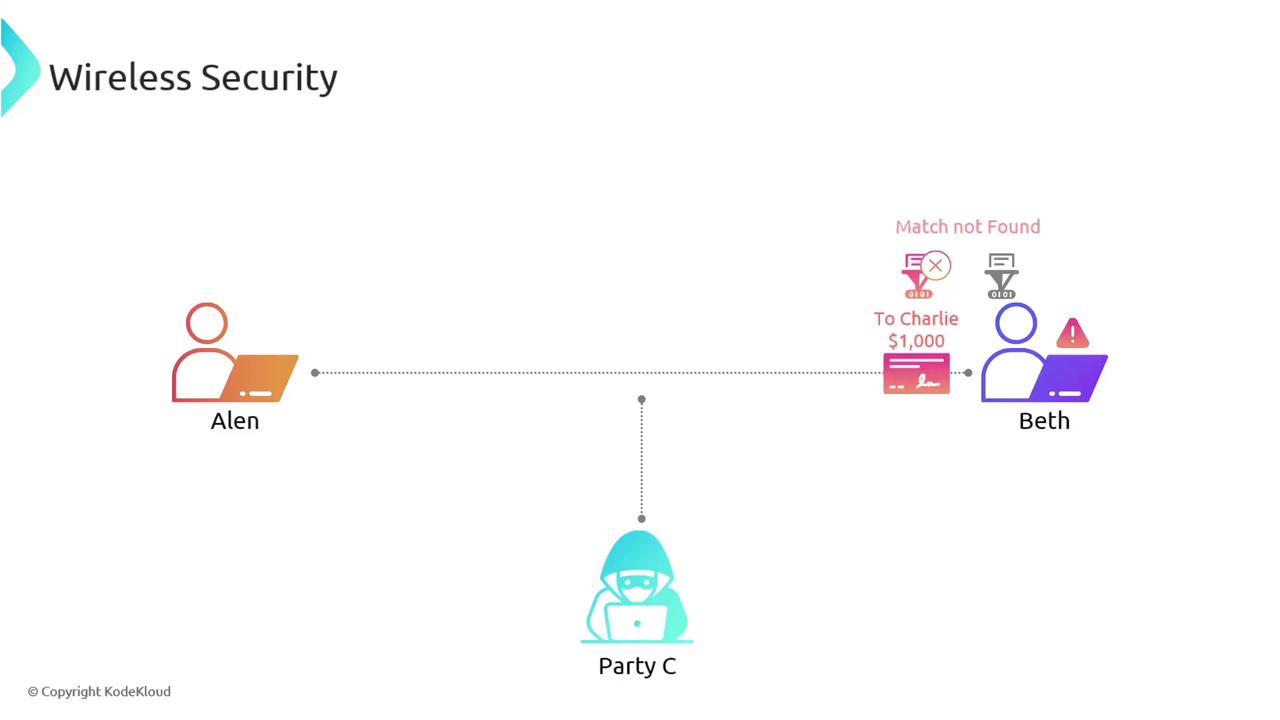
Always verify data integrity to prevent fraudulent transactions or data tampering, as even minor alterations can lead to significant security issues.