The Challenge with Legacy Applications
Many legacy apps cannot call Vault’s HTTP API. Even if Vault Agent auto-authenticates and fetches a token, the application can’t use it without direct Vault access. To bridge this gap, Vault Agent can render secrets into a local file that the application reads like any other configuration.What Is Consul Template?
Vault Agent’s templating builds on Consul Template, a standalone utility that:- Renders data from Vault or Consul into files
- Manages automatic secrets retrieval and renewal
- Operates without a running Consul cluster when used with Vault
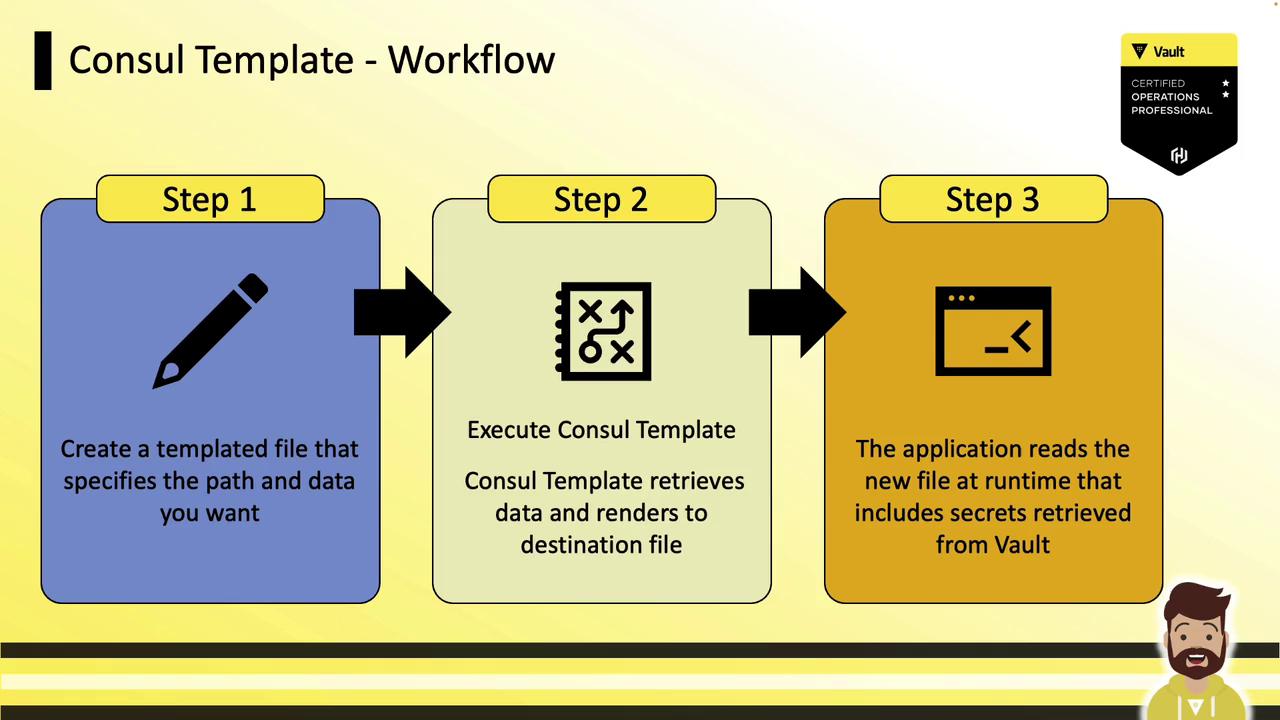
How Consul Template Works
Consul Template follows a simple three-step workflow:- Template Definition
Create a template file specifying Vault paths and placeholders. - Rendering
Run Consul Template; it fetches secrets and writes them to the destination file. - Application Consumption
The app reads the rendered file at runtime as a static config.
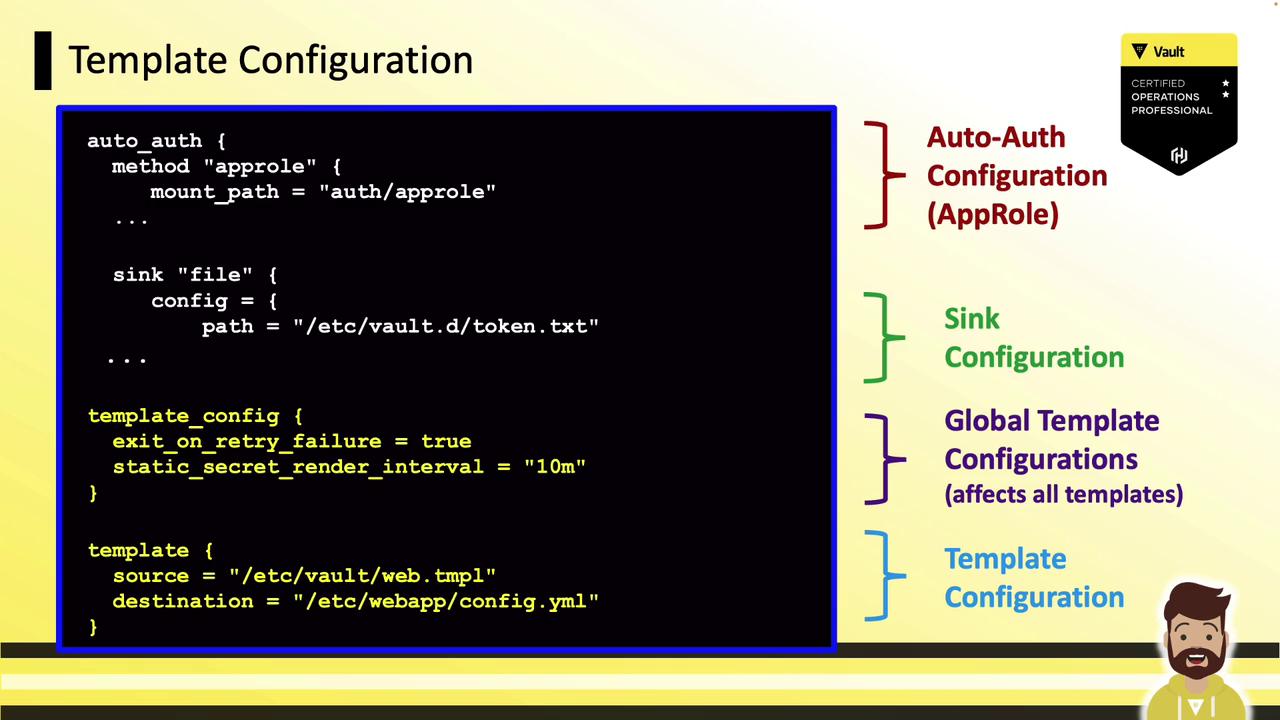
Example Template (config.tmpl)
secret "database/creds/readonly"points to the Vault secret path..Data.usernameand.Data.passwordextract the JSON fields returned by Vault.
config.yml contains:
config.yml for its credentials.
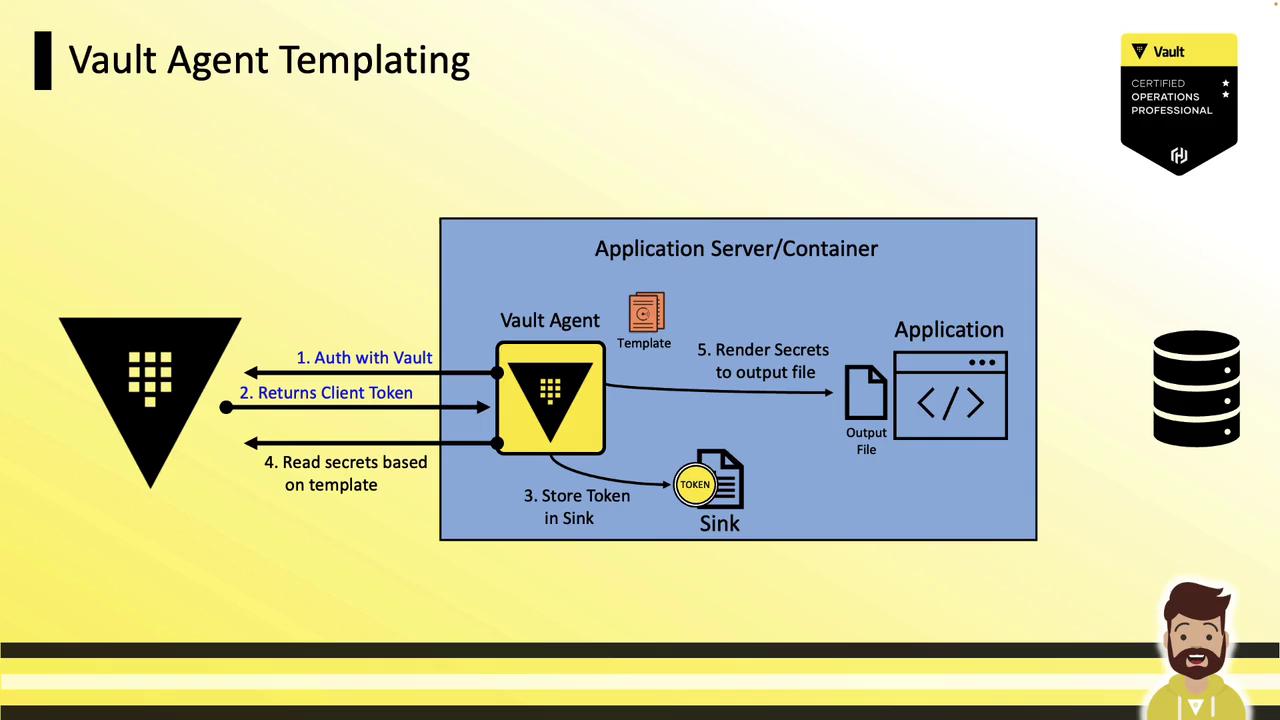
Vault Agent Templating Overview
Vault Agent now embeds Consul Template functionality—no separate binary needed. It handles both auto-auth and templating in one process:- Auto Auth
Vault Agent authenticates (e.g., AppRole, Kubernetes) and writes the token to a sink. - Templating
It reads secrets via the template and renders them to a local file. - Application
The app reads the rendered file and connects to external services using up-to-date credentials.
Comparing Consul Template vs. Vault Agent Templating
| Feature | Consul Template | Vault Agent Templating |
|---|---|---|
| Binary | Separate consul-template | Built into vault agent |
| Authentication | External token required | Integrated Auto Auth |
| Secret Renewal | Managed by Consul Template | Managed by Vault Agent |
| Configuration | HCL or CLI flags | HCL in agent.hcl |
Example Vault Agent Configuration
Use this HCL snippet to enable templating in Vault Agent:Ensure you’re running Vault Agent version 1.5+ to use built-in templating.
Storing tokens on disk can be a security risk. Protect the sink file with appropriate OS permissions.
/etc/vault/web.tmpl) can mirror the earlier Consul Template example.