CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Threat Actors and Motivations
In this lesson, we examine the various threat actors in today’s security landscape, their motivations, and how they exploit vulnerabilities. Understanding these concepts is crucial for analyzing and mitigating security risks in any environment.
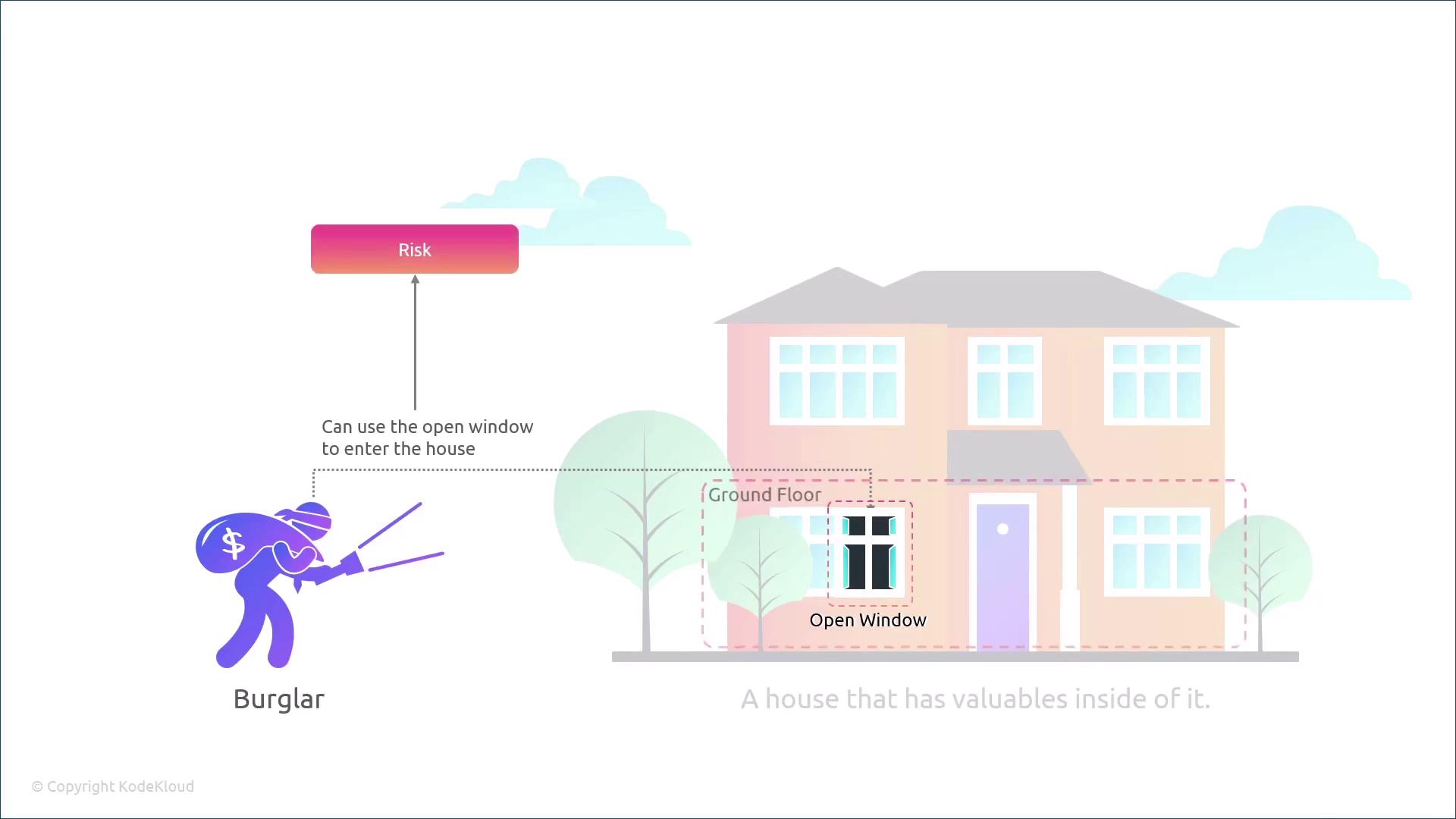
Imagine you own a house filled with valuables. Now, picture an open window in that house. This open window represents a vulnerability—a weakness that an attacker can exploit—even if every other entry point is well secured. Later in this course, we will explore vulnerabilities in depth, covering weaknesses in hardware, software, networks, and physical security.
Now, consider a burglar planning to break into the house. This burglar is the threat actor. With both a vulnerability (the open window) and a threat actor (the burglar), there exists a potential threat: the risk that an intruder could exploit the vulnerability.
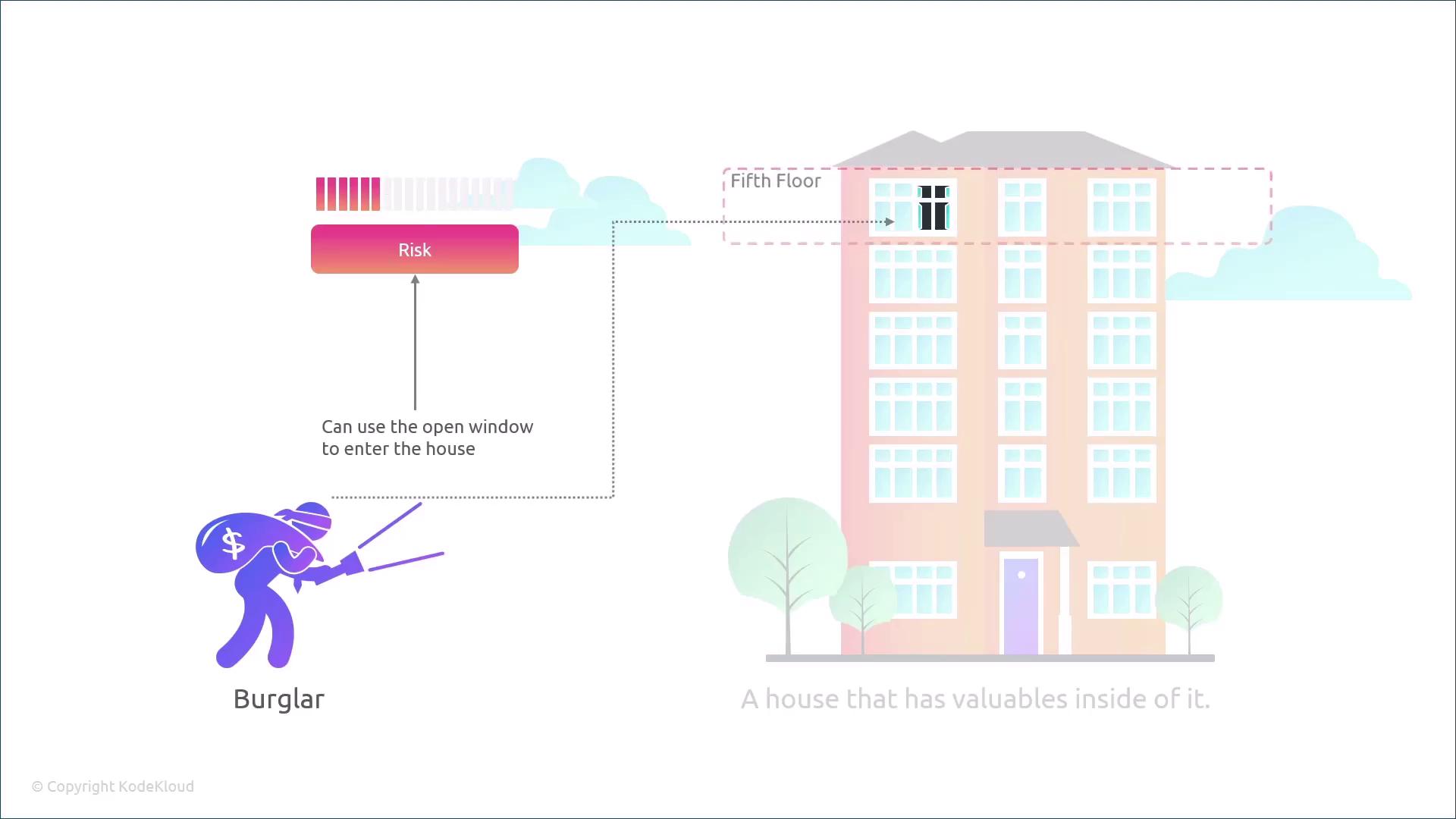
A threat is defined as the potential for someone to exploit a vulnerability. The risk level depends on the likelihood of the threat actor’s successful exploitation and the possible impact. For instance, if the open window is on the ground floor, the risk is considerably higher.
Conversely, if the open window is on the fifth floor, both the probability of entry and the associated risk are reduced.
Key Concepts
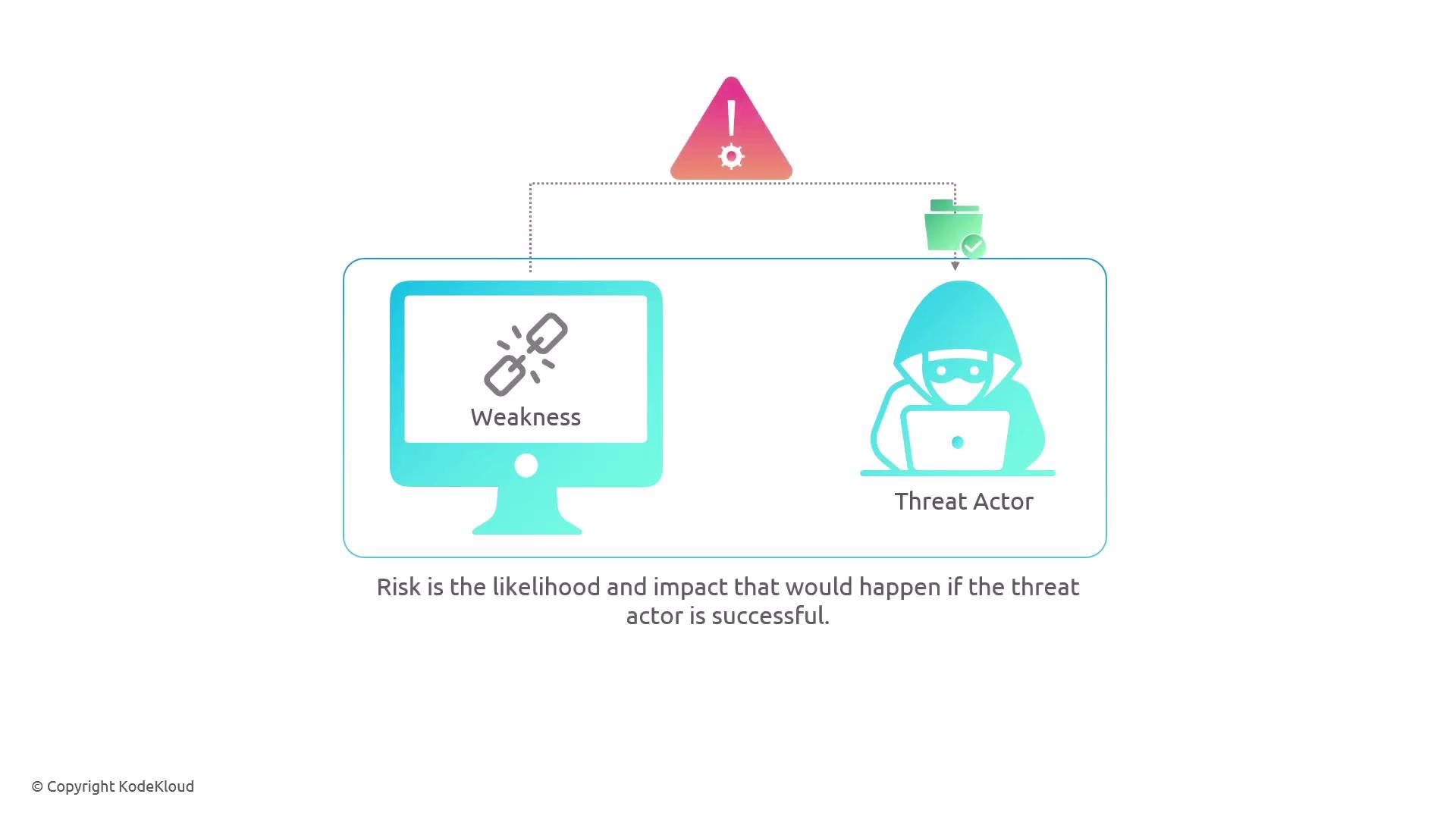
Before diving deeper into threat actors, it is important to understand the differences between vulnerabilities, threats, and risk:
- A vulnerability is a flaw or weakness.
- A threat involves a threat actor who is willing and able to exploit a vulnerability.
- Risk is determined by the likelihood of the exploitation and the potential impact.
When assessing risk, two essential factors come into play:
- The likelihood that a threat will exploit a vulnerability.
- The potential impact if the exploitation is successful.
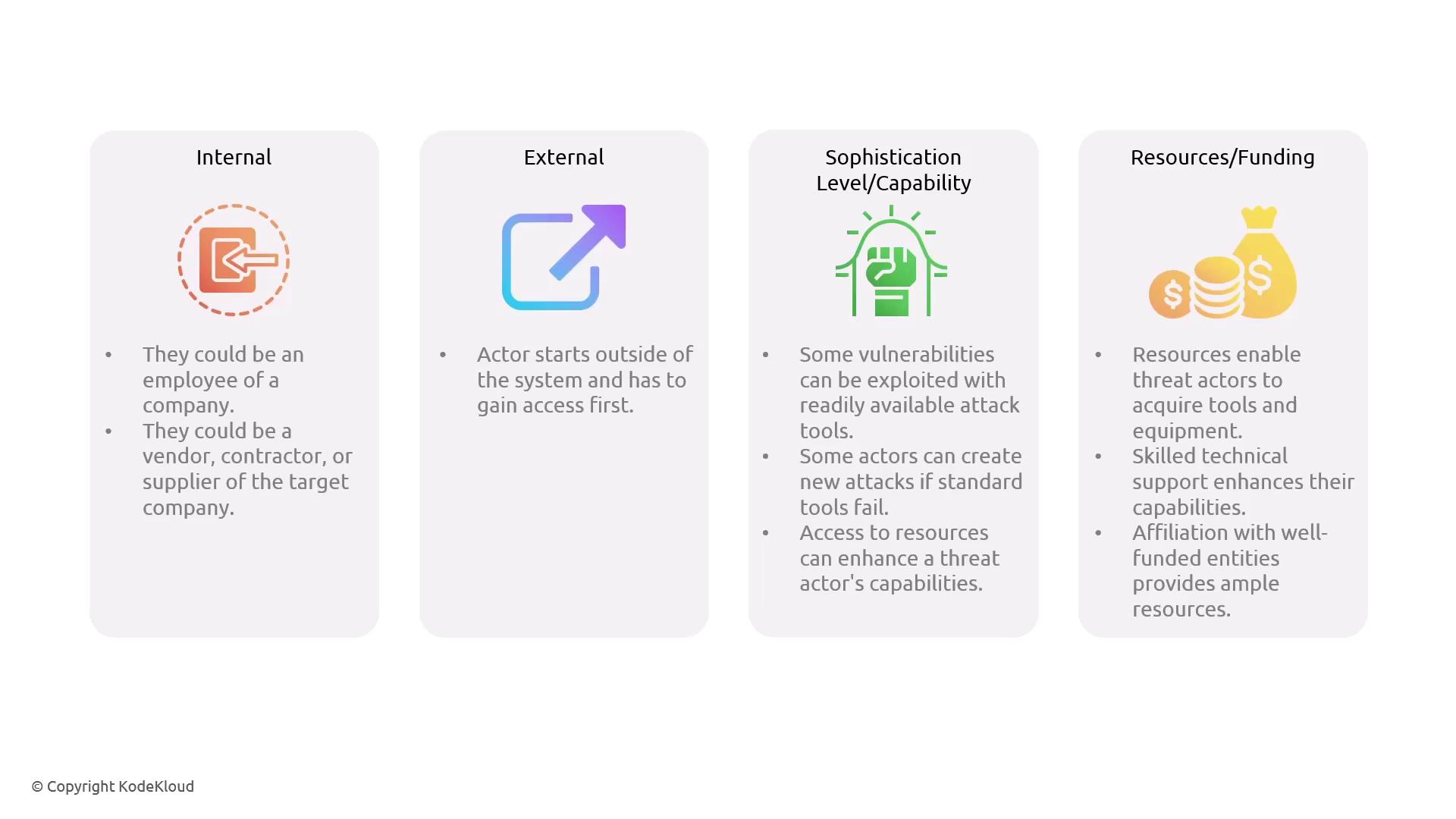
Not all threat actors are alike. They are categorized and differentiated by several attributes, including their origin, capabilities, and available resources. For example:
- Internal Threat Actors: These individuals already have access permissions within the system. This category includes employees, vendors, contractors, or suppliers.
- External Threat Actors: These attackers must first gain access to the system before attempting to exploit vulnerabilities.
The capabilities of a threat actor also play a significant role. Some vulnerabilities require minimal effort to exploit because numerous attack tools and kits are readily available online. In contrast, advanced threat actors may develop entirely new exploits when existing tools fall short. Their advanced capabilities are often supported by substantial resources, including financial backing, specialized equipment, and skilled personnel such as coders or hackers. Well-funded threat actors—such as those affiliated with nation-states or organized crime—typically possess significant resources.
For instance, nation-state threat actors may include members of a country's military or government agencies, typically armed with extensive resources and advanced capabilities compared to other threat actors.
This concludes our overview of threat actors and their motivations.
Understanding vulnerabilities, threats, and risk enables you to better analyze diverse security scenarios and devise more effective strategies against potential attacks.
For additional information on cybersecurity concepts, consider exploring these resources:
Watch Video
Watch video content