HashiCorp Certified: Vault Operations Professional 2022
Create a working Vault server configuration given a scenario
Enable and Configure Auth Methods
As a Vault Operations professional, you must enable, configure, and integrate Vault’s authentication methods for daily operations and certification exams. This guide introduces auth methods, explains their workflow, reviews supported options, and shows how to manage them via CLI and API.
What Are Auth Methods?
Auth methods in Vault validate credentials, assign identities, and issue client tokens. Every interaction with Vault—whether by a person or a machine—begins with authentication. Vault maps your credentials (from an external identity provider or an internal user store) to one or more policies, then issues a token that inherits those policies with a time-to-live (TTL).

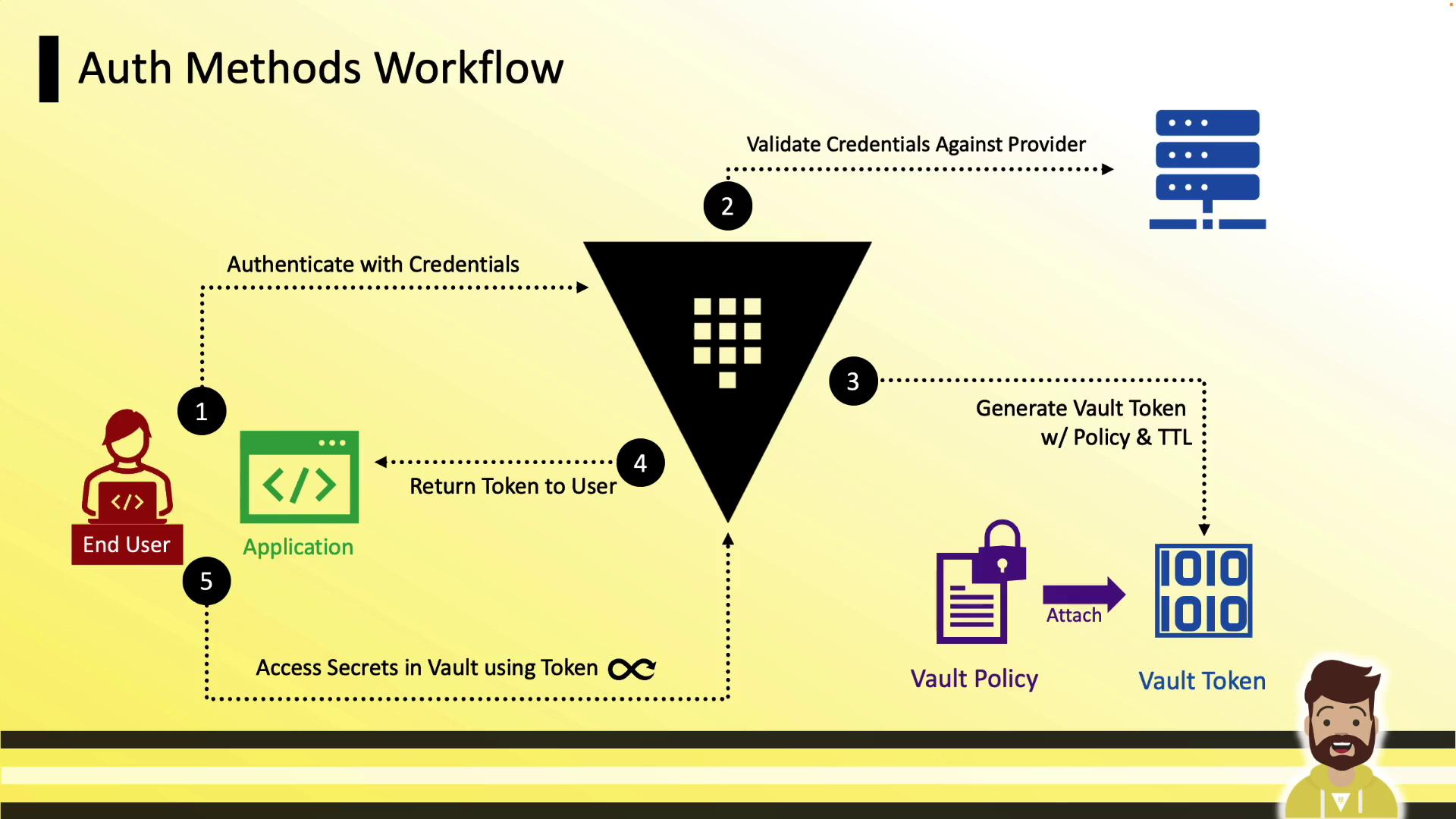
Auth Methods Workflow
- Client (human or system) submits credentials to an auth method (e.g., LDAP, userpass, JWT).
- Vault validates credentials internally or with an external provider.
- On success, Vault creates a token, attaches policies, and sets TTLs.
- The client uses the token to read secrets, write data, or generate dynamic credentials until the token expires.
Supported Auth Methods
Vault supports a wide range of authentication methods, including cloud platforms, OIDC/OAuth providers, identity services, and built-in options.
| Category | Methods |
|---|---|
| External (human/system) | AWS, Azure, Kubernetes, GitHub, Okta, OIDC, JWT, RADIUS, and more |
| Internal (built-in Vault) | AppRole, userpass, token, TLS |
Exam Tip
On Vault certification exams, focus on built-in methods (AppRole, userpass, token) since they don’t require external integrations.

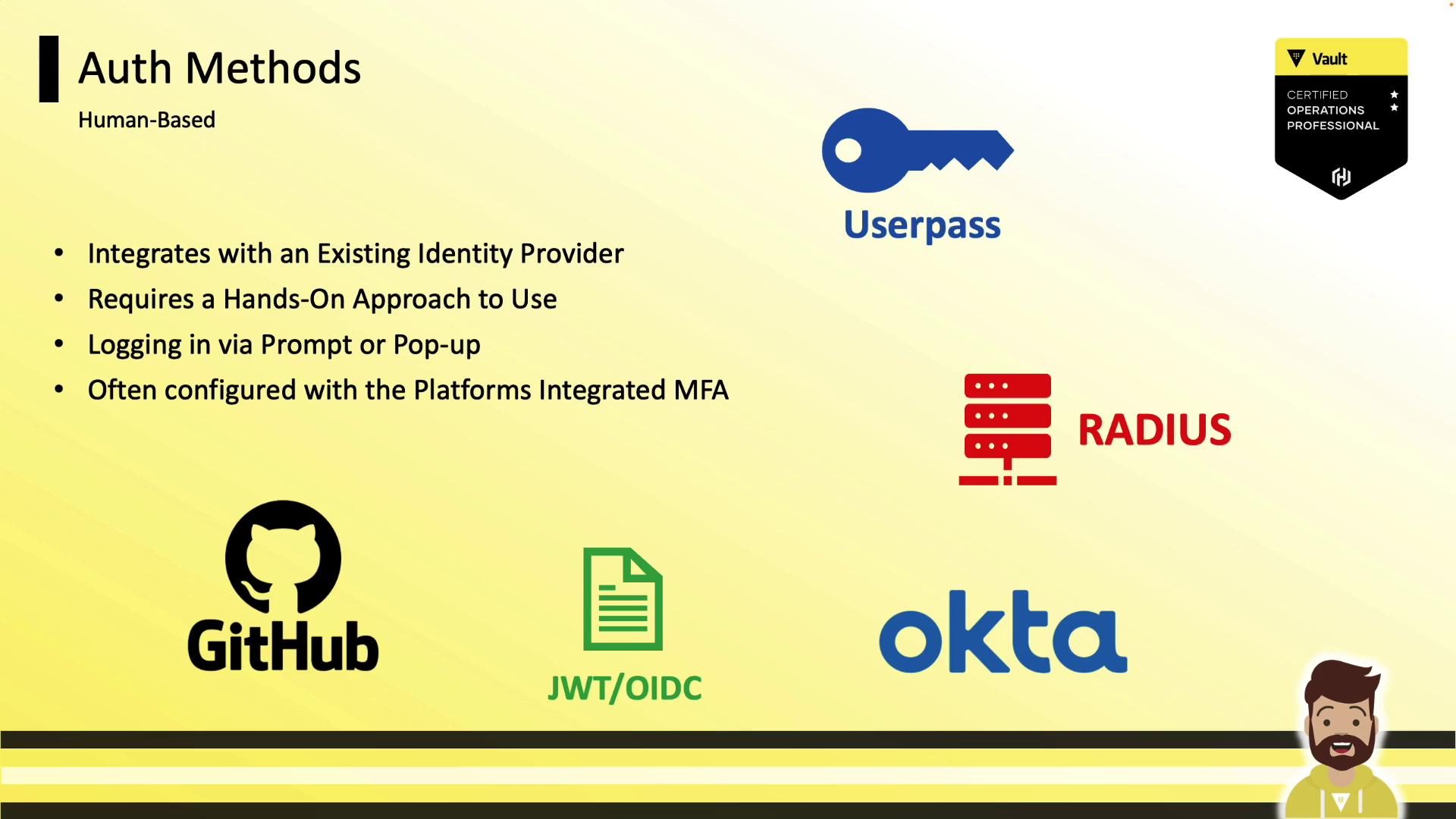
Human vs. System Authentication
Human-based auth methods integrate with identity providers or prompt users for credentials and MFA.
Examples:
- GitHub
- JWT/OIDC
- Okta
- RADIUS
- userpass
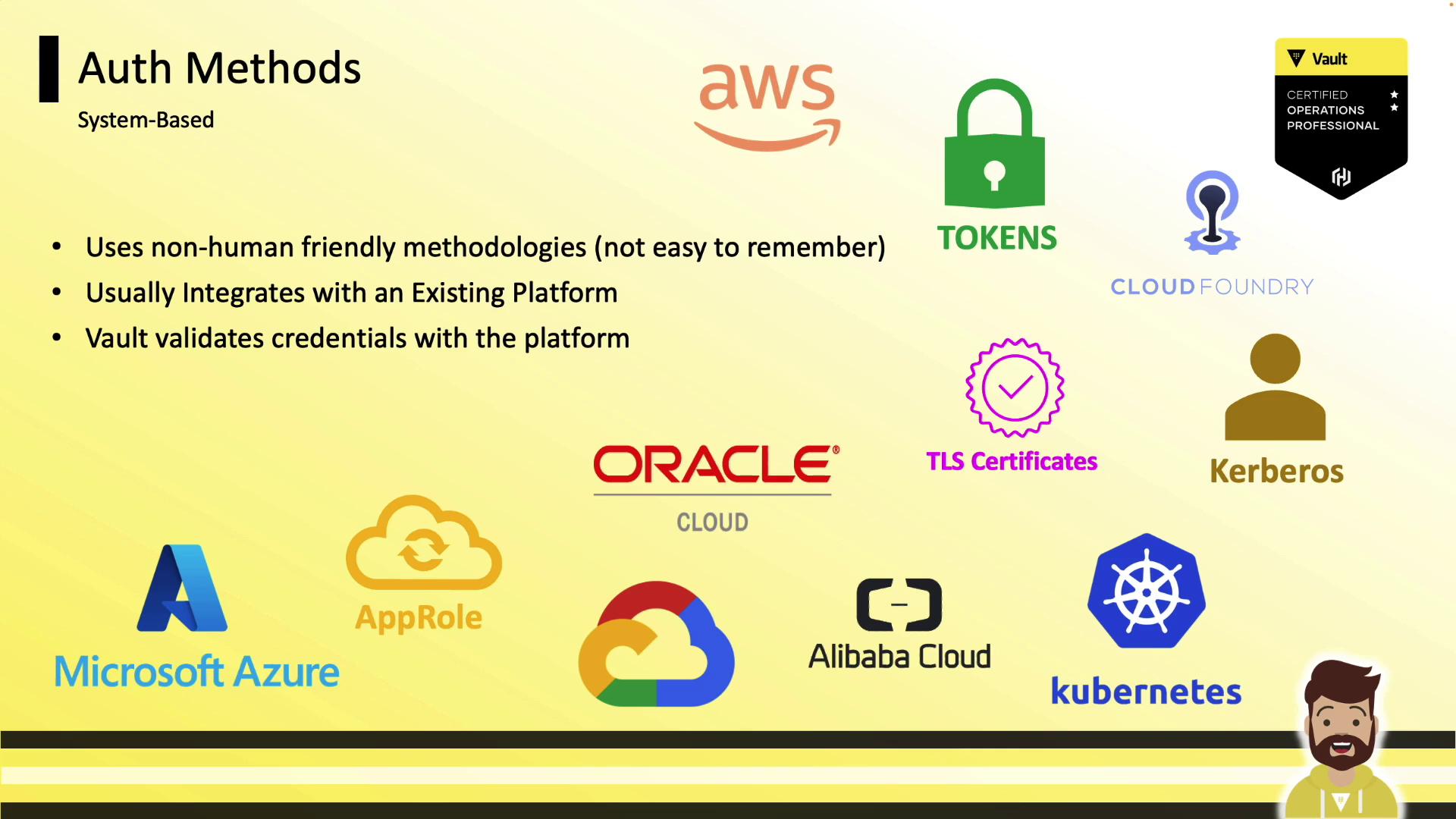
System-based auth methods rely on machine-friendly credentials issued by platform services.
Examples:
- AWS, Azure, GCP, Kubernetes, Alibaba, Oracle Cloud
- Kerberos (via Active Directory)
- TLS certificates
Managing Auth Methods in Vault
By default, Vault enables only two auth methods: identity and token. You can enable additional methods (even the same type at different paths). The token method is always active and cannot be disabled. To make changes, you need a valid Vault token with appropriate policies.
Permission Required
All auth method operations require a Vault token with the sys/auth/* capability. Without it, enable/disable and configuration commands will fail.


CLI: Enable, Disable, and List Auth Methods
Enable the AppRole method at its default path:
vault auth enable approle
# => Success! Enabled approle auth method at: approle/
Disable an auth method:
vault auth disable approle
# => Success! Disabled the auth method (if it existed) at: approle/
List enabled auth methods:
vault auth list
# => Path Type Accessor
# ---- ---- --------
# hcvop/ approle auth_approle_d8c20abe
# token/ token auth_token_89ce3371
# vault-course/ approle auth_approle_b3f0c92d
Custom Path Example
vault auth enable -path=training approle
vault auth list
# => Path Type Accessor
# training/ approle auth_approle_f1a2b3c4
Tuning Auth Methods
Adjust the max lease TTL for training/:
vault auth tune -max-lease-ttl=1h training/
# => Success! Tuned auth method: training/
Using an Auth Method
When interacting with credentials or roles, prefix the path with auth/. For example, create an AppRole role:
vault write auth/approle/role/hcvop \
secret_id_ttl=10m \
token_num_uses=10 \
token_ttl=20m \
token_max_ttl=30m \
secret_id_num_uses=40
# => Success! Data written to: auth/approle/role/hcvop
API Example: Enable an Auth Method
curl \
--header "X-Vault-Token: $VAULT_TOKEN" \
--request POST \
--data '{"type":"approle"}' \
https://vault.example.com/v1/sys/auth/approle
This API call enables the AppRole auth method at approle/.
Next Steps
Continue to the AppRole, userpass, and token method deep-dives for detailed workflows and best practices.
Links and References
Watch Video
Watch video content