CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Malicious Activities
In this article, we explore a range of malicious activities—including malware, application attacks, password attacks, physical attacks, and attack indicators. We begin by delving into the world of malware and its various forms.
What Is Malware?
Malware, short for malicious software, is any software that performs actions not intended by the user. This umbrella term covers harmful programs such as viruses, worms, Trojan horses, potentially unwanted programs (PUPs) or bloatware, spyware, keyloggers, ransomware, logic bombs, and rootkits.
![]()
Viruses
Computer viruses are designed to replicate themselves by infecting files and spreading to other computers. They are typically categorized by the type of file or media they target.

Boot Viruses
A boot virus resides in a computer's boot sector, ensuring it executes each time the system starts. These viruses can also inhabit removable media like USB drives, posing a significant threat whenever such media are used at startup.
![]()
Note
Memory-resident viruses load a copy of themselves into the computer's RAM, allowing them to continue running even after the initial process has ended.
Memory-Resident Viruses
Memory-resident viruses embed themselves into a system’s memory (RAM), sustaining their presence and functionality even if the originating process is terminated.

Macro Viruses and Worms
Macro viruses exploit built-in macro features in applications like Microsoft Office and PDFs. Typically hidden within documents, these macros activate upon opening, often without the user's knowledge.
In contrast, worms function independently, executing without direct user interaction. They can run simply when a user visits a compromised website or accesses a shared network drive.

Trojans
Trojans are deceptive in nature because they disguise themselves as legitimate software. Unlike potentially unwanted programs (PUPs), which may be bundled with other software and not always harmful, Trojans are specifically engineered to trick users into installing them.
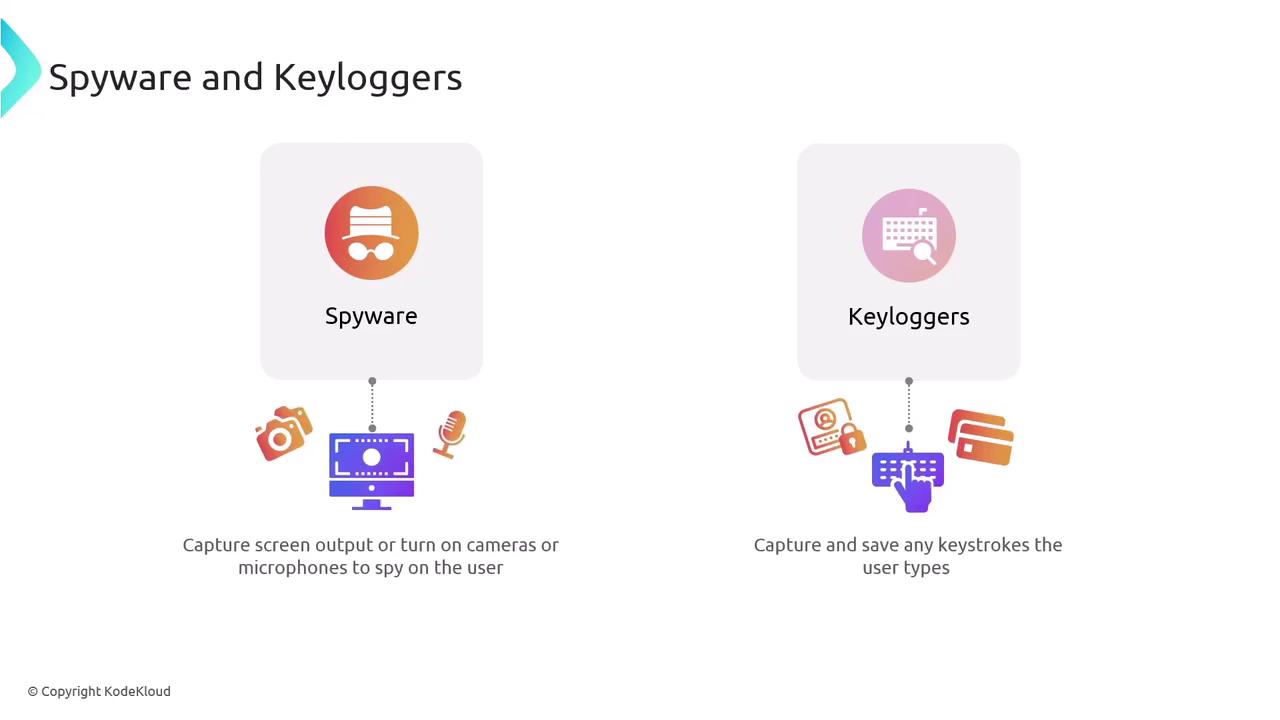
Spyware and Keyloggers
Spyware and keyloggers both monitor user activities, but they do so in different ways. Keyloggers capture every keystroke, potentially exposing sensitive information such as passwords and credit card numbers. Spyware, on the other hand, can record screen output or even activate cameras and microphones to spy on users.
Ransomware and Logic Bombs
Ransomware is designed to extort money from users by encrypting or locking access to critical files. A notable example is the REvil variant, which targets large organizations using files with the .ryk extension. Not all malware is designed for immediate activation; some, known as logic bombs, trigger at a specific time or in response to a particular event.

Warning
Rootkits are extremely dangerous as they are engineered to escalate privileges, granting system administrator access. This enables them to hide their presence and bypass security measures. Implementing robust security protocols is essential to guard against such threats.
Rootkits
Rootkits focus on stealth by elevating their access to system-administrator levels. This privilege escalation not only conceals their presence but also enhances their ability to manipulate and control the infected system.
By familiarizing yourself with these various types of malware, you can better safeguard your systems and networks against potential threats. For further insights into cybersecurity best practices, consider reviewing our additional Cybersecurity Documentation.
Watch Video
Watch video content