CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Misconfiguration Vulnerabilities
Misconfiguration vulnerabilities occur when systems, applications, or networks aren't set up securely, creating exploitable weaknesses. Typically, these vulnerabilities stem from human error, insufficient knowledge, or inadequate security practices.
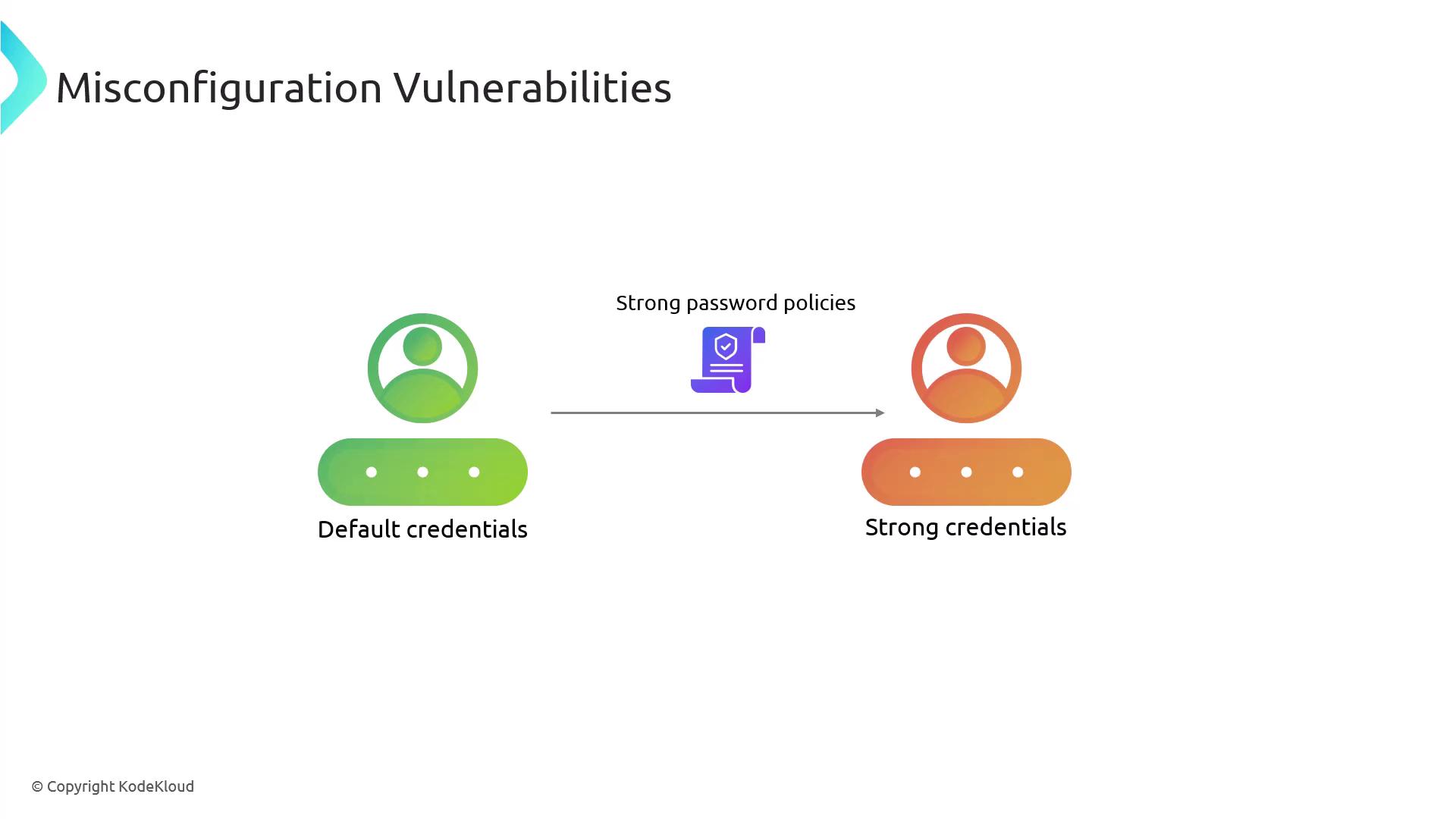
A frequent example involves the use of default credentials. New equipment often arrives with pre-configured usernames and passwords to streamline the setup process. However, these default settings are usually the same across several devices from a single manufacturer and are often documented in the user manual. Consequently, attackers can readily take advantage of these known credentials.
Tip
Immediately change default credentials after installation and enforce strong password policies to fortify system security.
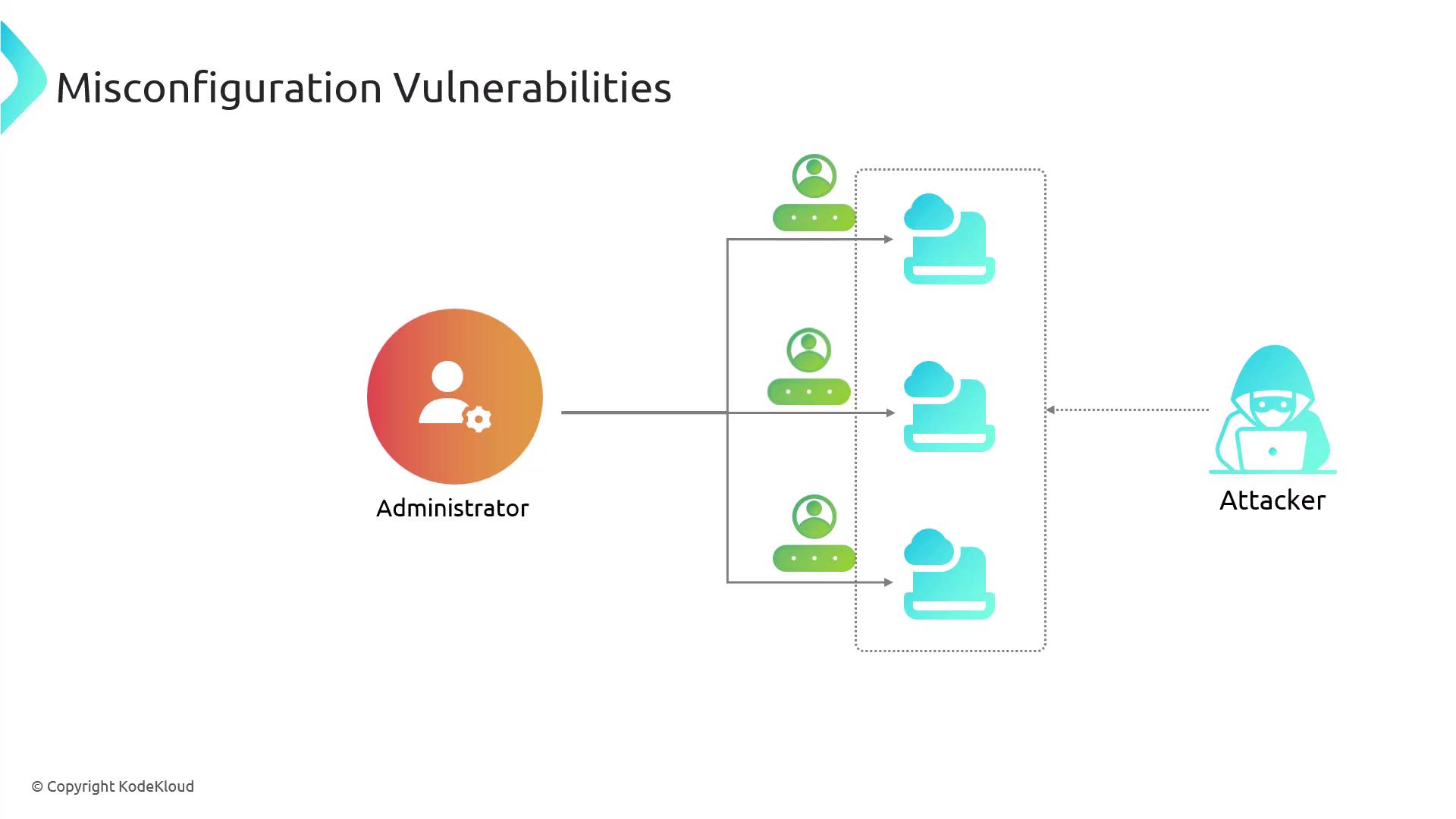
Retaining default credentials provides an easy entry point for attackers. It is essential to reinforce security by updating credentials immediately upon deployment.
Beyond default credentials, it's crucial to regularly review and update configuration settings. For instance, systems or network devices might have unnecessary open TCP or UDP ports that serve no purpose if no associated application is running. These open ports, whether due to human error or legacy configurations, can expose systems to significant risks.
Security Alert
Conduct regular security audits and vulnerability assessments to identify and remediate any misconfigurations promptly.

By following security best practices, consistently auditing systems, and ensuring correct configuration, organizations can substantially reduce the risks associated with misconfiguration vulnerabilities.
Watch Video
Watch video content