HashiCorp Certified: Vault Associate Certification
Learning the Vault Architecture
Seal and Unseal
Vault’s seal and unseal mechanism protects your data at rest by ensuring the encryption key is only accessible in memory when explicitly unlocked. Every time Vault starts, it launches in a sealed state. In this state, Vault knows where your data resides (via its configured storage backend) but cannot decrypt it until the master key is reconstructed.
Vault Sealed State
When Vault is sealed:
- Only
vault statusand the unseal operation are permitted. - All other actions—reading or writing secrets, generating tokens, etc.—remain blocked.
Unsealing Vault reconstructs the master key, decrypts the in-memory encryption key, and allows normal operations. Sealing removes the encryption key from memory, requiring a fresh unseal to resume.

Why Seal Vault Manually?
Common reasons to seal Vault immediately include:
- Suspected exposure of unseal key shards (e.g., accidentally published in a public repo)
- Departure or unavailability of key-holding personnel
- Detection of network intrusion
- Malware or spyware discovered on Vault nodes
Warning
If unseal key shards are compromised or lost, Vault cannot decrypt the data at rest until a valid threshold of shards is provided. Store and distribute shards securely.
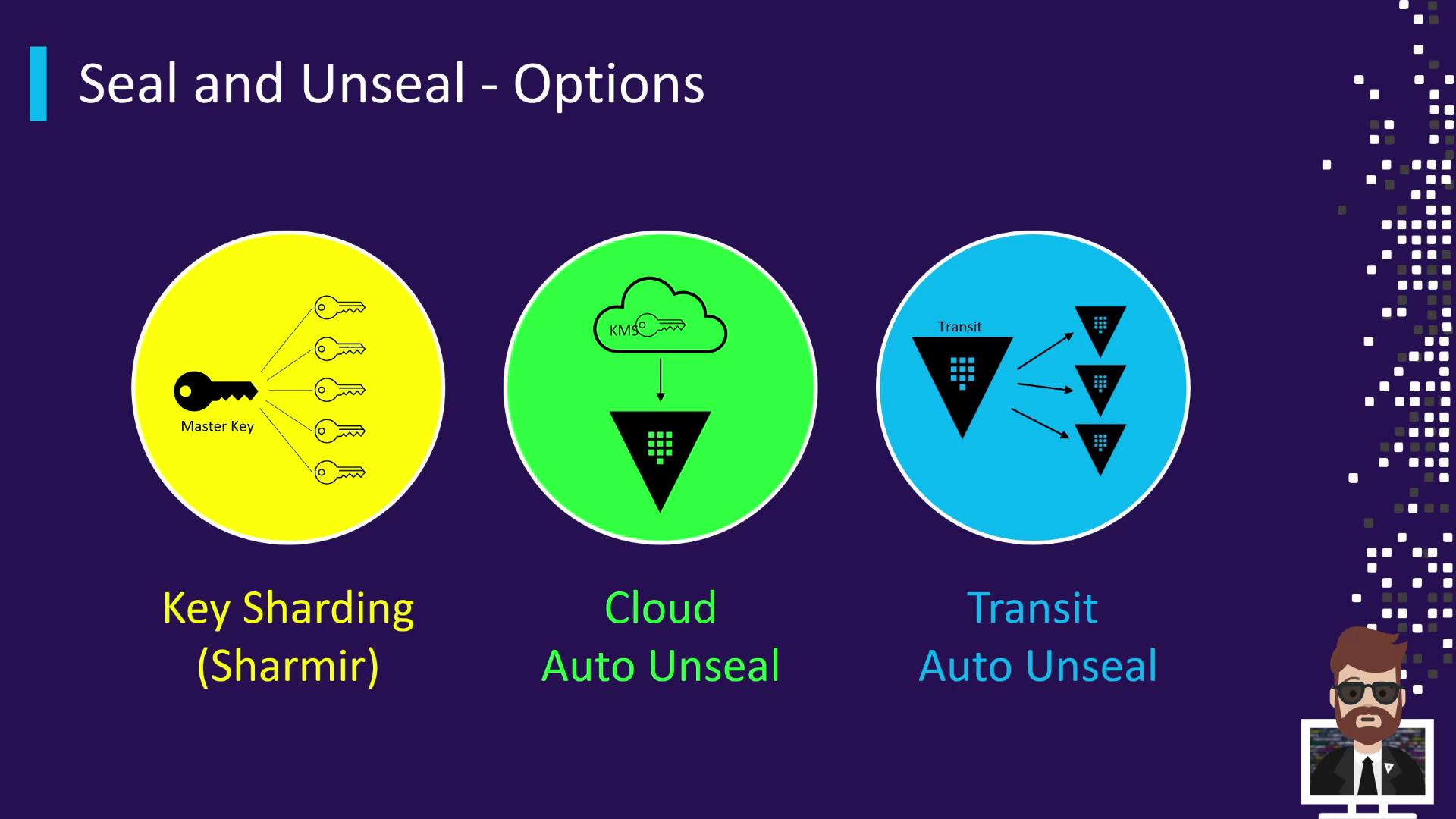
Sealing & Unsealing Methods
Vault supports three primary unseal mechanisms:
| Method | Description | Example Providers |
|---|---|---|
| Key Sharding | Default Shamir’s Secret Sharing splits the master key into N shares with a threshold. | n=5 shares, threshold=3 |
| Cloud Auto Unseal | Integrates with a cloud KMS to auto-unseal on startup. | AWS KMS, Azure Key Vault |
| Transit Auto Unseal | Uses a remote Vault (transit cluster) to protect and unseal the master key. | Vault Transit Secrets Engine (remote cluster) |
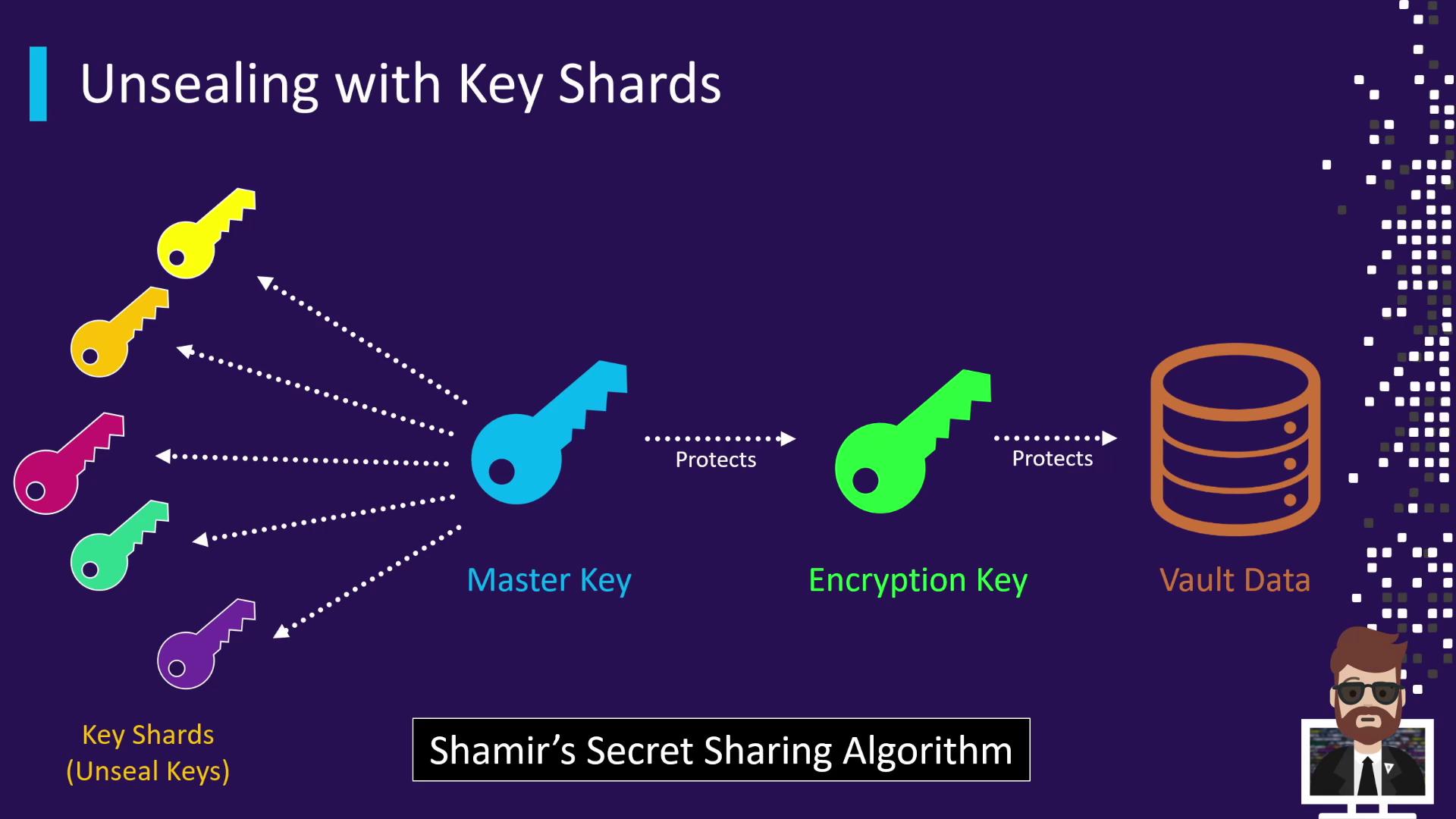
When Vault is initialized, the master key is split into multiple key shards using Shamir’s Secret Sharing. For example, Vault might create 5 shards with a threshold of 3. Each shard is handed to a different trusted individual.
To unseal:
- Provide at least the threshold number of shards.
- Vault combines them to reconstruct the master key.
- The master key decrypts the encryption key in memory, and Vault transitions to an unsealed state.
Step-by-Step Demo
Verify sealed status:
vault status # Key Value # --- ----- # Seal Type shamir # Sealed true # Total Shares 5 # Threshold 3 # Unseal Progress 0/3Submit two shards (order doesn’t matter):
vault unseal <key-shard-1> # Unseal Progress: 1/3 vault unseal <key-shard-2> # Unseal Progress: 2/3Provide the third shard:
vault unseal <key-shard-3> # Key Value # --- ----- # Seal Type shamir # Sealed false # Total Shares 5 # Threshold 3 # Version 1.7.0 # Storage Type consul # Cluster Name vault-cluster # Cluster ID xxx-xxx-xxx-xxx # HA Enabled true
Once unsealed, Vault displays runtime and cluster details and begins serving requests.
Best Practices for Key Shards
- Separate custody: Distribute shares so no single person holds the threshold.
- Encrypt at rest: Supply PGP public keys during initialization to encrypt each shard.
- Offline storage: Keep shards out of online systems and automated backups.
- Balance threshold: A higher threshold boosts security but may affect availability.
Note
Preparing PGP keys for shard encryption helps ensure that only the intended recipient can decrypt their shard.
Links and References
- Vault Secrets Engines
- HashiCorp Vault Documentation
- Shamir’s Secret Sharing on Wikipedia
- AWS KMS
- Azure Key Vault
- Vault Transit Secrets Engine
Watch Video
Watch video content