CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Application Attacks
Web applications are frequent targets for a variety of attack methods. This guide highlights several common techniques used by threat actors to exploit vulnerabilities in web software, including injection attacks, buffer overflows, replay attacks, privilege escalation, forgery, and directory traversal. Understanding these attack vectors is essential for developing resilient and secure applications.
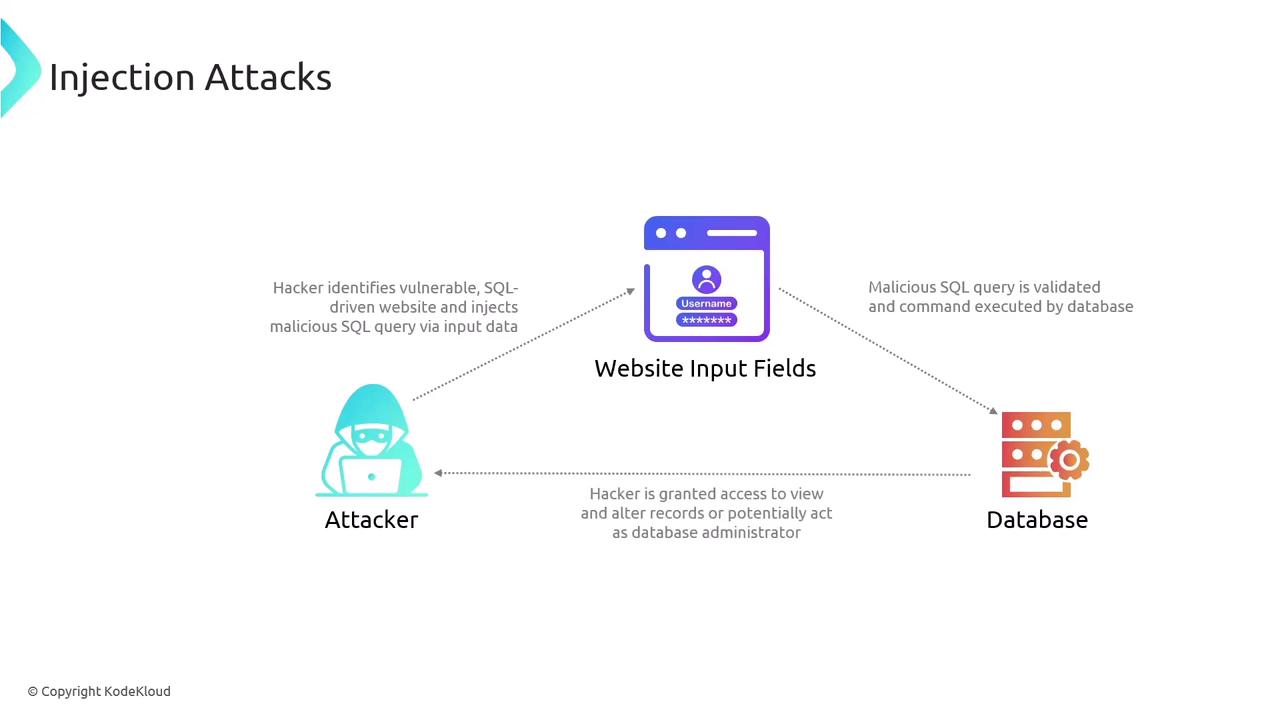
Injection Attacks
Injection attacks occur when an application improperly handles user-provided data, allowing attackers to embed malicious code into input fields. A common form is SQL injection, where attackers inject harmful SQL queries into an application's input. Without proper input validation, these queries can bypass authentication, alter data, access unauthorized information, or even execute system commands.
Security Tip
Always validate and sanitize user inputs to mitigate the risk of injection attacks. Consider using parameterized queries or prepared statements in your database interactions.
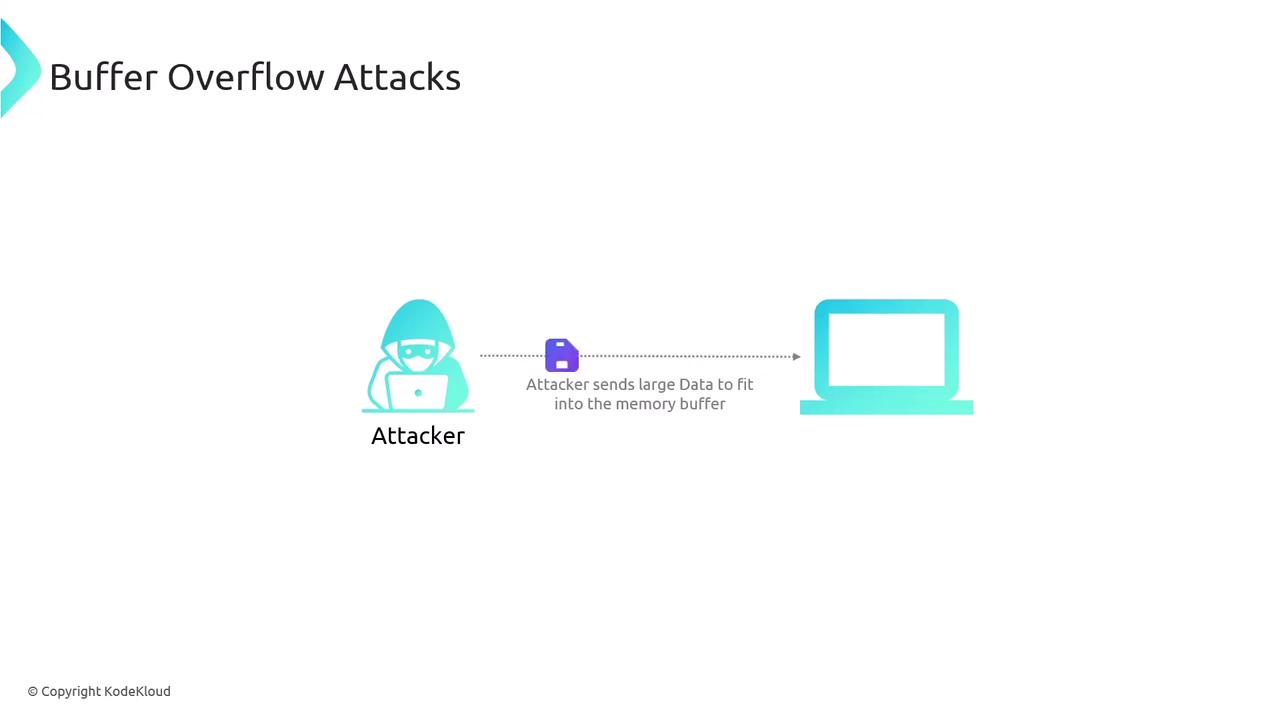
Buffer Overflow Attacks
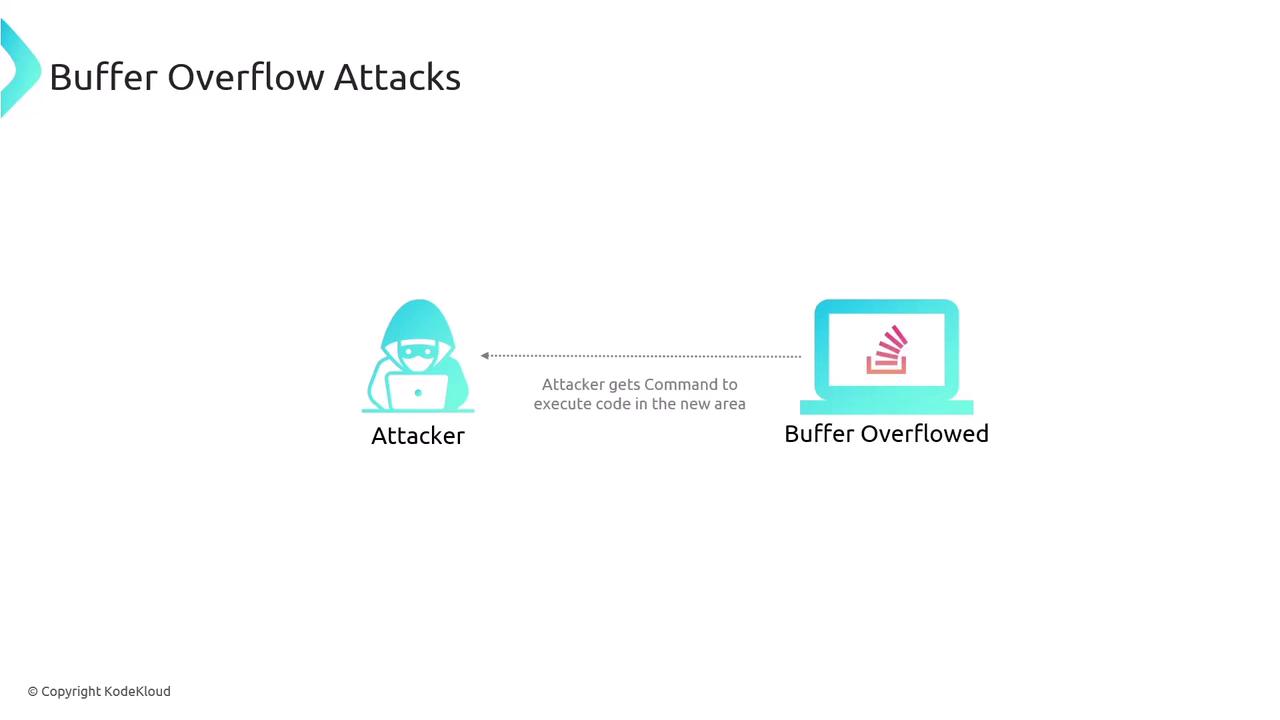
Buffer overflow attacks target vulnerabilities in how applications manage memory. Buffers are allocated memory areas meant to store specific types of information. When an attacker sends data exceeding the buffer's capacity, it can spill over into adjacent memory areas, potentially allowing execution of unintended code.
This overflow can enable an attacker to manipulate the execution flow by writing malicious code into the overflowed region.
Important
Ensure robust memory management and use programming languages or tools that offer built-in protections against buffer overflows. Always perform bounds checks and use safe functions for memory operations.
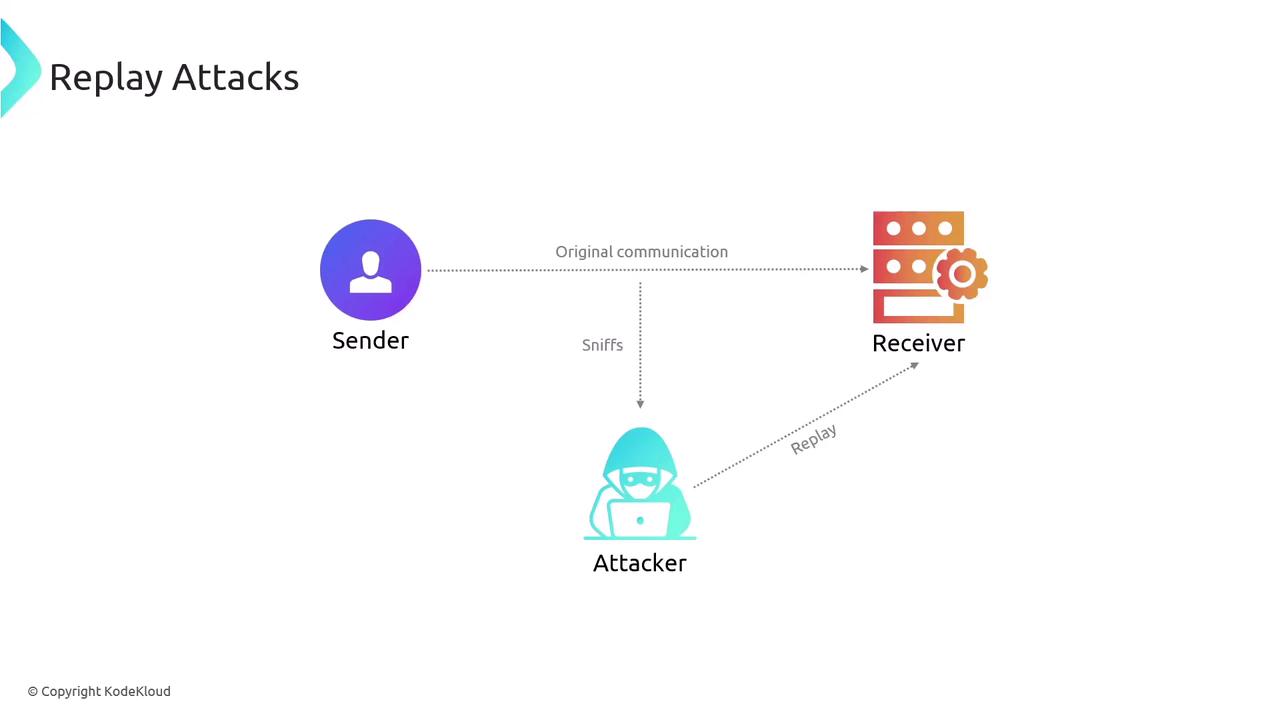
Replay Attacks
Replay attacks involve capturing and reusing valid session tokens or cookies to impersonate an authenticated user. By intercepting these tokens, an attacker can trick the web application into accepting them, thus bypassing the re-authentication process and gaining unauthorized access.
Best Practice
Incorporate robust session management and token invalidation strategies. Implement mechanisms like token expiration, one-time use tokens, and secure transmission protocols to prevent replay attacks.
Privilege Escalation and Directory Traversal
Privilege escalation occurs when an attacker gains elevated system permissions, enabling them to execute high-impact commands. Similarly, directory traversal involves manipulating web server directory structures via URL inputs. This technique can expose sensitive files or functionalities by accessing directories beyond the intended scope.
Understanding both privilege escalation and directory traversal is crucial because elevated privileges and unauthorized directory access can lead to significant data breaches and system manipulation.
By focusing on robust input validation, secure memory management, diligent session security, and properly configured directory access, developers can substantially reduce the risk of these vulnerabilities being exploited.
For further reading on web application security best practices, visit OWASP Web Security Testing Guide.
Watch Video
Watch video content