In this guide, you’ll learn how to leverage the HashiCorp Vault Identity Secrets Engine to:
- Create a user with the userpass auth method
- Define entities and entity aliases
- Observe how combined policies affect access
- (Optionally) Manage entities via the Vault UI
Before you begin, make sure a Vault server is running and you have a root token.
- Vault ≥ 1.0 installed and unsealed
- Root token for policy/entity management
vault CLI available in your $PATH
1. Review Existing Policies
List current policies to confirm what’s available:
Expected output:
default
engineering
kv-policy
manager
root
Policy Permissions Overview
| Policy | Path | Capabilities |
|---|
| kv-policy | kv/data/automation | read |
| manager | kv/data/operations/** | read |
2. Create a Userpass User
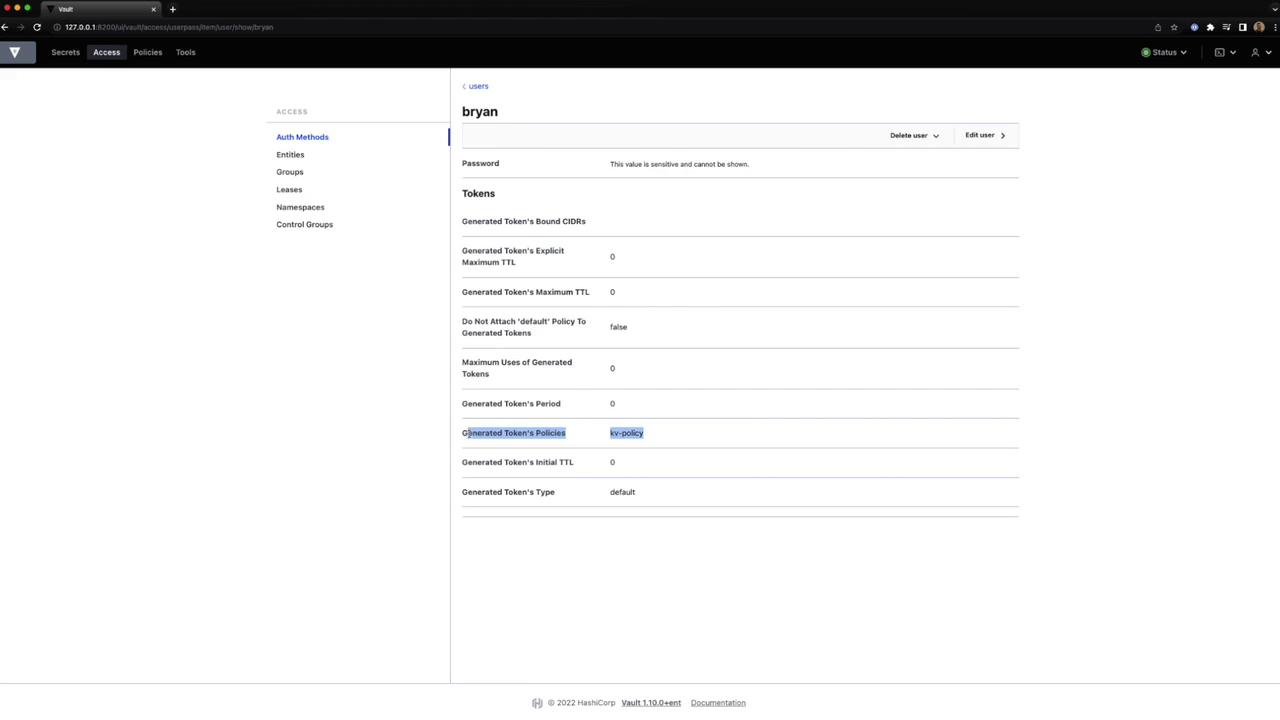
Define a new user bryan with the kv-policy attached:
vault write auth/userpass/users/bryan \
password=bryan \
policies=kv-policy
Success! Data written to: auth/userpass/users/bryan
vault policy read kv-policy
path "kv/data/automation" {
capabilities = ["read"]
}
manager policy:
vault policy read manager
path "kv/data/operations/**" {
capabilities = ["read"]
}
3. Authenticate as bryan and Test Access
Log in with the new user:
vault login -method=userpass username=bryan
Password (will be hidden):
token_policies ["default" "kv-policy"]
Test Allowed Access
vault kv get kv/automation
=== Secret Path ===
kv/data/automation
======= Metadata =======
Key Value
version 1
======= Data =======
Key Value
certification hcvop
Test Denied Access
vault kv get kv/operations/admin
Error reading kv/data/operations/admin: 403 Permission denied
You should see a 403 Permission denied error because kv-policy does not cover operations/**.
4. Obtain the Userpass Mount Accessor
Re-authenticate as root and list auth methods to retrieve the mount_accessor:
Path Type Accessor
---- ---- --------
token token auth_token_9e81d3bb
userpass/ userpass auth_userpass_0479382c
auth_userpass_0479382c value for the next step.
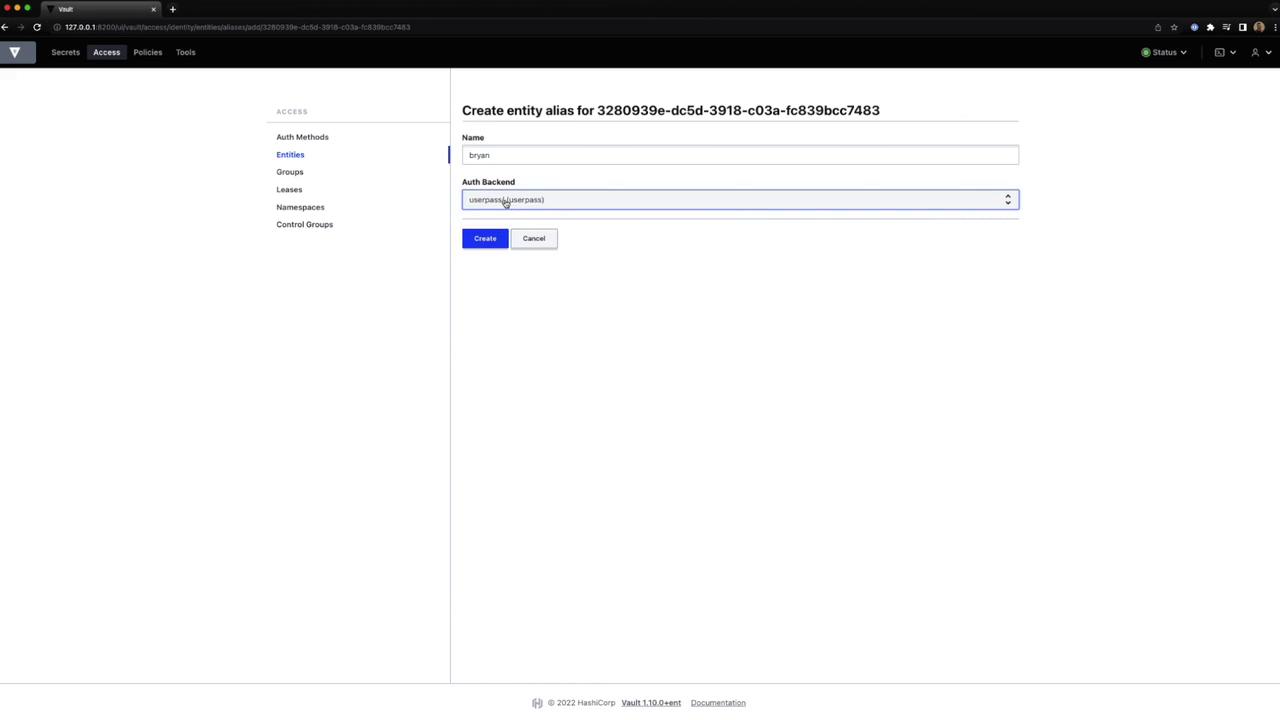
5. Create an Entity and Entity Alias
-
Create an entity named “Bryan Krausen” with the
manager policy:
vault write identity/entity \
name="Bryan Krausen" \
policies=manager
Key Value
--- -----
id 7a0f656b-8c8e-d6fd-83da-1d5650d85c38
name Bryan Krausen
-
Link the user to that entity via an alias:
vault write identity/entity-alias \
name="bryan" \
canonical_id="7a0f656b-8c8e-d6fd-83da-1d5650d85c38" \
mount_accessor="auth_userpass_0479382c"
Key Value
--- -----
canonical_id 7a0f656b-8c8e-d6fd-83da-1d5650d85c38
id 7a2a8c47-d65b-44a5-c0b5-8a45a9ddb588
6. Verify Combined Policies
Log back in as bryan:
vault login -method=userpass username=bryan
Password (will be hidden):
policies ["default" "kv-policy" "manager"]
identity_policies ["manager"]
Test Enhanced Access
-
Automation secret (via
kv-policy):
vault kv get kv/automation
-
Operations secret (via
manager policy):
vault kv get kv/operations/admin
=== Secret Path ===
kv/data/operations/admin
===== Data =====
Key Value
--- -----
creds lj3ofdj2posl2
You can repeat this process to add additional aliases (e.g., GitHub, OIDC) to grant the same manager policy across auth methods.
7. Using the Vault UI
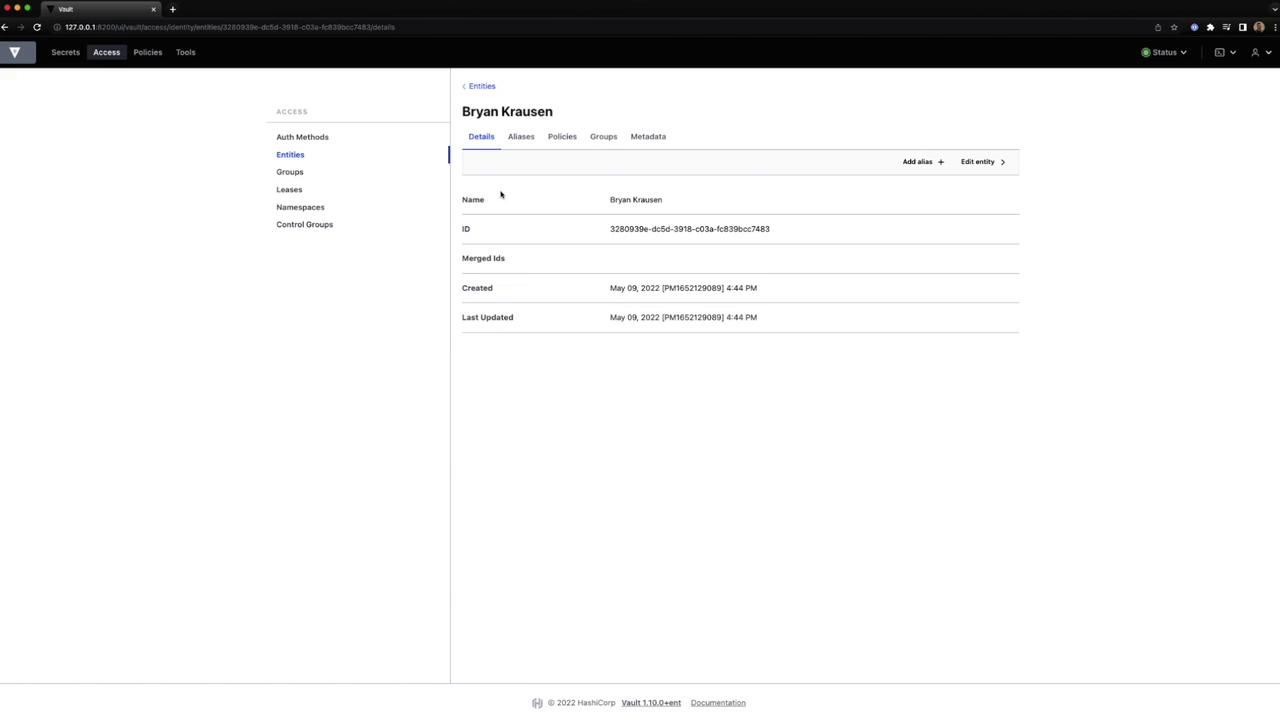
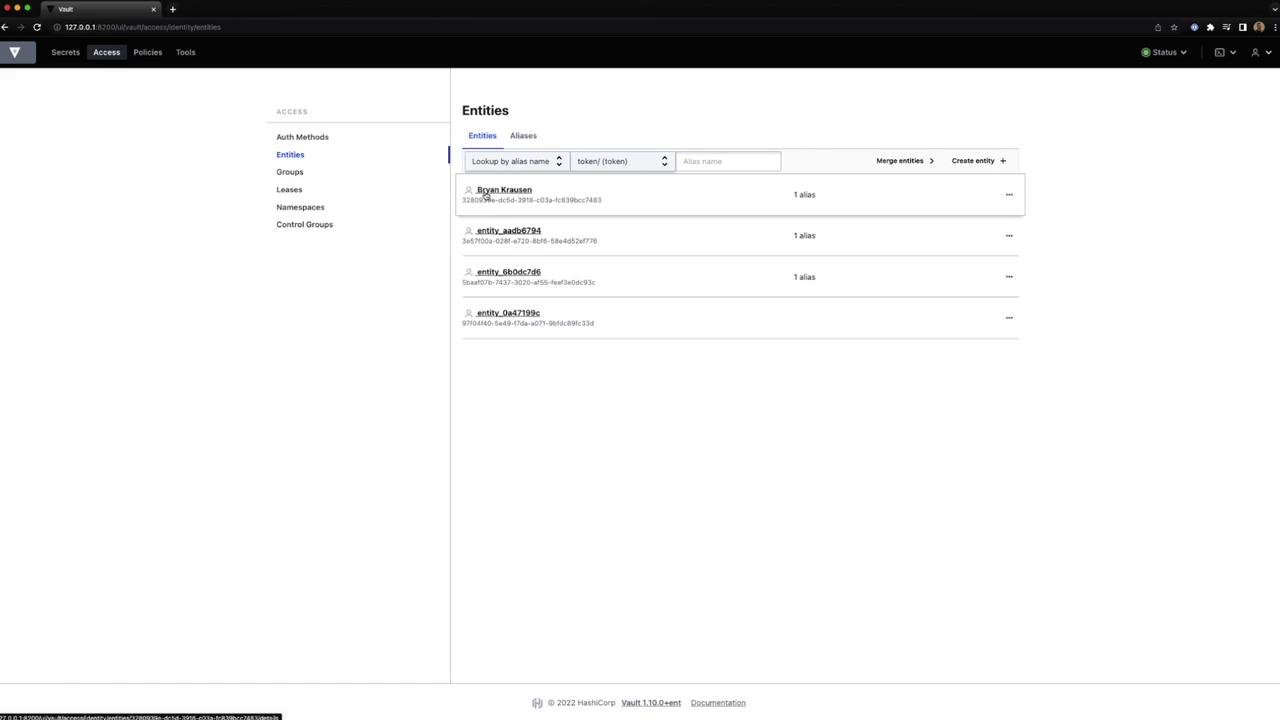
- In the Vault UI, navigate to Access → Entities.
- Create or delete entities, view details, and manage aliases.
- To add an alias, choose Create Entity Alias:
- Inspect token settings and policies:
- View or merge entities as needed:
Links and References