GCP DevOps Project
Sprint 03
CICD Design Discussion
Streamlining your software delivery with a robust CI/CD pipeline ensures that every code change in GitHub is automatically built, tested, and deployed to Google Kubernetes Engine (GKE). This guide walks through planning, building, storing, and deploying Docker images to GKE using Kubernetes manifests.
Key Pipeline Questions
- How do we automate Docker image builds?
- Where should we store Docker images?
- How do we deploy images to GKE with Kubernetes manifests?
1. Automating Docker Image Builds
Manual Docker builds after each commit are not scalable. We need an automated build system that triggers on every Git push.
Note
Popular CI/CD tools for GitHub integrations include GitHub Actions and Google Cloud Build.
Example snippet for a Cloud Build trigger (cloudbuild.yaml):
steps:
- name: 'gcr.io/cloud-builders/docker'
args: ['build', '-t', 'gcr.io/$PROJECT_ID/my-app:$SHORT_SHA', '.']
images:
- 'gcr.io/$PROJECT_ID/my-app:$SHORT_SHA'
2. Storing Docker Images
After building, push your image to a registry. Below is a comparison of popular options:
| Registry Type | Use Case | Example Push Command |
|---|---|---|
| Docker Hub | Public/Open Source projects | docker push myuser/my-app:latest |
| Google Artifact Registry/Registry | Private GCP workloads | docker push gcr.io/my-project/my-app:latest |
| Self-hosted Registry | On-prem or hybrid deployments | docker push registry.mycompany.com/my-app:stable |
Warning
Ensure proper IAM roles or credentials are configured before pushing images. Avoid embedding credentials in your repository.
3. Deploying to GKE with Kubernetes Manifests
Kubernetes manifests define how your application runs in GKE. At minimum, you need:
- Deployment: Manages pods and updates
- Service: Exposes pods inside/outside the cluster
Common Kubernetes Resources
| Resource Type | Description | Example CLI |
|---|---|---|
| Deployment | Declarative update for Pods | kubectl apply -f deployment.yaml |
| Service | Stable network endpoint for Pods | kubectl apply -f service.yaml |
| Horizontal Pod Autoscaler (HPA) | Automatic scaling based on CPU/memory | kubectl apply -f hpa.yaml |
| Ingress | HTTP routing into the cluster | kubectl apply -f ingress.yaml |
Beyond the basics, you can add:
![]()
4. End-to-End CI/CD Workflow
Combine build, storage, and deployment into a single automated flow:
- Detect changes in the GitHub repository (e.g., on
mainbranch). - Trigger build: Run Docker build, run tests, and tag the image.
- Push image to the artifact registry.
- Deploy to GKE:
kubectl apply -fthe updated YAML manifests.
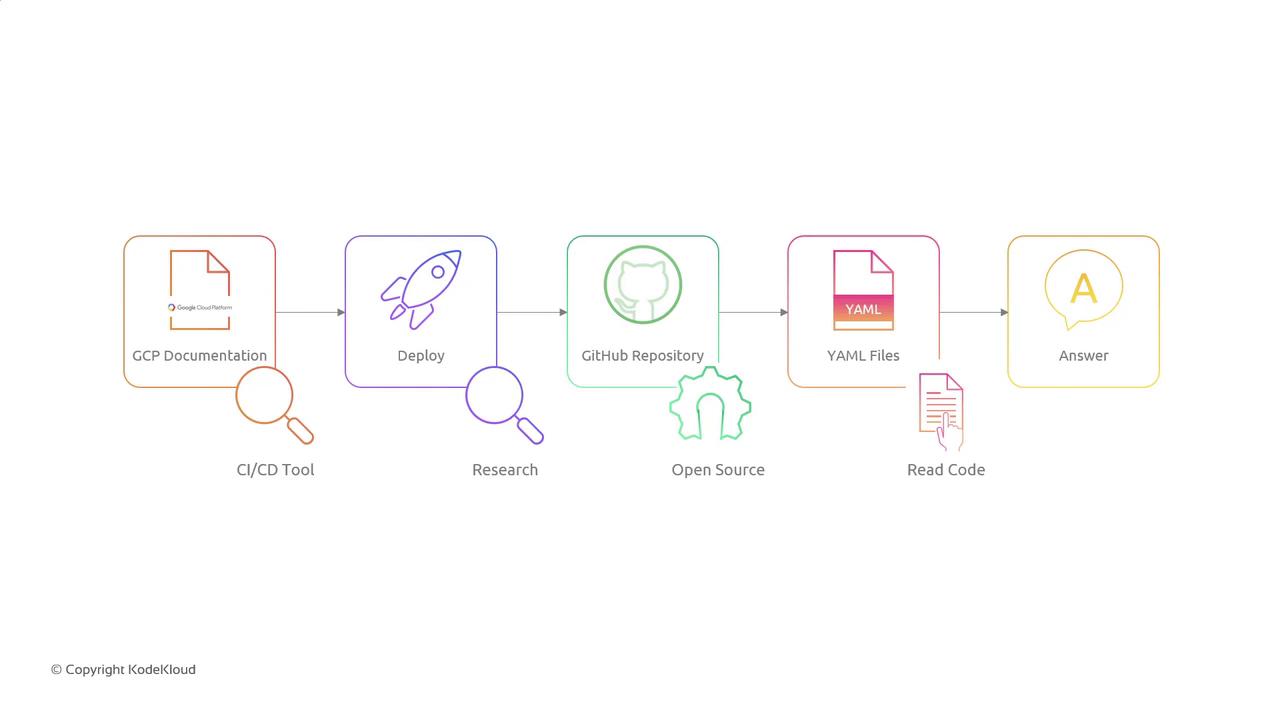
5. Research and Collaboration
Before implementation, perform a research phase to refine your CI/CD strategy:
- Review Google Cloud Build documentation for CI/CD best practices.
- Explore open-source pipeline examples on GitHub.
- Audit existing Kubernetes YAML files to learn naming conventions and labels.
- Collaborate with senior engineers to validate security and scalability requirements.
Links and References
With these design considerations, you’re ready to implement a fully automated CI/CD pipeline that builds, stores, and deploys Docker images to GKE. Good luck!
Watch Video
Watch video content