HashiCorp Certified: Vault Operations Professional 2022
Configure Vault Agent
Vault Agent Templating
In this guide, we'll configure Vault Agent Templating to allow legacy applications to consume Vault secrets via local files without modifying application code.
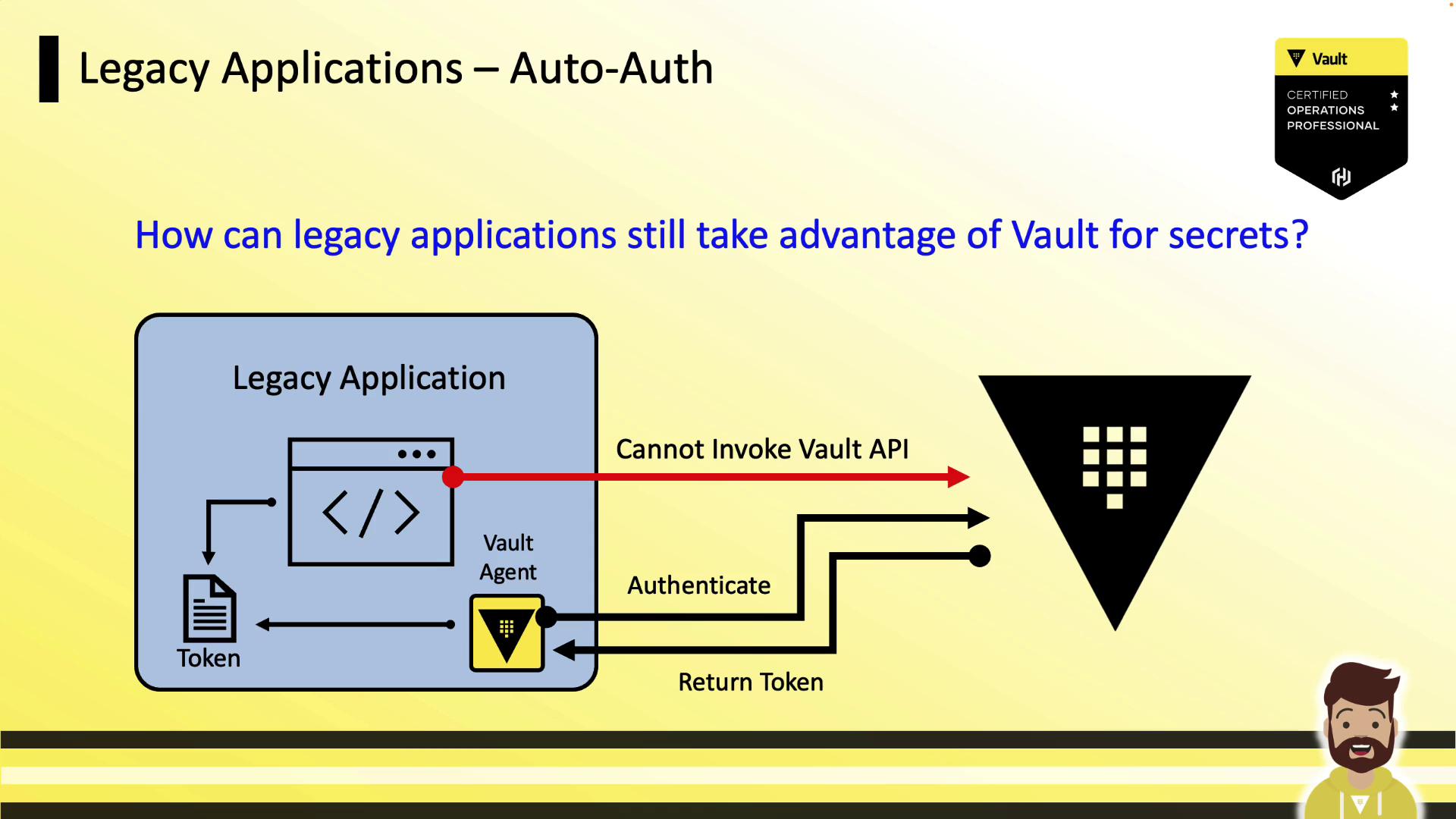
The Challenge
Legacy applications often cannot call the Vault HTTP API directly, so they lack a mechanism to fetch secrets using a Vault token. By delegating authentication and token management to Vault Agent, we can render secrets into files that such applications read like standard configuration.
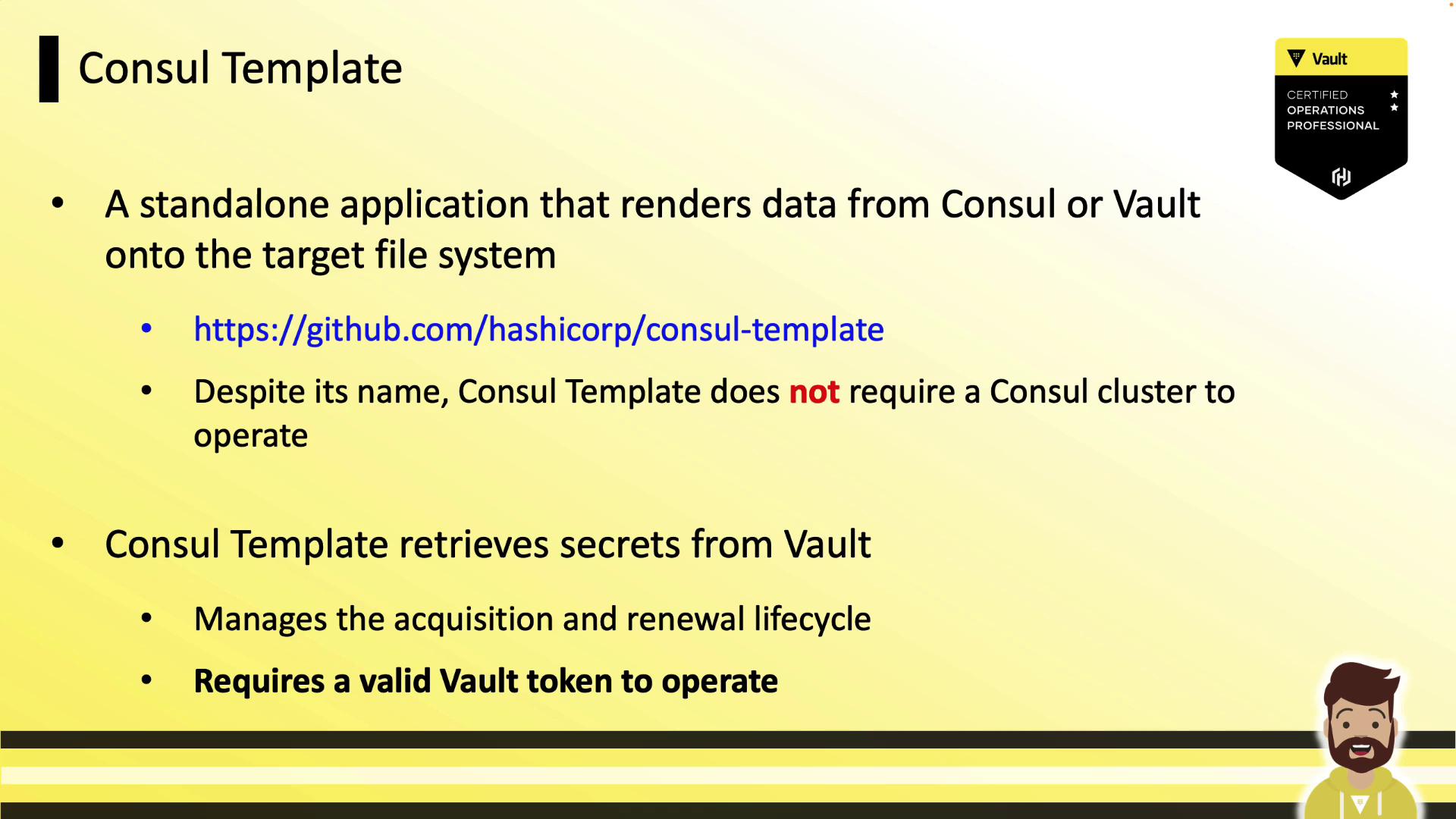
Consul Template Overview
Vault Agent Templating leverages the Consul Template engine. Despite its name, Consul Template can fetch and renew secrets directly from Vault.
Consul Template is a standalone binary that:
- Retrieves secrets from Vault (or data from Consul).
- Manages token acquisition and renewal.
- Renders secrets to a file based on a provided template.
- Requires a valid Vault token to operate.
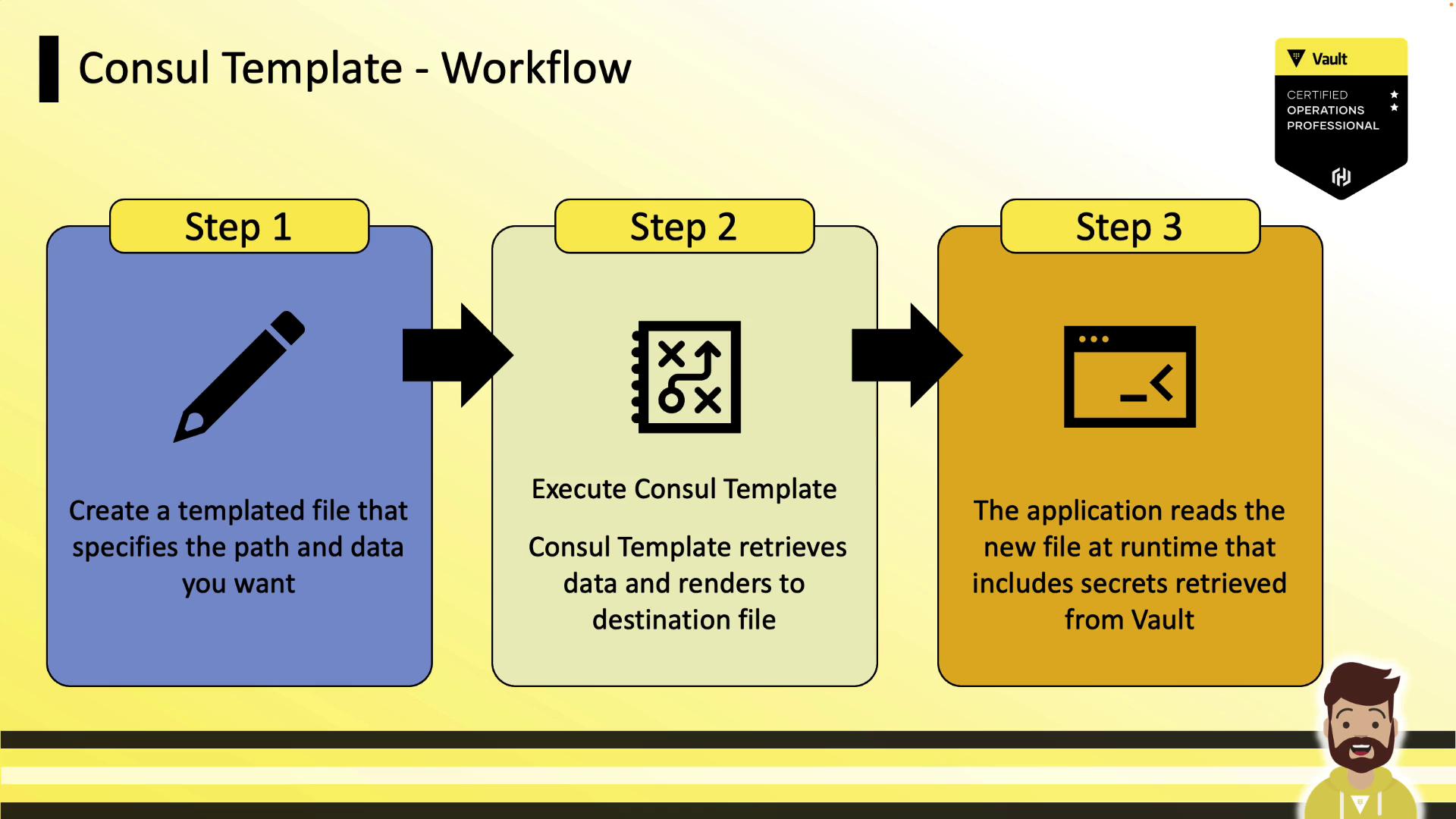
Consul Template Workflow
| Step | Description |
|---|---|
| 1. Create template | Define a file with Vault paths and data keys (e.g., {{ with secret "database/creds/readonly" }}) |
| 2. Run Consul Template | Fetch secrets and render to the destination file |
| 3. Application reads file | Legacy app uses the rendered file without calling Vault |
Example: Template Input (web.tmpl) and Rendered Output
Input (web.tmpl):
production:
adapter: postgresql
encoding: unicode
database: orders
host: postgres.hcvop.com
{{ with secret "database/creds/readonly" }}
username: "{{ .Data.username }}"
password: "{{ .Data.password }}"
{{ end }}
Output (config.yml):
production:
adapter: postgresql
encoding: unicode
database: orders
host: postgres.hcvop.com
username: "v-vault-readonly-fm3dfm20sm2s"
password: "fjk39fk49fks02k_3ks02mdz1s1"
Vault Agent Templating
Vault Agent integrates the Consul Template engine directly, removing the need for a separate binary. It uses Auto Auth to authenticate and then renders secrets via templates.
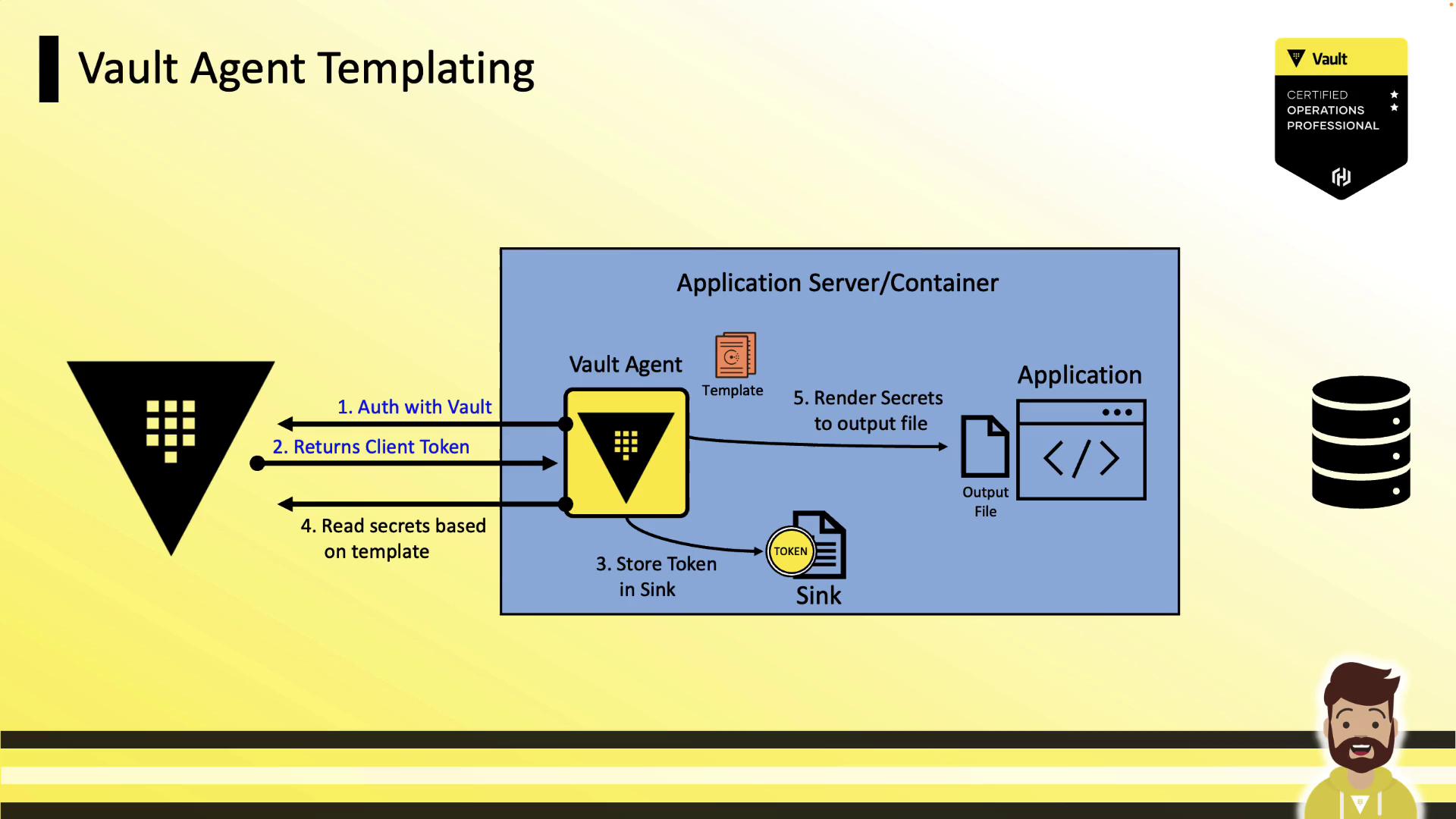
Templating Workflow
- Authentication
Vault Agent uses Auto Auth (AppRole, Kubernetes, AWS, etc.) to authenticate and writes the token to a sink. - Templating
The embedded Consul Template engine reads the template and fetches secrets from Vault. - Rendering
Secrets are written to the specified destination file. - Application Access
The legacy application reads the rendered file as its configuration.
Note
Vault Agent Templating supports multiple template blocks. Each block can point to a different source and destination file.
Configuration Example
Below is a minimal vault.hcl enabling Auto Auth and templating:
auto_auth {
method "approle" {
mount_path = "auth/approle"
role_name = "my-role"
}
sink "file" {
config = {
path = "/etc/vault.d/token.txt"
}
}
}
template_config {
exit_on_retry_failure = true
static_secret_render_interval = "10m"
}
template {
source = "/etc/vault/web.tmpl"
destination = "/etc/webapp/config.yml"
}
| Configuration Block | Purpose | Example Setting |
|---|---|---|
| auto_auth | Defines authentication method and token sink | method "approle" { ... } |
| template_config | Global templating options (retry, intervals) | exit_on_retry_failure = true |
| template | Template source and output destination | source = "/etc/vault/web.tmpl" |
Warning
The exit_on_retry_failure flag will terminate Vault Agent if templating consistently fails. Use with caution in production environments.
With this setup, unmodified legacy applications can seamlessly consume dynamic Vault-managed secrets via local configuration files.
Links and References
Watch Video
Watch video content