GKE - Google Kubernetes Engine
Managing Security Aspects
Control encryption of sensitive data on GKE
In this article, we explore the three states of application data—at rest, in transit, and in use—and detail how Google Kubernetes Engine (GKE) implements encryption mechanisms to protect customer data throughout its lifecycle.
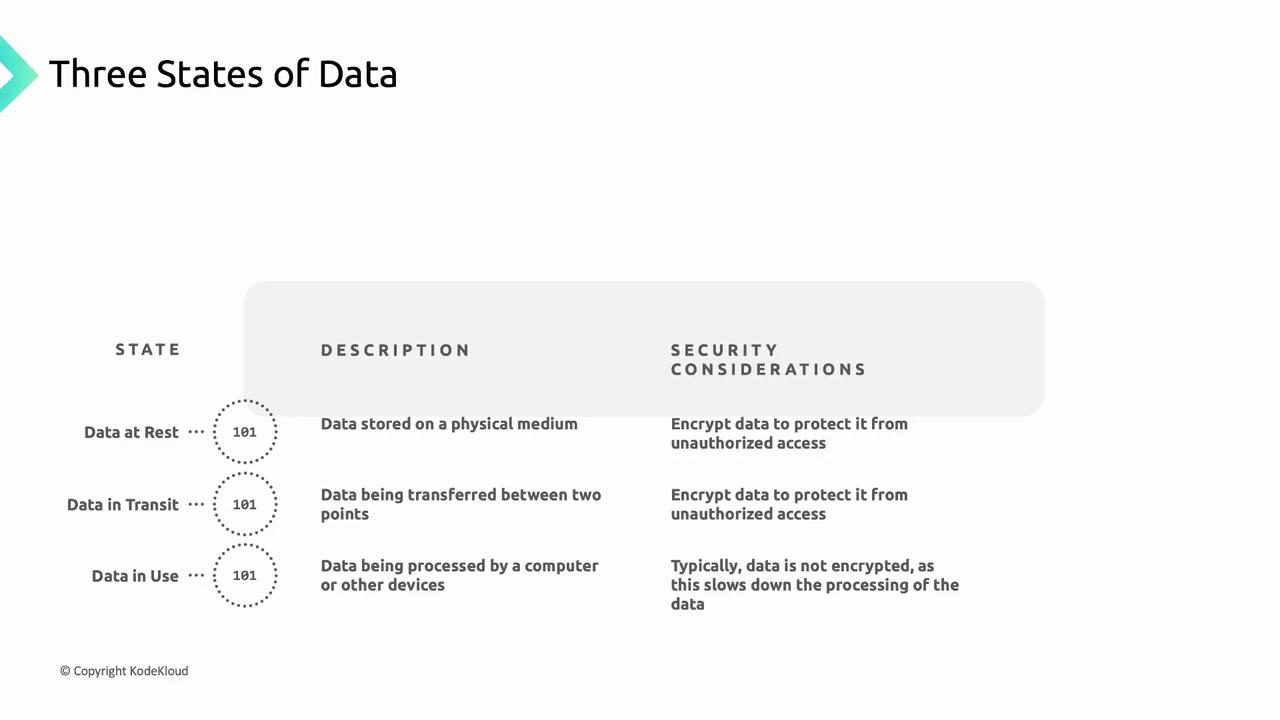
Data States Overview
| Data State | Definition | Examples |
|---|---|---|
| Data at rest | Stored on disks, SSDs, databases, or cloud storage, typically dormant | Persistent volumes, database backups |
| Data in transit | Transmitted across networks using protocols like HTTP(S) or gRPC | API calls, file transfers |
| Data in use | Actively processed in memory or cache by applications or OS processes | In-memory computations, data analytics |
GKE applies encryption by default across all three states to ensure confidentiality, integrity, and compliance.
Encryption at Rest
Google Cloud automatically encrypts all customer data at rest using the Advanced Encryption Standard (AES-256). To meet compliance or key ownership requirements, you can use Cloud Key Management Service (Cloud KMS):
- Create, rotate, and manage your own cryptographic keys.
- Implement envelope encryption for layered security.
- Audit and control key usage with IAM policies.

Note
Customer-managed encryption keys (CMEK) let you maintain full control over key rotation, access policies, and audit logs.
Encryption in Transit
All data exchanged between clients and Google Cloud services is protected by HTTPS (TLS). Key features include:
- TLS handshake powered by BoringSSL.
- Default support for strong cipher suites and forward secrecy.
- Encryption for both user-facing traffic and internal API calls.
This ensures authenticity, integrity, and privacy for every request and response.
Warning
Ensure your clients and services support TLS 1.2 or higher to comply with Google’s security requirements.
Encryption in Use
GKE’s Confidential Nodes leverage Compute Engine Confidential VMs to encrypt VM memory, protecting data during processing.
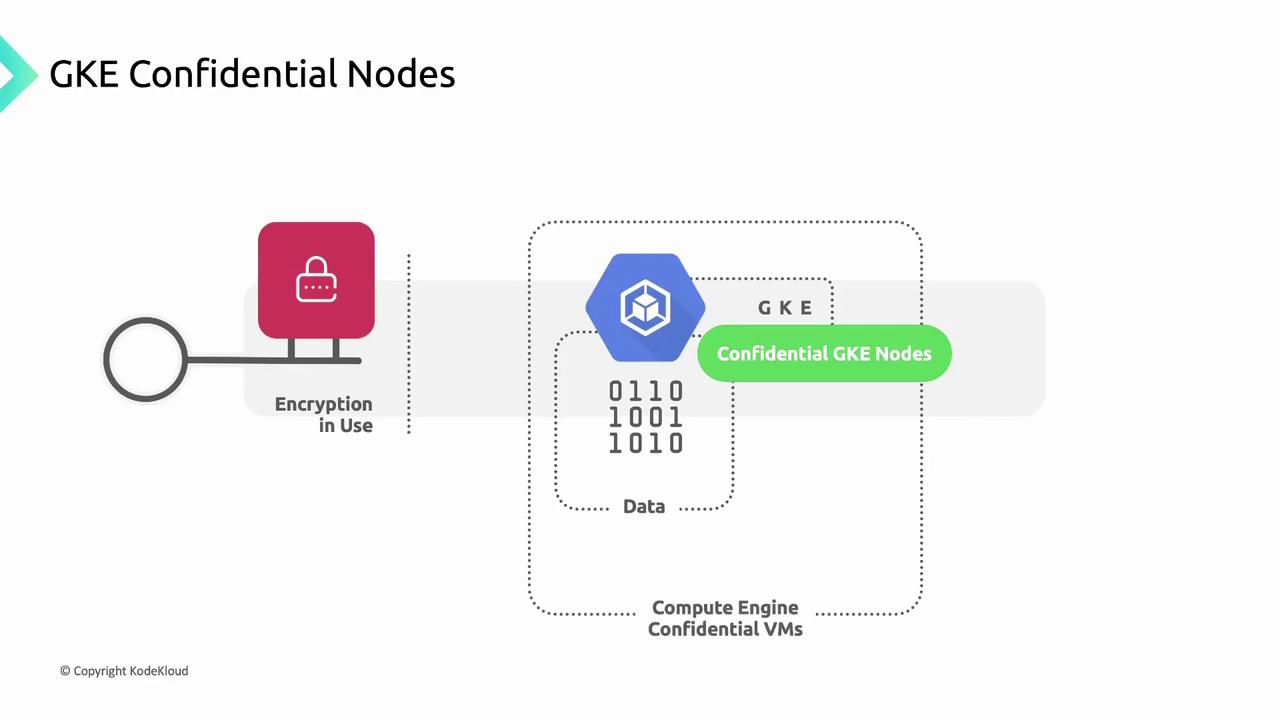
Enabling Confidential Nodes
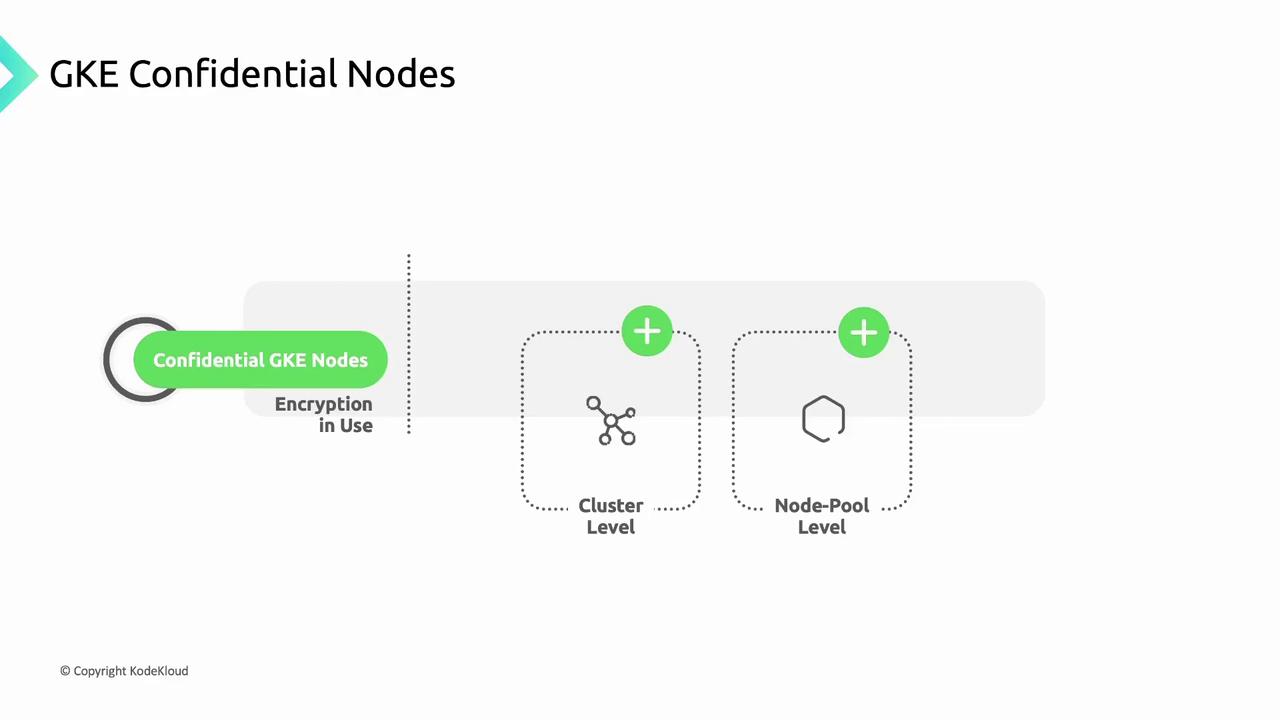
Confidential Nodes can be activated at:
Cluster level
- Enable during cluster creation to apply encryption-in-use across all node pools.
- This setting is irreversible for existing and new pools.
Node pool level
- In clusters with Confidential Nodes enabled, toggle per node pool when creating or updating.
- Only selected pools will enforce memory encryption.
Confidential GKE nodes incur no additional fees beyond standard Confidential VM pricing and produce slightly more detailed startup logs. They are available in regions and zones supporting N2D or C2D machine types.
References
Watch Video
Watch video content