CompTIA Security+ Certification
Security Operations
Wireless Security Settings Radius
Welcome to this in-depth lesson on wireless security settings. In today’s digital age, protecting your wireless network is crucial for safeguarding data, maintaining privacy, and preventing unauthorized access. This lesson covers five key topics—WPA3, AAA, RADIUS, Cryptographic Protocols, and Authentication Protocols—that are essential for passing the Security+ exam and enhancing your overall cybersecurity posture.
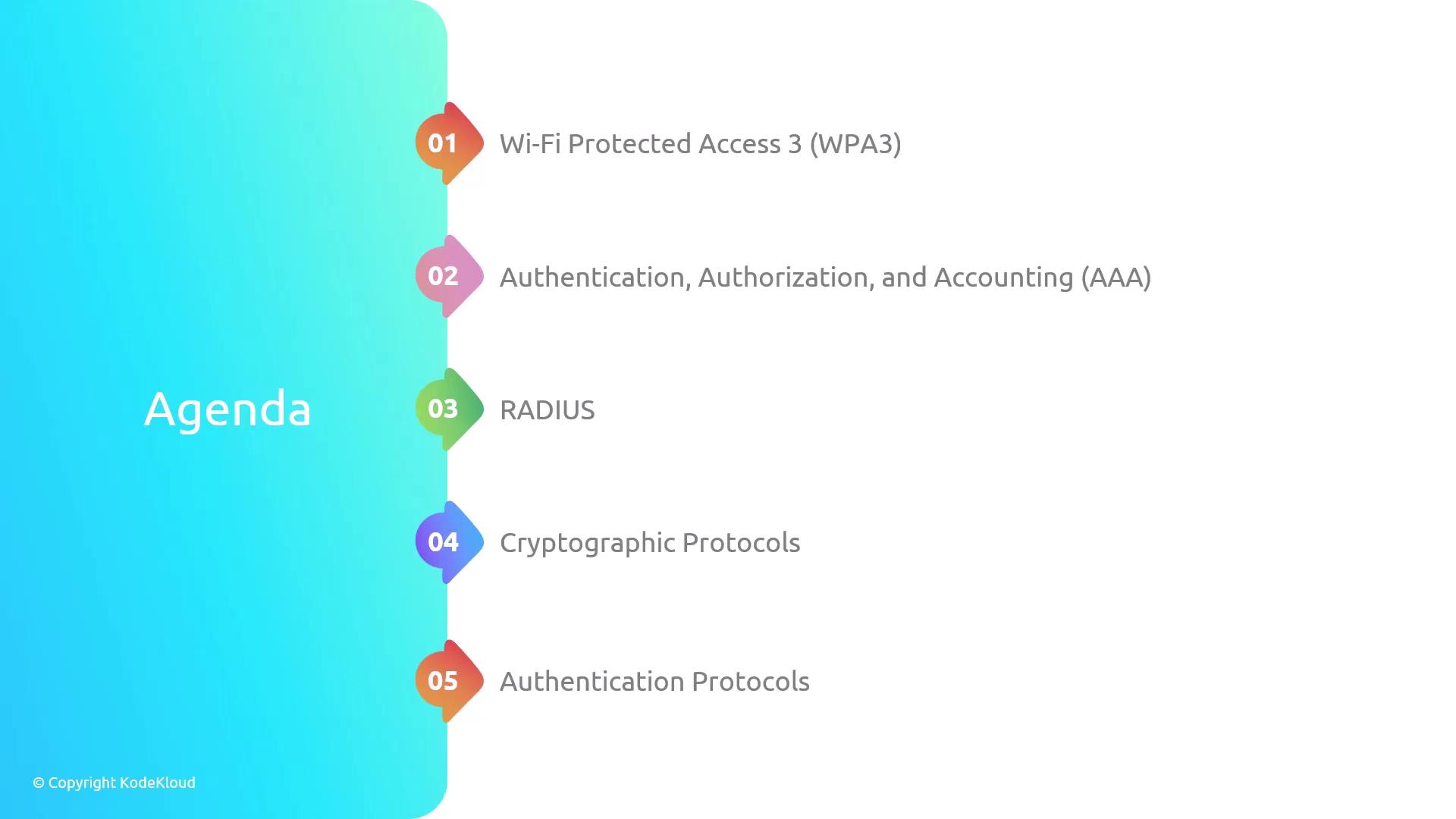
Below is an agenda outlining the areas that will be discussed:
Wi-Fi Protected Access 3 (WPA3)
WPA3 is the latest security protocol developed by the Wi‑Fi Alliance to secure wireless networks more effectively than previous standards like WPA2 and WPA. It offers enhanced authentication methods, improved encryption, and advanced key management techniques to protect against modern threats.
Key Features of WPA3
Enhanced Authentication:
WPA3 introduces Simultaneous Authentication of Equals (SAE), a robust key exchange method that mitigates the risk of offline dictionary attacks.Improved Encryption:
With mandatory 128-bit encryption for personal networks and 192-bit encryption for enterprise networks, WPA3 uses longer key lengths that significantly increase security.Forward Secrecy:
This security measure ensures session keys are temporary. Even if a session key is compromised, past communications remain secure.
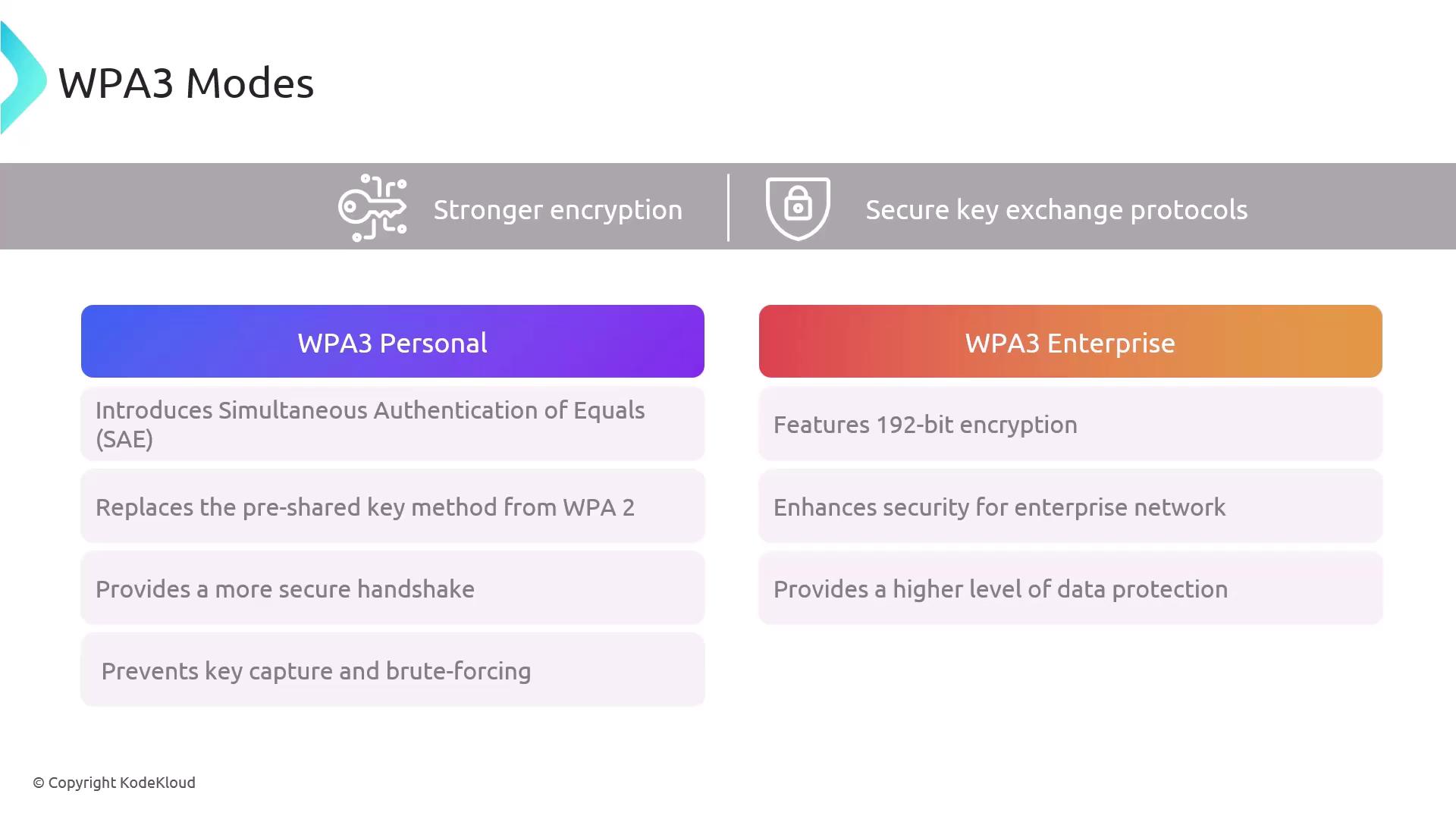
WPA3 Modes
WPA3 is available in two modes:
- WPA3 Personal: Uses SAE to replace traditional pre-shared keys, preventing brute-force key recovery.
- WPA3 Enterprise: Requires 192-bit encryption for business environments, enhancing overall network security.
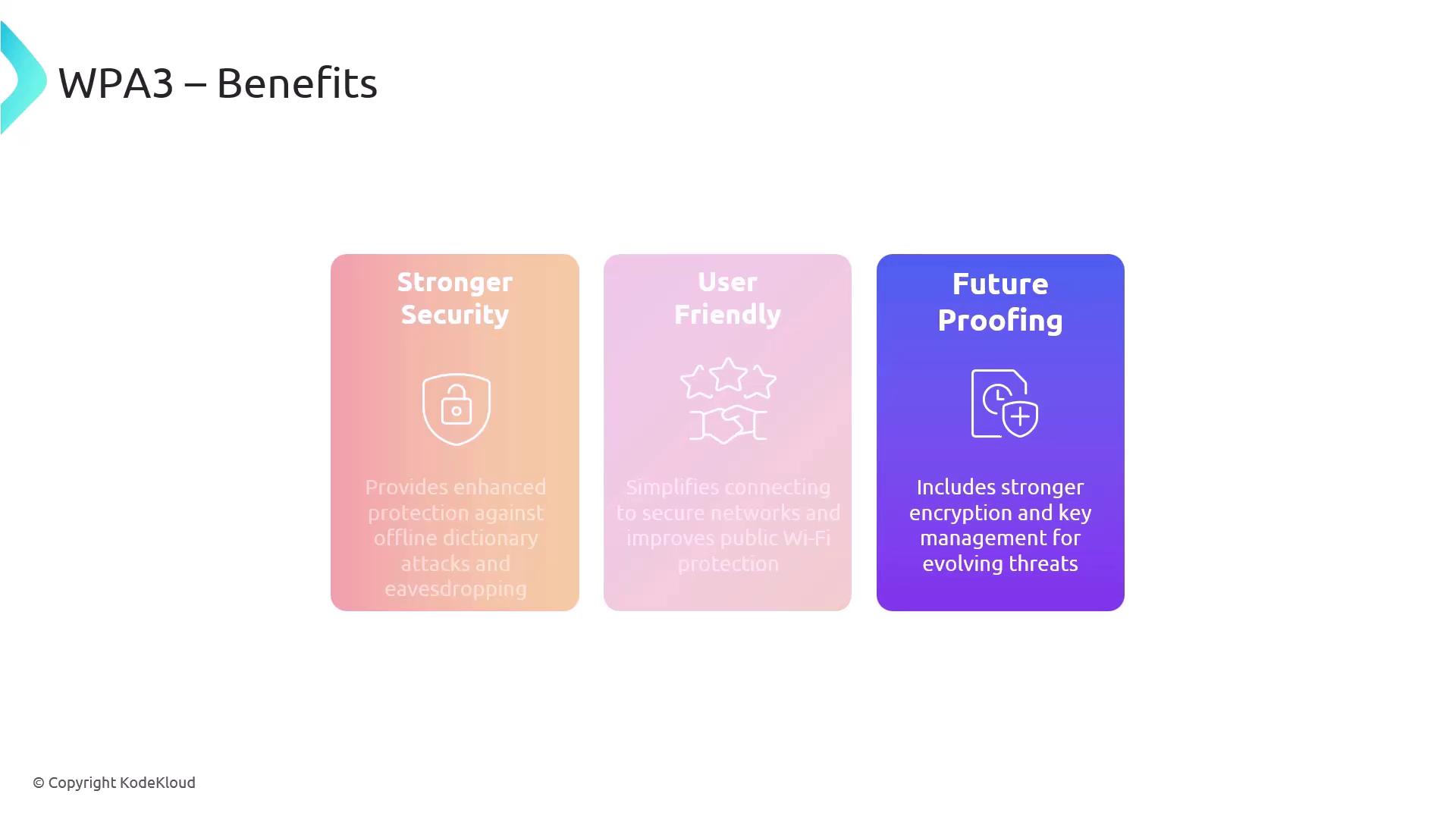
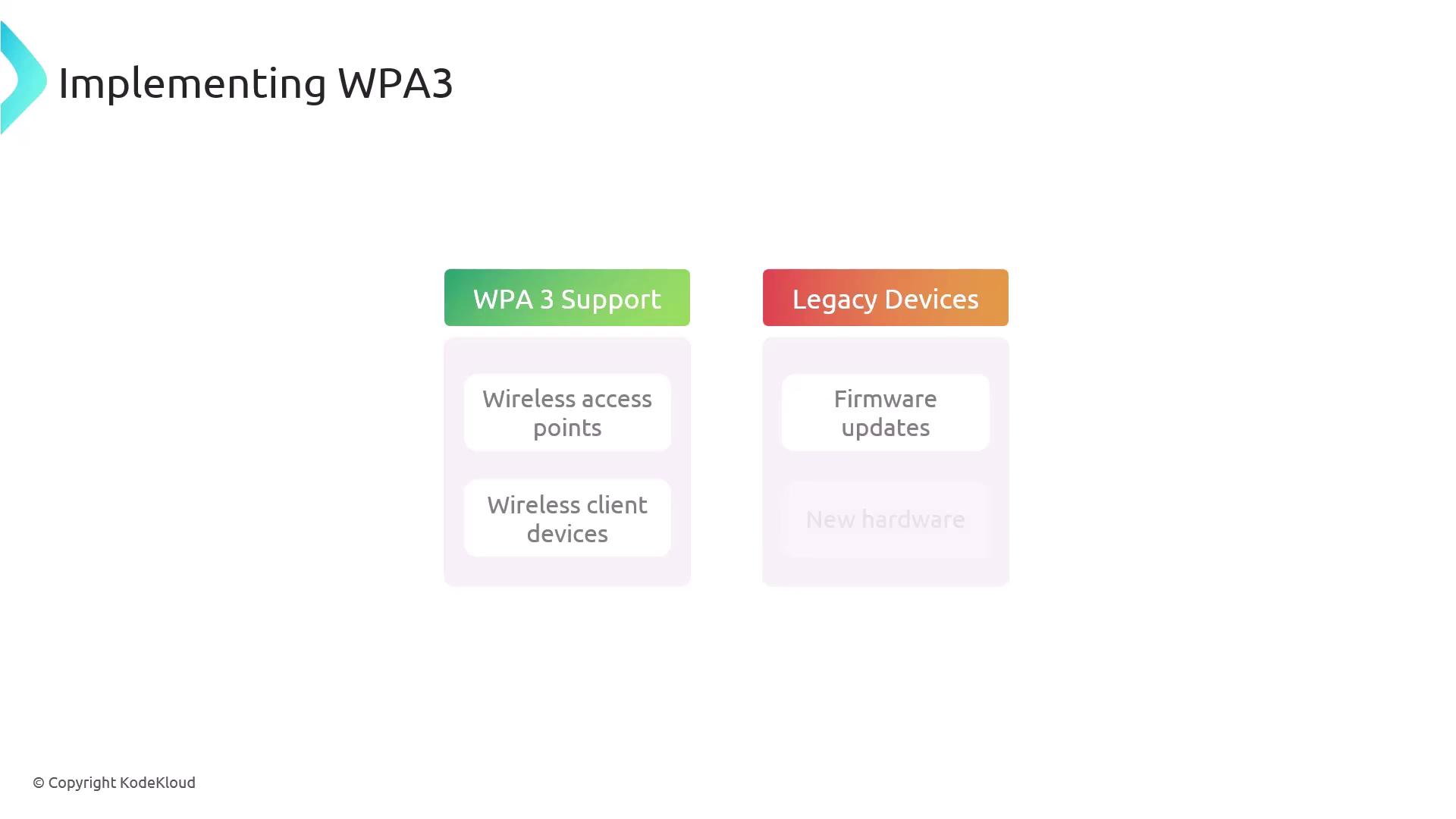
The benefits of WPA3 include stronger resistance to offline attacks, improved protection for public Wi-Fi networks, and a more streamlined connection process. However, both wireless access points and client devices must support WPA3; legacy devices might need firmware updates or new hardware.
RADIUS (Remote Authentication Dial-In User Service)
RADIUS is a critical networking protocol that supports Authentication, Authorization, and Accounting (AAA). It centralizes the process of verifying user credentials, assigning access levels, and logging user activities for enhanced network security.
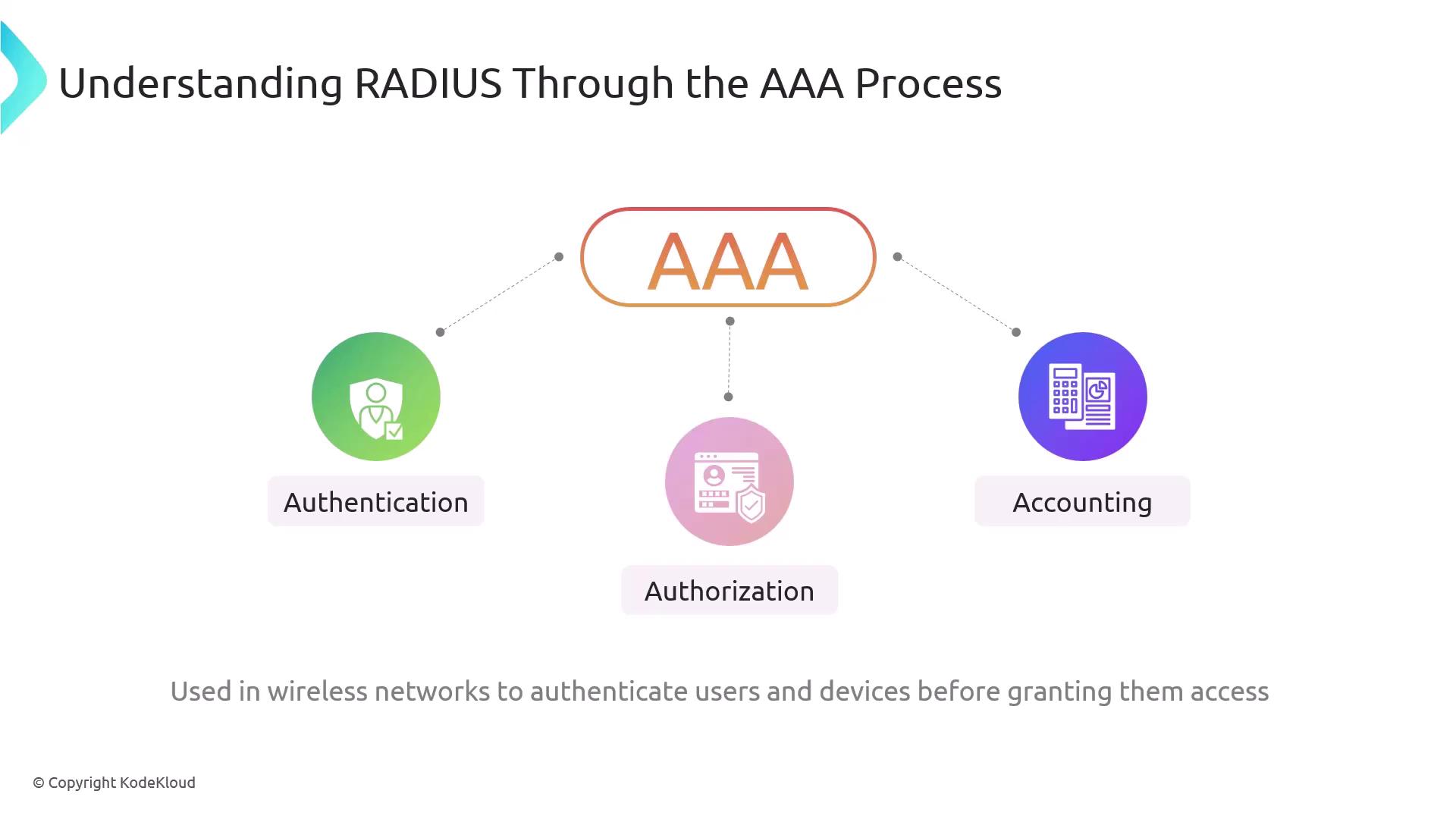
How RADIUS Works
Authentication:
When a user attempts to connect, the RADIUS server checks the credentials against its user database.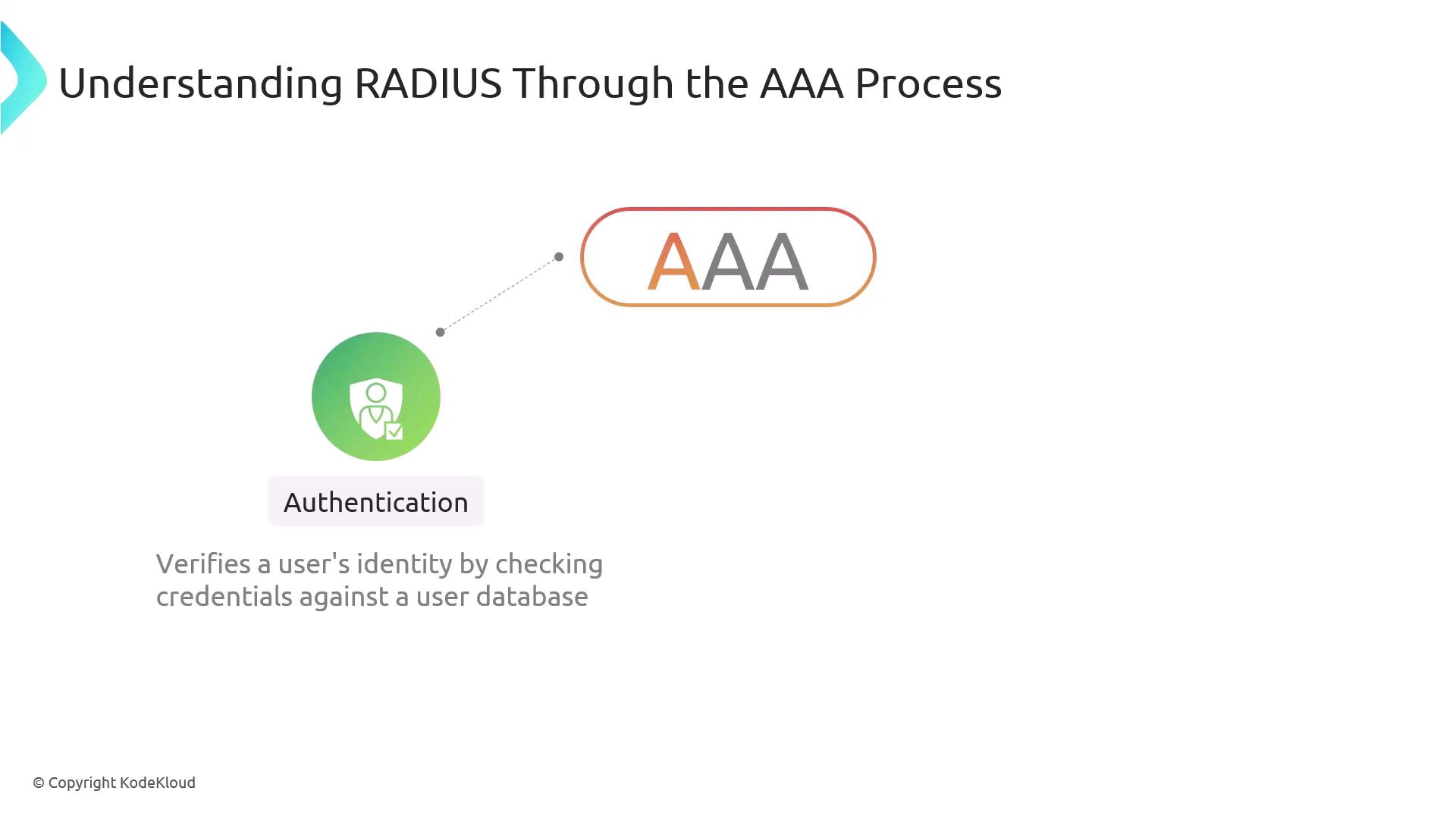
Authorization:
After successful authentication, the server determines which network resources the user is permitted to access.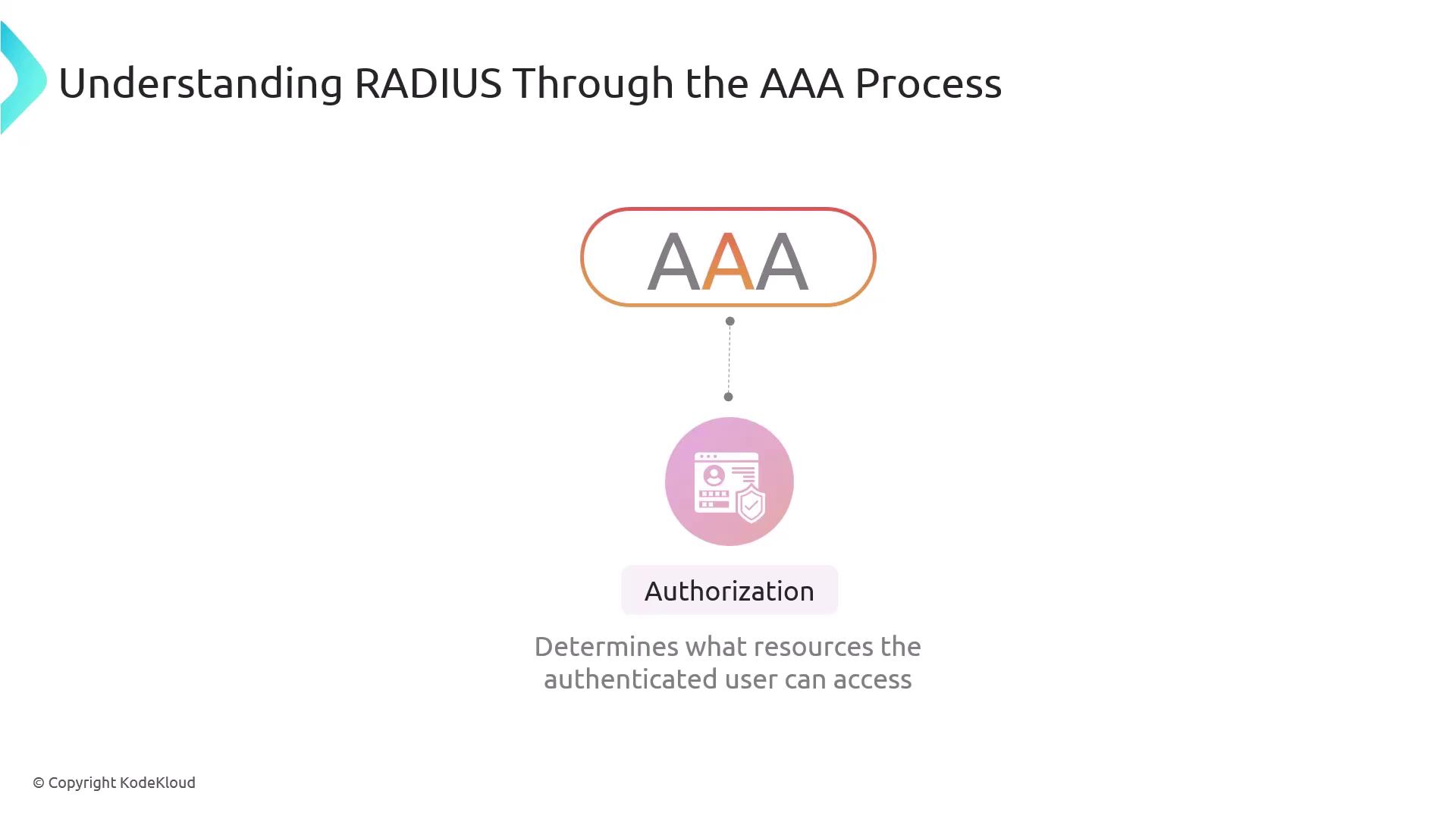
Accounting:
The RADIUS server logs session details such as duration and accessed resources, keeping a record of user activity.
RADIUS System Components
The RADIUS ecosystem includes:
| Component | Description |
|---|---|
| RADIUS Client | Typically a wireless access point that initiates authentication requests. |
| RADIUS Server | Verifies user credentials and decides on authorization. |
| User Database | Stores user credentials and access policies (can be local, LDAP, or Active Directory). |
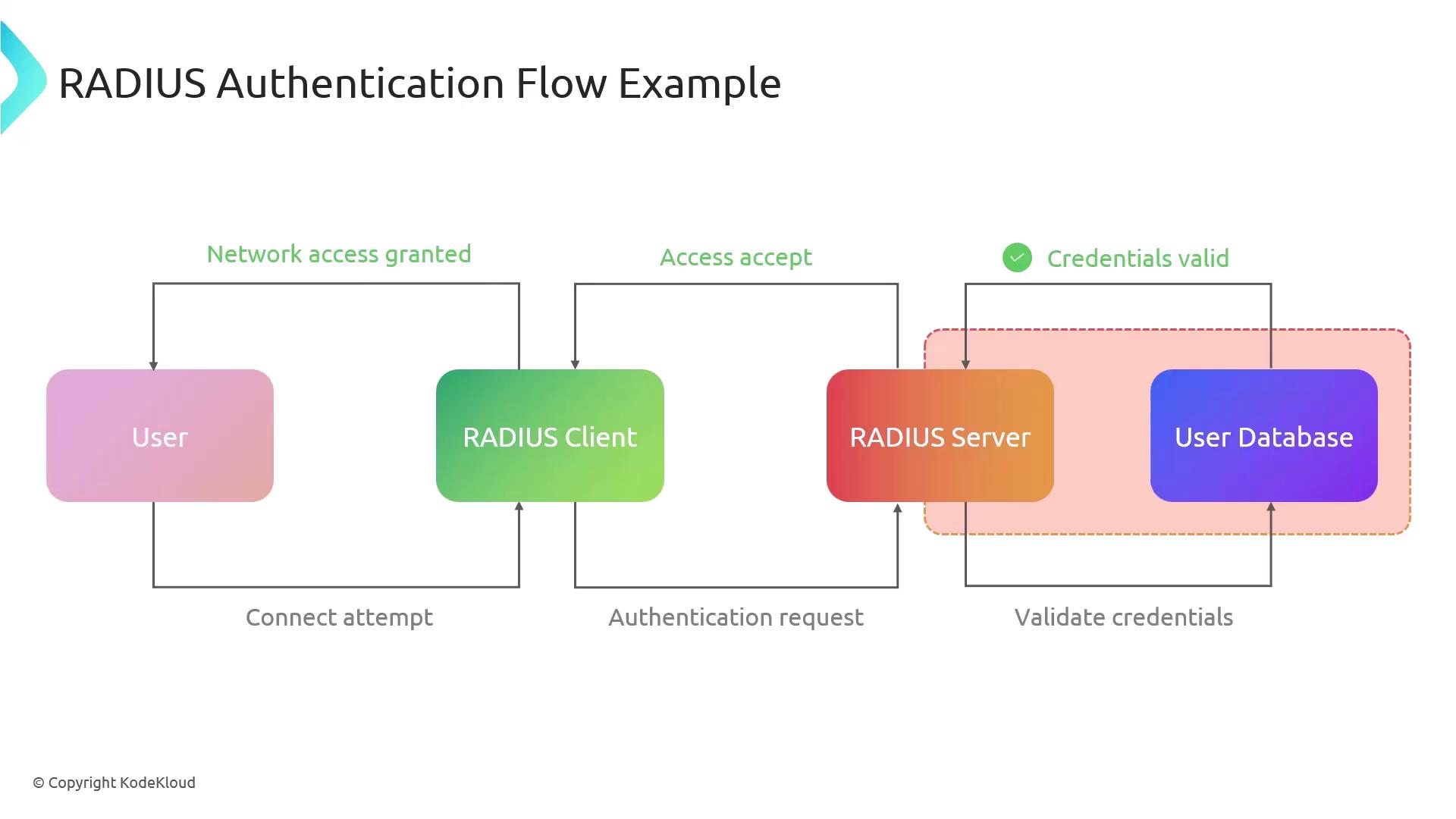
Example: RADIUS Authentication Flow
A user initiates a connection to a wireless network.
The wireless access point (RADIUS client) sends an authentication request to the RADIUS server.
The RADIUS server validates the credentials against the user database.
If the credentials are valid, the server sends an access-accept message, granting network access.
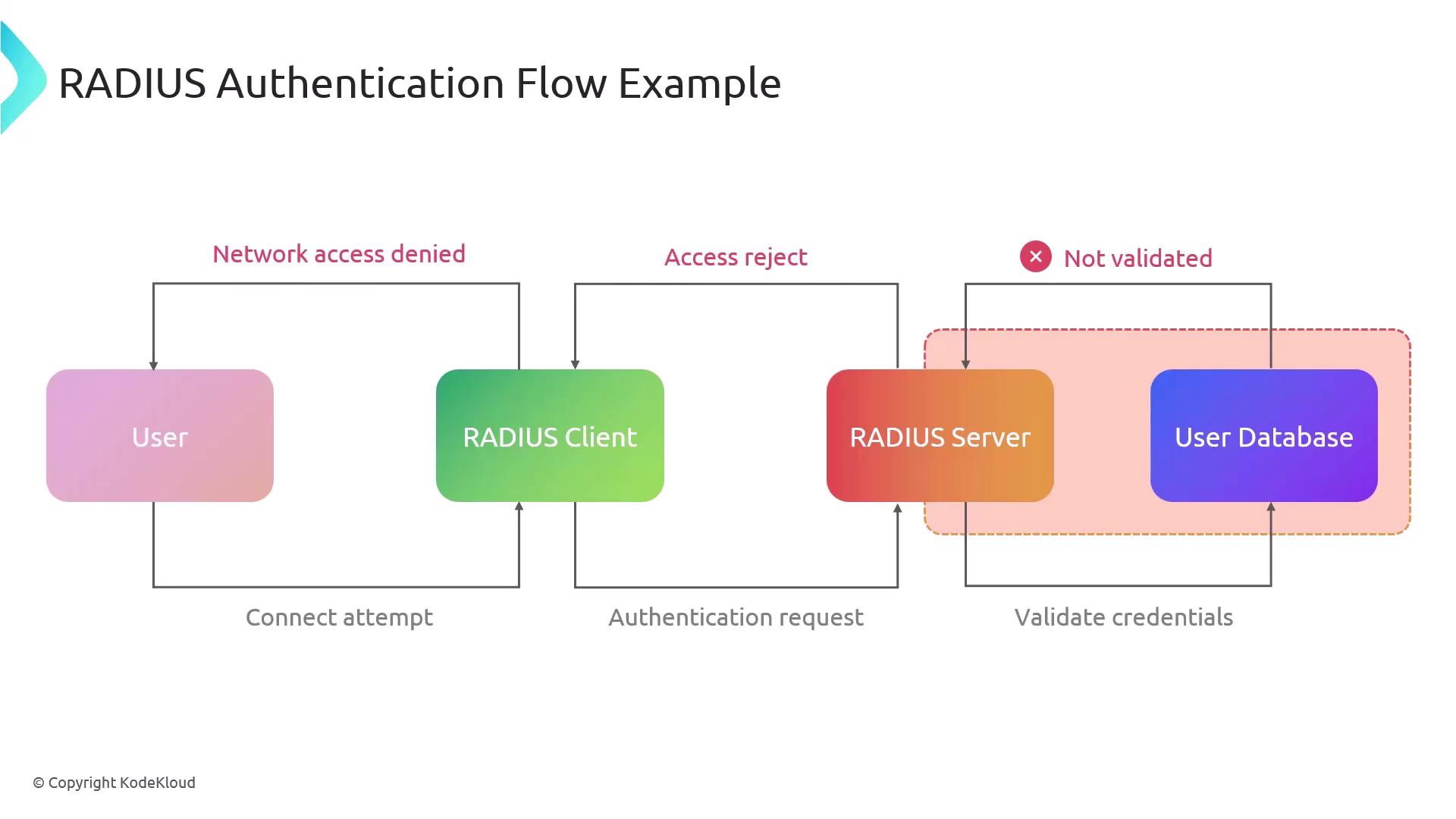
If the credentials are invalid, an access-reject message is sent to the client, denying network access.
RADIUS offers several benefits, such as centralized management, scalability, and robust security integration with protocols like the Extensible Authentication Protocol (EAP).
Cryptographic Protocols
Cryptographic protocols are at the heart of securing communications over networks by ensuring confidentiality, integrity, and authentication. They are used to protect data from unauthorized access and tampering.
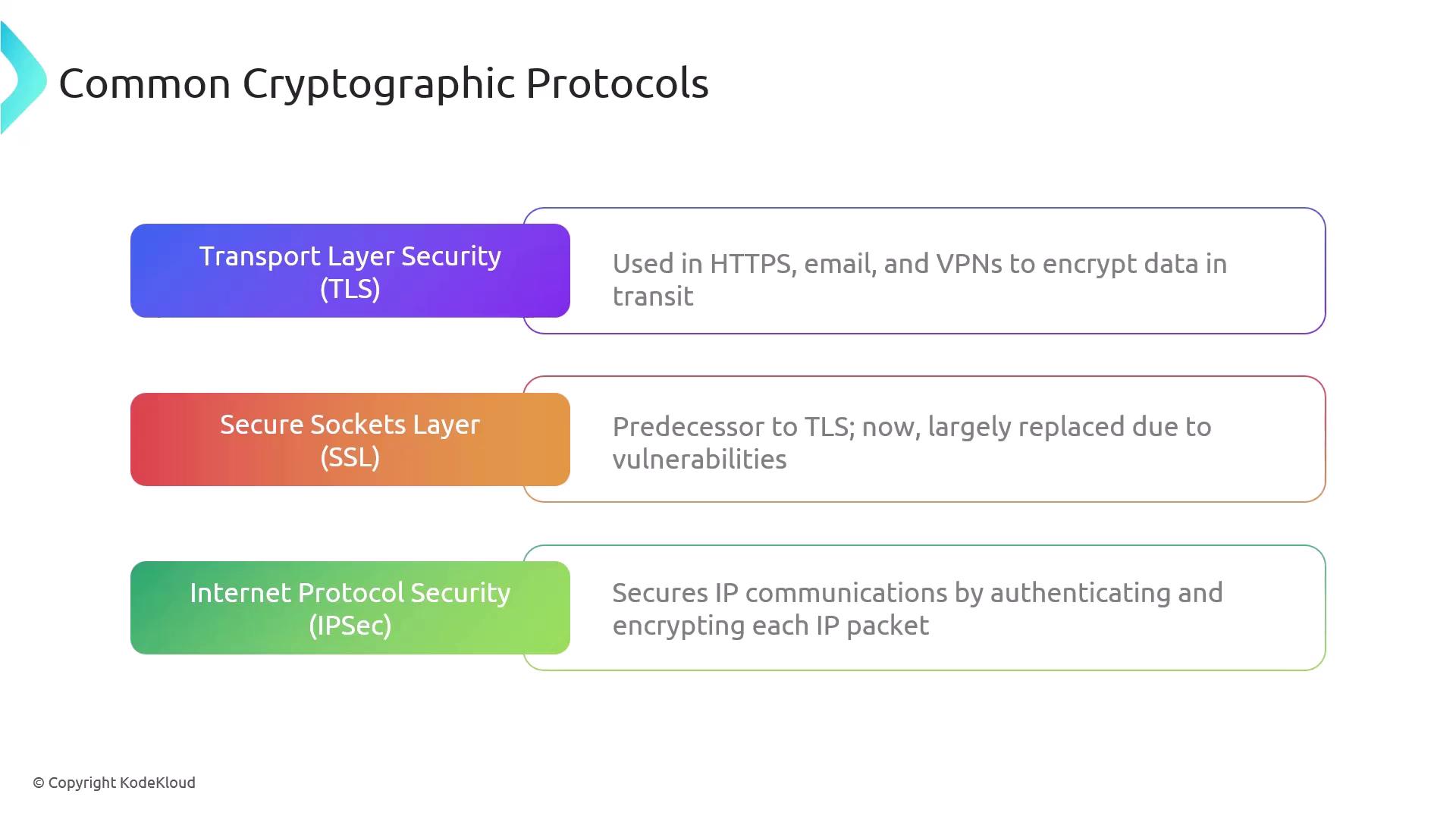
Common Cryptographic Protocols
TLS (Transport Layer Security):
Widely used with HTTPS for secure communications on the web, email, and VPN connections.SSL (Secure Sockets Layer):
Predecessor to TLS, now largely replaced due to vulnerabilities.IPsec (Internet Protocol Security):
Provides secured IP communications through authentication and encryption of each packet.WPA3 Cryptographic Enhancements:
Uses robust encryption standards—128-bit for personal use and 192-bit for enterprise setups—to secure wireless networks.
WPA3 leverages these advanced protocols to further enhance wireless security by ensuring that data is transmitted securely with strong encryption and key management.

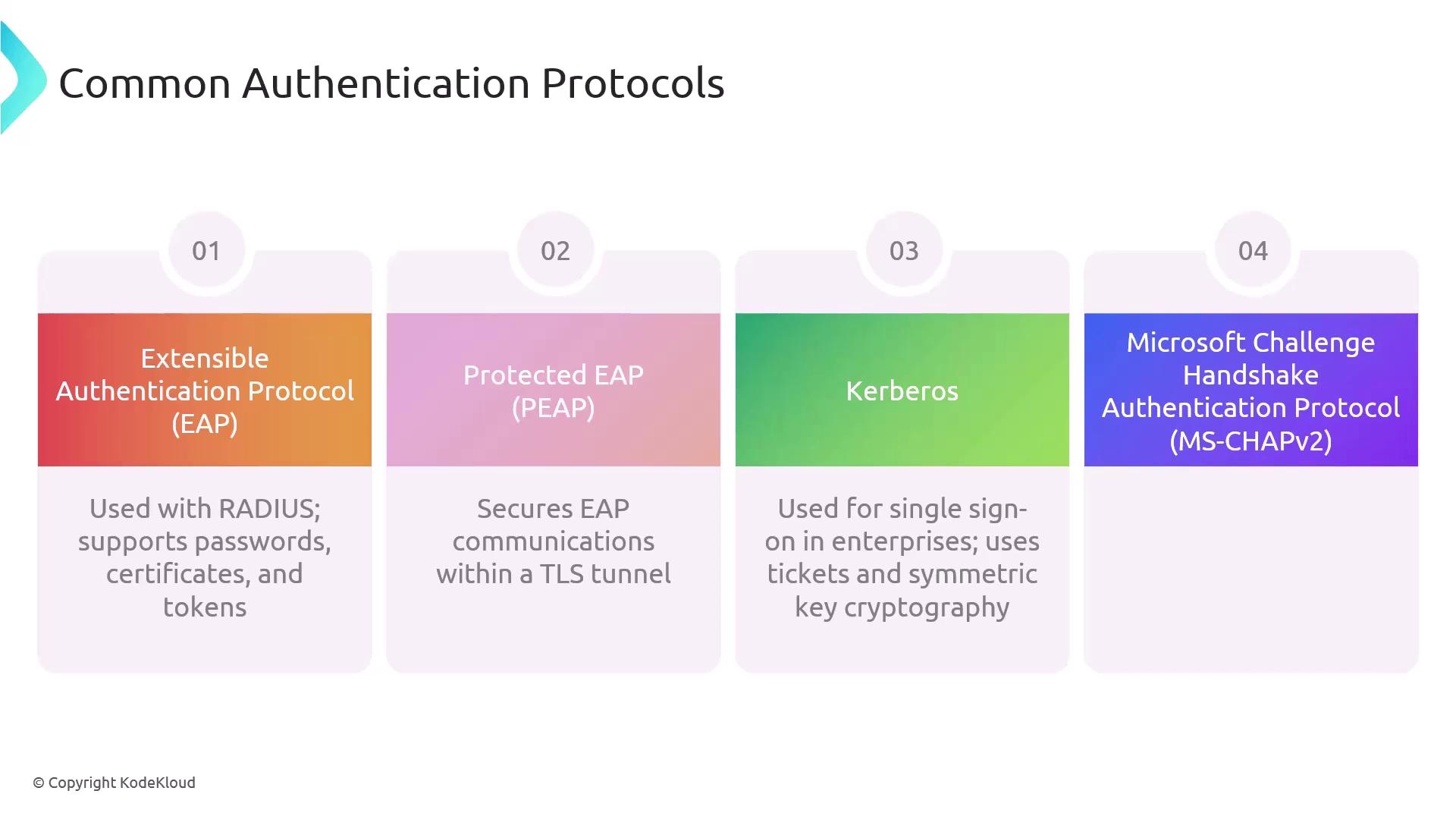
Wireless Authentication Protocols
Authentication protocols verify identities to ensure that only authorized users and devices access the network. Here are some widely used wireless authentication protocols:
EAP (Extensible Authentication Protocol):
Frequently used alongside RADIUS, it supports a variety of authentication methods including passwords, certificates, and tokens.PEAP (Protected Extensible Authentication Protocol):
Encapsulates EAP within a TLS tunnel, offering an additional layer of security.Kerberos:
Utilized in enterprise environments for single sign-on, it uses ticket-based authentication and symmetric key cryptography.MSCHAPv2 (Microsoft Challenge Handshake Authentication Protocol version 2):
Employs a challenge-response mechanism to authenticate users, commonly used in VPNs and dial-up connections.
Wireless security settings—including WPA3, RADIUS, cryptographic protocols, and authentication protocols—form the backbone of a secure network environment. By properly implementing these technologies, organizations can effectively safeguard the confidentiality, integrity, and availability of their communications in the face of evolving cyber threats.

Thank you for following along and enhancing your understanding of wireless security. For further reading, consider exploring additional resources on Kubernetes Documentation or Docker Hub.
Watch Video
Watch video content